信息网络安全 ›› 2025, Vol. 25 ›› Issue (3): 494-503.doi: 10.3969/j.issn.1671-1122.2025.03.011
一种保护数据隐私的匿名路由联邦学习框架
- 福建师范大学计算机与网络空间安全学院,福州 350117
-
收稿日期:2024-06-11出版日期:2025-03-10发布日期:2025-03-26 -
通讯作者:汪晓丁 E-mail:wangdin1982@fjnu.edu.cn -
作者简介:李佳东(2001—),男,福建,硕士研究生,CCF会员,主要研究方向为联邦学习、数据安全|曾海涛(2001—),男,福建,硕士研究生,主要研究方向为人工智能、区块链|彭莉(2001—),女,江西,硕士研究生,主要研究方向为目标检测模型优化|汪晓丁(1982—),男,福建,副教授,博士,CCF会员,主要研究方向为网络优化、无线通信网络 -
基金资助:国家自然科学基金(U1905211)
An Anonymous Routing Federated Learning Framework for Data Privacy Protection
LI Jiadong, ZENG Haitao, PENG Li, WANG Xiaoding( )
)
- College of Computer and Cyber Security, Fujian Normal University, Fuzhou 350117, China
-
Received:2024-06-11Online:2025-03-10Published:2025-03-26 -
