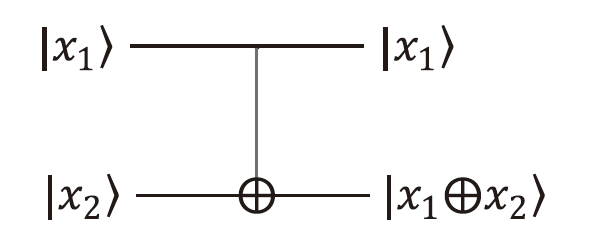信息网络安全 ›› 2024, Vol. 24 ›› Issue (9): 1364-1374.doi: 10.3969/j.issn.1671-1122.2024.09.005
d维量子系统中无需纠缠的量子身份认证协议
- 陕西师范大学数学与统计学院,西安 710119
-
收稿日期:2024-05-06出版日期:2024-09-10发布日期:2024-09-27 -
通讯作者:李志慧lizhihui@snnu.edu.cn -
作者简介:段昊哲(1999—),女,内蒙古,硕士研究生,主要研究方向为密码学|李志慧(1966—),女,陕西,教授,博士,主要研究方向为有限域和密码学|韦性佳(1991—),男,甘肃,博士研究生,主要研究方向为密码学|胡珂欣(1999—),女,山东,硕士研究生,主要研究方向为密码学 -
基金资助:国家自然科学基金(12071271)
Quantum Identity Authentication Protocol without Entanglement in d-Dimensional Quantum System
DUAN Haozhe, LI Zhihui( ), WEI Xingjia, HU Kexin
), WEI Xingjia, HU Kexin
- School of Mathematics and Statistics, Shaanxi Normal University, Xi’an, 710119, China
-
Received:2024-05-06Online:2024-09-10Published:2024-09-27
摘要:
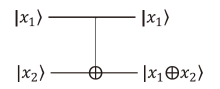
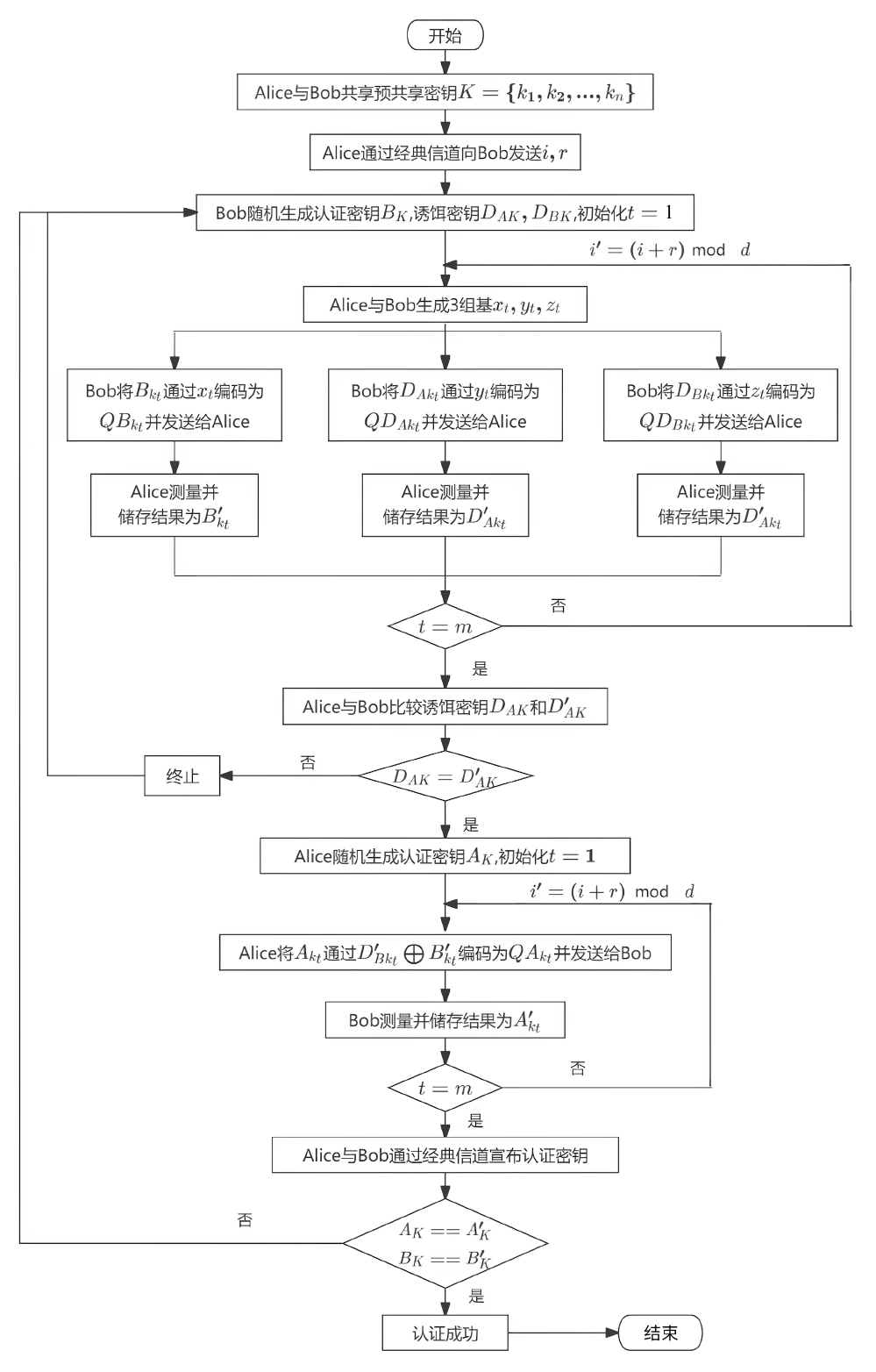
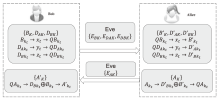
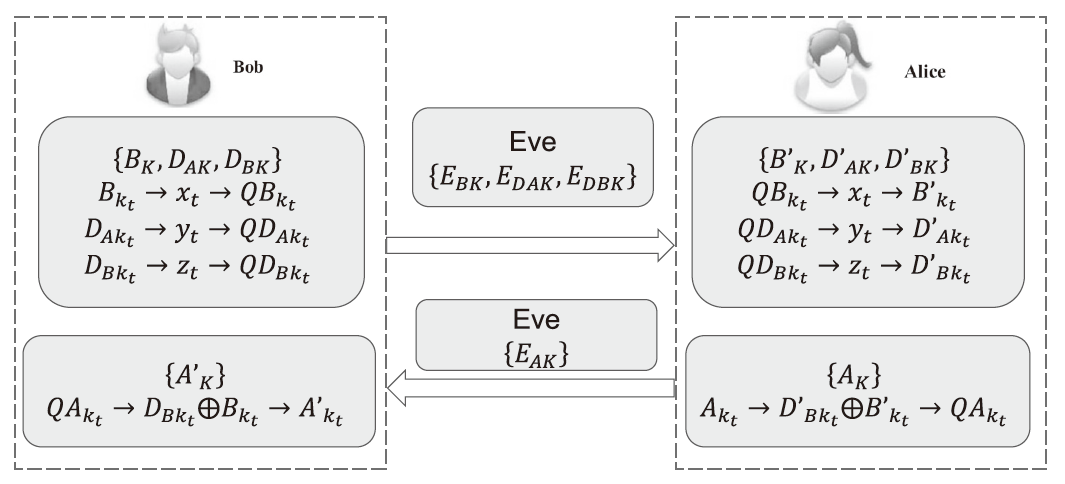
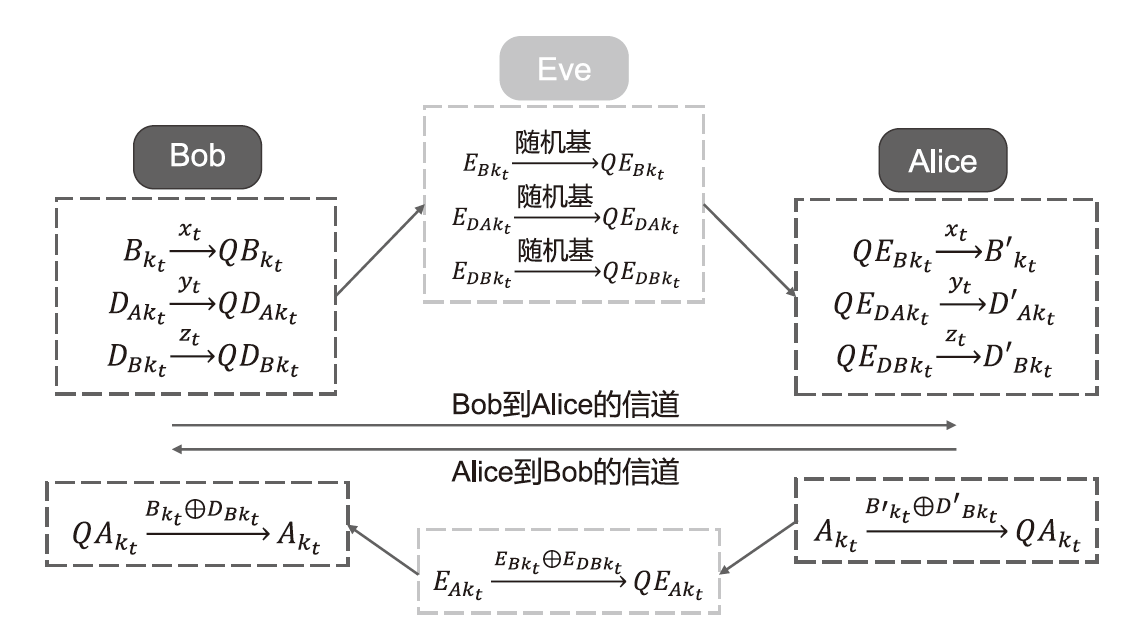
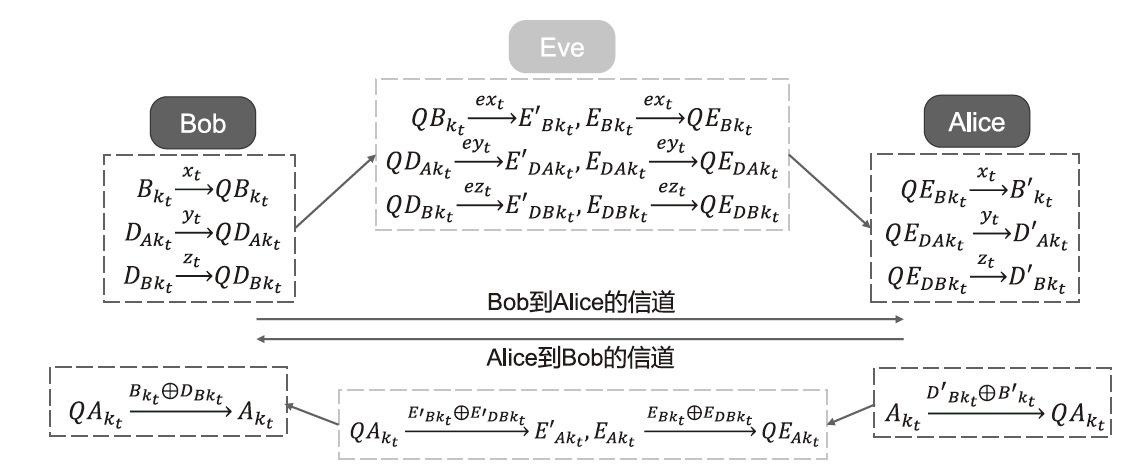
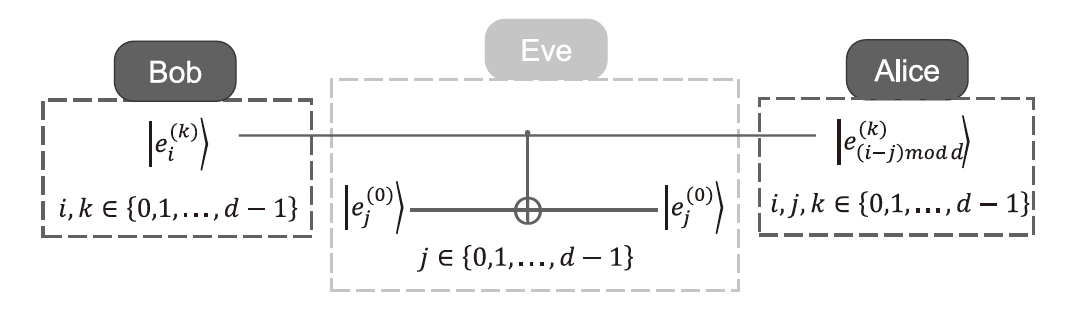
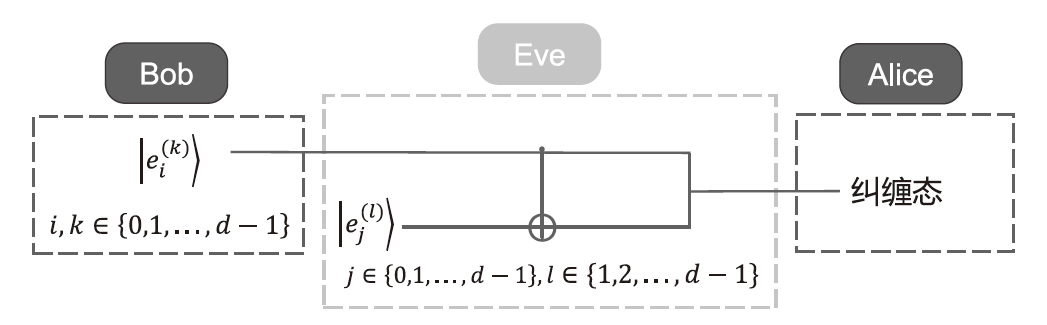
单光子量子身份认证协议不需要任何纠缠光子源,在一定程度上节省了量子资源。目前已有研究证明了在2维量子系统中,单光子量子身份认证协议在CNOT攻击下的安全性。文章基于奇素数d维计算基的受控非门与受控非门的相位反冲,证明了d维相互无偏基的受控非门的输出结果,即目标比特选择第一组相互无偏基中的向量时,控制比特发生改变,而目标比特选择其余d-1组相互无偏基中的任一向量时,产生纠缠态。基于此输出结果,文章提出了在奇素数d维量子系统中的量子身份认证协议,该协议可以在不泄露通信双方认证的预共享密钥的前提下验证双方的身份,且可以使用随机生成的密钥检测敌手的存在。在d维的协议中,通信双方选择的量子比特数目越多,协议成功的概率越高。安全性分析表明,该协议可以抵御冒充攻击、拦截测量重发攻击、纠缠测量攻击以及CNOT攻击。
中图分类号:
引用本文
段昊哲, 李志慧, 韦性佳, 胡珂欣. d维量子系统中无需纠缠的量子身份认证协议[J]. 信息网络安全, 2024, 24(9): 1364-1374.
DUAN Haozhe, LI Zhihui, WEI Xingjia, HU Kexin. Quantum Identity Authentication Protocol without Entanglement in d-Dimensional Quantum System[J]. Netinfo Security, 2024, 24(9): 1364-1374.
