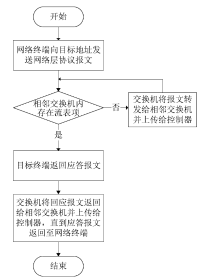
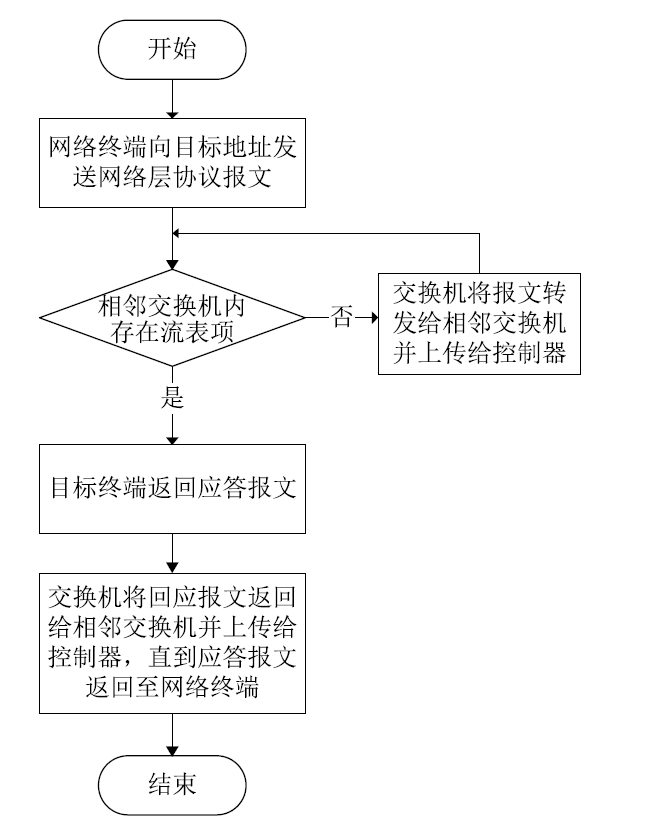
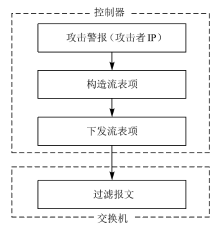
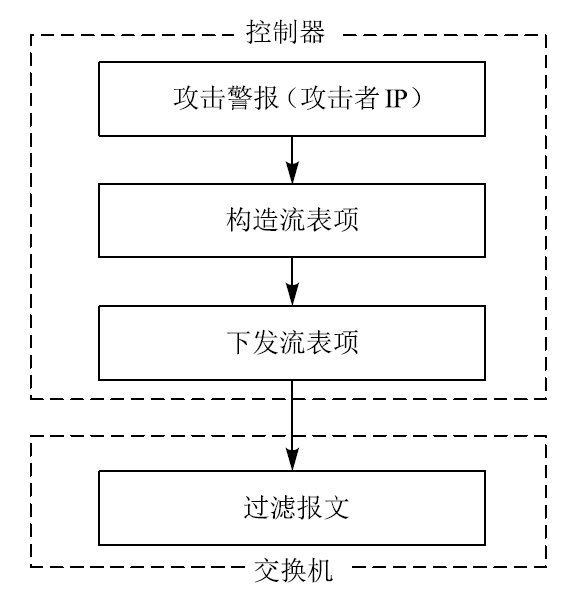
信息网络安全 ›› 2020, Vol. 20 ›› Issue (3): 9-17.doi: 10.3969/j.issn.1671-1122.2020.03.002
一种基于拓扑分析的网络攻击流量分流和阻断方法
宋宇波1,2,3( ), 樊明1,2,3, 杨俊杰1,2,3, 胡爱群1,2,3
), 樊明1,2,3, 杨俊杰1,2,3, 胡爱群1,2,3
- 1.东南大学网络空间安全学院,南京 211189
2.江苏省计算机网络技术重点实验室,南京 211189
3.网络通信与安全紫金山实验室,南京 211189
-
收稿日期:2019-11-20出版日期:2020-03-10发布日期:2020-05-11 -
作者简介:作者简介:宋宇波(1977—),男,江苏,副教授,博士,主要研究方向为网络流量安全分析;樊明(1995—),男,江苏,硕士研究生,主要研究方向为网络流量分析;杨俊杰(1996—),男,辽宁,硕士研究生,主要研究方向为无线设备指纹;胡爱群(1964—),男,江苏,教授,博士,主要研究方向为无线网络安全、无线指纹识别。
-
基金资助:国家自然科学基金[61601113];国家重点研发计划[2018YFB2202200,2018YFB2100403]
Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis
SONG Yubo1,2,3( ), FAN Ming1,2,3, YANG Junjie1,2,3, HU Aiqun1,2,3
