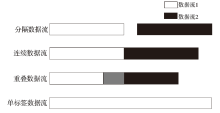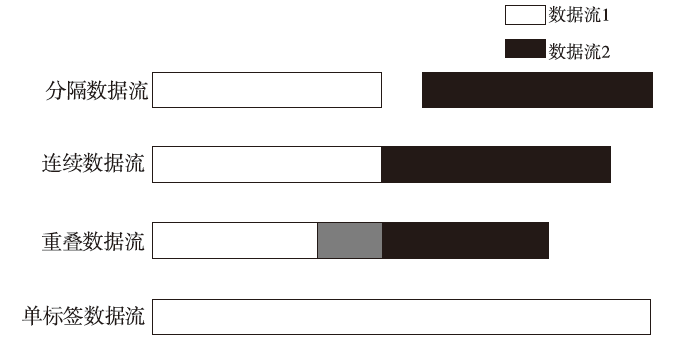信息网络安全 ›› 2024, Vol. 24 ›› Issue (7): 1088-1097.doi: 10.3969/j.issn.1671-1122.2024.07.010
一种Tor网站多网页多标签指纹识别方法
- 中国人民公安大学信息网络安全学院,北京 100038
-
收稿日期:2024-02-26出版日期:2024-07-10发布日期:2024-08-02 -
通讯作者:蔡满春caimanchun@ppsuc.edu.cn -
作者简介:蔡满春(1972—),男,河北,教授,博士,主要研究方向为密码学与通信保密|席荣康(1997—),男,河南,硕士研究生,主要研究方向为匿名通信|朱懿(2000—),男,上海,硕士研究生,主要研究方向为网络安全、深度学习|赵忠斌(1998—),男,四川,硕士研究生,主要研究方向为网络安全、机器学习。 -
基金资助:国家重点研发计划(2018YFC0823205);中国人民公安大学2022年度基本科研业务费项目(2022JKF02009)
A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website
CAI Manchun( ), XI Rongkang, ZHU Yi, ZHAO Zhongbin