Contact:WANG Xiaoding E-mail:wangdin1982@fjnu.edu.cn
摘要:
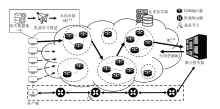
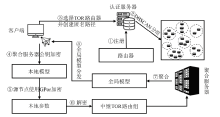
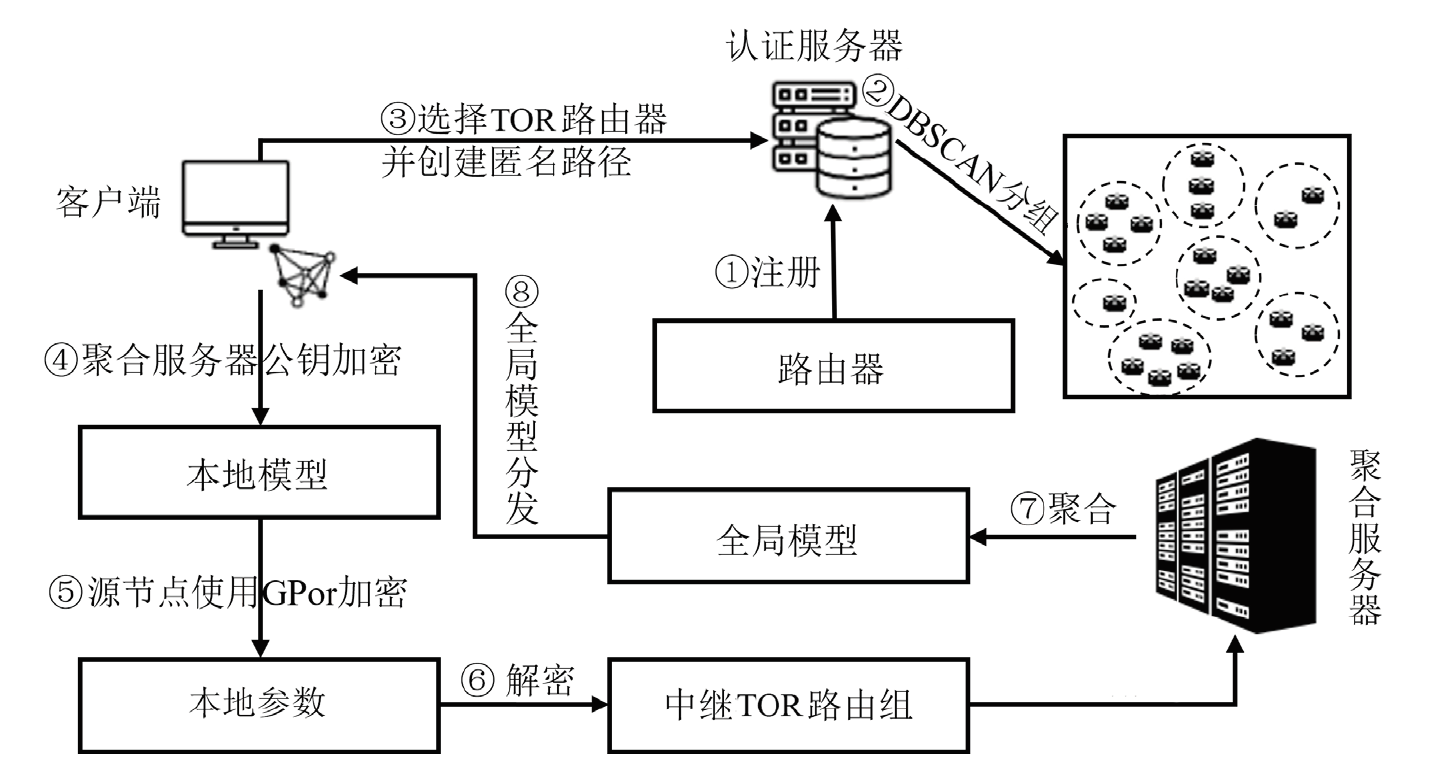
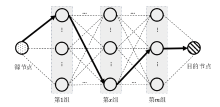
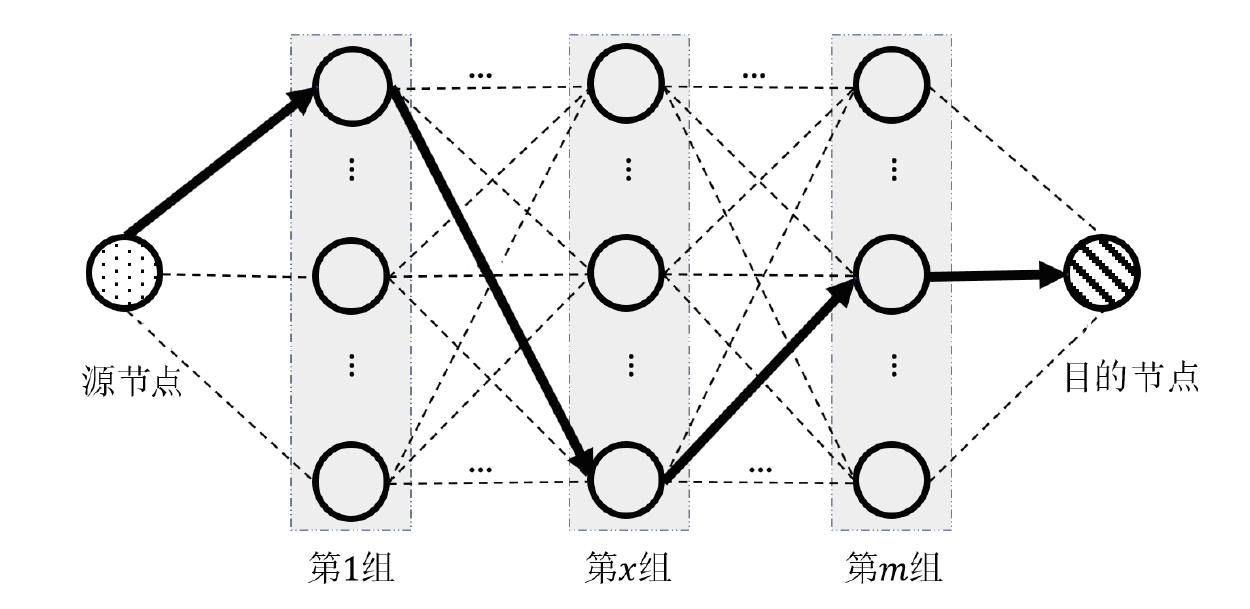
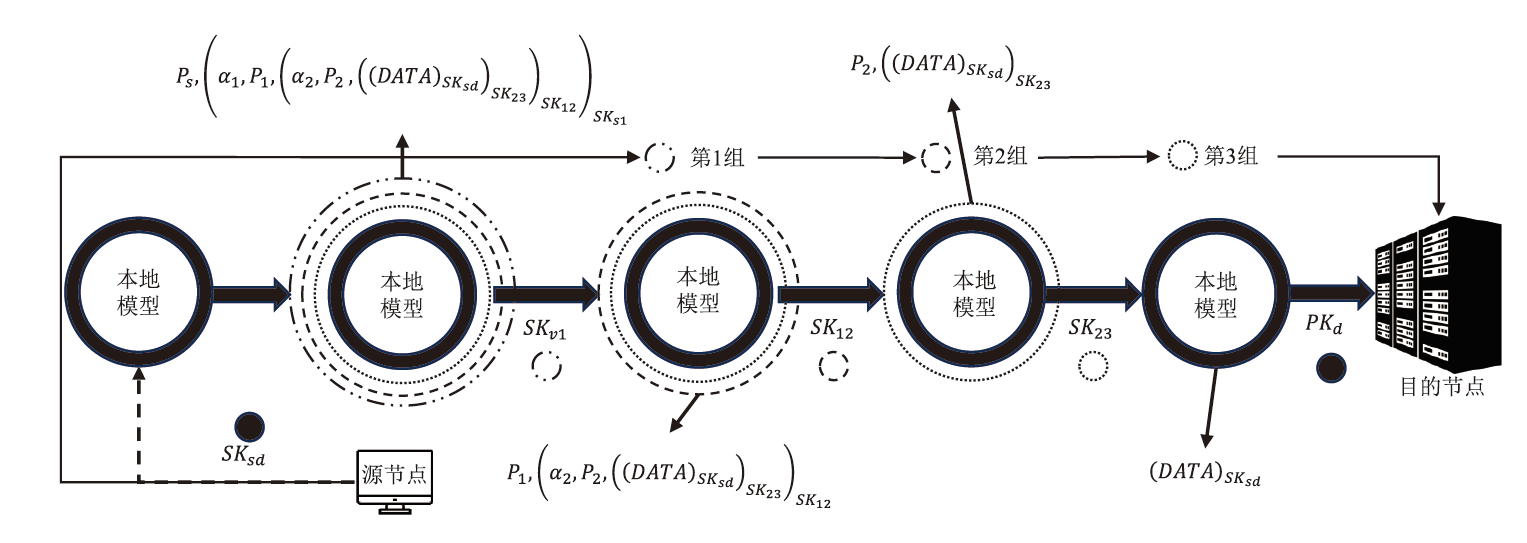
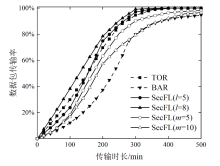
