信息网络安全 ›› 2023, Vol. 23 ›› Issue (7): 9-21.doi: 10.3969/j.issn.1671-1122.2023.07.002
云边缘环境中基于属性加密的可验证EMR外包解决方案
- 华北电力大学控制与计算机工程学院,北京 102206
-
收稿日期:2023-04-20出版日期:2023-07-10发布日期:2023-07-14 -
通讯作者:谢晨露 E-mail:372238228@qq.com -
作者简介:石润华(1974—),男,安徽,教授,博士,主要研究方向为量子信息安全。|谢晨露(1997—),女,山东,硕士研究生,主要研究方向为数据外包加密与访问控制 -
基金资助:国家自然科学基金(61772001)
Verifiable Outsourcing EMR Scheme with Attribute-Based Encryption in Cloud-Edge Environments
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2023-04-20Online:2023-07-10Published:2023-07-14 -
Contact:XIE Chenlu E-mail:372238228@qq.com
摘要:
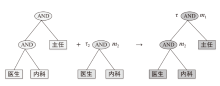
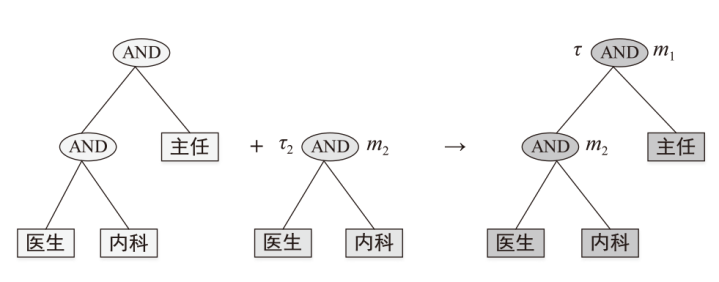
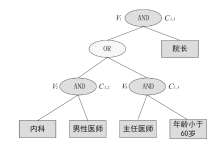