), XI Rongkang, ZHU Yi, ZHAO Zhongbin
- College of Information and Cyber Security, People’s Public Security University of China, Beijing 100038, China
-
Received:2024-02-26Online:2024-07-10Published:2024-08-02
摘要:
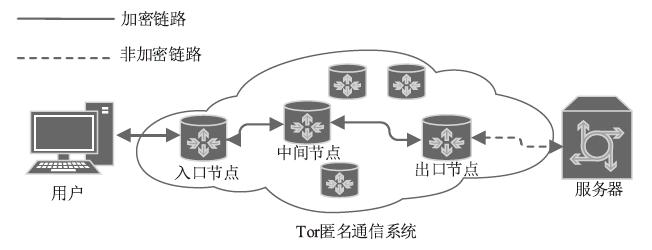
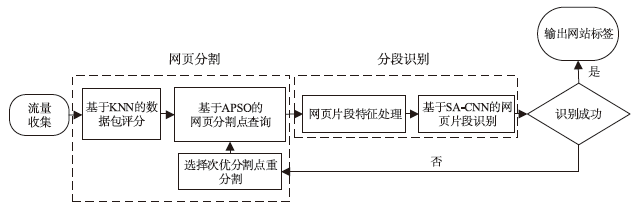
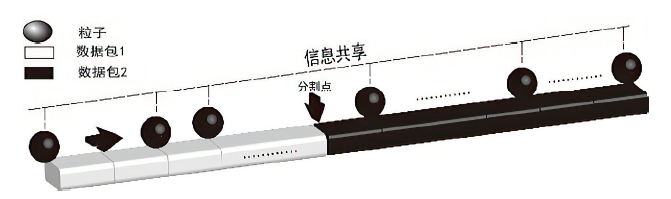
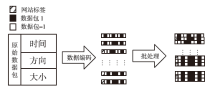
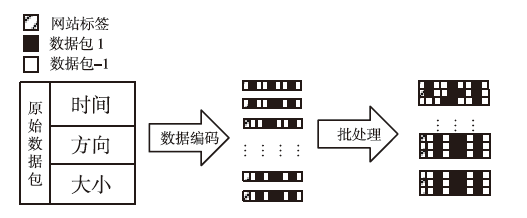
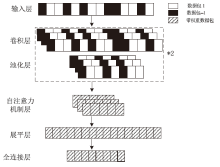
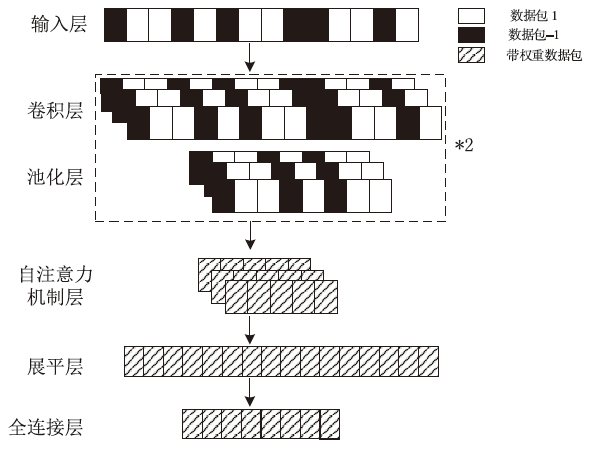
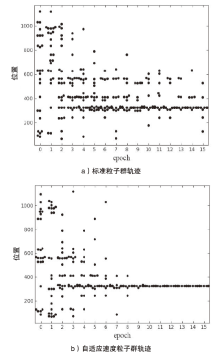
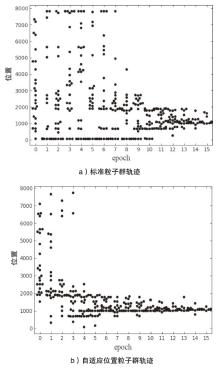
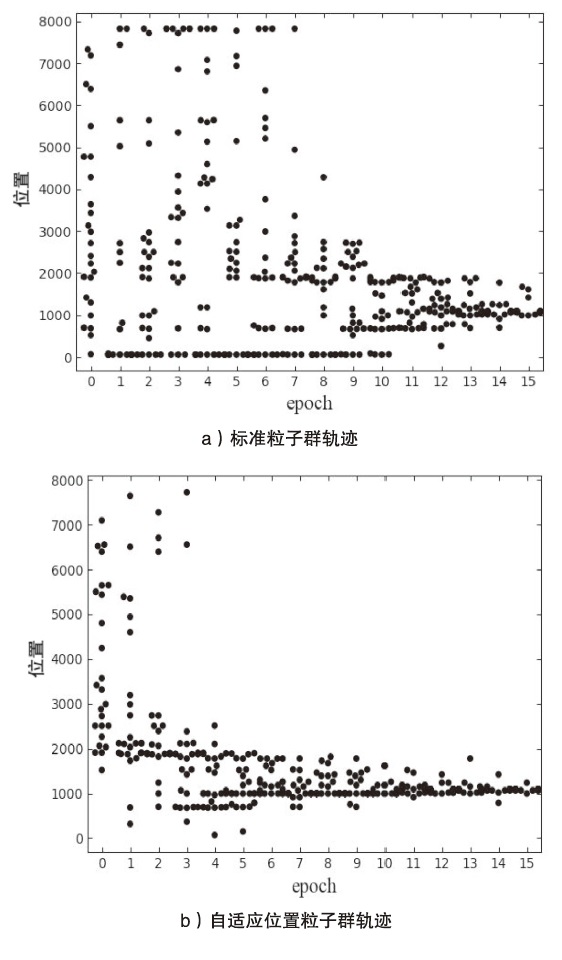
