信息网络安全 ›› 2024, Vol. 24 ›› Issue (9): 1352-1363.doi: 10.3969/j.issn.1671-1122.2024.09.004
面向云辅助工业物联网的高效可搜索属性基加密方案
张学旺1( ), 陈思宇1, 罗欣悦1, 雷志滔1, 谢昊飞2
), 陈思宇1, 罗欣悦1, 雷志滔1, 谢昊飞2
- 1.重庆邮电大学软件工程学院,重庆 400065
2.重庆邮电大学自动化学院,重庆 400065
-
收稿日期:2024-06-03出版日期:2024-09-10发布日期:2024-09-27 -
通讯作者:张学旺zhangxw@cqupt.edu.cn -
作者简介:张学旺(1974—),男,湖南,副教授,博士,CCF会员,主要研究方向为区块链、物联网、数据安全、隐私保护、大数据、智能数据处理|陈思宇(1999—),男,四川,硕士研究生,主要研究方向为属性基加密、互联网软件及安全技术|罗欣悦(2001—),女,四川,硕士研究生,主要研究方向为区块链、互联网软件及安全技术|雷志滔(1998—),男,四川,硕士研究生,主要研究方向为区块链、互联网软件及安全技术|谢昊飞(1978—),男,湖南,教授,博士,CCF会员,主要研究方向为网络化控制系统、无线感知、工业物联网 -
