信息网络安全 ›› 2024, Vol. 24 ›› Issue (9): 1375-1385.doi: 10.3969/j.issn.1671-1122.2024.09.006
基于同态加密的前馈神经网络隐私保护方案
- 武汉理工大学计算机与人工智能学院,武汉 430070
-
收稿日期:2024-05-29出版日期:2024-09-10发布日期:2024-09-27 -
通讯作者:向广利glxiang@whut.edu.cn -
作者简介:林湛航(2000—),男,湖北,硕士研究生,主要研究方向为信息安全、隐私保护|向广利(1973—),男,河南,教授,博士,CCF会员,主要研究方向为信息安全、人工智能|李祯鹏(2001—),男,湖北,硕士研究生,主要研究方向为隐私保护、同态加密|徐子怡(2001—),女,江西,硕士研究生,主要研究方向为信息安全 -
基金资助:国家自然科学基金(62276196)
Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption
LIN Zhanhang, XIANG Guangli( ), LI Zhenpeng, XU Ziyi
), LI Zhenpeng, XU Ziyi
- School of Computer and Artificial Intelligence, Wuhan University of Technology, Wuhan 430070, China
-
Received:2024-05-29Online:2024-09-10Published:2024-09-27
摘要:
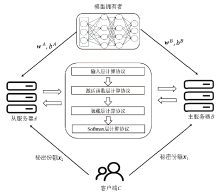
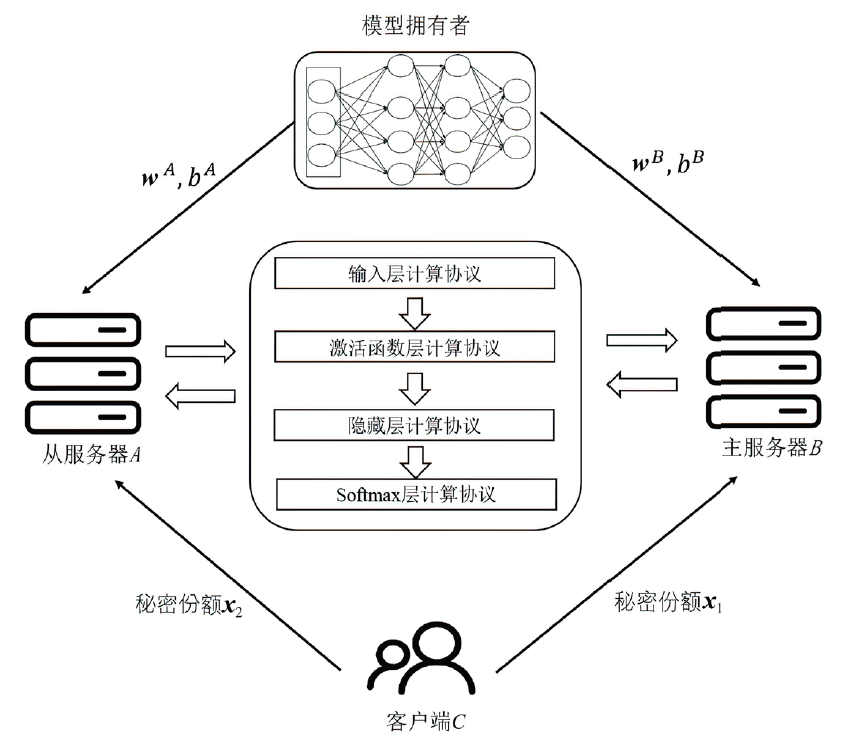
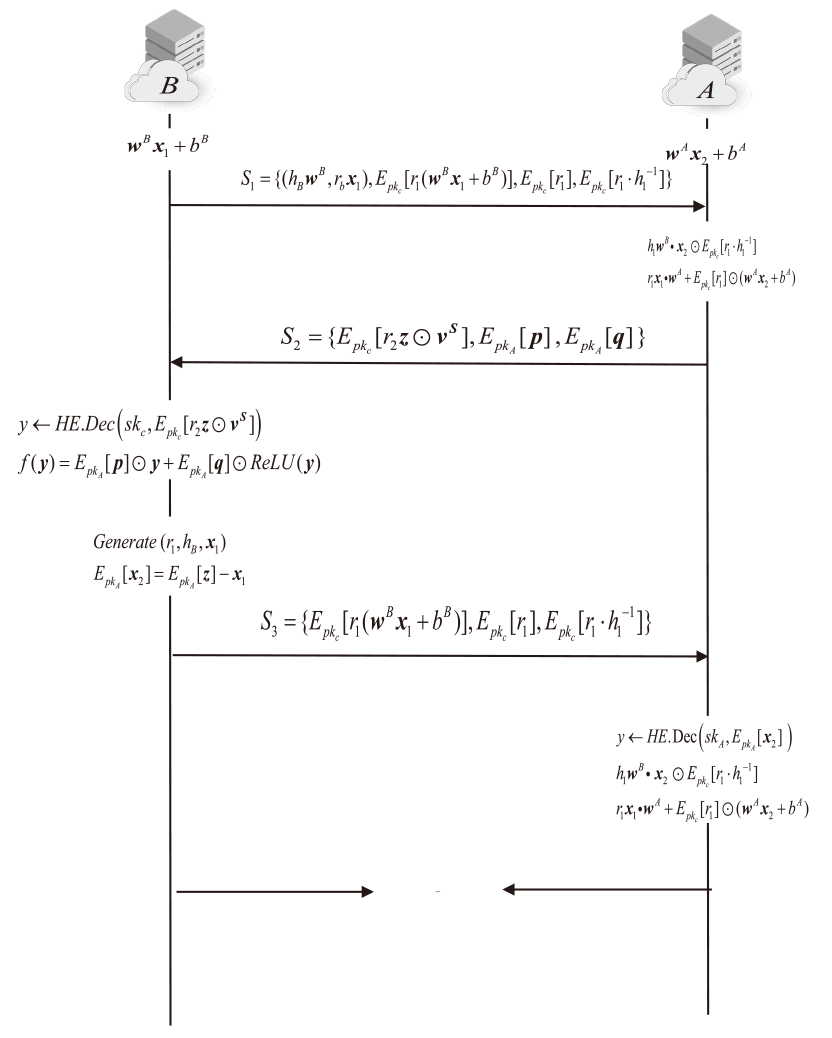
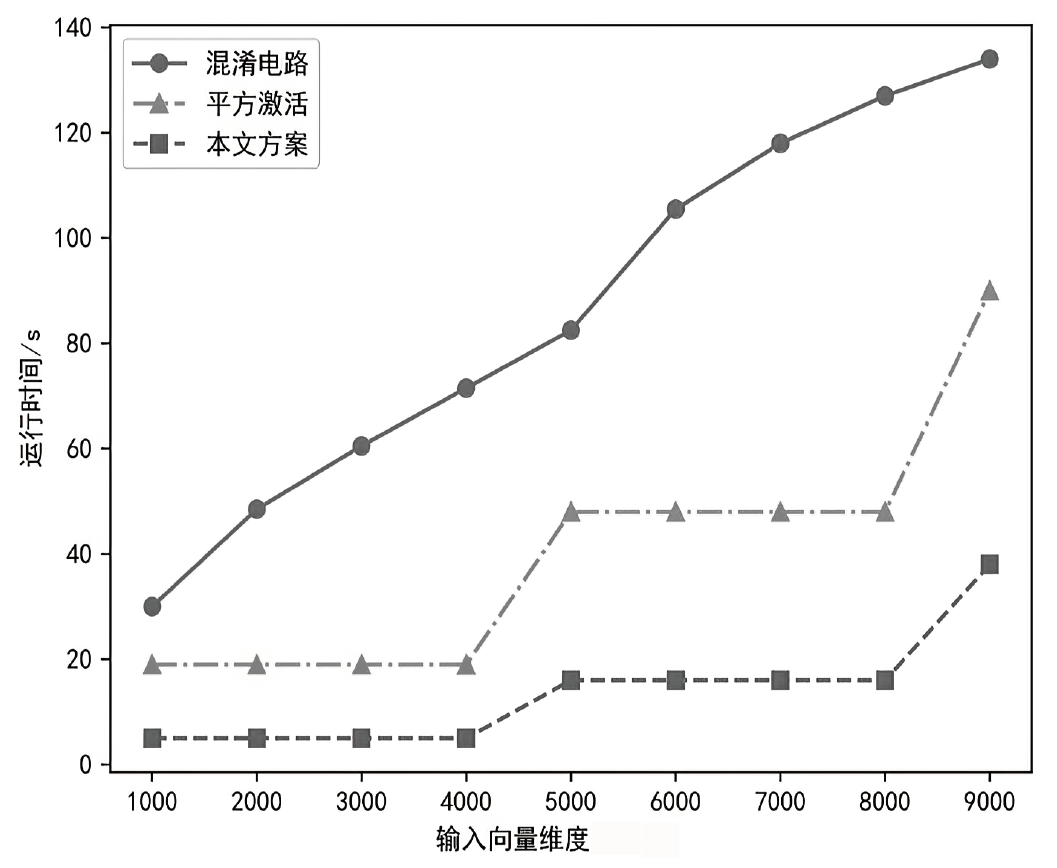
当前的隐私保护机器学习方法在保障数据隐私方面取得了一定进展,然而在计算效率和服务器资源利用等方面仍存在挑战。为了充分利用服务器资源,针对前馈神经网络,文章提出一种基于主从服务器架构的同态加密前馈神经网络隐私保护方案。该方案通过秘密共享技术将数据和模型参数分发至两个不共谋的服务器,并利用同态加密技术对服务器间的交互信息进行加密。在计算效率方面,通过避免耗时的密文向量和明文矩阵乘法,缩短了方案的运行时间。在安全性方面,通过引入随机噪声对秘密份额加噪,防止了服务器获得原始数据信息。实验结果表明,文章所提方案在计算复杂度和通信开销上均有显著改善。
中图分类号:
引用本文
林湛航, 向广利, 李祯鹏, 徐子怡. 基于同态加密的前馈神经网络隐私保护方案[J]. 信息网络安全, 2024, 24(9): 1375-1385.
