信息网络安全 ›› 2018, Vol. 18 ›› Issue (11): 66-72.doi: 10.3969/j.issn.1671-1122.2018.11.009
指定审计员的云数据安全存储方案
- 1. 桂林电子科技大学机电工程学院,广西桂林 541004
2. 桂林电子科技大学广西密码学与信息安全重点实验室,广西桂林 541004
3. 桂林电子科技大学计算机与信息安全学院,广西桂林 541004
-
收稿日期:2018-08-01出版日期:2018-11-10发布日期:2020-05-11 -
作者简介:作者简介:赵萌(1981—),女,江苏,讲师,硕士,主要研究方向为应用密码学;丁勇(1975—),男,重庆,教授,博士,主要研究方向为密码学;王玉珏(1981—),男,安徽,讲师,博士,主要研究方向为应用密码学、云计算安全。
-
基金资助:国家自然科学基金[61772150,61862012,61862011,61602125]:国家密码发展基金[MMJJ20170217];广西重点研发计划[AB17195025];广西密码学与信息安全重点实验室研究课题[GCIS201702]
Secure Cloud Data Storage with Designated Auditors
Meng ZHAO1, Yong DING2,3, Yujue WANG2,3( )
)
- 1. School of Mechanical and Electrical Engineering, Guilin University of Electronic Technology, Guilin Guangxi 541004, China
2. Guangxi Key Laboratory of Cryptography and Information Security, Guilin University of Electronic Technology, Guilin Guangxi 541004, China
3. School of Computer Science and Information Security, Guilin University of Electronic Technology, Guilin Guangxi 541004, China
-
Received:2018-08-01Online:2018-11-10Published:2020-05-11
摘要:
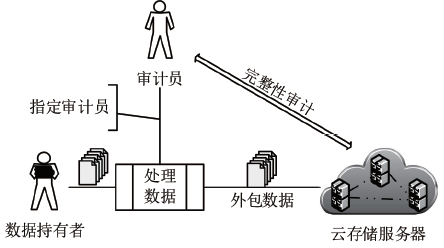
借助云存储技术,用户无需构建本地软硬件存储设施,从而减少了本地存储的成本。面对云存储环境下用户外包数据完整性保护需求以及数据持有者失去数据控制权的问题,数据持有者可以指定预期的审计员对其外包数据进行完整性审计。文章基于双线性群提出一种指定审计员的云安全存储方案,要求审计员在完整性审计阶段使用其私钥才可验证云存储服务器的响应,从而判断外包数据的完整性。文章进一步研究了在数据处理阶段数据持有者同时指定两个审计员的场景,在执行完整性审计时审计员之间无需交互。由安全分析和效率分析可知,文中方案是安全高效的。
中图分类号:
引用本文
赵萌, 丁勇, 王玉珏. 指定审计员的云数据安全存储方案[J]. 信息网络安全, 2018, 18(11): 66-72.
Meng ZHAO, Yong DING, Yujue WANG. Secure Cloud Data Storage with Designated Auditors[J]. Netinfo Security, 2018, 18(11): 66-72.
| [1] | ARMBRUST M, FOX A, GRIFFITH R, et al.Above the Clouds: A Berkeley View of Cloud Computing[R]. USA: Electrical Engineering and Computer Sciences, University of California at Berkeley, TR UCB/EECS-2009-28, 2009. |
| [2] | WANG Yujue, WU Qianhong.A Survey on Cryptographic Technologies for Data Integrity Checking in Clouds[J]. Journal of Cyber Security, 2017, 2(3): 23-35. |
| 王玉珏,伍前红. 云存储完整性验证密码学技术研究进展[J]. 信息安全学报,2017,2(3):23-35. | |
| [3] | YU Nenghai, HAO Zhuo, XU Jiajia, et al.Review of Cloud Computing Security[J]. Acta Electronica Sinica, 2013, 41(2): 371-381. |
| 俞能海,郝卓,徐甲甲,等. 云安全研究进展综述[J]. 电子学报,2013,41(2):371-381. | |
| [4] | ATENIESE G, BURNS R, CURTMOLA R, et al.Provable Data Possession at Untrusted Stores[C]//ACM. 14th ACM Conference on Computer and Communications Security, October 28-31, 2007, Alexandria, Virginia, USA. New York: ACM, 2007: 598-609. |
| [5] | JUELS A, KALISKI JR B S. PORs: Proofs of Retrievability for Large Files[C]//ACM. 14th ACM Conference on Computer and Communications Security, October 28-31, 2007, Alexandria, Virginia, USA. New York: ACM, 2007: 584-597. |
| [6] | SHACHAM H, WATERS B.Compact Proofs of Retrievability[J]. Journal of Cryptology, 2013, 26(3): 442-483. |
| [7] | WANG Qian, WANG Cong, REN Kui, et al.Enabling Public Auditability and Data Dynamics for Storage Security in Cloud Computing[J]. IEEE Transactions on Parallel and Distributed Systems, 2011, 22(5): 847-859. |
| [8] | WANG Cong, Chow S S M, Wang Qian, et al. Privacy-preserving Public Auditing for Secure Cloud Storage[J]. IEEE Transactions on Computers, 2013, 62(2): 362-275. |
| [9] | ZHAO Yang, REN Huaqiang, XIONG Hu, et al.Cloud Data Integrity Verification Scheme without Bilinear Pairing[J]. Netinfo Security, 2015, 15(7): 7-12. |
| 赵洋,任化强,熊虎,等. 无双线性对的云数据完整性验证方案[J]. 信息网络安全,2015,15(7):7-12. | |
| [10] | ZHANG Jianhong, LI Pengyan.An Efficient Data Integrity Verification Scheme for Cloud Storage[J]. Netinfo Security, 2017, 17(3): 1-5. |
| 张键红,李鹏燕. 一种有效的云存储数据完整性验证方案[J]. 信息网络安全,2017,17(3):1-5. | |
