信息网络安全 ›› 2020, Vol. 20 ›› Issue (3): 83-89.doi: 10.3969/j.issn.1671-1122.2020.03.011
基于iTrace_v6的IPv6网络攻击溯源研究
- 中国人民公安大学,北京 100076
-
收稿日期:2019-10-15出版日期:2020-03-10发布日期:2020-05-11 -
作者简介:作者简介:王腾飞(1996—),男,河南,硕士研究生,主要研究方向为网络安全;蔡满春(1975—),男,河北,副教授,博士,主要研究方向为密码学、网络安全;芦天亮(1985—),男,河北,副教授,博士,主要研究方向为网络安全、恶意代码;岳婷(1996—),女,四川,硕士研究生,主要研究方向为恶意代码、网络安全。
-
基金资助:国家重点研发计划[2016YFB0801100];国家自然科学基金[61602489]
IPv6 Network Attack Source Tracing Method Based on iTrace_v6
WANG Tengfei, CAI Manchun( ), LU Tianliang, YUE Ting
), LU Tianliang, YUE Ting
- People’s Public Security University of China, Beijing 100076, China
-
Received:2019-10-15Online:2020-03-10Published:2020-05-11
摘要:
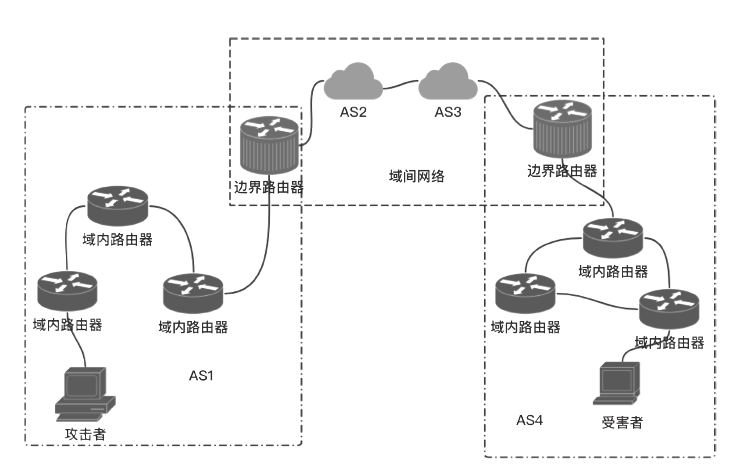
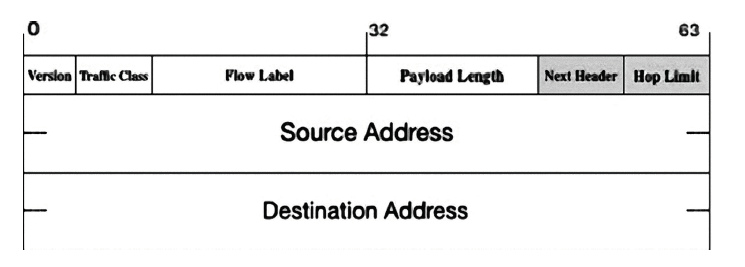
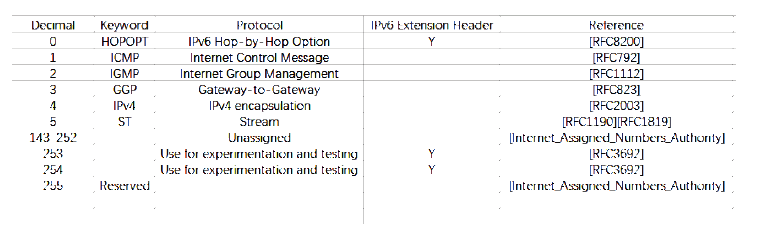
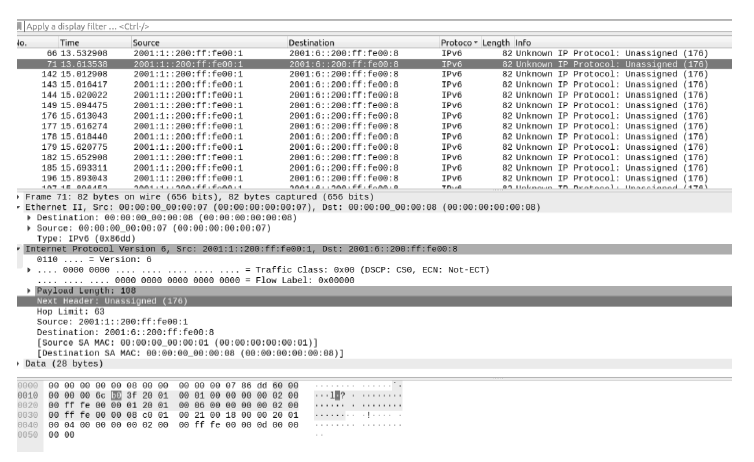
网络攻击追踪溯源技术作为一种主动的安全防御反制技术,是信息安全技术体系中应急响应的重要技术手段。IPv4网络的网络攻击溯源技术已有大量的研究成果,但由于路由器算力有限、对链路负面影响较大、日志系统部署困难等因素,一些溯源技术只能停滞在实验验证阶段;已成型的一些网络攻击回溯系统也存在着存储开销大、需要较多人工干预等方面的缺陷;在IPv6网络中,IP数据报格式、路由协议等发生了较大的改变,并且新出现的邻居发现协议等使得网络攻击手段更加多样,IPv6网络迫切需要高效稳定的网络攻击溯源方法。结合IPv6网络的特点,文章提出了一种基于iTrace_v6的IPv6网络攻击溯源方案,通过双重触发机制提高溯源包生成的效率,能够在显著减少对攻击持续时间依赖的情况下完成攻击路径的还原,通过区间阈值的使用来避免对网络链路的负面影响。基于NS3的仿真网络实验表明,本文算法性能优于已有的算法。
中图分类号:
引用本文
王腾飞, 蔡满春, 芦天亮, 岳婷. 基于iTrace_v6的IPv6网络攻击溯源研究[J]. 信息网络安全, 2020, 20(3): 83-89.
WANG Tengfei, CAI Manchun, LU Tianliang, YUE Ting. IPv6 Network Attack Source Tracing Method Based on iTrace_v6[J]. Netinfo Security, 2020, 20(3): 83-89.
| [1] | SANDERS C, SMITH J.Applied Network Security Monitoring: Collection, Detection, and Analysis[M]. New York: Syngress Publishing, 2013. |
| [2] | CHEN Zhouguo, PU Shi, ZHU Shixiong.General Traceback Technical Framework for Internet.[J] Computer Systems & Applications, 2012, 21(9): 166-170. |
| 陈周国,蒲石,祝世雄.一种通用的互联网追踪溯源技术框架[J].计算机系统应用,2012,21(9):166-170. | |
| [3] | CHEN Zhouguo, PU Shi, ZHU Shixiong.Levels Analysis of Network Attack Traceback.[J] Computer Systems & Applications, 2014, 23(1): 1-7. |