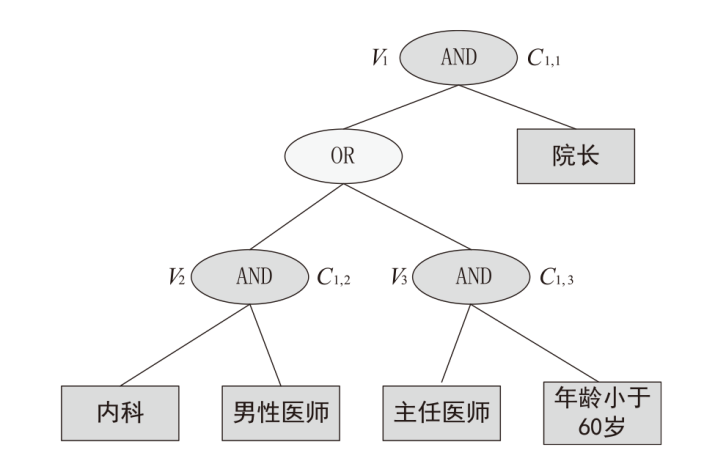
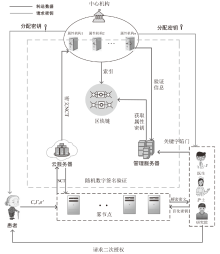
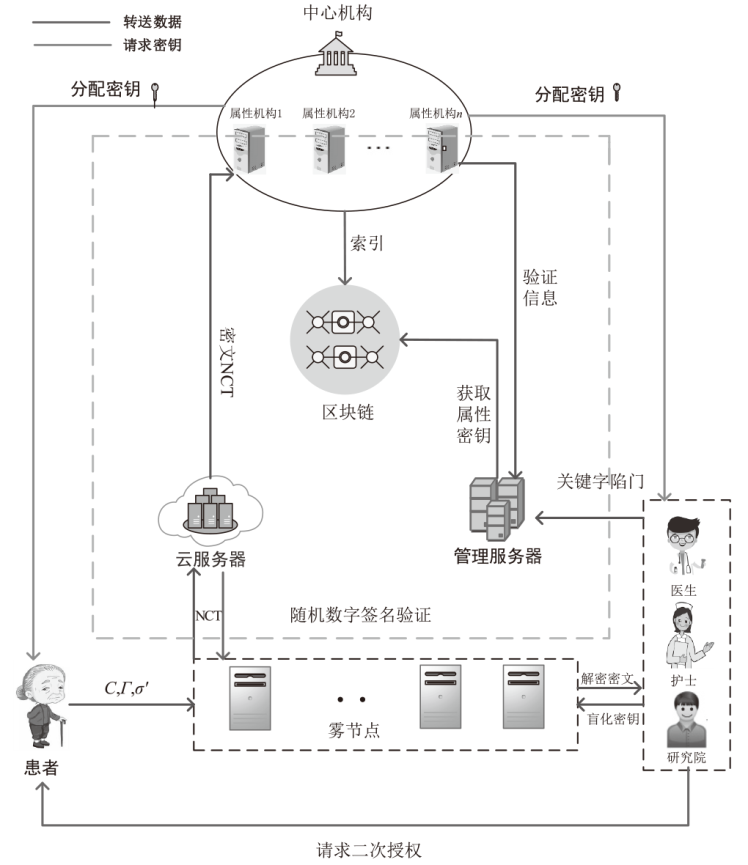
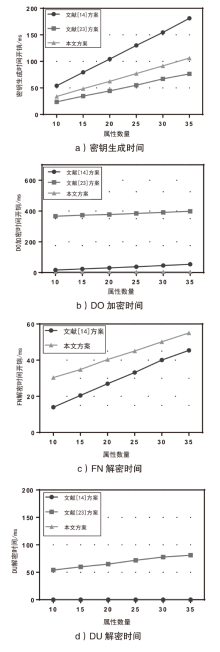
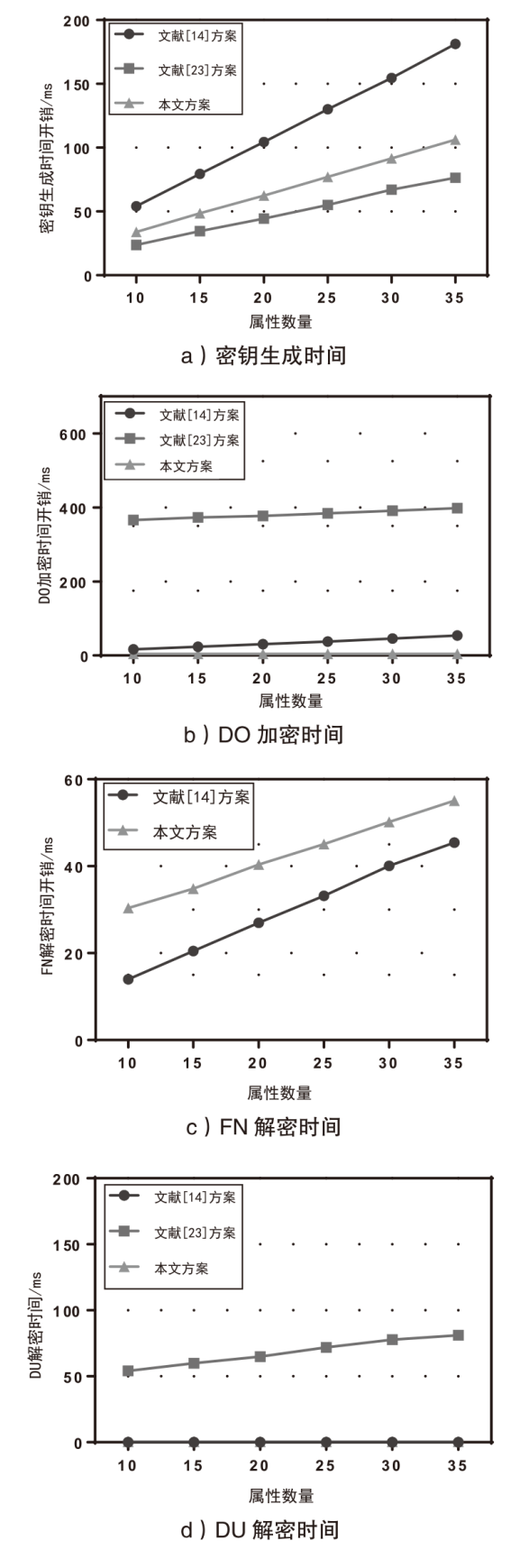
随着云计算和边缘计算的兴起,基于属性的加密(ABE)算法是一种很有应用价值的加密方法,它可以为云存储的电子病历(EMR)提供细粒度的访问控制策略。然而,在ABE中,访问控制越精细,所需属性的数量就越大,相应需要更高的加密计算成本。为了减轻数据拥有者的加密负担,文章设计了一种可验证的外包加密方案,其中数据拥有者侧雾节点完全负责ABE的加密计算,同时用户侧雾节点帮助合法的数据使用者执行相应的解密计算。此外,文章引入代理重加密以及在线索引与离线陷门技术,其中代理重加密实现电子病历的双重访问控制,而在线索引与离线陷门保证了合法用户的匿名性。最后,在区块链、管理服务器和属性机构的协助下,该方案能够验证雾节点外包加密和云存储密文的正确性。实验结果表明,该方案的数据拥有者加密时间最少,实现了减少数据拥有者加密负担,同时满足了细粒度访问控制和加密消息的可验证性。
中图分类号:
引用本文
石润华, 谢晨露. 云边缘环境中基于属性加密的可验证EMR外包解决方案[J]. 信息网络安全, 2023, 23(7): 9-21.