表1
Eve增益与检测的概率
| Bob 控制 比特 | Eve目标比特 | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| … | … | |||||||||||||
| Alice | Eve | Alice | Eve | Alice | Eve | … | Alice | Eve | Alice | Eve | … | Alice | Eve | |
| … | E | E | … | E | E | |||||||||
| … | E | E | … | E | E | |||||||||
| … | E | E | … | E | E | |||||||||
| … | … | … | … | … | … | … | … | … | … | E | E | … | E | E |
| … | E | E | … | E | E | |||||||||
| … | E | E | … | E | E | |||||||||
| … | E | E | … | E | E | |||||||||
| … | E | E | … | E | E | |||||||||
| … | … | … | … | … | … | … | … | … | … | E | E | … | E | E |
| … | E | E | … | E | E | |||||||||
表2
Alice与Bob共享的60位预共享密钥
| 比特 | 0 | 1 | 1 | 2 | 3 | 1 | 4 | 3 | 0 | 1 | 2 | 1 | 4 | 4 | 0 | 3 | 2 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 位置 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 |
| 比特 | 1 | 2 | 1 | 4 | 3 | 4 | 3 | 2 | 1 | 1 | 0 | 4 | 0 | 0 | 4 | 3 | 3 |
| 位置 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 | 32 | 33 | 34 |
| 比特 | 0 | 2 | 1 | 3 | 2 | 4 | 3 | 2 | 3 | 4 | 4 | 2 | 1 | 1 | 3 | 0 | 4 |
| 位置 | 35 | 36 | 37 | 38 | 39 | 40 | 41 | 42 | 43 | 44 | 45 | 46 | 47 | 48 | 49 | 50 | 51 |
| 比特 | 0 | 0 | 2 | 1 | 3 | 4 | 1 | 2 | 2 | ||||||||
| 位置 | 52 | 53 | 54 | 55 | 56 | 57 | 58 | 59 | 60 |
表4
双方制备基和Bob编码
| 迭代次数 | Alice与Bob制备基 | Bob编码 | |||||||
|---|---|---|---|---|---|---|---|---|---|
| 3 | 1 | 2 | 0 | 4 | 3 | ||||
| 1 | 2 | 0 | 1 | 3 | 2 | ||||
| 2 | 0 | 2 | 4 | 2 | 2 | ||||
| 0 | 2 | 0 | 0 | 2 | 2 | ||||
| 2 | 0 | 0 | 2 | 2 | 0 | ||||