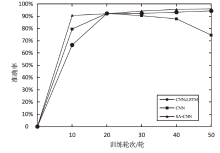
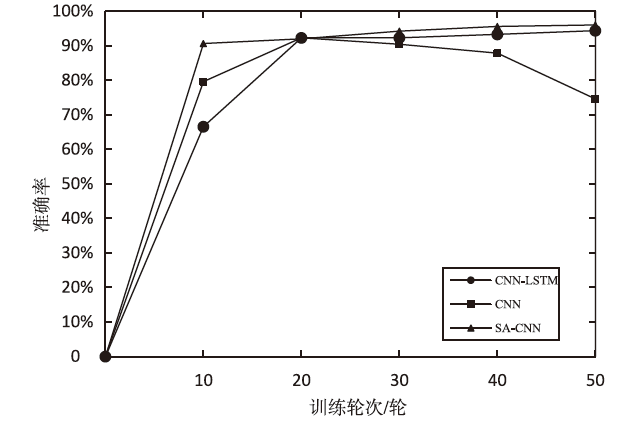
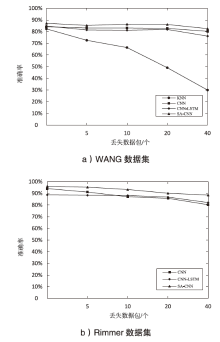
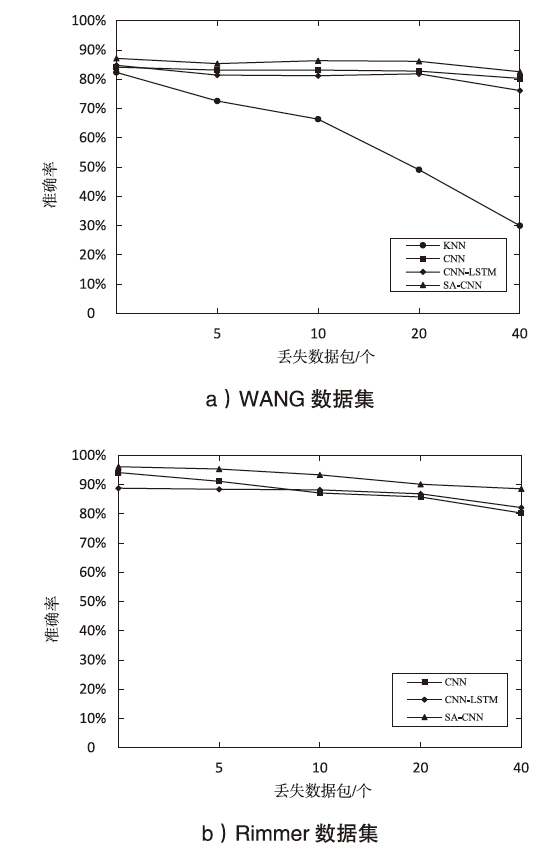
Tor匿名通信系统经常被不法分子用来从事暗网犯罪活动,Tor网页指纹识别技术为暗网监管提供技术手段。针对单标签Tor网页指纹识别技术在网络监管中实用性差的问题,文章提出一种多网页多标签Tor指纹识别方法。首先,对标准粒子群算法、K最近邻算法进行参数优化并整合,提出自适应粒子群优化K最近邻模型APSO-KNN,进行连续多标签网页分割。然后,利用自注意力机制和一维卷积神经网络模型对网页分割片段进行内容识别。最后,利用APSO-KNN记忆打分机制选择识别失败的网页的次优分割点进行网页重分割。实验结果表明,APSO-KNN采用粒子搜索机制代替穷举遍历机制寻找分割点能取得96.30%的分割准确率,分割效率较传统KNN算法有显著提高。深度学习模型SA-1DCNN抗网页分割误差性能远优于机器学习模型,识别准确率可达96.1%。
中图分类号:
引用本文
蔡满春, 席荣康, 朱懿, 赵忠斌. 一种Tor网站多网页多标签指纹识别方法[J]. 信息网络安全, 2024, 24(7): 1088-1097.
CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website[J]. Netinfo Security, 2024, 24(7): 1088-1097.
使用本文
| [1] | LI Jianping. The Secret Corner of Internet: Dark Network and Monitoring[J]. Security Work, 2021(6): 62-63. |
| 李建平. 互联网隐秘的角落:暗网与监控[J]. 保密工作, 2021 (6): 62-63. | |
| [2] | HINTZ A. Fingerprinting Web Privacy Enhancing Technologies[M]. Berlin: Springer, 2002. |
| [3] | DINGLEDINE R, MATHEWSON N, SYVERSON P. Tor: The Second-Generation Onion Router[J]. Journal of the Franklin Institute, 2004, 239(2): 135-139. |
| [4] | ABE K, GOTO S. Fingerprinting Attack on Tor Anonymity Using Deep Learning[EB/OL]. (2016-08-01)[2023-12-06]. https://core.ac.uk/reader/229876143. |
| [5] | RIMMER V, PREUVENEERS D, JUAREZ M, et al. Automated Website Fingerprinting through Deep Learning[EB/OL]. (2017-12-09)[2023-12-12]. https://arxiv.org/abs/1708.06376v2. |
| [6] |
ZHANG Daowei, DUAN Haixin. Website Fingerprinting Technique Based on Image Texture[J]. Journal of Computer Applications, 2020, 40(6): 1685-1691.
doi: 10.11772/j.issn.1001-9081.2019111981 |
|
张道维, 段海新. 基于图像纹理的网站指纹技术[J]. 计算机应用, 2020, 40(6): 1685-1691.
doi: 10.11772/j.issn.1001-9081.2019111981 |
|
| [7] |
WANG Tengfei, CAI Manchun, YUE Ting, et al. Tor Anonymous Traffic Identification Based on Histogram-XGBoost[J]. Computer Engineering and Applications, 2021, 57(14): 110-115.
doi: 10.3778/j.issn.1002-8331.2005-0161 |
|
王腾飞, 蔡满春, 岳婷, 等. Histogram-XGBoost的Tor匿名流量识别[J]. 计算机工程与应用, 2021, 57(14): 110-115.
doi: 10.3778/j.issn.1002-8331.2005-0161 |
|
| [8] |
MA Mingyan, CHEN Wei, WU Lifa. CNN_BiLSTM Network Based Intrusion Detection Method[J]. Computer Engineering and Applications, 2022, 58 (10): 116-124.
doi: 10.3778/j.issn.1002-8331.2102-0062 |
|
马明艳, 陈伟, 吴礼发. 基于CNN_BiLSTM 的网络入侵检测方法[J]. 计算机工程与应用, 2022, 58(10): 116-124.
doi: 10.3778/j.issn.1002-8331.2102-0062 |
|
| [9] |
XI Rongkang, CAI Manchun, LU Tianliang. Tor Traffic Analysis Model Based on Data Enhancement and Stream Data Processing[J]. Computer Engineering, 2023, 49(3): 177-184.
doi: 10.19678/j.issn.1000-3428.0064386 |
|
席荣康, 蔡满春, 芦天亮. 基于数据增强和流数据处理的 Tor 流量分析模型[J]. 计算机工程. 2023, 49(3): 177-184.