| [11] | WANG Yujue, WU Qianhong, QIN Bo, et al.Identity-based Data Outsourcing with Comprehensive Auditing in Clouds[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(4): 940-952. |
| [12] | WANG Huaqun, HE Debiao, TANG Shaohua.Identity-based Proxy-oriented Data Uploading and Remote Data Integrity Checking in Public Cloud[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(6): 1165-1176. |
| [13] | WANG Boyang, CHOW S S M, Li Ming, et al. Storing Shared Data on the Cloud via Security-mediator[C]//IEEE. 33rd International Conference on Distributed Computing Systems, July 8-11, 2013, Philadelphia, Pennsylvania, USA. New Jersey: IEEE, 2013: 124-133. |
| [14] | WANG Yujue, WU Qianhong, QIN Bo, et al.Ownership-hidden Group-oriented Proofs of Storage from Pre-homomorphic Signatures[J]. Peer-to-Peer Networking and Applications, 2018, 11(2): 235-251. |
| [15] | WANG Yujue, WU Qianhong, QIN Bo, et al.Online/Offline Provable Data Possession[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(5): 1182-1194. |
| [16] | WANG Yujue, WU Qianhong, WONG D S, et al.Securely Outsourcing Exponentiations with Single Untrusted Program for Cloud Storage[C]//Springer. 19th European Symposium on Research in Computer Security, September 7-11, 2014, Wroclaw, Poland. Heidelberg: Springer, 2014: 326-343. |
| [17] | YU Yong, AU M H A, MU Yi, et al. Enhanced Privacy of a Remote Data Integrity-checking Protocol for Secure Cloud Storage[J]. International Journal of Information Security, 2015, 14(4): 307-318. |
| [18] | YU Yong, AU M H A, ATENIESE G, et al. Identity-based Remote Data Integrity Checking with Perfect Data Privacy Preserving for Cloud Storage[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(4): 767-778. |
| [19] | CUI Hui, MU Yi, Au M H.Proof of Retrievability with Public Verifiability Resilient Against Related-key Attacks[J]. IET Information Security, 2015, 9(1): 43-49. |
| [20] | WANG Huaqun.Proxy Provable Data Possession in Public Clouds[J]. IEEE Transactions on Services Computing, 2013, 6(4): 551-559. |
| [21] | LU Xiuqing, XIAN Hequn.A Big Data Integrity Auditing Scheme Based on User Authorization in Cloud Storage[J]. Netinfo Security, 2018, 18(4): 32-37. |
| 鲁秀青,咸鹤群. 云存储中基于用户授权的大数据完整性审计方案[J]. 信息网络安全,2018,18(4):32-37. | |
| [22] | REN Yongjun, XU Jiang, WANG Jin, et al.Designated-verifier Provable Data Possession in Public Cloud Storage[J]. International Journal of Security and Its Applications, 2013, 7(6): 11-20. |
| [1] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [2] | 刘渊, 乔巍. 云环境下基于Kubernetes集群系统的容器网络研究与优化[J]. 信息网络安全, 2020, 20(3): 36-44. |
| [3] | 张建航, 曹泽阳, 宋晓峰, 徐庆征. 抗量子本原格上高效的身份基消息恢复签名方案[J]. 信息网络安全, 2020, 20(1): 26-32. |
| [4] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [5] | 李晓冉, 郝蓉, 于佳. 具有数据上传管控的无证书可证明数据持有方案[J]. 信息网络安全, 2020, 20(1): 83-88. |
| [6] | 任良钦, 王伟, 王琼霄, 鲁琳俪. 一种新型云密码计算平台架构及实现[J]. 信息网络安全, 2019, 19(9): 91-95. |
| [7] | 余奕, 吕良双, 李肖坚, 王天博. 面向移动云计算场景的动态网络拓扑描述语言[J]. 信息网络安全, 2019, 19(9): 120-124. |
| [8] | 王紫璇, 吕良双, 李肖坚, 王天博. 基于共享存储的OpenStack虚拟机应用分发策略[J]. 信息网络安全, 2019, 19(9): 125-129. |
| [9] | 张雪锋, 彭华. 一种基于SM9算法的盲签名方案研究[J]. 信息网络安全, 2019, 19(8): 61-67. |
| [10] | 崔艳鹏, 冯璐铭, 闫峥, 蔺华庆. 基于程序切片技术的云计算软件安全模型研究[J]. 信息网络安全, 2019, 19(7): 31-41. |
| [11] | 刘建华, 郑晓坤, 郑东, 敖章衡. 基于属性加密且支持密文检索的安全云存储系统[J]. 信息网络安全, 2019, 19(7): 50-58. |
| [12] | 侯林, 李明洁, 徐剑, 周福才. 基于变长认证跳表的分布式动态数据持有证明模型[J]. 信息网络安全, 2019, 19(7): 67-74. |
| [13] | 葛新瑞, 崔巍, 郝蓉, 于佳. 加密云数据上支持可验证的关键词排序搜索方案[J]. 信息网络安全, 2019, 19(7): 82-89. |
| [14] | 秦中元, 韩尹, 张群芳, 朱雪金. 一种改进的多私钥生成中心云存储访问控制方案[J]. 信息网络安全, 2019, 19(6): 11-18. |
| [15] | 邵必林, 李肖俊, 边根庆, 赵煜. 云存储数据完整性审计技术研究综述[J]. 信息网络安全, 2019, 19(6): 28-36. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||