| 4 | 0 | 1 | 0 | 4 | 1 | ||||
表5
Alice解码并测量
| 迭代次数 | Alice解码所用基 | Alice测量结果 | ||||
|---|---|---|---|---|---|---|
| 4 | 1 | 3 | ||||
| 1 | 1 | 2 | ||||
| 2 | 2 | 1 | ||||
| 3 | 4 | 4 | ||||
| 0 | 0 | 0 | ||||
| 3 | 2 | 1 | ||||
表6
Alice编码与Bob解码
| Alice解码 | Bob解码所用基 | Bob测量结果 | ||
|---|---|---|---|---|
| 2 | 2 | 2 | ||
| 4 | 3 | 4 | ||
| 1 | 3 | 1 | ||
| 2 | 2 | 2 | ||
| 3 | 0 | 3 | ||
| 0 | 4 | 0 |
| [1] | LI Xiaoyu, BARNUM H. Quantum Authentication Using Entangled States[J]. International Journal of Foundations of Computer Science, 2004, 15(4): 609-617. |
| [2] | WANG Jian, ZHANG Quan, TANG Chaojing. Multiparty Simultaneous Quantum Identity Authentication Based on Entanglement Swapping[J]. Chinese Physics Letters, 2006, 23(9): 2360-2363. |
| [3] | LIU Lijuan, LI Zhihui, ZHI Danli. A Multi-Party Quantum Key Distribution Protocol with Quantum Identity Authentication[J]. Netinfo Security, 2020, 20(11): 59-66. |
| 刘利娟, 李志慧, 支丹利. 可实现身份认证的多方量子密钥分发协议[J]. 信息网络安全, 2020, 20(11): 59-66. | |
| [4] | LI Xiang, ZHANG Kejia, ZHANG Long, et al. A New Quantum Multiparty Simultaneous Identity Authentication Protocol with the Classical Third-Party[EB/OL]. (2022-05-30)[2024-04-25]. https://pubmed.ncbi.nlm.nih.gov/35455145/. |
| [5] | ZHANG Shun, CHEN Zhangkai, LIANG Fengyu, et al. A Quantum Identity Authentication Based on Bell State[J]. Netinfo Security, 2019, 19(11): 43-48. |
| 张顺, 陈张凯, 梁风雨, 等. 基于Bell态的量子双向身份认证协议[J]. 信息网络安全, 2019, 19(11): 43-48. | |
| [6] | ZHONG Jifeng, RUAN Banyao, LIU Zhihao. Quantum Secret Sharing with Identity Authentication Based on GHZ States Entanglement Swapping[EB/OL]. (2023-10-15)[2024-04-25]. https://link.springer.com/article/10.1007/s10773-023-05455-0#citeas. |