LIN Zhanhang, XIANG Guangli, LI Zhenpeng, XU Ziyi. Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption[J]. Netinfo Security, 2024, 24(9): 1375-1385.
| [1] | HAMDAN M A, MAKLOUF A M, MNIF H. Review of Authentication with Privacy-Preserving Schemes for 5G-Enabled Vehicular Networks[C]// IEEE. 2022 15th International Conference on Security of Information and Networks. New York: IEEE, 2022, 15(4): 1-6. |
| [2] | RANGARAJU S, NESS S, DHARMALINGAM R. Incorporating AI-Driven Strategies in DevSecOps for Robust Cloud Security[J]. International Journal of Innovative Science and Research Technology, 2023, 8(23): 2359-2365. |
| [3] | TANUWIDJAJA H C, CHOI R, BAEK S, et al. Privacy-Preserving Deep Learning on Machine Learning as a Service-a Comprehensive Survey[J]. IEEE Access, 2020, 8(2): 167425-167447. |
| [4] | YANG Wencheng, WANG Song, CUI Hui, et al. A Review of Homomorphic Encryption for Privacy-Preserving Biometrics[EB/OL].(2023-03-29)[2024-04-30]. https://doi.org/10.3390/s23073566. |
| [5] | WANG Jianhua, LI Lin, ZHAO Zhendong, et al. A Neural Network Prediction Scheme Based on Total Homomorphic Encryption Algorithm[J]. Artificial Intelligence, 2022, 3(4): 97-108. |
| 王建华, 黎琳, 赵镇东, 等. 一种基于全同态加密算法的神经网络预测方案[J]. 人工智能, 2022, 3(4):97-108. | |
| [6] | GILAD-BACHRACH R, DOWLIN N, LAINE K, et al. Cryptonets: Applying Neural Networks to Encrypted Data with High Throughput and Accuracy[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2016, 48(2): 201-210. |
| [7] | HESAMIFARD E, TAKABI H, GHASEMI M. Cryptodl: Towards Deep Learning over Encrypted Data[C]// ACSAC. Annual Computer Security Applications Conference. New York: ACM, 2016, 6(3): 11-21. |
| [8] | MOHASSEL P, ZHANG Yupeng. SecureML: A System for Scalable Privacy-Preserving Machine Learning[C]// IEEE. 2017 IEEE Symposium on Security and Privacy. New York: IEEE, 2017, 36(2): 19-38. |
| [9] | LIU Jian, JUUTI M, LU Yao, et al. Oblivious Neural Network Predictions via Minionn Transformations[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017, 14(6): 619-631. |
| [10] | MOHASSEL P, RINDAL P. ABY3: A Mixed Protocol Framework for Machine Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018, 21(3): 35-52. |
| [11] | JUVEKAR C, VAIKUNTANATHAN V, CHANDRAKASAN A. Gazelle: A Low Latency Framework for Secure Neural Network Inference[C]// USENIX. 27th USENIX Security Symposium. Berkeley: USENIX, 2018, 23(2): 1651-1669. |
| [12] | WAGH S, GUPTA D, CHANDRAN N. SecureNN: 3-Party Secure Computation for Neural Network Training[J]. Proceedings on Privacy Enhancing Technologies, 2019, 2019(3): 26-49. |
| [13] | LI Jinguo, YAN Yan, ZHANG Kai, et al. FPCNN: A Fast Privacy-Preserving Outsourced Convolutional Neural Network with Low-Bandwidth[EB/OL]. (2023-11-01)[2024-04-30]. https://api.semanticscholar.org/CorpusID:265169136. |