), FAN Ming1,2,3, YANG Junjie1,2,3, HU Aiqun1,2,3
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Jiangsu Key Laboratory of Computer Networking Technology, Nanjing 211189, China
3. Network Communication and Security Purple Mountain Laboratory, Nanjing 211189, China
-
Received:2019-11-20Online:2020-03-10Published:2020-05-11
摘要:
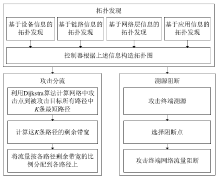
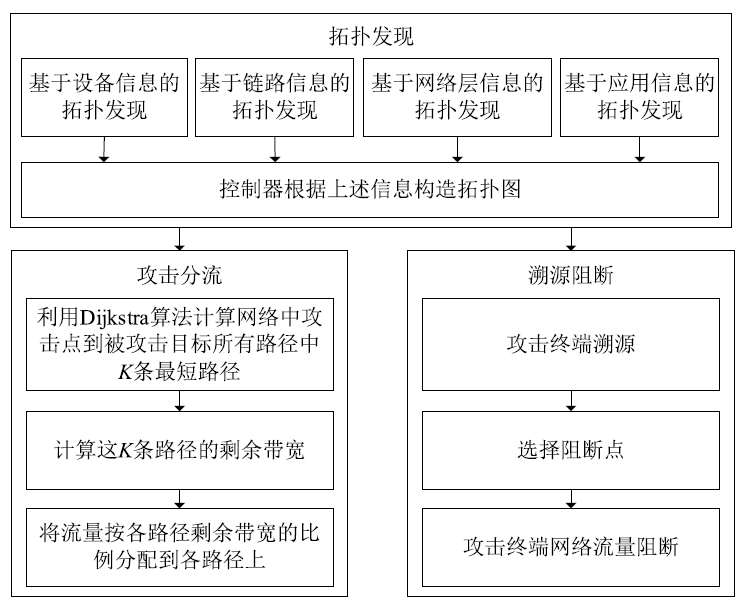
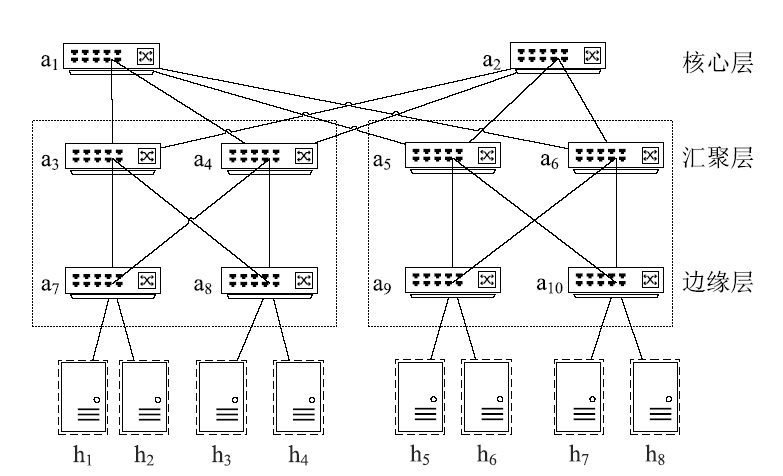
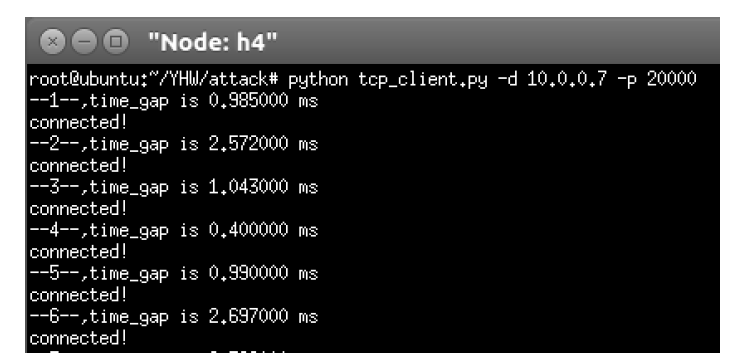
现有的针对流量型网络攻击的防御方法主要是在监测点发现异常后对流量进行阻断,仅能降低所在路径的攻击流量但无法降低整个网络的负载。针对这种情况,文章提出一种基于拓扑分析的网络攻击流量分流和阻断方法,基于拓扑分析从网络全局角度出发实现攻击流量分流阻断。该方法基于多种发现策略获取网络拓扑,在网络攻击阶段采用基于K条最短路径分流的方法实现网络流量分流;同时基于主机行为特征对网络攻击进行溯源,并采用基于流表的报文实时过滤方案进行阻断。实验结果表明,该方法具有系统开销小、鲁棒性好、阻断效率高的特点,实用价值较强。
中图分类号:
引用本文
宋宇波, 樊明, 杨俊杰, 胡爱群. 一种基于拓扑分析的网络攻击流量分流和阻断方法[J]. 信息网络安全, 2020, 20(3): 9-17.