| [7] | ZHANG Zheshen, ZENG Guihua, ZHOU Nanrun, et al. Quantum Identity Authentication Based on Ping-Pong Technique for Photons[J]. Physics Letters A, 2006, 356(3): 199-205. |
| [8] | ZHANG Shun, CHEN Zhangkai, SHI Runhua, et al. A Novel Quantum Identity Authentication Based on Bell States[J]. International Journal of Theoretical Physics, 2020, 59(1): 236-249. |
| [9] | MIHARA T. Quantum Identification Schemes with Entanglements[EB/OL]. (2002-05-08)[2024-04-25]. https://journals.aps.org/pra/abstract/10.1103/PhysRevA.65.052326. |
| [10] | LJUNGGREN D, KARLSSON A, BOURENNANE M. Authority-Based User Authentication in Quantum Key Distribution[EB/OL]. [2024-04-25]. https://www.nstl.gov.cn/paper_detail.html?id=3f85086e6a8da4313351ca0f000b833d. |
| [11] | MAJUMDAR R, DAS S. SOK: An Evaluation of Quantum Authentication through Systematic Literature Review[EB/OL]. [2024-04-25]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1r3k0c60a0510ax0n4340c30t9582975&site=xueshu_se. |
| [12] | YUAN Hao, LIU Yimin, PAN Guozhu, et al. Quantum Identity Authentication Based on Ping-Pong Technique without Entanglements[J]. Quantum Information Processing, 2014, 13(11): 2535-2549. |
| [13] | LUCAMARINI M, MANCINI S. Secure Deterministic Communication without Entanglement[EB/OL]. (2005-04-14)[2024-04-25]. https://journals.aps.org/prl/abstract/10.1103/PhysRevLett.94.140501. |
| [14] | SHI Weimin, ZHANG Jianbiao, ZHOU Yihua, et al. A Novel Quantum Deniable Authentication Protocol without Entanglement[J]. Quantum Information Processing, 2015, 14(6): 2183-2193. |