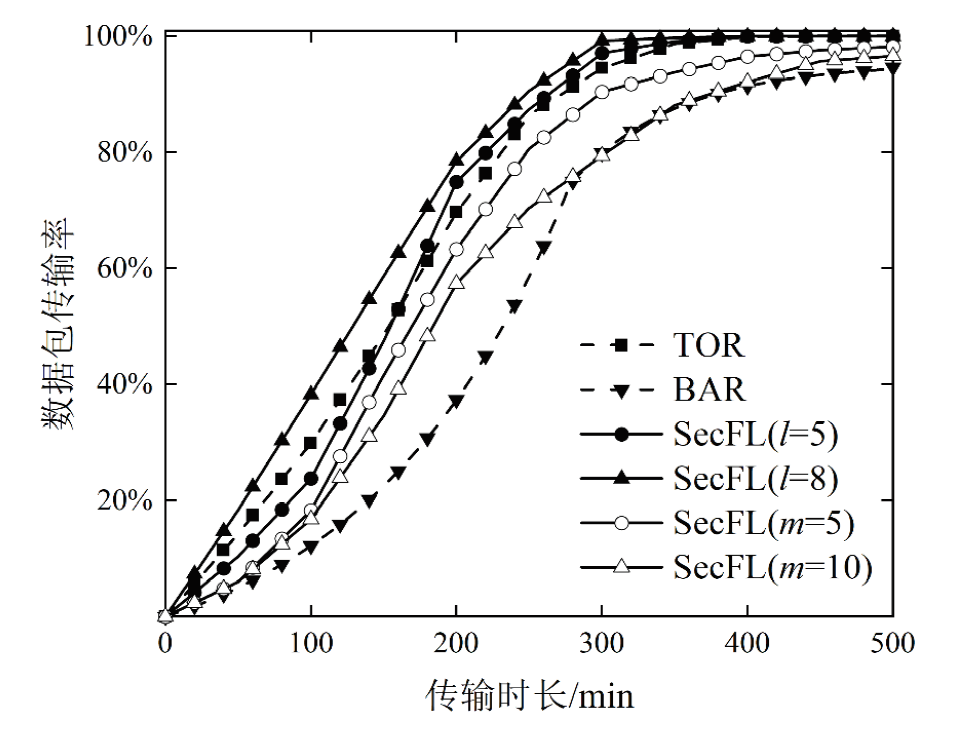
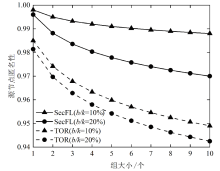
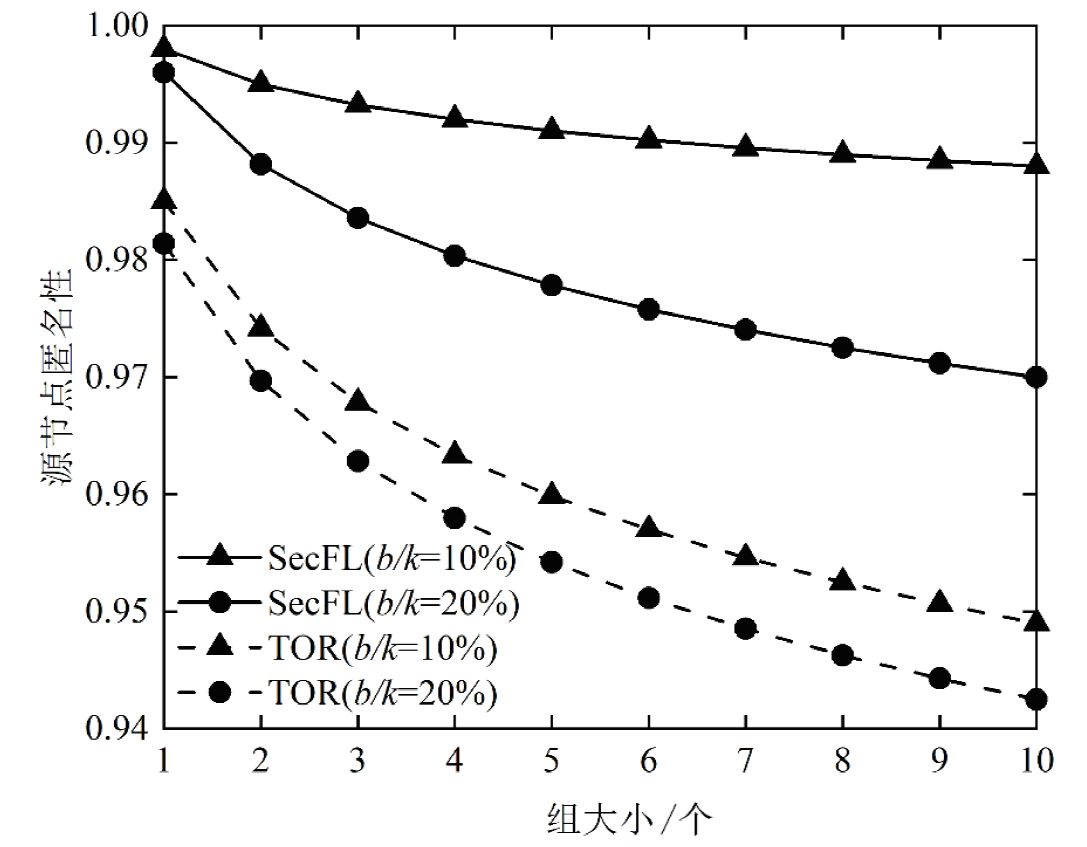
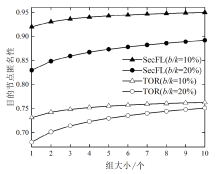
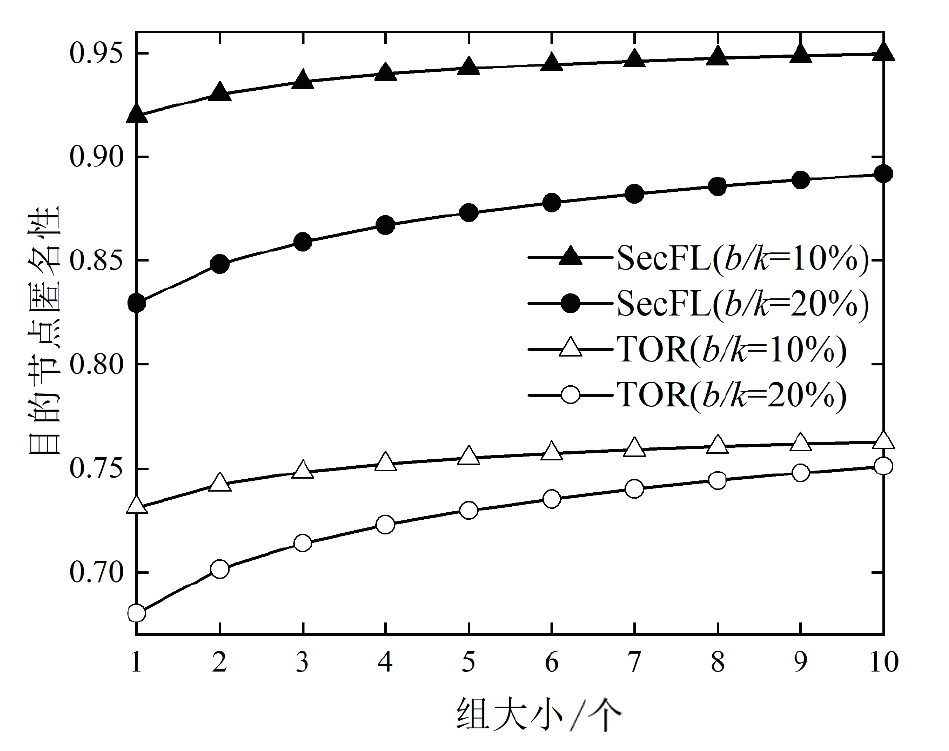
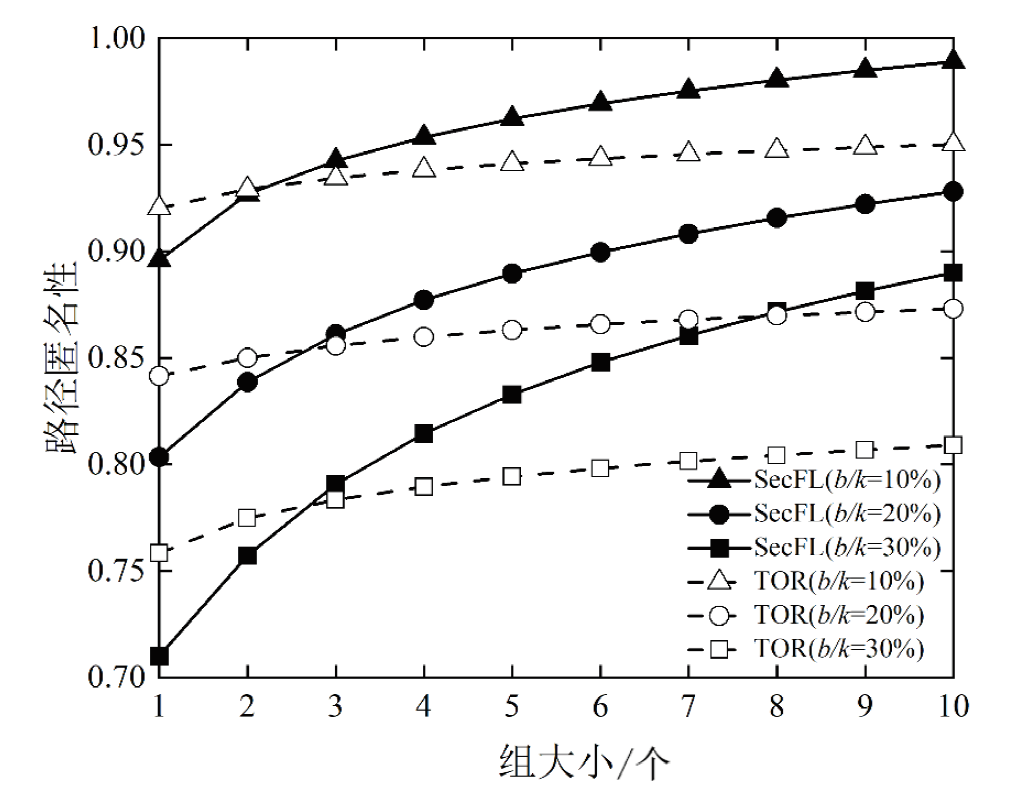
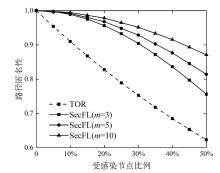
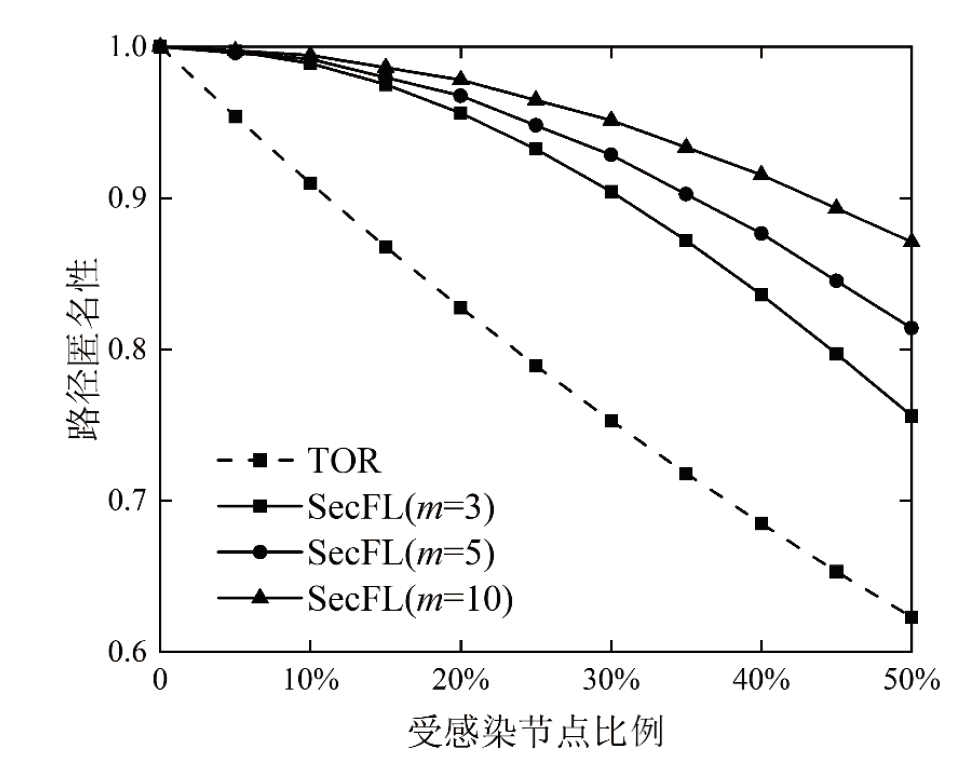