SHI Runhua, XIE Chenlu. Verifiable Outsourcing EMR Scheme with Attribute-Based Encryption in Cloud-Edge Environments[J]. Netinfo Security, 2023, 23(7): 9-21.
表1
符号说明
| 符号 | 含义表示 |
|---|---|
| 乘法循环群 | |
| 哈希函数 | |
| 属性集合 | |
| 生成元 | |
| 系统公钥 | |
| 系统私钥 | |
| 用户公钥、私钥 | |
| 属性主密钥 | |
| 用户属性密钥 | |
| 关键字 | |
| 关键字索引 | |
| DO计算的密文 | |
| 数字签名 | |
| DO公钥加密后得到的密文 | |
| FN属性加密后得到的密文 | |
| 陷门 | |
| 盲化后的属性密钥 | |
| 验证数字签名时生成的验证信息 | |
| MS计算数字签名得到的验证证明 | |
| 重加密密钥 | |
| 重加密密文 |
表3
性能对比
| 功能 | 方案名称 | ||
|---|---|---|---|
| 文献[14]方案 | 文献[23]方案 | 本文方案 | |
| 密钥生成 | |||
| DO加密 | |||
| FN加密 | — | — | |
| 数字签名 | — | — | |
| DU解密 | 3(Ee+E2) | ||
| FN解密 | — | ||
表4
存储开销对比
| 方案开销 | 文献[14]方案 | 文献[23]方案 | 本文方案 |
|---|---|---|---|
| 密文存储 开销 | |||
| 密钥存储 开销 |
| [1] |
ZAGHLOUL E, LI Tongtong, MUTKA W, et al. dd-MABE: Distributed Multilevel Attribute-Based EMR Management and Applications[J]. IEEE Transactions on Services Computing, 2022, 15(5): 1592-1605.
doi: 10.1109/TSC.2020.3003321 URL |
| [2] |
QIN Baodong, DENG R H, LIU Shengli, et al. Attribute-Based Encryption with Efficient Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(7): 1384-1393.
doi: 10.1109/TIFS.2015.2410137 URL |
| [3] | LENG Jiewu, RUAN Guolei, JIANG Pingyu, et al. Blockchain-Empowered Sustainable Manufacturing and Product Lifecycle Management in Industry 4.0: A Survey[EB/OL]. (2020-07-28) [2023-03-22]. https://www.sciencedirect.com/science/article/abs/pii/S1364032120304032. |
| [4] | QING Yong, SUN Wei, XIONG Hu, et al. Outsourcing Encryption and Decryption CP-ABE Scheme with Revocation Storage in Cloud Computing[J]. Netinfo Security, 2017, 17(6): 6-13. |
| 卿勇, 孙伟, 熊虎, 等. 云计算中可撤销存储的外包加解密CP-ABE方案[J]. 信息网络安全, 2017, 17(6)6-13. | |
| [5] |
ZHONG Hong, ZHOU Yiyuan, ZHANG Qingyang, et al. An Efficient and Outsourcing-Supported Attribute-Based Access Control Scheme for Edge-Enabled Smart Healthcare[J]. Future Generation Computer Systems, 2021, 115: 486-496.
