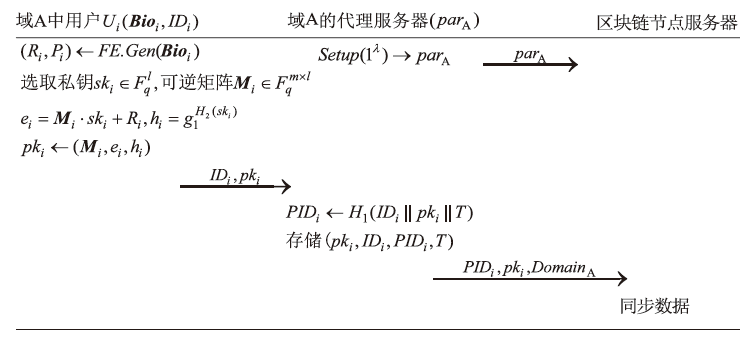
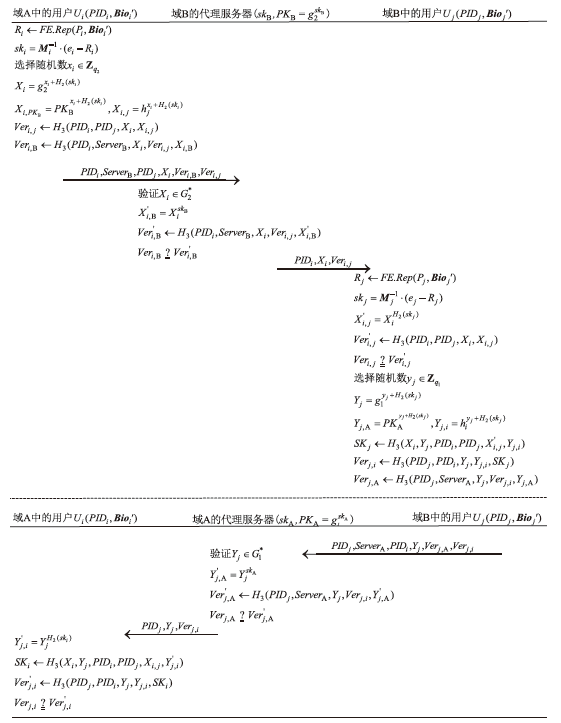
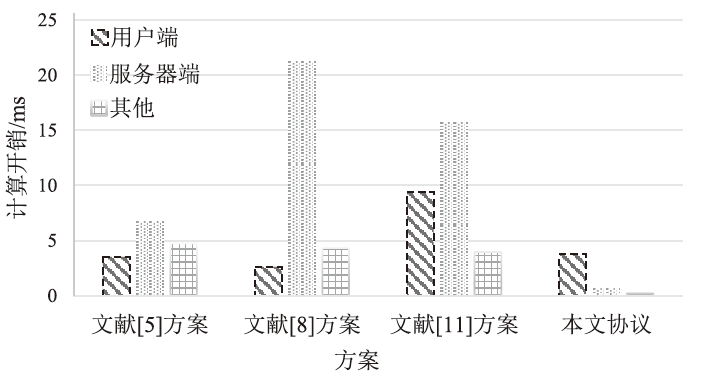
信息网络安全 ›› 2025, Vol. 25 ›› Issue (12): 1948-1960.doi: 10.3969/j.issn.1671-1122.2025.12.010
基于区块链的隐私保护跨域认证协议
- 信息工程大学网络空间安全学院,郑州 450001
-
收稿日期:2025-02-10出版日期:2025-12-10发布日期:2026-01-06 -
通讯作者:顾纯祥 E-mail:gcxiang5209@126.com -
作者简介:张观平(2000—),男,江西,硕士研究生,主要研究方向为密码协议分析|魏福山(1983—),男,甘肃,副教授,博士,主要研究方向为安全协议、无线网络的安全认证|陈熹(1988—),男,湖北,讲师,硕士,主要研究方向为密码学、网络安全协议分析|顾纯祥(1976—),男,安徽,教授,博士,主要研究方向为密码协议的安全性分析 -
基金资助:国家重点研发计划(2023YFA1009500);国家自然科学基金(61772548);河南省优秀青年科学基金(222300420099)
Blockchain-Based Privacy-Preserving Cross-Domain Authentication Protocol
ZHANG Guanping, WEI Fushan, CHEN Xi, GU Chunxiang( )
)
- Institute of Cyberspace Security, Information Engineering University, Zhengzhou 450001, China
-
Received:2025-02-10Online:2025-12-10Published:2026-01-06 -
Contact:GU Chunxiang E-mail:gcxiang5209@126.com
摘要:
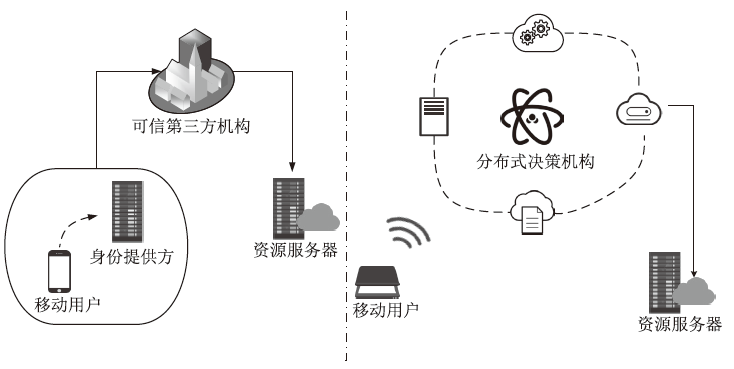
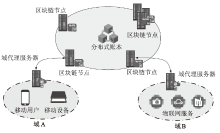
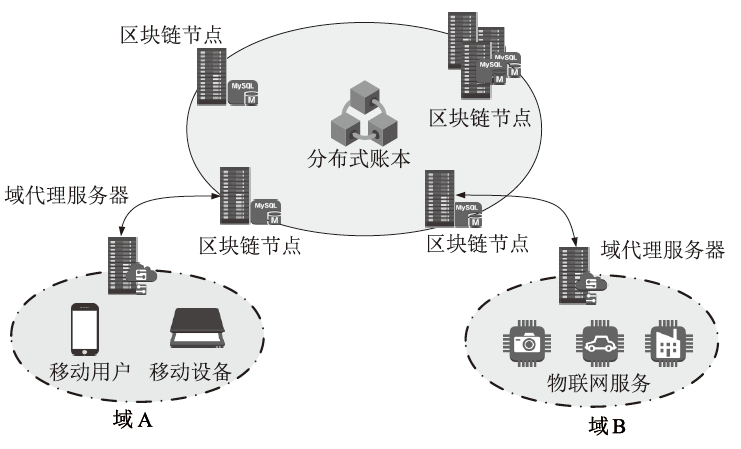
在物联网环境下,跨域认证面临隐私保护不足和依赖可信第三方等问题。为应对这些挑战,文章提出基于区块链的隐私保护跨域认证协议。在区块链技术的支持下,该协议实现了不同参数域实体之间的身份认证与密钥交换,同时有效减轻了服务器和用户端的性能负担。具体而言,用户的生物特征向量经过模糊提取器生成秘密值,结合格加密技术计算密钥,从而在保护用户生物特征隐私的同时完成隐式身份认证。此外,用户在跨域访问过程中生成的伪身份、公钥及各信任域的公共参数被上传至区块链,以确保协议参与方验证结果的正确性和行为的不可抵赖性。在随机预言模型下,基于判定性Learning with Error困难问题和离散对数难题,证明了该协议能够抵抗多项式敌手攻击。与同类协议相比,文章所提协议能够较好地兼容现有安全机制,并具有较低的计算与通信开销,从而为跨域认证提供一种高效且安全的解决方案。