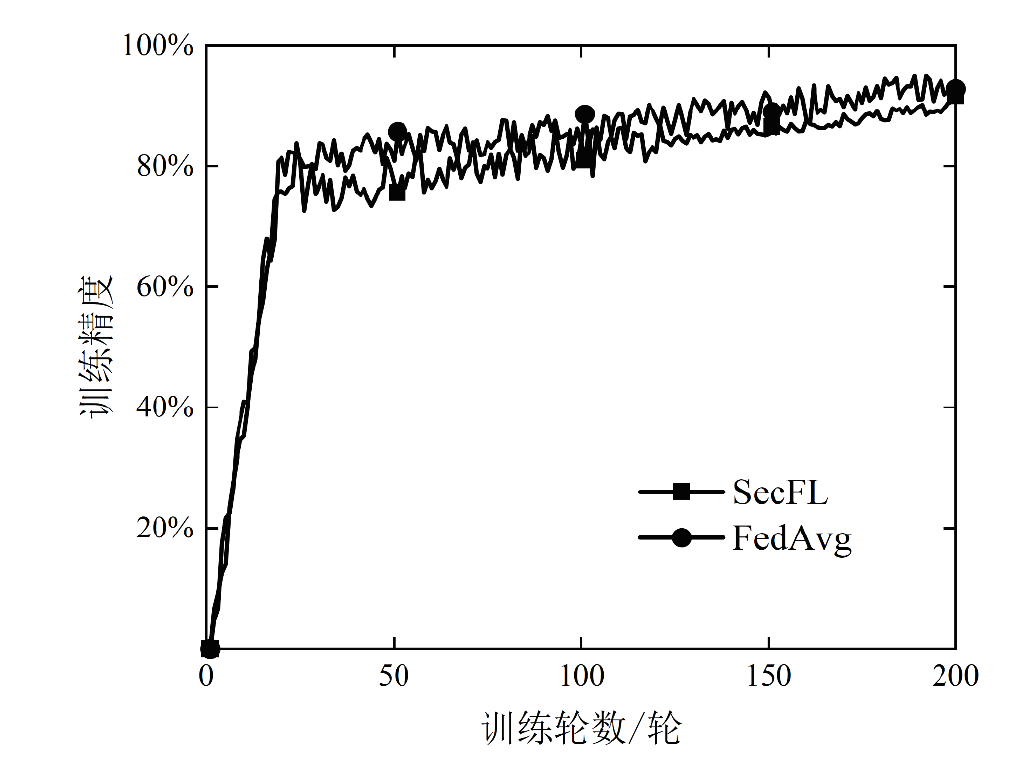
联邦学习作为一种分布式机器学习框架,能够在不共享训练数据的前提下,实现多方参与者协同训练全局模型,从而有效确保客户端数据隐私安全。然而,联邦学习仍面临模型参数泄露风险和通信过程中的身份隐私威胁。针对上述问题,文章提出一种保护数据隐私的匿名路由联邦学习框架(SecFL),旨在确保联邦学习模型中的参数安全与可信传输。SecFL设计了一种组配对洋葱路由协议,基于配对的密码学对数据进行分层加密,并引入“组”的概念,使组内所有节点能够解密相应层,从而在保证消息机密性和安全性的同时提升系统匿名性。实验结果表明,SecFL在匿名路由性能与安全防护效果方面均显著优于传统方案。相较于洋葱路由和广播匿名路由,SecFL在更短时间内使消息传递率达到100%,源节点和目的节点的匿名性分别提升了3.9%和1.9%。在50%节点遭受攻击的情况下,路径匿名性指标最多提升了24.8%。此外,SecFL框架在联邦学习中的收敛性能也较好。
中图分类号:
引用本文
李佳东, 曾海涛, 彭莉, 汪晓丁. 一种保护数据隐私的匿名路由联邦学习框架[J]. 信息网络安全, 2025, 25(3): 494-503.
LI Jiadong, ZENG Haitao, PENG Li, WANG Xiaoding. An Anonymous Routing Federated Learning Framework for Data Privacy Protection[J]. Netinfo Security, 2025, 25(3): 494-503.