基金资助:国家重点研发计划(2022YFB3204503);重庆市城市管理科研项目(城管科字2023第35号)
Efficient Searchable Attribute-Based Encryption Scheme for Cloud-Assisted Industrial IoT
ZHANG Xuewang1( ), CHEN Siyu1, LUO Xinyue1, LEI Zhitao1, XIE Haofei2
), CHEN Siyu1, LUO Xinyue1, LEI Zhitao1, XIE Haofei2
- 1. School of Software Engineering, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
2. School of Automation, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
-
Received:2024-06-03Online:2024-09-10Published:2024-09-27
摘要:
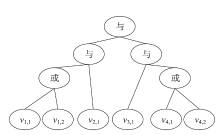
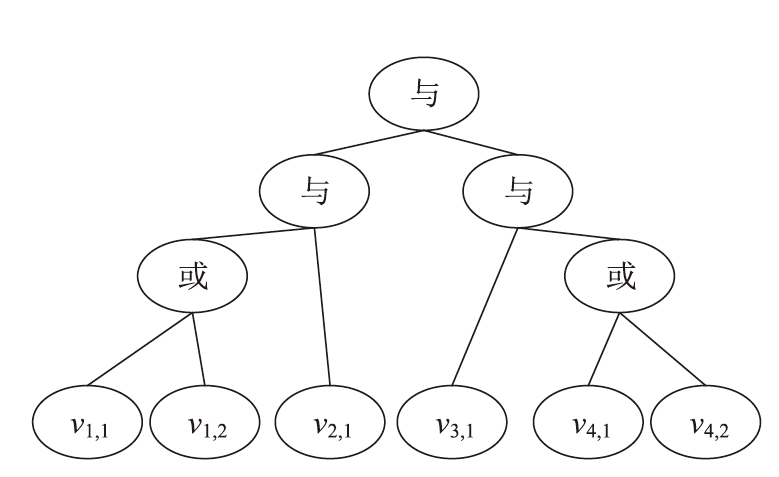
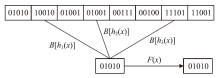
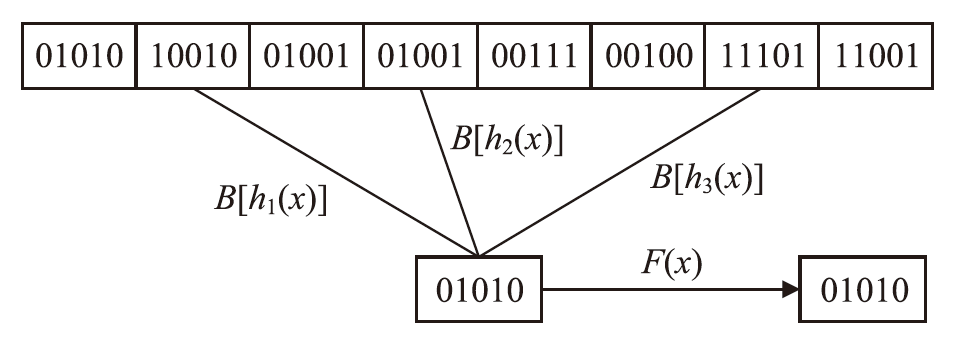
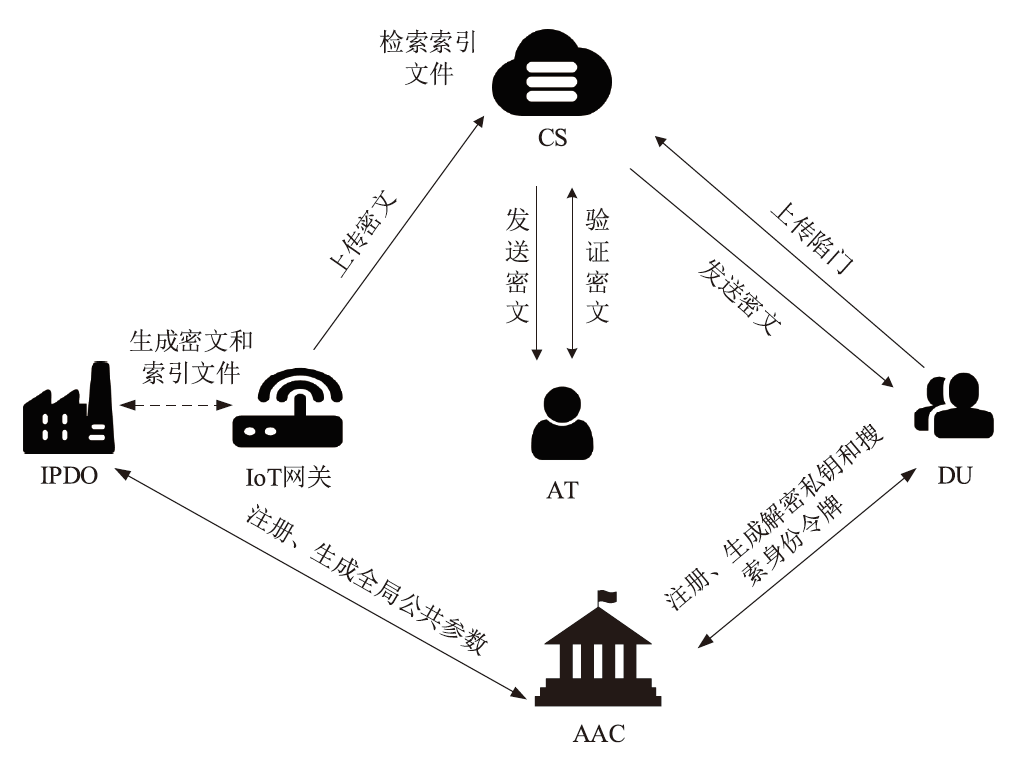
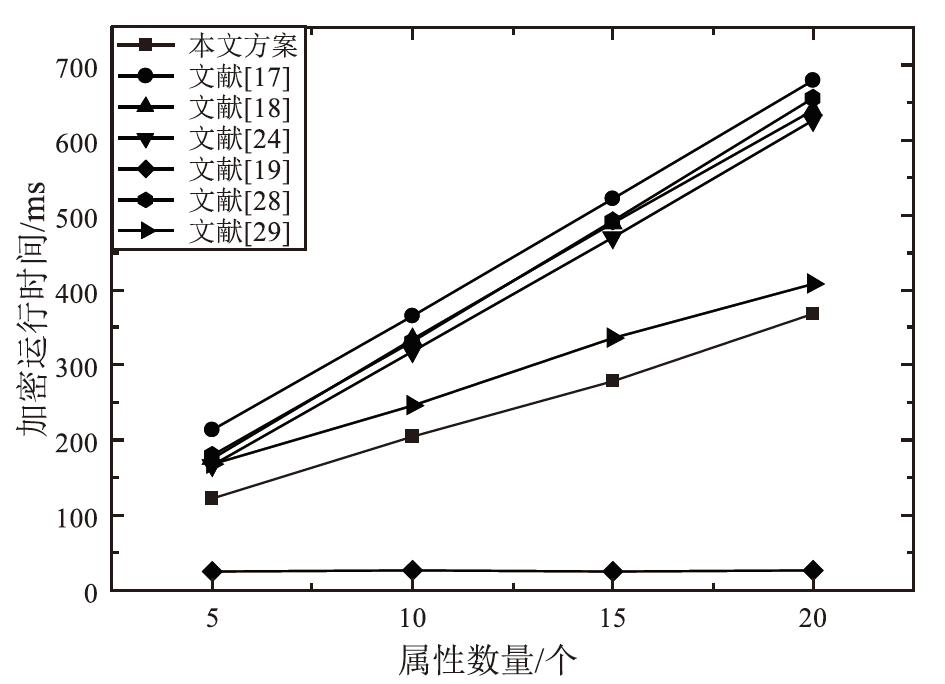
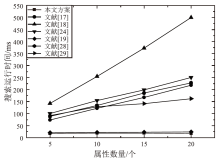
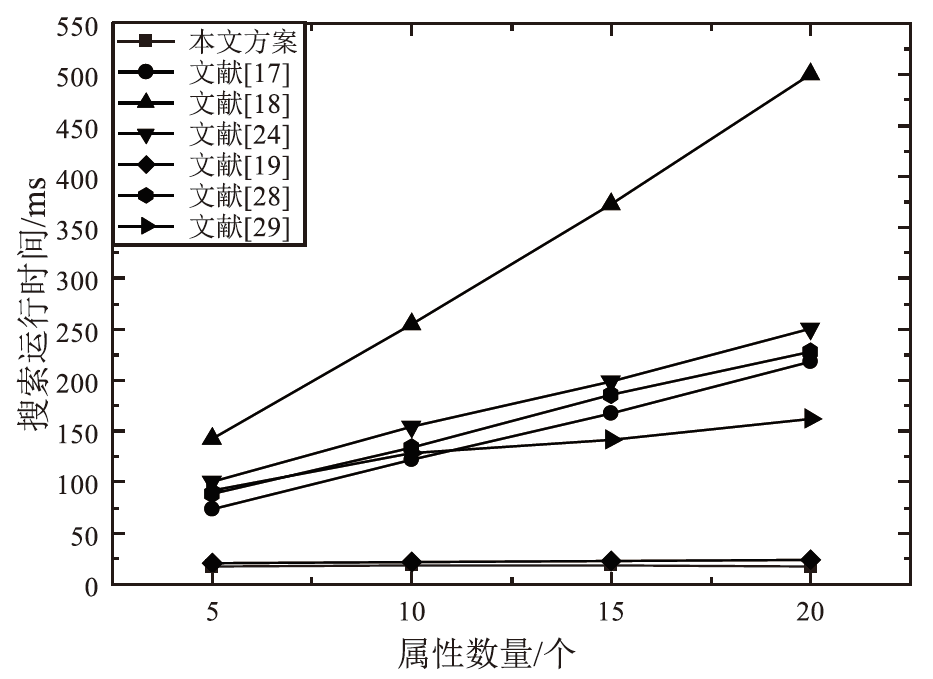
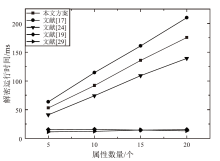
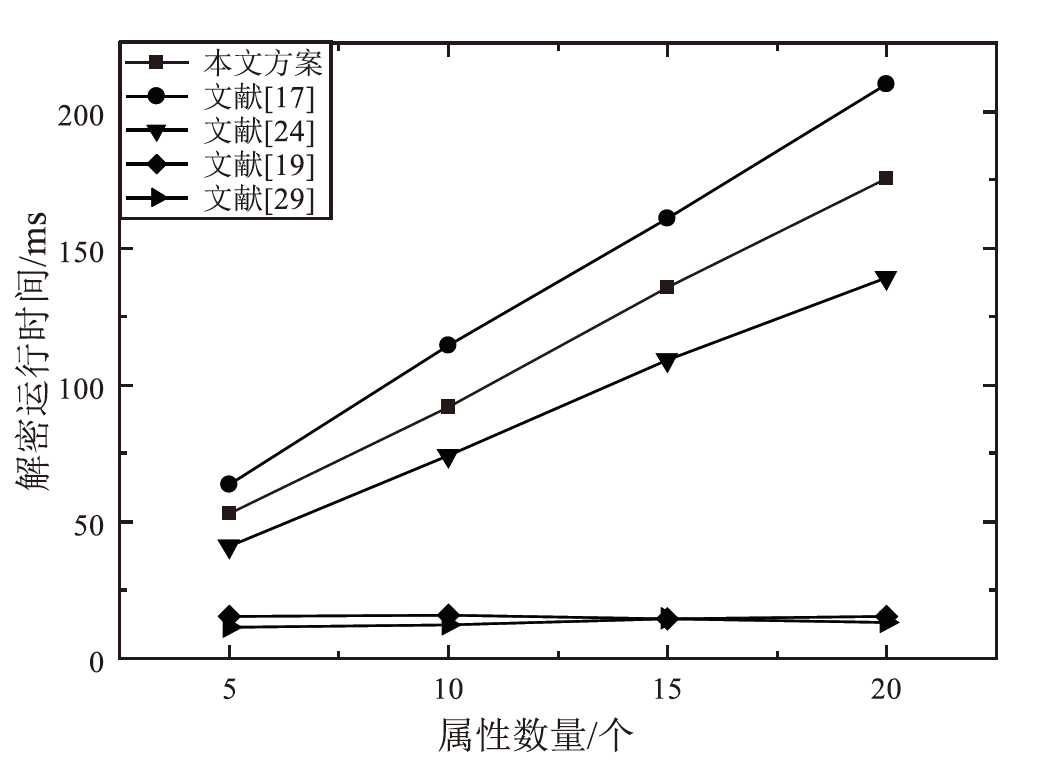
云存储可以有效存储和管理工业物联网生成的海量数据,但缺乏灵活安全的访问控制机制,且上传的加密数据难以高效检索。为解决这些问题,文章提出一种面向工业物联网的高效可搜索属性基加密方案,该方案具有隐私保护、多关键词搜索和数据验证等功能。方案利用对称加密和属性基加密以在线/离线加密方式加密明文,利用异或过滤器和随机秘密值实现部分访问策略隐藏,提高工业数据的安全性。此外,方案基于多项式方程实现支持子集查询的多关键词高效搜索,通过签名加密的方式验证云服务器中数据的完整性。安全性分析表明,该方案在DBDH困难问题假设下可以抵御选择明文攻击。理论分析和仿真实验结果表明,该方案在加密、陷门生成和搜索等阶段与对比方案相比具有更高的效率,功能更全面。
中图分类号:
引用本文
张学旺, 陈思宇, 罗欣悦, 雷志滔, 谢昊飞. 面向云辅助工业物联网的高效可搜索属性基加密方案[J]. 信息网络安全, 2024, 24(9): 1352-1363.
ZHANG Xuewang, CHEN Siyu, LUO Xinyue, LEI Zhitao, XIE Haofei. Efficient Searchable Attribute-Based Encryption Scheme for Cloud-Assisted Industrial IoT[J]. Netinfo Security, 2024, 24(9): 1352-1363.