| 陈周国,蒲石,祝世雄.网络攻击追踪溯源层次分析[J].计算机系统应用,2014,23(1):1-7. | |
| [4] | ALENEZI M, REED M J.IP Traceback Methodologies[C]// IEEE . 2011 3rd Computer Science and Electronic Engineering Conference (CEEC), July 13-14,2011, Colchester, UK. New York:IEEE, 2011: 98-102. |
| [5] | BELLOVIN S. ICMP Traceback Message[EB/OL]. , 2019-9-15. |
| [6] | BABA T, MATSUDA S.Tracing Network Attacks to Their Sources[J]. IEEE Internet Computing, 2002, 6(2): 1-26. |
| [7] | FENG Bo, GUO Fan, TAN Suwen.Attack Source Traceback Scheme Based on Probabilistic Packet Marking for IPv6 Network[J]. Computer Engineering and Applications, 2016, 52(6): 102-106. |
| 冯波,郭帆,谭素雯.基于IPv6的概率包标记路径溯源方案[J].计算机工程与应用, 2016, 52(6):102-106. | |
| [8] | ZHU Tian, TIAN Ye, MA Di, et al.Packet Verification Based Traceback Method for IPv6 Translation Mechanism[J]. Journal of Computer Applications, 2013, 33(4): 926-930. |
| 朱田,田野,马迪,等.基于包验证的面向IPv6翻译机制的IP追溯方法[J].计算机应用, 2013, 33(4):926-930. | |
| [9] | YANG M, YANG M.RIHT: A Novel Hybrid IP Traceback Scheme[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(2): 789-797. |
| [10] | SINGH K, SINGH P, KUMAR K, et al.A Systematic Review of IP Traceback Schemes for Denial of Service Attacks[J]. Computers & Security, 2016, 25(8): 111-139. |
| [11] | MANKIN A, MASSEY D, WU ChienLung, et al. On Design and Evaluation of Intention-Driven ICMP Traceback[C]// IEEE. Proceedings Tenth International Conference on Computer Communications and Networks, October 15-17, 2002, Scottsdale, AZ, USA. New York:IEEE, 2002: 3-28. |
| [12] | SAURABH S, SAIRAM A S.ICMP based IP Traceback with Negligible Overhead for Highly Distributed Reflector Attack Using Bloom Filters[J]. Computer Communications, 2014, 42(2): 60-69. |
| [13] | GAO Z.Tracing Cyber Attacks from the Practical Perspective[J]. IEEE Communications Magazine, 2005, 43(5): 123-131. |
| [14] | MURUGESAN V, SHALINIE M, YANG M H.Design and Analysis of Hybrid Single Packet IP Traceback Scheme[J]. Iet Networks, 2018, 7(3): 141-151. |