中图分类号:
引用本文
张观平, 魏福山, 陈熹, 顾纯祥. 基于区块链的隐私保护跨域认证协议[J]. 信息网络安全, 2025, 25(12): 1948-1960.
ZHANG Guanping, WEI Fushan, CHEN Xi, GU Chunxiang. Blockchain-Based Privacy-Preserving Cross-Domain Authentication Protocol[J]. Netinfo Security, 2025, 25(12): 1948-1960.
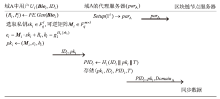
表1
域A的参数设置
| 参数符号 | 说明 |
|---|---|
| 生物特征向量分量取值参数 | |
| 安全参数所生成的大素数 | |
| 阶为 | |
| 群 | |
| 模糊提取器输出秘密值的向量维数 | |
| 选取的随机向量维数 | |
| 哈希函数 | |
| 哈希函数 | |
| 哈希函数 | |
| 长期公钥 |
| [1] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Advances in Cryptology-CRYPTO 1984. Heidelberg:Springer, 1984: 47-53. |
| [2] | BONEH D, FRANKLIN M. Identity-Based Encryption from the Weil Pairing[C]// Springer. Advances in Cryptology-CRYPTO 2001. Heidelberg: Springer, 2001: 213-229. |
| [3] | HORWITZ J, LYNN B. Toward Hierarchical Identity-Based Encryption[C]// Springer. Advances in Cryptology-EUROCRYPT 2002. Heidelberg: Springer, 2002: 466-481. |
| [4] | AL-RIYAMI S S, PATERSON K G. Certificateless Public Key Cryptography[C]// Springer. Advances in Cryptology -ASIACRYPT 2003. Heidelberg: Springer, 2003: 452-473. |
| [5] |
SHEN Meng, LIU Huisen, ZHU Liehuang, et al. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT[J]. IEEE Journal on Selected Areas in Communications, 2020, 38(5): 942-954.