使用本文
| [1] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2016-02-17)[2024-05-16]. https://arxiv.org/abs/1602.05629v4. |
| [2] | BONAWITZ K, EICHNER H, GRIESKAMP W, et al. Towards Federated Learning at Scale: System Design[J]. (2019-03-22)[2024-05-16]. https://doi.org/10.48550/arXiv.1902.01046. |
| [3] |
LI Tian, SAHU A K, TALWALKAR A, et al. Federated Learning: Challenges, Methods, and Future Directions[J]. IEEE Signal Processing Magazine, 2020, 37(3): 50-60.
doi: 10.1109/MSP.2020.2975749 |
| [4] |
WANG Teng, HUO Zheng, HUANG Yaxin, et al. Review on Privacy-Preserving Technologies in Federated Learning[J]. Journal of Computer Applications, 2023, 43(2): 437-449.
doi: 10.11772/j.issn.1001-9081.2021122072 |
|
王腾, 霍峥, 黄亚鑫, 等. 联邦学习中的隐私保护技术研究综述[J]. 计算机应用, 2023, 43(2): 437-449.
doi: 10.11772/j.issn.1001-9081.2021122072 |
|
| [5] | MELIS L, SONG Congzheng, DE C E, et al. Exploiting Unintended Feature Leakage in Collaborative Learning[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 691-706. |
| [6] | LAI Chengzhe, ZHAO Yining, ZHENG Dong. A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption[J]. Netinfo Security, 2024, 24(1): 93-105. |
| 赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105. | |
| [7] | SINGH P, SINGH M K, SINGH R, et al. Federated Learning:Challenges, Methods, and Future Directions[M]. Heidelberg: Springer, 2022. |
| [8] | ZHU Ligeng, LIU Zhijian, HAN Song. Deep Leakage from Gradients[J]. Neural Information Processing Systems, 2019(1323): 14774-14784. |
| [9] | WAINAKH A, VENTOLA F, MÜßIG T, et al. User-Level Label Leakage from Gradients in Federated Learning[EB/OL]. (2021-05-19)[2024-05-16]. https://doi.org/10.48550/arXiv.2105.09369. |
| [10] | ZHANG Xinwei, CHEN Xiangyi, HONG Mingyi, et al. Understanding Clipping for Federated Learning: Convergence and Client-Level Differential Privacy[EB/OL]. (2021-06-25)[2024-05-16]. https://doi.org/10.48550/arXiv.2106.13673. |
| [11] | BONAWITZ K, IVANOV V, KREUTER B, et al. Practical Secure Aggregation for Privacy-Preserving Machine Learning[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1175-1191. |
| [12] | SAV S, PYRGELIS A, TRONCOSO-PASTORIZA J R, et al. POSEIDON: Privacy-Preserving Federated Neural Network Learning[EB/OL]. (2021-01-08)[2024-05-16]. https://arxiv.org/abs/2009.00349v3. |
| [13] | DINGLEDINE R, MATHEWSON N, SYVERSON P F. Tor: The Second-Generation Onion Router[EB/OL]. (2004-08-09)[2024-05-16]. https://www.usenix.org/conference/13th-usenix-security-symposium/tor-second-generation-onion-router. |
| [14] | LAI R W F, CHEUNG H K F, CHOW S S M, et al. Another Look at Anonymous Communication[J]. IEEE Transactions on Dependable and Secure Computing, 2017, 16(5): 731-742. |
| [15] | VAKDE G, BIBIKAR R, LE Zhengyi, et al. EnPassant: Anonymous Routing for Disruption-Tolerant Networks with Applications in Assistive Environments[J]. Security and Communication Networks, 2011, 4(11): 1243-1256. |
| [16] | SHI Cong, LUO Xiapu, TRAYNOR P, et al. ARDEN: Anonymous Networking in Delay Tolerant Networks[J]. Ad Hoc Networks, 2012, 10(6): 918-930. |
| [17] | CAMENISCH J, HOHENBERGER S, KOHLWEISS M, et al. How to Win the Clonewars: Efficient Periodic N-Times Anonymous Authentication[C]// ACM. Proceedings of the 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 201-210. |
| [18] |
LI Yijing, TAO Xiaofeng, ZHANG Xuefei, et al. Privacy-Preserved Federated Learning for Autonomous Driving[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(7): 8423-8434.
