信息网络安全 ›› 2018, Vol. 18 ›› Issue (11): 73-80.doi: 10.3969/j.issn.1671-1122.2018.11.010
即时通信网络数据劫持分析研究
- 1.解放军信息工程大学,河南郑州 450000
2. 中国科学院信息工程研究所信息安全国家重点实验室,北京 100093
3. 31011部队,北京 100093
-
收稿日期:2018-04-15出版日期:2018-11-10发布日期:2020-05-11 -
作者简介:作者简介:袁庆军(1993—),男,河北,硕士,主要研究方向为侧信道分析、网络空间安全等;陆思奇(1990—),男,山东,讲师,硕士,主要研究方向为协议分析、区块链等;韦忠兴(1993—),男,广西,实习研究员,主要研究方向为漏洞挖掘;苟杰(1991—),男,陕西,硕士,主要研究方向为信息系统安全。
-
基金资助:国家自然科学基金[61872381]
Analysis of Data Hijacking in Instant Communication Network
Qingjun YUAN1, Siqi LU1,2( ), Zhongxing WEI1, Jie GOU3
), Zhongxing WEI1, Jie GOU3
- 1. PLA University of Information Engineering, Zhengzhou Henan 450000, China
2. State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
3. 31011 PLA Troops, Beijing 100093, China
-
Received:2018-04-15Online:2018-11-10Published:2020-05-11
摘要:
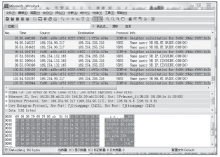
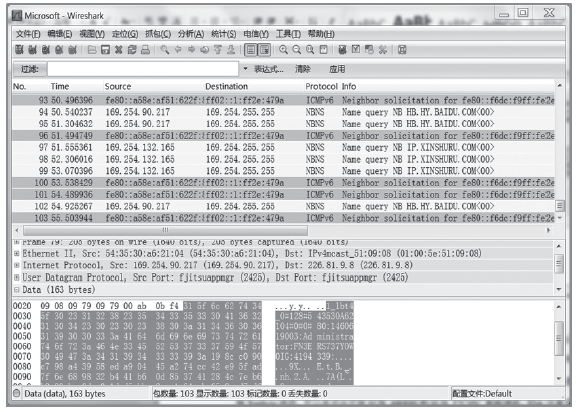
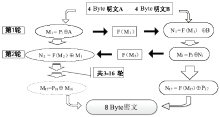
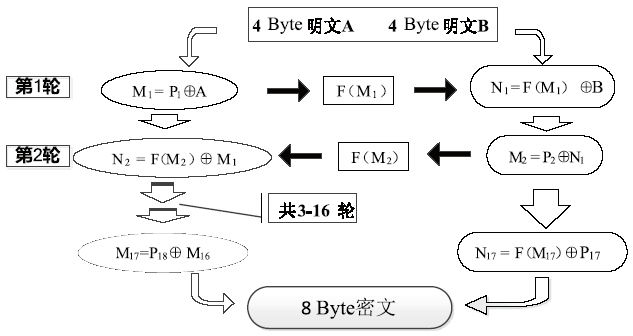
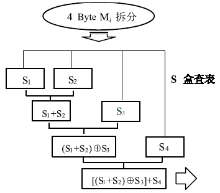