SONG Yubo, FAN Ming, YANG Junjie, HU Aiqun. Multipath Solution and Blocking Method of Network Attack Traffic Based on Topology Analysis[J]. Netinfo Security, 2020, 20(3): 9-17.
| [1] | CNCERT. Internet Security Situation in China in the First Half of 2019[EB/OL]. , 2018-8-13. |
| 国家互联网应急中心. 2019 年上半年我国互联网网络安全态势[EB/OL]. , 2018-8-13. | |
| [2] | YAN Qiao, YU F R, GONG Qingxiang, et al.Software-defined Networking(SDN) and Distributed Denial of Service(DDoS) Attacks in cloud Computing Environments: A Survey, Some Research Issues, and Challenges[J]. IEEE Communications Surveys & Tutorials, 2015, 18(1): 602-622. |
| [3] | CUI Yunhe, YAN Lianshan, LI Saifei, et al. SD-Anti-DDoS: Fast and Efficient DDoS Defense in Software-defined Networks[EB/OL]. , 2019-9-11. |
| [4] | WANG Xiulei, CHEN Ming, XING Changyou.SDSNM: a Software-defined Security Networking Mechanism to Defend Against DDoS Attacks[C]//IEEE. 9th International Conference on Frontier of Computer Science and Technology, August 26-28, 2015, Dalian, China. New Jersey: IEEE, 2015: 115-121. |
| [5] | BURAGOHAIN C, MEDHI N.FlowTrApp: An SDN Based Architecture for DDoS Attack Detection and Mitigation in Data Centers[C]//IEEE. 3rd International Conference on Signal Processing and Integrated Networks, February 11-12, 2016, Noida, India. New Jersey: IEEE, 2016: 519-524. |
| [6] | SARWAR M A, HUSSAIN M, ANWAR M U, et al. FlowJustifier: An Optimized Trust-based Request Prioritization Approach for Mitigation of SDN Controller DDoS Attacks in the IoT Paradigm[EB/OL]. , 2019-9-10. |
| [7] | RAHMAN O, QURAISHI M A G, LUNG C H. DDoS Attacks Detection and Mitigation in SDN Using Machine Learning[EB/OL]. , 2019-9-10. |
| [8] | SAHAY R, BLANC G, ZHANG Zonghua, et al. Towards Autonomic DDoS Mitigation Using Software Defined Networking[EB/OL]. , 2019-9-10. |
| [9] | VON AHN L, BLUM M, HOPPER N J, et al.CAPTCHA: Using Hard AI Problems for Security[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 4-8, Warsaw, Poland. Heidelberg: Springer, 2003: 294-311. |
| [10] | CHUNG C J, KHATKAR P, XING Tianyi, et al.NICE: Network Intrusion Detection and Countermeasure Selection in Virtual Network Systems[J]. IEEE Transactions on Dependable and Secure Computing, 2013, 10(4): 198-211. |
| [11] | XING Tianyi, HUANG Dijiang, XU Le, et al.Snortflow: A Openflow-based Intrusion Prevention System in Cloud Environment[C]//IEEE. 2nd GENI Research and Educational Experiment Workshop, March 20-22, 2013, Salt Lake City, UT, USA. New Jersey: IEEE, 2013: 89-92. |