doi: 10.1109/JSAC.49 URL |
| [6] |
CHEN Jing, ZHAN Zeyi, HE Kun, et al. XAuth: Efficient Privacy-Preserving Cross-Domain Authentication[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 19(5): 3301-3311.
doi: 10.1109/TDSC.2021.3092375 URL |
| [7] |
WANG Linjie, TIAN Youliang, ZHANG Duo. Toward Cross-Domain Dynamic Accumulator Authentication Based on Blockchain in Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2022, 18(4): 2858-2867.
doi: 10.1109/TII.2021.3116049 URL |
| [8] |
TONG Fei, CHEN Xing, WANG Kaiming, et al. CCAP: A Complete Cross-Domain Authentication Based on Blockchain for Internet of Things[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 3789-3800.
doi: 10.1109/TIFS.2022.3214733 URL |
| [9] |
CUI Jie, LIU Nan, ZHANG Qingyang, et al. Efficient and Anonymous Cross-Domain Authentication for IIoT Based on Blockchain[J]. IEEE Transactions on Network Science and Engineering, 2022, 10(2): 899-910.
doi: 10.1109/TNSE.2022.3224453 URL |
| [10] |
LIU Yizhong, LIU Andi, XIA Yu, et al. A Blockchain-Based Cross-Domain Authentication Management System for IoT Devices[J]. IEEE Transactions on Network Science and Engineering, 2023, 11(1): 115-127.
doi: 10.1109/TNSE.2023.3292624 URL |
| [11] |
WANG Fengqun, CUI Jie, ZHANG Qingyang, et al. Blockchain-Based Lightweight Message Authentication for Edge-Assisted Cross-Domain Industrial Internet of Things[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 21(4): 1587-1604.
doi: 10.1109/TDSC.2023.3285800 URL |
| [12] |
SU Yuan, WANG Yuheng, LI Jiliang, et al. Oracle Based Privacy-Preserving Cross-Domain Authentication Scheme[J]. IEEE Transactions on Sustainable Computing, 2024, 9(4): 602-614.
doi: 10.1109/TSUSC.2024.3350343 URL |
| [13] | WANG Mei, HE Kun, CHEN Jing, et al. Biometrics-Authenticated Key Exchange for Secure Messaging[C]// ACM. 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 2618-2631. |
| [14] |
WU Yongdong, WENG Jian, WANG Zhengxia, et al. Attacks and Countermeasures on Privacy-Preserving Biometric Authentication Schemes[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(2): 1744-1755.
doi: 10.1109/TDSC.2022.3162623 URL |
| [15] | NANDAKUMAR K, JAIN A K. Biometric Template Protection: Bridging the Performance Gap between Theory and Practice[J]. IEEE Signal Processing Magazine, 2015, 32(5): 88-100. |
| [16] |
DAUGMAN J. Information Theory and the IrisCode[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(2): 400-409.
doi: 10.1109/TIFS.2015.2500196 URL |
| [17] | REGEV O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography[J]. Journal of the ACM, 2009, 56(6): 1-40. |
| [18] |
ALBRECHT M R, PLAYER R, SCOTT S. On the Concrete Hardness of Learning with Errors[J]. Journal of Mathematical Cryptology, 2015, 9(3): 169-203.
doi: 10.1515/jmc-2015-0016 URL |
| [19] |
BABAI L. On Lovasz Lattice Reduction and the Nearest Lattice Point Problem[J]. Combinatorica, 1986, 6(1): 1-13.
doi: 10.1007/BF02579403 URL |
| [20] | AGGARWAL D, DADUSH D, STEPHENS-DAVIDOWITZ N. Solving the Closest Vector Problem in 2n Time: The Discrete Gaussian Strikes Again![C]// IEEE. 2015 IEEE 56th Annual Symposium on Foundations of Computer Science. New York: IEEE, 2015: 563-582. |
| [21] |
DODIS Y, OSTROVSKY R, REYZIN L, et al. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data[J]. SIAM Journal on Computing, 2008, 38(1): 97-139.