表2
各方案计算开销对比
| 方案 | 加密阶段 | 搜索阶段 | 陷门生成阶段 | 解密阶段 |
|---|---|---|---|---|
| 文献[ | P+(4N+5)E+ET | (2S+3)P+SET | (S+5)E | (2S+1)P+SET |
| 文献[ | (4N+2)E+ET | (2S+1)P+(2S+2)E | (2S+1)E | — |
| 文献[ | (4N+Q+1)E+ET | (2S+3)P+2E | (2S+4)E | SP+2SET |
| 文献[ | 2E+ET | 3P+ET | (2S+1)E | 2P |
| 文献[ | (2N+1)E+ET | (2S+1)P | (2S+1)E | — |
| 文献[ | (2N+4)E+(Q+1)P | (S+3)P | (S+4)E | P |
| 本文方案 | (2N+5)E+2ET | P+E+ET | E | (2S+1)P |
| [1] | SISINNI E, SAIFULLAH A, HAN Song, et al. Industrial Internet of Things: Challenges, Opportunities, and Directions[J]. IEEE Transactions on Industrial Informatics, 2018, 14(11): 4724-4734. |
| [2] | ZHANG Xiaojun, XU Chunxiang, WANG Huaxiong, et al. FS-PEKS: Lattice-Based Forward Secure Public-Key Encryption with Keyword Search for Cloud-Assisted Industrial Internet of Things[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(3): 1019-1032. |
| [3] | SINGH A, CHATTERJEE K. Cloud Security Issues and Challenges: A Survey[J]. Journal of Network and Computer Applications, 2017, 79: 88-115. |
| [4] | USMAN M, JAN M A, HE Xiangjian, et al. P2DCA: A Privacy-Preserving-Based Data Collection and Analysis Framework for IoMT Applications[J]. IEEE Journal on Selected Areas in Communications, 2019, 37(6): 1222-1230. |
| [5] | YIN Hui, ZHANG Wei, DENG Hua, et al. An Attribute-Based Searchable Encryption Scheme for Cloud-Assisted IIoT[J]. IEEE Internet of Things Journal, 2023, 10(12): 11014-11023. |
| [6] | ZHANG Ke, LONG Jiahuan, WANG Xiaofen, et al. Lightweight Searchable Encryption Protocol for Industrial Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2021, 17(6): 4248-4259. |
| [7] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. 24th Annual International Conference on Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2005: 457-473. |
| [8] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. 2007 IEEE Symposium on Security and Privacy. NewYork: IEEE, 2007: 321-334. |
| [9] | XIONG Hu, HUANG Xin, YANG Minghao, et al. Unbounded and Efficient Revocable Attribute-Based Encryption with Adaptive Security for Cloud-Assisted Internet of Things[J]. IEEE Internet of Things Journal, 2022, 9(4): 3097-3111. |
| [10] | SUN Jianfei, YUAN Yu, TANG Mingjian, et al. Privacy-Preserving Bilateral Fine-Grained Access Control for Cloud-Enabled Industrial IoT Healthcare[J]. IEEE Transactions on Industrial Informatics, 2022, 18(9): 6483-6493. |
| [11] |
SUN Jianfei, XIONG Hu, LIU Ximeng, et al. Lightweight and Privacy-Aware Fine-Grained Access Control for IoT-Oriented Smart Health[J]. IEEE Internet of Things Journal, 2020, 7(7): 6566-6575.