| [12] | CONTI M, GANGWAL A, GAUR M S.A Comprehensive and Effective Mechanism for DDoS Detection in SDN[C]//IEEE. 13th International Conference on Wireless and Mobile Computing, Networking and Communications, October 9-11, 2017, Rome, Italy. New Jersey: IEEE, 2017: 1-8. |
| [13] | DA SILVA A S, WICKBOLDT J A, GRANVILLE L Z, et al. ATLANTIC: A Framework for Anomaly Traffic Detection, Classification, and Mitigation in SDN[C]//IEEE. NOMS 2016-2016 IEEE/IFIP Network Operations and Management Symposium, April 25-29, 2016, Istanbul, Turkey. New Jersey: IEEE, 2016: 27-35. |
| [14] | BARKI L, SHIDLING A, METI N, et al.Detection of Distributed Denial of Service Attacks in Software Defined Networks[C]//IEEE. 2016 International Conference on Advances in Computing, Communications and Informatics, September 21-24, 2016, Jaipur, India. New Jersey: IEEE, 2016: 2576-2581. |
| [15] | ABUBAKAR A, PRANGGONO B.Machine Learning Based Intrusion Detection System for Software Defined Networks[C]//IEEE. 7th International Conference on Emerging Security Technologies, September 6-8, 2017, Canterbury, UK. New Jersey: IEEE, 2017: 138-143. |
| [16] | BRAGA R, MOTA E, PASSITO A.Lightweight DDoS Flooding Attack Detection Using NOX/OpenFlow[C]//IEEE. IEEE Local Computer Network Conference, October 10-14, 2010, Denver, CO, USA. New Jersey: IEEE, 2010: 408-415. |
| [1] | 周枝凝, 王斌君, 翟一鸣, 仝鑫. 基于ALBERT动态词向量的垃圾邮件过滤模型[J]. 信息网络安全, 2020, 20(9): 107-111. |
| [2] | 沈金伟, 赵一, 梁春林, 张萍. 基于循环分组的RFID群组标签所有权转移协议[J]. 信息网络安全, 2020, 20(9): 102-106. |
| [3] | 夏天雨, 顾益军. 一种基于改进DynamicTriad模型的动态链路预测方法[J]. 信息网络安全, 2020, 20(9): 97-101. |
| [4] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [5] | 李世斌, 李婧, 唐刚, 李艺. 基于HMM的工业控制系统网络安全状态预测与风险评估方法[J]. 信息网络安全, 2020, 20(9): 57-61. |
| [6] | 徐瑜, 周游, 林璐, 张聪. 无监督机器学习在游戏反欺诈领域的应用研究[J]. 信息网络安全, 2020, 20(9): 32-36. |
| [7] | 毋泽南, 田立勤, 陈楠. 基于随机Petri网的系统安全性量化分析研究[J]. 信息网络安全, 2020, 20(9): 27-31. |
| [8] | 仝鑫, 王罗娜, 王润正, 王靖亚. 面向中文文本分类的词级对抗样本生成方法[J]. 信息网络安全, 2020, 20(9): 12-16. |
| [9] | 吴警, 芦天亮, 杜彦辉. 基于Char-RNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2020, 20(9): 6-11. |
| [10] | 余小军, 吴亚飚, 张玉清. 云安全体系结构设计研究[J]. 信息网络安全, 2020, 20(9): 62-66. |
| [11] | 刘文懋, 尤扬. 5G新型基础设施的安全防护思路和技术转换[J]. 信息网络安全, 2020, 20(9): 67-71. |
| [12] | 毕亲波, 赵呈东. 基于STRIDE-LM的5G网络安全威胁建模研究与应用[J]. 信息网络安全, 2020, 20(9): 72-76. |
| [13] | 余果, 王冲华, 陈雪鸿, 李俊. 认证视角下的工业互联网标识解析安全[J]. 信息网络安全, 2020, 20(9): 77-81. |
| [14] | 刘红, 谢永恒, 王国威, 蒋帅. 基于跨领域本体的信息安全分析[J]. 信息网络安全, 2020, 20(9): 82-86. |
| [15] | 王文华, 郝新, 刘焱, 王洋. AI系统的安全测评和防御加固方案[J]. 信息网络安全, 2020, 20(9): 87-91. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||