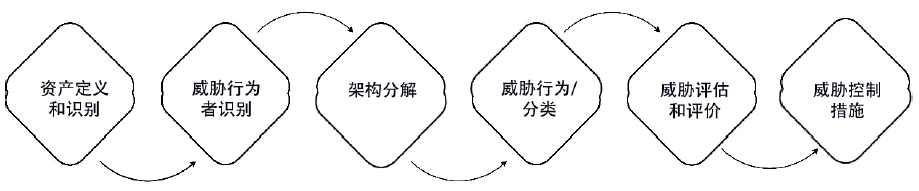
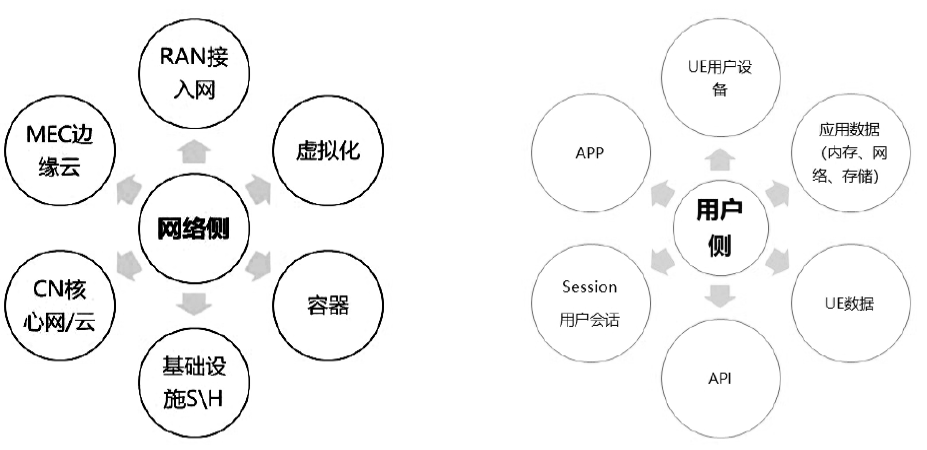
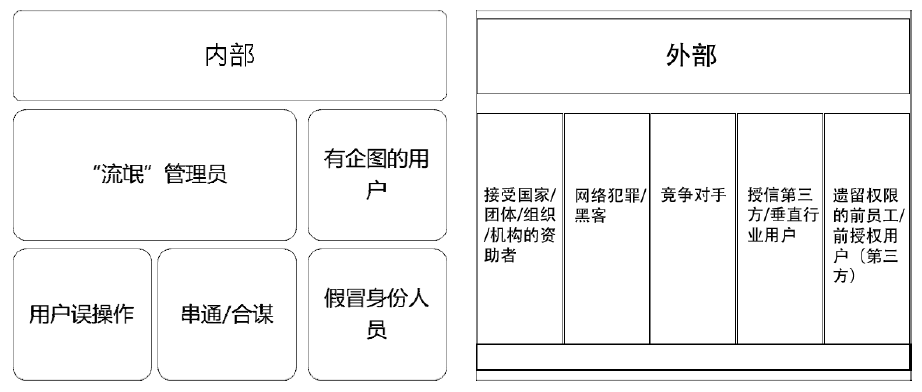
信息网络安全 ›› 2020, Vol. 20 ›› Issue (9): 72-76.doi: 10.3969/j.issn.1671-1122.2020.09.015
基于STRIDE-LM的5G网络安全威胁建模研究与应用
- 北京启明星辰信息安全技术有限公司,北京 100093
Research and Application of 5G Cybersecurity Threat Modeling Based on STRIDE-LM
- Beijing Venustech Information Security Technology Co.LTD, Beijing 100093, China