doi: 10.1109/JIOT.2020.2974257 |
| [12] | WANG Huiyong, LIANG Jialing, DING Yong, et al. Ciphertext-Policy Attribute-Based Encryption Supporting Policy-Hiding and Cloud Auditing in Smart Health[EB/OL]. [2024-04-23]. https://www.sciencedirect.com/science/article/abs/pii/S0920548922000630?via%3Dihub. |
| [13] | ZHANG Zhaoqian, ZHANG Jianbiao, YUAN Yilin, et al. An Expressive Fully Policy-Hidden Ciphertext Policy Attribute-Based Encryption Scheme with Credible Verification Based on Blockchain[J]. IEEE Internet of Things Journal, 2022, 9(11): 8681-8692. |
| [14] | SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]// IEEE. The 2000 IEEE Symposium on Security and Privacy. New York: IEEE, 2000: 44-55. |
| [15] | KAUSHIK K, VARADHARAJAN V, NALLUSAMY R. Multi-User Attribute Based Searchable Encryption[C]// IEEE. 2013 IEEE 14th International Conference on Mobile Data Management. New York: IEEE, 2013: 200-205. |
| [16] |
YIN Xinchun, WANG Mengyu, NING Jianting. Lightweight Searchable Medical Data Sharing Scheme[J]. Journal on Communications, 2022, 43(5): 110-122.
doi: 10.11959/j.issn.1000-436x.2022090 |
|
殷新春, 王梦宇, 宁建廷. 轻量级可搜索医疗数据共享方案[J]. 通信学报, 2022, 43(5):110-122.
doi: 10.11959/j.issn.1000-436x.2022090 |
|
| [17] | HU Yuanyuan, CHEN Yanli, ZHU Minhui. Privacy Protection Attribute-Based Ciphertext Search Scheme[J]. Application Research of Computers, 2019, 36(4): 1158-1164. |
| 胡媛媛, 陈燕俐, 朱敏惠. 可实现隐私保护的基于属性密文可搜索方案[J]. 计算机应用研究, 2019, 36(4):1158-1164. | |
| [18] | ZHANG Kai, LI Yanping, LU Laifeng. Privacy-Preserving Attribute-Based Keyword Search with Traceability and Revocation for Cloud-Assisted IoT[EB/OL]. (2021-05-30)[2024-04-23]. https://onlinelibrary.wiley.com/doi/10.1155/2021/9929663. |
| [19] | YANG Xiaodong, LI Ting, MA Tingchun, et al. Searchable Encryption Scheme Supporting Policy Hiding and Constant Ciphertext Length[J]. Journal of Electronics & Information Technology, 2021, 43(4): 900-907. |
| 杨小东, 李婷, 麻婷春, 等. 支持策略隐藏且密文长度恒定的可搜索加密方案[J]. 电子与信息学报, 2021, 43(4):900-907. | |
| [20] |
HUANG Baohua, HUANG Pirong, ZHAO Weihong, et al. Multi-Keyword Searchable Encryption Scheme Supporting Attribute Revocation in Cloud Storage[J]. Computer Engineering, 2021, 47(11): 29-36.
doi: 10.19678/j.issn.1000-3428.0061050 |
|
黄保华, 黄丕荣, 赵伟宏, 等. 云存储中支持属性撤销的多关键词可搜索加密方案[J]. 计算机工程, 2021, 47(11):29-36.
doi: 10.19678/j.issn.1000-3428.0061050 |
|
| [21] |
MIAO Yinbin, TONG Qiuyun, CHOO K K R, et al. Secure Online/Offline Data Sharing Framework for Cloud-Assisted Industrial Internet of Things[J]. IEEE Internet of Things Journal, 2019, 6(5): 8681-8691.
doi: 10.1109/JIOT.2019.2923068 |
| [22] |
HE Heng, ZHANG Ji, LI Peng, et al. A Lightweight Secure Conjunctive Keyword Search Scheme in Hybrid Cloud[J]. Future Generation Computer Systems, 2019, 93: 727-736.
doi: 10.1016/j.future.2018.09.026 |
| [23] |
SUN Jin, REN Lili, WANG Shangping, et al. Multi-Keyword Searchable and Data Verifiable Attribute-Based Encryption Scheme for Cloud Storage[J]. IEEE Access, 2019, 7: 66655-66667.