doi: 10.1016/j.future.2020.09.021 URL |
| [6] |
LI Xuejun, ZHANG Dan, LI Hui. Efficient Revocable Attribute-Based Encryption Scheme[J]. Journal on Communications, 2019, 40(6): 32-39.
doi: 10.11959/j.issn.1000-436x.2019150 |
|
李学俊, 张丹, 李晖. 可高效撤销的属性基加密方案[J]. 通信学报, 2019, 40(6): 32-39.
doi: 10.11959/j.issn.1000-436x.2019150 |
|
| [7] | MA Min, FU Yu, HUANG Kai. A Principal Component Analysis Scheme for Security Outsourcing in Cloud Environment Based on Secret Sharing[J]. Netinfo Security, 2023, 23(4): 61-71. |
| 马敏, 付钰, 黄凯. 云环境下基于秘密共享的安全外包主成分分析方案[J]. 信息网络安全, 2023, 23(4): 61-71. | |
| [8] |
HOU Yichen, SAHIL G, HUI Lin, et al. A Data Security Enhanced Access Control Mechanism in Mobile Edge Computing[J]. IEEE Access, 2020, 8: 136119-136130.
doi: 10.1109/Access.6287639 URL |
| [9] | WANG Shulan, WANG Haiyan, LI Jianqiang, et al. A Fast CP-ABE System for Cyber-Physical Security and Privacy in Mobile Healthcare Network[J]. IEEE Transactions on Industry Applications, 2020, 56(4): 4467-4477. |
| [10] |
ZHANG Yinghui, ZHENG Dong, DENG R H. Security and Privacy in Smart Health: Efficient Policy-Hiding Attribute-Based Access Control[J]. IEEE Internet of Things Journal, 2018, 5(3): 2130-2145.
doi: 10.1109/JIOT.2018.2825289 URL |
| [11] |
XUE Yingjie, XUE Kaiping, GAI Na, et al. An Attribute-Based Controlled Collaborative Access Control Scheme for Public Cloud Storage[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(11): 2927-2942.
doi: 10.1109/TIFS.10206 URL |
| [12] | ZHOU Zhibing, HUANG Dijiang. Efficient and Secure Data Storage Operations for Mobile Cloud Computing[C]// IEEE. 2012 8th International Conference on Network and Service Management and 2012 Workshop on Systems Virtualiztion Management. New York: IEEE, 2012: 37-45. |
| [13] | ASIM M, PETKOVIC M, IGNATENKO T. Attribute-Based Encryption with Encryption and Decryption Outsourcing[EB/OL]. [2023-03-22]. https://ro.ecu.edu.au/cgi/viewcontent.cgi?article=1163&context=ism. |
| [14] |
LIN Suqing, ZHANG Rui, HUI Ma, et al. Revisiting Attribute-Based Encryption with Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(10): 2119-2130.
doi: 10.1109/TIFS.2015.2449264 URL |
| [15] | ATALLAH M, PANTAZOPOULOS K, RICE J, et al. Secure Outsourcing of Scientific Computations[J]. Trends in Software Engineering, 2002, 54: 215-272. |
| [16] | BENJAMIN D, ATALLAH M. Private and Cheating-Free Outsourcing of Algebraic Computations[C]// IEEE. Proceedings of the 6th Annual Conference on Privacy, Security and Trust. New York: IEEE, 2008: 240-245. |
| [17] | ZHAO Zhiyuan, WANG Jianhua, XU Kaiyong, et al. Fully Outsourced Attribute-Based Encryption with Verifiability for Cloud Storage[J]. Journal of Computer Research and Development, 2019, 56(2): 442-452. |
| 赵志远, 王建华, 徐开勇, 等. 面向云存储的支持完全外包属性基加密方案[J]. 计算机研究与发展, 2019, 56(2): 442-452. | |
| [18] | LENG Qingsong, LUO Wangping. Attribute-Based Encryption with Outsourced Encryption[J]. Communications Technology, 2021, 54(9): 2242-2246. |
| 冷青松, 罗王平. 支持加密外包的基于属性加密方案[J]. 通信技术, 2021, 54(9): 2242-2246. | |
| [19] | WU Zhiwei. Privacy Protection and Data Sharing Schemes Based on Edge Computing in Smart Grid[D]. Beijing: North China Electric Power University, 2022. |
| 吴志伟. 智能电网中基于边缘计算的隐私保护与数据共享方案[D]. 北京: 华北电力大学, 2022. | |
| [20] |
WANG Shulan, ZHOU Junwei, LIU J K, et al. An Efficient File Hierarchy Attribute-Based Encryption Scheme in Cloud Computing[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(6): 1265-1277.