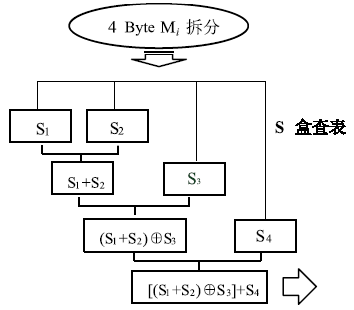
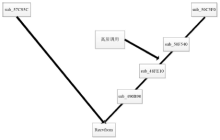
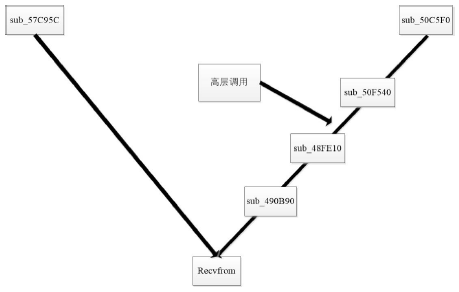
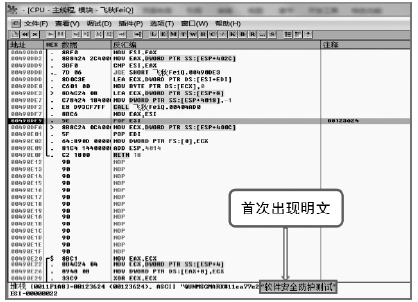
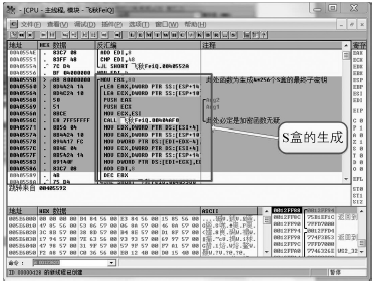
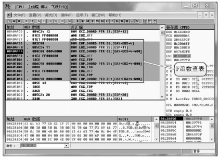
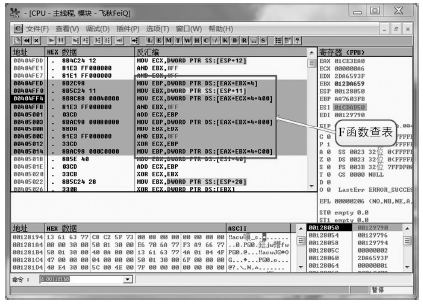
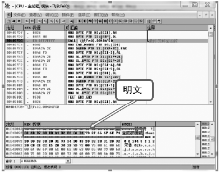
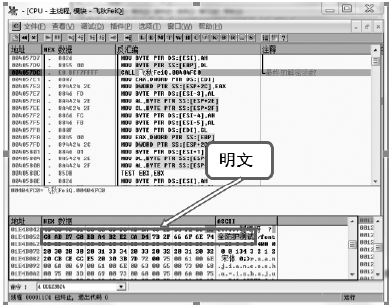
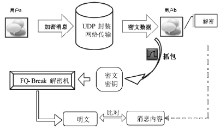
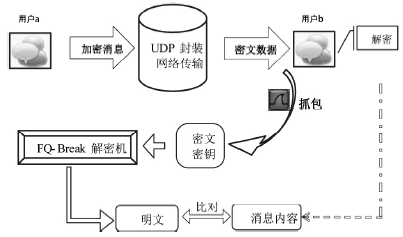
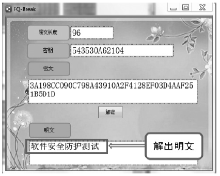
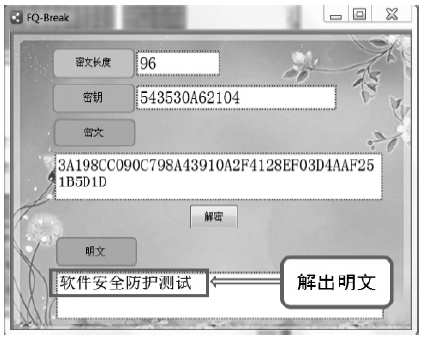
数据劫持是对即时通信网络中数据包进行截获分析的重要手段,严重威胁即时通讯网络安全。针对即时通信网络中安全理论和数据保护机制的研究,文章利用静态反汇编与动态调试结合的方法,解析通信数据的加解密操作,分析其通信数据保护机制。分析结果表明,即时通讯网络的保护机制存在一定缺陷,易被内部用户劫持。内部用户可通过分析通信数据,猜测数据包构成、通信机制和加密机制,获取关键参数、恢复系统密钥,截取软件解密关键代码,编写通信数据解密程序,获取通信网络中其他用户传递的秘密信息。进而篡改通信信息,破坏即时通信网络的机密性、可用性和可控性。
中图分类号:
引用本文
袁庆军, 陆思奇, 韦忠兴, 苟杰. 即时通信网络数据劫持分析研究[J]. 信息网络安全, 2018, 18(11): 73-80.
Qingjun YUAN, Siqi LU, Zhongxing WEI, Jie GOU. Analysis of Data Hijacking in Instant Communication Network[J]. Netinfo Security, 2018, 18(11): 73-80.