doi: 10.19678/j.issn.1000-3428.0064386 |
|
| [10] | WEI Shuning, CHEN Xingru, TANG Yong, et al. Research on the Application of AR-HELM Algorithm in Network Traffic Classification[J]. Netinfo Security, 2018, 18(1): 9-14. |
| 魏书宁, 陈幸如, 唐勇, 等. AR-HELM 算法在网络流量分类中的应用研究[J]. 信息网络安全, 2018, 18(1): 9-14. | |
| [11] | ATTARIAN R, ABDI L, HASHEMI S. AdaWFPA: Adaptive Online Website Fingerprinting Attack for Tor[J]. Computer Communications, 2019, 148: 74-85. |
| [12] | JUAREZ M, AFROZ S, ACAR G, et al. A Critical Evaluation of Website Fingerprinting Attacks[C]// ACM. Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2014: 263-274. |
| [13] | WANG Tao, GOLDBERG I. On Realistically Attacking Tor with Website Fingerprinting[J]. Proceedings on Privacy Enhancing Technologies, 2016(4): 21-36. |
| [14] | XU Yixiao, WANG Tao, LI Qi, et al. A Multi-Tab Website Fingerprinting Attack[C]// ACM. Proceedings of the 34th Annual Computer Security Applications Conference. New York: ACM, 2018: 327-341. |
| [15] | CUI Weiqi, CHEN Tao, FIELDS C, et al. Revisiting Assumptions for Website Fingerprinting Attacks[C]// ACM. Proceedings of the 2019 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2019: 328-339. |
| [16] | MENG Xiankun. Research on Tor Website Fingerprinting Based on Machine Learning[D]. Xi’an: Xidian University, 2020. |
| 孟献昆. 基于机器学习的匿名Tor网站指纹识别研究[D]. 西安: 西安电子科技大学, 2020. | |
| [17] | MA Chencheng, DU Xuehui, CAO Lifeng, et al. Burst-Analysis Website Fingerprinting Attack Based on Deep Neural Network[J]. Journal of Computer Research and Development, 2020, 57(4): 746-766. |
| 马陈城, 杜学绘, 曹利峰, 等. 基于深度神经网络burst特征分析的网站指纹攻击方法[J]. 计算机研究与发展, 2020, 57(4): 746-766. | |
| [18] | CHEN C C, LIN Yichen. What Drives Live-Stream Usage Intention? The Perspectives of Flow, Entertainment, Social Interaction, and Endorsement[J]. Telematics and Informatics, 2018, 35(1): 293-303. |
| [19] | ZHANG Fan, GAO Zhonghe, NIU Kun. Research on Network Traffic Anomaly Detection Based on KNN[J]. Communications Technology, 2021, 54(5): 1235-1239. |
| 张凡, 高仲合, 牛琨. 基于KNN的网络流量异常检测研究[J]. 通信技术, 2021, 54(5): 1235-1239. | |
| [20] | LECUN Y, BENGIO Y, HINTON G. Deep Learning[J]. Nature, 2015, 521: 436-444. |
| [21] | KATHAROPOULOS A, VYAS A, PAPPAS N, et al. Transformers Are RNNs: Fast Autoregressive Transformers with Linear Attention[EB/OL]. (2020-01-29)[2024-01-22]. https://arxiv.org/pdf/2006.16236v2.pdf. |
| [22] | LIN Zhouhan, FENG Minwei, SANTOS C N, et al. A Structured Self-Attentive Sentence Embedding[EB/OL]. (2017-03-09)[2024-01-25]. https://arxiv.org/pdf/1703.03130.pdf. |
| [23] | WANG Xuejian, YU Lantao, REN Kan, et al. Dynamic Attention Deep Model for Article Recommendation by Learning Human Editors’ Demonstration[C]// ACM. Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2017: 2051-2059. |
| [24] | GU X D, YANG M, LUO J Z. A Novel Website Fing Erprinting Attack against Multi-Tab Browsing Behavior[C]// IEEE. Proceedings of the 19th IEEE Int Conference on Computer Supported Cooperative Work in Design. New York: IEEE, 2015: 234-239. |
| [1] | 孙隽丰, 李成海, 宋亚飞. ACCQPSO:一种改进的量子粒子群优化算法及其应用[J]. 信息网络安全, 2024, 24(4): 574-586. |
| [2] | 张雪博, 刘敬浩, 付晓梅. 基于改进Logistic回归算法的抗Web DDoS攻击模型的设计与实现[J]. 信息网络安全, 2017, 17(6): 62-67. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 49
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 94
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||