doi: 10.1109/TIFS.2016.2523941 URL |
| [21] |
ZHANG Zhiyong, LI Cheng, GBB, et al. Efficient Compressed Ciphertext Length Scheme Using Multi-Authority CP-ABE for Hierarchical Attributes[J]. IEEE Access, 2018, 6: 38273-38284.
doi: 10.1109/ACCESS.2018.2854600 URL |
| [22] |
GUO Rui, LI Xiong, ZHENG Dong, et al. An Attribute-Based Encryption Scheme with Multiple Authorities on Hierarchical Personal Health Record in Cloud[J]. The Journal of Supercomputing, 2020, 76(7):4884-4903.
doi: 10.1007/s11227-018-2644-7 |
| [23] |
LI Jiguo, CHEN Ningyu, ZHANG Yichen. Extended File Hierarchy Access Control Scheme with Attribute-Based Encryption in Cloud Computing[J]. IEEE Transactions on Emerging Topics in Computing, 2021, 9(2): 983-993.
doi: 10.1109/TETC.2019.2904637 URL |
| [24] |
BONEH D, FRANKLIN M. Identity-Based Encryption from the Weil Paring[J]. SIAM Journal on Computing, 2003, 32(3): 586-615.
doi: 10.1137/S0097539701398521 URL |
| [1] | 刘芹, 王卓冰, 余纯武, 王张宜. 面向云安全的基于格的高效属性基加密方案[J]. 信息网络安全, 2023, 23(9): 25-36. |
| [2] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [3] | 张晓旭, 石润华. EHR系统中一种验证外包加密数据正确性的访问控制方案[J]. 信息网络安全, 2023, 23(5): 85-94. |
| [4] | 李莉, 朱江文, 杨春艳. 基于属性加密的可撤销机制研究综述[J]. 信息网络安全, 2023, 23(4): 39-50. |
| [5] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [6] | 李家辉, 秦素娟, 高飞, 孙东旭. 基于属性加密的区块链组织交易可控可监管隐私保护方案[J]. 信息网络安全, 2023, 23(12): 103-112. |
| [7] | 朱怡昕, 苗张旺, 甘静鸿, 马存庆. 基于细粒度访问控制的勒索软件防御系统设计[J]. 信息网络安全, 2023, 23(10): 31-38. |
| [8] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [9] | 郭宝霞, 王佳慧, 马利民, 张伟. 基于零信任的敏感数据动态访问控制模型研究[J]. 信息网络安全, 2022, 22(6): 86-93. |
| [10] | 刘嘉微, 马兆丰, 王姝爽, 罗守山. 基于区块链的隐私信用数据受限共享技术研究[J]. 信息网络安全, 2022, 22(5): 54-63. |
| [11] | 张学旺, 姚亚宁, 黎志鸿, 张豪. 基于联盟链和Asmuth-Bloom秘密共享算法的数据共享方案[J]. 信息网络安全, 2022, 22(11): 17-23. |
| [12] | 李桐, 任帅, 王刚, 孟庆宇. 基于变色龙认证树的云边端协同流式数据完整性验证模型[J]. 信息网络安全, 2022, 22(1): 37-45. |
| [13] | 靳姝婷, 何泾沙, 朱娜斐, 潘世佳. 基于本体推理的隐私保护访问控制机制研究[J]. 信息网络安全, 2021, 21(8): 52-61. |
| [14] | 沈卓炜, 高鹏, 许心宇. 基于安全协商的DDS安全通信中间件设计[J]. 信息网络安全, 2021, 21(6): 19-25. |
| [15] | 芦效峰, 付淞兵. 属性基加密和区块链结合的可信数据访问控制方案[J]. 信息网络安全, 2021, 21(3): 7-8. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||