| [1] | LI Qiang, LIU Baoxu, JIANG Zhengwei, et al.Analysis of Model of QQ Forensic in Android System[J]. Netinfo Security, 2016,16(1):40-44. |
| 李强, 刘宝旭, 姜政伟, 等. 一种Android系统下的QQ取证模型分析[J]. 信息网络安全, 2016,16(1):40-44. | |
| [2] | PEDIY.Research on Communication Encryption of FeiQ[EB/OL]. , 2016-10-8. |
| [3] | SCHNEIER B.Description of a New Variable-length Key, 64-bit Block Cipher (Blowfish)[EB/OL]. ,2018-2-15. |
| [4] | PATEL P, PATEL R, PATEL N.Integrated ECC and Blowfish for Smartphone Security[J].Procedia Computer Science, 2016, 78(3): 210-216. |
| [5] | RUBAB S, JAVED Y.Efficient Image Steganogrphic Algorithms Utilizing Transforms: Wavelet and Contourlet with Blowfish Encryption[J]. International Journal of Computer Network & Information Security, 2015, 7(2): 15-24. |
| [6] | PATIL P, NARAYANKAR P, NARAYAN D G, et al. A Comprehensive Evaluation of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish[EB/OL]. ,2018-2-15. |
| [7] | GAO Junfeng, ZHANG Yuefeng, LUO Senlin, et al.Research on Reverse Analysis Method of Network Coding Protocol Taint Backtracking[J]. Netinfo Security, 2017,17(1):68-76. |
| 高君丰, 张岳峰, 罗森林,等.网络编码协议污点回溯逆向分析方法研究[J]. 信息网络安全, 2017,17(1):68-76. | |
| [8] | LIU Yu, WANG Minghua, SU Purui, et al.Communication Protocol Reverse Engineering of Malware Using Dynamic Taint Analysis[J]. Electronic Journal,2012,40(4):661-668. |
| 刘豫, 王明华, 苏璞睿,等. 基于动态污点分析的恶意代码通信协议逆向分析方法[J]. 电子学报, 2012, 40(4): 661-668. | |
| [9] | ZHENG Lifen, XIN Yang.Analysis and Implementation of QQ Software Protocol Based on DPI Technology[J]. Netinfo Security,2016,16(1):51-58. |
| 郑丽芬,辛阳. 基于DPI的即时通信软件协议分析与实现[J]. 信息网络安全, 2016,16(1):51-58. | |
| [10] | BANERJEE U, VASHISHTHA A, SAXENA M.Evaluation of the Capabilities of WireShark as a Tool for Intrusion Detection[J]. International Journal of Computer Applications, 2010, 6(7): 1-5. |
| [11] | PADARYAN V A, LEDOVSKIKH I N.On the Representation of Results of Binary Code Reverse Engineering[J]. Programming & Computer Software, 2018, 44(3):200-206. |
| [12] | CHEN Jiaying. Reverse Engineering for Binary Protocol Based on Network Traces[EB/OL]. ,2018-2-15. |
| [13] | WANG Jiagang, GU Guochang,MA Chunguang,et al.Efficient and Configurable Transmission Protocol Based on UDP in Grid Computing[J].Frontiers of Electrical and Electronic Engineering, 2009, 4(1): 35-42. |
| [1] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [2] | 刘敏, 陈曙晖. 基于关联融合的VoLTE流量分析研究[J]. 信息网络安全, 2020, 20(4): 81-86. |
| [3] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [4] | 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72. |
| [5] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [6] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [7] | 董晓丽, 商帅, 陈杰. 分组密码9轮Rijndael-192的不可能差分攻击[J]. 信息网络安全, 2020, 20(4): 40-46. |
| [8] | 郭春, 陈长青, 申国伟, 蒋朝惠. 一种基于可视化的勒索软件分类方法[J]. 信息网络安全, 2020, 20(4): 31-39. |
| [9] | 陈璐, 孙亚杰, 张立强, 陈云. 物联网环境下基于DICE的设备度量方案[J]. 信息网络安全, 2020, 20(4): 21-30. |
| [10] | 江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4): 12-20. |
| [11] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [12] | 刘鹏, 何倩, 刘汪洋, 程序. 支持撤销属性和外包解密的CP-ABE方案[J]. 信息网络安全, 2020, 20(3): 90-97. |
| [13] | 宋宇波, 樊明, 杨俊杰, 胡爱群. 一种基于拓扑分析的网络攻击流量分流和阻断方法[J]. 信息网络安全, 2020, 20(3): 9-17. |
| [14] | 王腾飞, 蔡满春, 芦天亮, 岳婷. 基于iTrace_v6的IPv6网络攻击溯源研究[J]. 信息网络安全, 2020, 20(3): 83-89. |
| [15] | 张艺, 刘红燕, 咸鹤群, 田呈亮. 基于授权记录的云存储加密数据去重方法[J]. 信息网络安全, 2020, 20(3): 75-82. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||