doi: 10.1109/ACCESS.2019.2917772 |
| [24] | MIAO Yinbin, MA Jianfeng, LIU Ximeng, et al. Attribute-Based Keyword Search over Hierarchical Data in Cloud Computing[J]. IEEE Transactions on Services Computing, 2020, 13(6): 985-998. |
| [25] | NIU Shufen, HAN Song, XIE Yaya, et al. Attribute-Based Searchable Encryption Scheme Supporting Multiple Keywords Based on Blockchain[J]. Journal of Cyber Security, 2023, 8(1): 131-143. |
| [26] |
FAN Yundong, WU Xiaoping. Cloud Storage Access Control Scheme Based on Policy Hiding Attribute Encryption[J]. Computer Engineering, 2018, 44(7): 139-144, 149.
doi: 10.19678/j.issn.1000-3428.0047699 |
|
范运东, 吴晓平. 基于策略隐藏属性加密的云存储访问控制方案[J]. 计算机工程, 2018, 44(7):139-144,149.
doi: 10.19678/j.issn.1000-3428.0047699 |
|
| [27] | GRAF T M, LEMIRE D. Xor Filters: Faster and Smaller than Bloom and Cuckoo Filters[J]. ACM Journal of Experimental Algorithmics, 2020, 25(1): 1-16. |
| [28] | YIN Hongjian, ZHAO Yiming, ZHANG Lei, et al. Attribute-Based Searchable Encryption with Decentralized Key Management for Healthcare Data Sharing[EB/OL]. (2020-01-27)[2024-04-23]. http://arxiv.org/abs/1912.08258v3. |
| [29] | LIU Jingwei, FAN Yue, SUN Rong, et al. Blockchain-Aided Privacy-Preserving Medical Data Sharing Scheme for E-Healthcare System[J]. IEEE Internet of Things Journal, 2023, 10(24): 21377-21388. |
| [1] | 周健聪, 朱晓杰, 陈驰. 基于比特切片的高效动态可搜索加密方案[J]. 信息网络安全, 2024, 24(9): 1309-1316. |
| [2] | 谢小凤, 张鑫涛, 王鑫, 鲁秀青. 基于云存储的多关键字可搜索加密方案[J]. 信息网络安全, 2024, 24(9): 1444-1457. |
| [3] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [4] | 李强, 沈援海, 刘天旭, 黄晏瑜, 孙建国. 面向尺寸模式保护的高效对称可搜索加密方案[J]. 信息网络安全, 2024, 24(6): 843-854. |
| [5] | 叶清, 何俊霏, 杨智超. 基于格的可搜索公钥加密研究进展[J]. 信息网络安全, 2024, 24(6): 903-916. |
| [6] | 王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527. |
| [7] | 刘芹, 王卓冰, 余纯武, 王张宜. 面向云安全的基于格的高效属性基加密方案[J]. 信息网络安全, 2023, 23(9): 25-36. |
| [8] | 石润华, 谢晨露. 云边缘环境中基于属性加密的可验证EMR外包解决方案[J]. 信息网络安全, 2023, 23(7): 9-21. |
| [9] | 秦宝东, ,陈从正, ,何俊杰, 郑东. 基于可验证秘密共享的多关键词可搜索加密方案[J]. 信息网络安全, 2023, 23(5): 32-40. |
| [10] | 李莉, 朱江文, 杨春艳. 基于属性加密的可撤销机制研究综述[J]. 信息网络安全, 2023, 23(4): 39-50. |
| [11] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [12] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [13] | 李家辉, 秦素娟, 高飞, 孙东旭. 基于属性加密的区块链组织交易可控可监管隐私保护方案[J]. 信息网络安全, 2023, 23(12): 103-112. |
| [14] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [15] | 张学旺, 姚亚宁, 黎志鸿, 张豪. 基于联盟链和Asmuth-Bloom秘密共享算法的数据共享方案[J]. 信息网络安全, 2022, 22(11): 17-23. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||