| [15] | SHI Weimin, ZHOU Yihua, YANG Yuguang. Quantum Deniable Authentication Protocol[J]. Quantum Information Processing, 2014, 13(7): 1501-1510. |
| [16] | GOTTESMAN D, CHUANG I. Quantum Digital Signatures[EB/OL]. (2002-12-26)[2024-04-25]. https://arxiv.org/pdf/quant-ph/0105032. |
| [17] | RASS S, KÖNIG S, SCHAUER, et al. Implementation and Evaluation of Intrinsic Authentication in Quantum Key Distribution Protocols[J]. International Journal on Advances in Security, 2016, 9(1): 59-65. |
| [18] | HONG C H, HEO J, JANG J G, et al. Quantum Identity Authentication with Single Photon[EB/OL]. (2017-08-17)[2024-04-25]. https://link.springer.com/article/10.1007/s11128-017-1681-0. |
| [19] | RAO B D, JAYARAMAN R. A Novel Quantum Identity Authentication Protocol without Entanglement and Preserving Pre-Shared Key Information[EB/OL]. (2023-01-31)[2024-04-25]. https://link.springer.com/article/10.1007/s11128-023-03832-6. |
| [20] | ZHANG Qi, DU Mingming, ZHONG Wei, et al. Single-Photon Based Three-Party Quantum Secure Direct Communication with Identity Authentication[EB/OL]. (2023-11-27)[2024-04-25]. https://onlinelibrary.wiley.com/doi/10.1002/andp.202300407. |
| [21] | WANG Yuqi, JIAN Liya, LIU Shiming, et al. Two-Party Quantum Identity Authentication without Entanglement[EB/OL]. (2023-10-09)[2024-04-25]. https://pubs.aip.org/aip/jap/article-abstract/134/14/144401/2915874/Two-party-quantum-identity-authentication-without?redirectedFrom=fulltext. |
