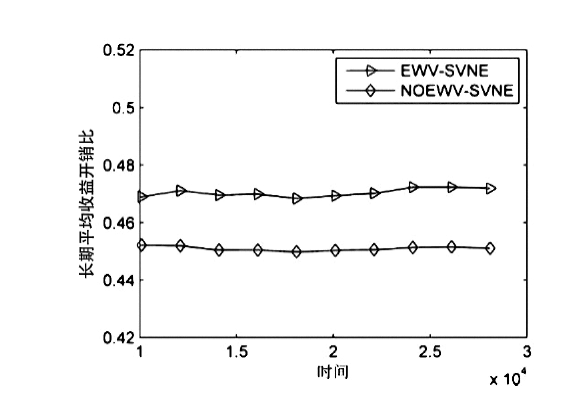
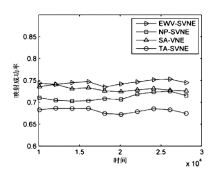
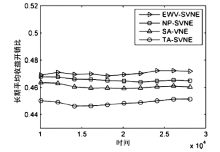
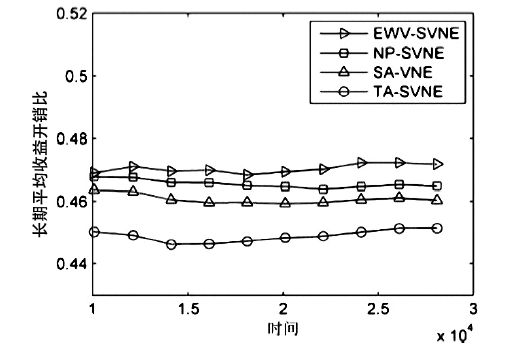
| [1] |
GUAN Yingying, ZONG Yue, LIU Yejun , et al. Virtual Network Embedding Supporting User Mobility in 5G Metro/Access Networks[EB/OL]. https://www.researchgate.net/publication/334485476_Virtual_Network_Embedding_Supporting_User_Mobility_in_5G_MetroAccess_Networks, 2020-2-10.
|
| [2] |
WANG Zhizhen, ZHENG Quan, CHEN Chen , et al. Virtual Network Mapping Algorithm Based on Network Simplex[J]. Computer Engineering, 2019,45(4):19-23, 30.
|
|
王志臻, 郑烇, 陈晨 , 等. 基于网络单纯形的虚拟网络映射算法[J]. 计算机工程, 2019,45(4):19-23,30.
|
| [3] |
FARKIANI B, BAKHSHI B, Mirhassani S A . Stochastic Virtual Network Embedding via Accelerated Benders Decomposition[J]. Future Generation Computer Systems, 2019,94:199-213.
doi: 10.1016/j.future.2018.11.048
URL
|
| [4] |
ZHU Guohui, LEI Lanjie, KANG Xiaoxuan . Network Function Virtualization Mapping Algorithm Based on Node Selection Strategy[J]. Study on Optical Communications, 2019,212(2):23-27.
|
|
朱国晖, 雷兰洁, 康潇轩 . 基于节点选择策略的网络功能虚拟化映射算法[J]. 光通信研究, 2019,212(2):23-27.
|
| [5] |
ZHENG Xiangwei, TIAN Jie, XIAO Xiancui , et al. A Heuristic Survivable Virtual Network Mapping Algorithm[J]. Soft Computing, 2019,23(5):1453-1463.
|
| [6] |
LIU Zhiguo, QIN Lingyu, LIU Qignli , et al. A Hybrid Virtual Network Mapping Algorithm Based on Threshold Load[J]. International Journal of Satellite Communications and Networking, 2019,37(3):224-233.
|
| [7] |
ZHANG Peiying, YAO Haipeng, LI Maozhen , et al. Virtual Network Embedding Based on Modified Genetic Algorithm[J]. Peer-to-Peer Networking and Applications, 2019,12(2):481-492.
|
| [8] |
XING Chiqiang, LAN Julong, HU Yuxiang . Virtual Network with Security Guarantee Embedding Algorithms[J]. JCP, 2013,8(11):2782-2788.
|
| [9] |
LIU Shuhao, CAI Zhiping, XU Hong , et al. Towards Security-aware Virtual Network Embedding[J]. Computer Networks, 2015,91:151-163.
|
| [10] |
GONG Shuiqing, CHEN Jing, HUANG Conghui , et al. Trust-aware Secure Virtual Network Embedding Algorithm[J]. Journal on Communications, 2015,36(11):180-189.
|
|
龚水清, 陈靖, 黄聪会 , 等. 信任感知的安全虚拟网络映射算法[J]. 通信学报, 2015,36(11):180-189.
|
| [11] |
BESIKTAS C, GOZUPEK D, ULAS A , et al. Secure Virtual Network Embedding with Flexible Bandwidth-based Revenue Maximization[J]. Computer Networks, 2017,121:89-99.
|
| [12] |
GONG Shuiqing, CHEN Jing, HUANG Conghui , et al. Virtual Network Embedding through Security Risk Awareness and Optimization[J]. KSII Transactions on Internet & Information Systems, 2016,10(7):234-248.
|
| [13] |
LIU Xinbo, WANG Buhong, LIU Shaiqi , et al. Heuristic Algorithm for Secure Virtual Network Embedding[J]. System Engineering and Electronics Technology, 2018,40(3):677-681.
|
|
刘新波, 王布宏, 刘帅琦 , 等. 安全虚拟网络映射的启发式算法[J]. 系统工程与电子技术, 2018,40(3):677-681.
|
| [14] |
Dwiardhika D, TACHIBANA T . Virtual Network Embedding Based on Security Level with VNF Placement[J]. Security and Communication Networks, 2019,2:1-11.
|
| [15] |
ZHANG Peiying, LI Haisheng, NI Yongjing , et al. Security Aware Virtual Network Embedding Algorithm Using Information Entropy TOPSIS[J]. Journal of Network and Systems Management, 2019(5):1-23.
|
| [16] |
LOGANATHAN J, JANAKIRAMAN S, DUMKA A . Optimal Spectrum-hole Detection Scheme for Cooperative CRN Using Dynamic Weighted VIKOR[J]. International Journal of Entweprise Information Systems(IJEIS), 2020,16(1):108-131.
|
 ), KANG Qiaoyan, HAN Xiaoyang
), KANG Qiaoyan, HAN Xiaoyang