| [15] | CARPENTER B. Transmission and Processing of IPv6 Extension Headers [EB/OL].,2019-9-15. |
| [16] | MANDHAR V, RANGA V. IP Traceback Schemes for DDoS Attack[EB/OL]. , 2019-9-15. |
| [17] | KAMALDEEP K, MALIK M, DUTTA M.Implementation of single-Packet Hybrid IP Traceback for IPv4 and IPv6 Networks[J]. IET Information Security, 2018, 12(1): 1-6. |
| [18] | PARASHAR A, RADHAKRISHNAN R. Improved Deterministic Packet Marking Algorithm for IPv6 Traceback[EB/OL]. , 2019-9-15. |
| [19] | YIM H B , JUNG J I . IP Traceback Algorithm for DoS/DDoS Attack[EB/OL]. , 2019-9-15. |
| [20] | LU Ning, WANG Shangguang, LI Feng, et al.Dynamically Scalable and Efficient Approach for Single-Packet Traceback[J]. Journal of Software, 2018, 29(11): 320-340. |
| 鲁宁,王尚广,李峰.可动态扩展的高效单包溯源方法[J].软件学报, 2018, 29(11):320-340. |
| [1] | 董威, 李永刚. 基于复杂网络的智能电网网络攻击影响分析研究[J]. 信息网络安全, 2020, 20(1): 52-60. |
| [2] | 陈良臣, 刘宝旭, 高曙. 网络攻击检测中流量数据抽样技术研究[J]. 信息网络安全, 2019, 19(8): 22-28. |
| [3] | 陈冠衡, 苏金树. 基于深度神经网络的异常流量检测算法[J]. 信息网络安全, 2019, 19(6): 68-75. |
| [4] | 傅建明, 黎琳, 郑锐, 苏日古嘎. 基于GAN的网络攻击检测研究综述[J]. 信息网络安全, 2019, 19(2): 1-9. |
| [5] | 夏玉明, 胡绍勇, 朱少民, 刘丽丽. 基于卷积神经网络的网络攻击检测方法研究[J]. 信息网络安全, 2017, 17(11): 32-36. |
| [6] | 宋国江, 肖荣华, 晏培. 工业控制系统中PLC面临的网络空间安全威胁[J]. 信息网络安全, 2016, 16(9): 228-233. |
| [7] | 裘玥. 匿名网络的安全监管隐患与信息获取技术研究[J]. 信息网络安全, 2015, 15(9): 106-108. |
| [8] | 俞诗源, 程三军. 大数据工具在网络攻击监测中的应用[J]. 信息网络安全, 2015, 15(9): 149-153. |
| [9] | 夏坤鹏, 谢正勇, 崔伟. 基于IDS报警和rootkit的威胁溯源方法研究[J]. 信息网络安全, 2015, 15(9): 231-235. |
| [10] | 金志虎, 甘玉玺, 金毅, 胡龙斌. 构建安全可靠的IPv6驻地网络的探讨[J]. 信息网络安全, 2015, 15(8): 59-66. |
| [11] | 芦天亮, 周运伟, 曹巍. 移动互联网攻击技术及违法犯罪手段分析[J]. 信息网络安全, 2014, 14(9): 176-179. |
| [12] | 严俊龙. 基于Metasploit框架自动化渗透测试研究[J]. , 2013, 13(2): 0-0. |
| [13] | 钱福民;张海港. 浅谈下一代基于IPv6互联网的安全保护[J]. , 2012, 12(Z): 0-0. |
| [14] | 温昱晖;任卫红;于毅;申永波. IPv6环境下信息安全等级保护面临的挑战与应对[J]. , 2012, 12(Z): 0-0. |
| [15] | 沈亮;张艳;顾健. 物联网网络层中基于IPv6的信息安全产品发展趋势研究[J]. , 2012, 12(8): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||