| [14] | REN Yanli, YU Lingzan, HE Gang, et al. A Scheme of Privacy-Preserving Convolutional Neural Network Prediction[J]. Chinese Journal of Computers, 2023, 46(8): 1606-1619. |
| 任艳丽, 余凌赞, 何港, 等. 一种隐私保护的卷积神经网络预测方案[J]. 计算机学报, 2023, 46(8):1606-1619. | |
| [15] | NARESH V S, THAMARAI M. Privacy-Preserving Data Mining and Machine Learning in Healthcare: Applications, Challenges, and Solutions[J]. (2023-01-24)[2024-04-30]. https://wires.onlinelibrary.wiley.com/doi/abs/10.1002/widm.1490. |
| [16] | ZHAO Xia, WANG Limin, ZHANG Yufei, et al. A Review of Convolutional Neural Networks in Computer Vision[J]. Artificial Intelligence Review, 2024, 57(4): 1-43. |
| [17] | DONG Aoxiang, STARR A, ZHAO Yifan. Neural Network-Based Parametric System Identification: A Review[J]. International Journal of Systems Science, 2023, 54(13): 2676-2688. |
| [18] | CHEON J H, KIM A, KIM M, et al. Homomorphic Encryption for Arithmetic of Approximate Numbers[C]// Springer. Advances in Cryptology-ASIACRYPT 2017: 23rd International Conference on the Theory and Applications of Cryptology and Information Security. Heidelberg: Springer, 2017, 1(23): 409-437. |
| [19] | CHATTOPADHYAY A K, SAHA S, NAG A, et al. Secret Sharing: A Comprehensive Survey, Taxonomy and Applications[EB/OL]. (2024-02-01)[2024-04-30]. https://doi.org/10.1016/j.cosrev.2023.100608. |
| [20] | XIA Zhihua, GU Qi, XIONG Lizhi, et al. Privacy-Preserving Image Retrieval Based on Additive Secret Sharing[J]. International Journal of Autonomous and Adaptive Communications Systems, 2024, 17(2): 99-126. |
| [1] | 温金明, 刘庆, 陈洁, 吴永东. 基于错误学习的全同态加密技术研究现状与挑战[J]. 信息网络安全, 2024, 24(9): 1328-1351. |
| [2] | 郭倩, 赵津, 过弋. 基于分层聚类的个性化联邦学习隐私保护框架[J]. 信息网络安全, 2024, 24(8): 1196-1209. |
| [3] | 李增鹏, 王思旸, 王梅. 隐私保护近邻检测研究[J]. 信息网络安全, 2024, 24(6): 817-830. |
| [4] | 胡丞聪, 胡红钢. 基于格的最优轮数口令认证秘密共享协议[J]. 信息网络安全, 2024, 24(6): 937-947. |
| [5] | 文伟平, 张世琛, 王晗, 时林. 基于虚拟机自省的Linux恶意软件检测方案[J]. 信息网络安全, 2024, 24(5): 657-666. |
| [6] | 郭建胜, 关飞婷, 李志慧. 一种带作弊识别的动态(t,n)门限量子秘密共享方案[J]. 信息网络安全, 2024, 24(5): 745-755. |
| [7] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [8] | 孙隽丰, 李成海, 宋亚飞. ACCQPSO:一种改进的量子粒子群优化算法及其应用[J]. 信息网络安全, 2024, 24(4): 574-586. |
| [9] | 杨志鹏, 刘代东, 袁军翼, 魏松杰. 基于自注意力机制的网络局域安全态势融合方法研究[J]. 信息网络安全, 2024, 24(3): 398-410. |
| [10] | 张新有, 孙峰, 冯力, 邢焕来. 基于多视图表征的虚假新闻检测[J]. 信息网络安全, 2024, 24(3): 438-448. |
| [11] | 傅彦铭, 陆盛林, 陈嘉元, 覃华. 基于深度强化学习和隐私保护的群智感知动态任务分配策略[J]. 信息网络安全, 2024, 24(3): 449-461. |
| [12] | 张强, 何俊江, 李汶珊, 李涛. 基于深度度量学习的异常流量检测方法[J]. 信息网络安全, 2024, 24(3): 462-472. |
| [13] | 余尚戎, 肖景博, 殷琪林, 卢伟. 关注社交异配性的社交机器人检测框架[J]. 信息网络安全, 2024, 24(2): 319-327. |
| [14] | 王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527. |
| [15] | 萨其瑞, 尤玮婧, 张逸飞, 邱伟杨, 马存庆. 联邦学习模型所有权保护方案综述[J]. 信息网络安全, 2024, 24(10): 1553-1561. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||