| [22] | XU Yuguang, ZHANG Lu, ZHU Hongfeng. Quantum Mutual Implicit Authentication Key Agreement Protocol without Entanglement with Key Recycling[EB/OL]. (2023-11-14)[2024-04-25]. https://link.springer.com/article/10.1007/s10773-023-05501-x. |
| [23] | LI Guodong, LIU Jiacheng, WANG Qingle, et al. Employing Single Photons for Measurement-Device-Independent Quantum Secure Direct Communication with Identity Authentication[J]. IEEE Communications Letters, 2024, 28(3): 473-477. |
| [24] | AZAHARI N S B, HARUN N Z B, AHMAD ZUKARNAIN Z B. Quantum Identity Authentication for Non-Entanglement Multiparty Communication: A Review, State of Art and Future Directions[J]. ICT Express, 2023, 9(4): 534-547. |
| [25] | IVONOVIC I D. Geometrical Description of Quantal State Determination[J]. Journal of Physics A: Mathematical and General, 1981, 14(12): 3241-3245. |
| [26] | WOOTTERS W K, FIELDS B D. Optimal State-Determination by Mutually Unbiased Measurements[J]. Annals of Physics, 1989, 191(2): 363-381. |
| [27] | QIN Huawang, TSO R, DAI Yuewei. Multi-Dimensional Quantum State Sharing Based on Quantum Fourier Transform[EB/OL]. (2018-01-24)[2024-04-25]. https://link.springer.com/article/10.1007/s11128-018-1827-8. |
| [28] | NIELSEN M A, CHUANG I L. Quantum Computation and Quantum Information[M]. Cambridge: Cambridge University Press, 2000. |
| [29] |
SHOR P W, PRESKILL J. Simple Proof of Security of the BB84 Quantum Key Distribution Protocol[J]. Physical Review Letters, 2000, 85(2): 441-444.
pmid: 10991303 |
| [1] | 刘利娟, 李志慧, 支丹利. 可实现身份认证的多方量子密钥分发协议[J]. 信息网络安全, 2020, 20(11): 59-66. |
| [2] | 张顺, 陈张凯, 梁风雨, 石润华. 基于Bell态的量子双向身份认证协议[J]. 信息网络安全, 2019, 19(11): 43-48. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||