doi: 10.1109/TITS.2021.3081560 |
| [19] | DOMINGO-FERRER J, BLANCO-JUSTICIA A, MANJÓN J, et al. Secure and Privacy-Preserving Federated Learning via Co-Utility[J]. IEEE Internet of Things Journal, 2022, 9(5): 3988-4000. |
| [20] | CATALANO D, FIORE D, GENNARO R. A Certificateless Approach to Onion Routing[J]. International Journal of Information Security, 2017, 16(3): 327-343. |
| [21] | GIRGIS A M, DATA D, DIGGAVI S, et al. Shuffled Model of Federated Learning: Privacy, Accuracy and Communication Trade-Offs[J]. IEEE Journal on Selected Areas in Information Theory, 2021, 2(1): 464-478. |
| [22] | LYU Lingjuan, YU Jiangshan, NANDAKUMAR K, et al. Towards Fair and Privacy-Preserving Federated Deep Models[J]. IEEE Transactions on Parallel and Distributed Systems, 2020, 31(11): 2524-2541. |
| [23] | CHEN Yijin, SU Ye, ZHANG Mingyue, et al. FedTor: An Anonymous Framework of Federated Learning in Internet of Things[J]. IEEE Internet of Things Journal, 2022, 9(19): 18620-18631. |
| [24] | KOTZANIKOLAOU P, CHATZISOFRONIOU G, BURMESTER M. Broadcast Anonymous Routing (BAR): Scalable Real-Time Anonymous Communication[J]. International Journal of Information Security, 2017, 16(3): 313-326. |
| [25] | HAN Guangjie, ZHOU Lina, WANG Hao, et al. A Source Location Protection Protocol Based on Dynamic Routing in WSNS for the Social Internet of Things[J]. Future Generation Computer Systems, 2018, 82: 689-697. |
| [26] | KIM S, HAN J, HA J, et al. SGX-Tor: A Secure and Practical Tor Anonymity Network with SGX Enclaves[J]. IEEE/ACM Transactions on Networking, 2018, 26(5): 2174-2187. |
| [27] | WOLINSKY D I, CORRIGAN-GIBBS H, FORD B, et al. Dissent in Numbers: Making Strong Anonymity Scale[C]// USENIX. The 10th USENIX Symposium on Operating Systems Design and Implementation (OSDI’12). Berlin:USENIX, 2012: 179-182. |
| [28] | HASIRCIOGLU B, GUNDUZ D. Private Wireless Federated Learning with Anonymous Over-the-Air Computation[C]// IEEE. ICASSP 2021 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). New York: IEEE, 2021: 5195-5199. |
| [1] | 徐茹枝, 仝雨蒙, 戴理朋. 基于异构数据的联邦学习自适应差分隐私方法研究[J]. 信息网络安全, 2025, 25(1): 63-77. |
| [2] | 温金明, 刘庆, 陈洁, 吴永东. 基于错误学习的全同态加密技术研究现状与挑战[J]. 信息网络安全, 2024, 24(9): 1328-1351. |
| [3] | 林湛航, 向广利, 李祯鹏, 徐子怡. 基于同态加密的前馈神经网络隐私保护方案[J]. 信息网络安全, 2024, 24(9): 1375-1385. |
| [4] | 郭倩, 赵津, 过弋. 基于分层聚类的个性化联邦学习隐私保护框架[J]. 信息网络安全, 2024, 24(8): 1196-1209. |
| [5] | 蔡满春, 席荣康, 朱懿, 赵忠斌. 一种Tor网站多网页多标签指纹识别方法[J]. 信息网络安全, 2024, 24(7): 1088-1097. |
| [6] | 李增鹏, 王思旸, 王梅. 隐私保护近邻检测研究[J]. 信息网络安全, 2024, 24(6): 817-830. |
| [7] | 傅彦铭, 陆盛林, 陈嘉元, 覃华. 基于深度强化学习和隐私保护的群智感知动态任务分配策略[J]. 信息网络安全, 2024, 24(3): 449-461. |
| [8] | 薛茗竹, 胡亮, 王明, 王峰. 基于联邦学习和区块链技术的TAP规则处理系统[J]. 信息网络安全, 2024, 24(3): 473-485. |
| [9] | 林怡航, 周鹏远, 吴治谦, 廖勇. 基于触发器逆向的联邦学习后门防御方法[J]. 信息网络安全, 2024, 24(2): 262-271. |
| [10] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [11] | 何泽平, 许建, 戴华, 杨庚. 联邦学习应用技术研究综述[J]. 信息网络安全, 2024, 24(12): 1831-1844. |
| [12] | 徐健锋, 张炜, 涂敏, 魏勍颋, 赖展晴, 王倩倩. 基于语义融合轨迹生成的k匿名轨迹集补全方法[J]. 信息网络安全, 2024, 24(12): 1911-1921. |
| [13] | 兰浩良, 王群, 徐杰, 薛益时, 张勃. 基于区块链的联邦学习研究综述[J]. 信息网络安全, 2024, 24(11): 1643-1654. |
| [14] | 顾海艳, 柳琪, 马卓, 朱涛, 钱汉伟. 基于可用性的数据噪声添加方法研究[J]. 信息网络安全, 2024, 24(11): 1731-1738. |
| [15] | 萨其瑞, 尤玮婧, 张逸飞, 邱伟杨, 马存庆. 联邦学习模型所有权保护方案综述[J]. 信息网络安全, 2024, 24(10): 1553-1561. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 12
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 25
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||