doi: 10.1137/060651380 URL |
| [22] |
DAUGMAN J G. High Confidence Visual Recognition of Persons by a Test of Statistical Independence[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 1993, 15(11): 1148-1161.
doi: 10.1109/34.244676 URL |
| [23] | ABDALLA M, FOUQUE P A, POINTCHEVAL D. Password-Based Authenticated Key Exchange in The Three-Party Setting[C]// Springer. Public Key Cryptography-PKC 2005: The 8th International Workshop on Theory and Practice in Public Key Cryptography. Heidelberg: Springer, 2005: 65-84. |
| [24] | WEI Xin, WANG Xinyan, YU Zhuo, et al. Cross Domain Authentication for IoT Based on Consortium Blockchain[J]. Journal of Software, 2021, 32(8): 2613-2628. |
| 魏欣, 王心妍, 于卓, 等. 基于联盟链的物联网跨域认证[J]. 软件学报, 2021, 32(8): 2613-2628. | |
| [25] | WEI Songjie, LI Shasha, WANG Jiahe. A Cross-Domain Authentication Protocol by Identity-Based Cryptography on Consortium Blockchain[J]. Chinese Journal of Computers, 2021, 44(5): 908-920. |
| 魏松杰, 李莎莎, 王佳贺. 基于身份密码系统和区块链的跨域认证协议[J]. 计算机学报, 2021, 44(5): 908-920. |
| [1] | 杨建新, 汪晓丁, 林晖. 基于HotStuff和多叉树的改进共识算法[J]. 信息网络安全, 2025, 25(9): 1447-1455. |
| [2] | 佘维, 马天祥, 冯海格, 刘炜. 基于RBF机制的无痕区块链隐蔽通信方案[J]. 信息网络安全, 2025, 25(8): 1302-1312. |
| [3] | 刘峰, 黄灏. 一种基于智能合约预言机技术的主动式去中心化监管传感网络架构[J]. 信息网络安全, 2025, 25(6): 898-909. |
| [4] | 朱率率, 刘科乾. 基于掩码的选择性联邦蒸馏方案[J]. 信息网络安全, 2025, 25(6): 920-932. |
| [5] | 赵锋, 范淞, 赵艳琦, 陈谦. 基于本地差分隐私的可穿戴医疗设备流数据隐私保护方法[J]. 信息网络安全, 2025, 25(5): 700-712. |
| [6] | 叶佳骏, 高翠凤, 薛吟兴. 基于静态分析的价格预言机操纵源代码检测方法研究[J]. 信息网络安全, 2025, 25(5): 732-746. |
| [7] | 秦金磊, 康毅敏, 李整. 智能电网中轻量级细粒度的多维多子集隐私保护数据聚合[J]. 信息网络安全, 2025, 25(5): 747-757. |
| [8] | 朱晓强, 张皓文, 林彦孜, 刘吉强. 基于可信数字身份的轻量级分布式认证方案[J]. 信息网络安全, 2025, 25(5): 817-827. |
| [9] | 胡宇涵, 杨高, 蔡红叶, 付俊松. 三维分布式无线智能系统数据传输路径隐私保护方案[J]. 信息网络安全, 2025, 25(4): 536-549. |
| [10] | 何可, 王建华, 于丹, 陈永乐. 基于自适应采样的机器遗忘方法[J]. 信息网络安全, 2025, 25(4): 630-639. |
| [11] | 杨亚涛, 丁渝诚, 刘培鹤, 桑鹏. 基于区块链的隐私保护和数字认证研究[J]. 信息网络安全, 2025, 25(4): 640-653. |
| [12] | 张雨轩, 黄诚, 柳蓉, 冷涛. 结合提示词微调的智能合约漏洞检测方法[J]. 信息网络安全, 2025, 25(4): 664-673. |
| [13] | 李佳东, 曾海涛, 彭莉, 汪晓丁. 一种保护数据隐私的匿名路由联邦学习框架[J]. 信息网络安全, 2025, 25(3): 494-503. |
| [14] | 王后珍, 江皓朗, 刘继辰, 涂航. 基于Paillier同态加密的隐私保护排序方案[J]. 信息网络安全, 2025, 25(12): 1975-1989. |
| [15] | 关志, 胡建斌, 李悦, 陈钟. 基于可信执行环境的区块链技术与应用综述[J]. 信息网络安全, 2025, 25(11): 1673-1690. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||