信息网络安全 ›› 2025, Vol. 25 ›› Issue (5): 732-746.doi: 10.3969/j.issn.1671-1122.2025.05.006
基于静态分析的价格预言机操纵源代码检测方法研究
- 中国科学技术大学计算机科学与技术学院,合肥 230026
-
收稿日期:2024-04-29出版日期:2025-05-10发布日期:2025-06-10 -
通讯作者:薛吟兴yxxue@ustc.edu.cn -
作者简介:叶佳骏(1999—),男,广东,硕士研究生,主要研究方向为区块链智能合约安全|高翠凤(1997—),女,河北,博士研究生,CCF会员,主要研究方向为区块链智能合约安全|薛吟兴(1982—),男,江苏,研究员,博士,CCF会员,主要研究方向为软件工程、网络安全、软件安全 -
基金资助:国家自然科学基金(61972373);江苏省基础研究计划(自然科学基金)面上项目(BK20201192)
Research on Price Oracle Manipulation Source Code Detection Method Based on Static Analysis
YE Jiajun, GAO Cuifeng, XUE Yinxing( )
)
- Department of Computer Science and Technology, University of Science and Technology of China, Hefei 230026, China
-
Received:2024-04-29Online:2025-05-10Published:2025-06-10
摘要:
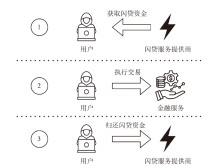
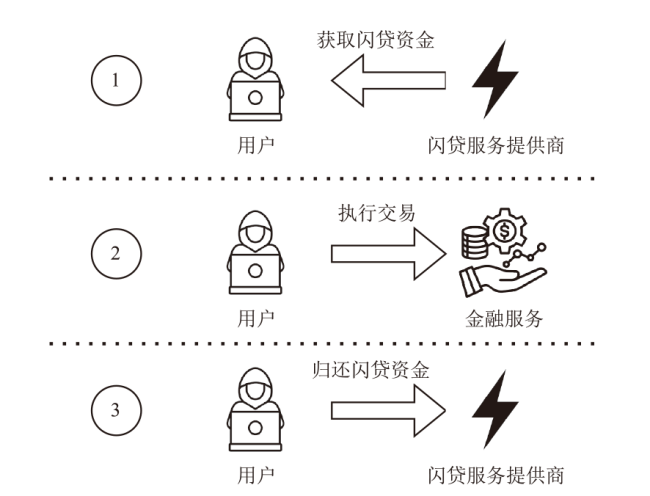
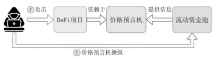
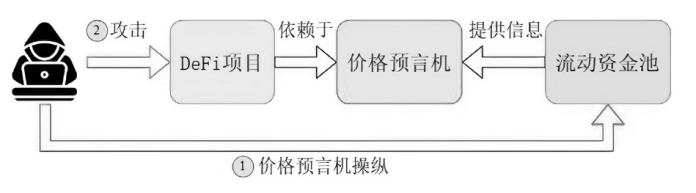
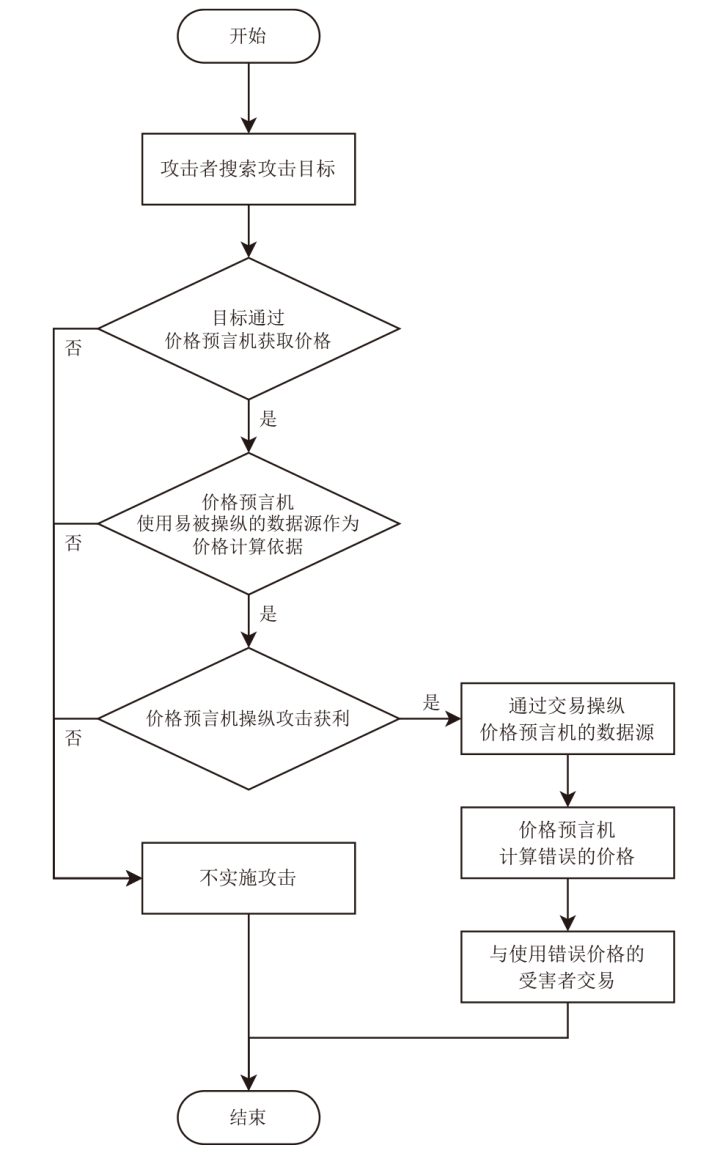
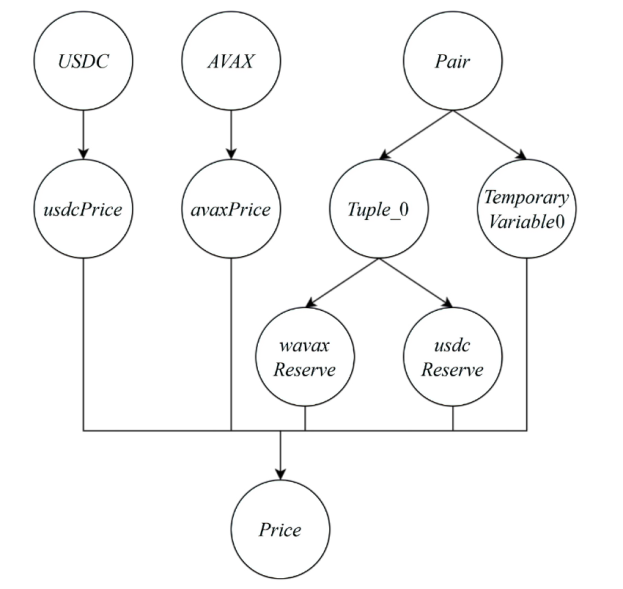
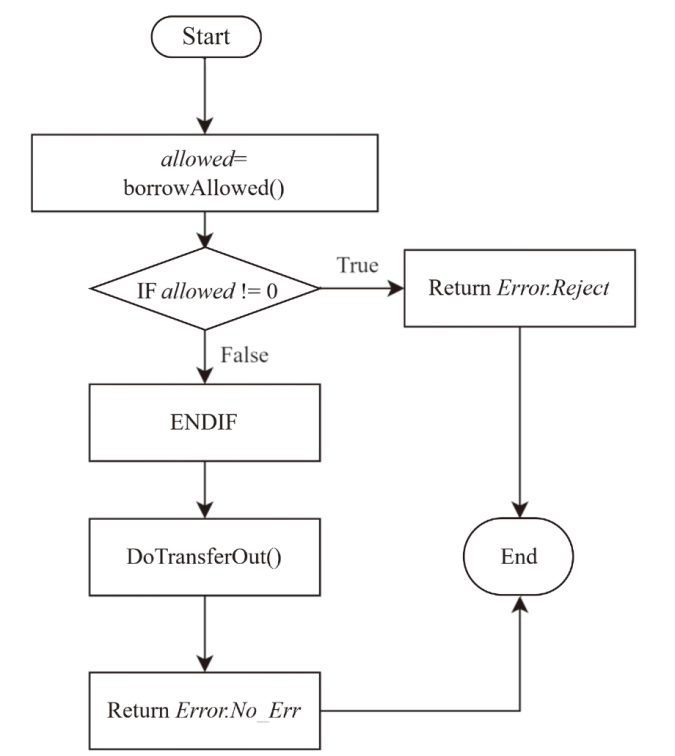
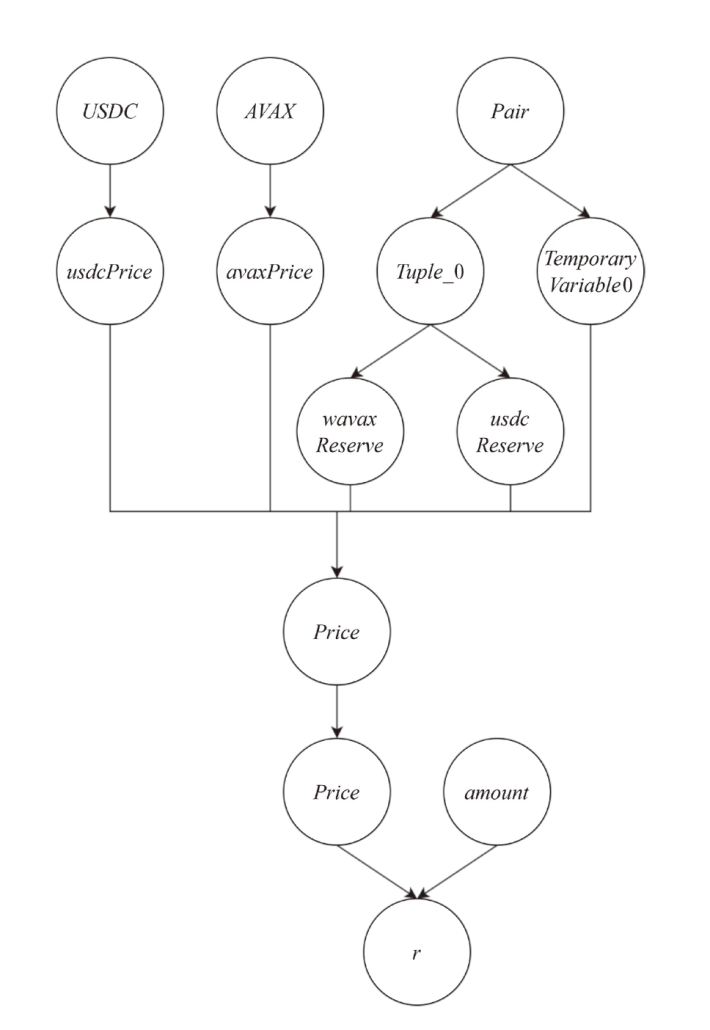
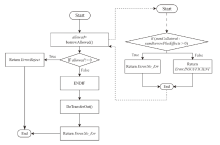
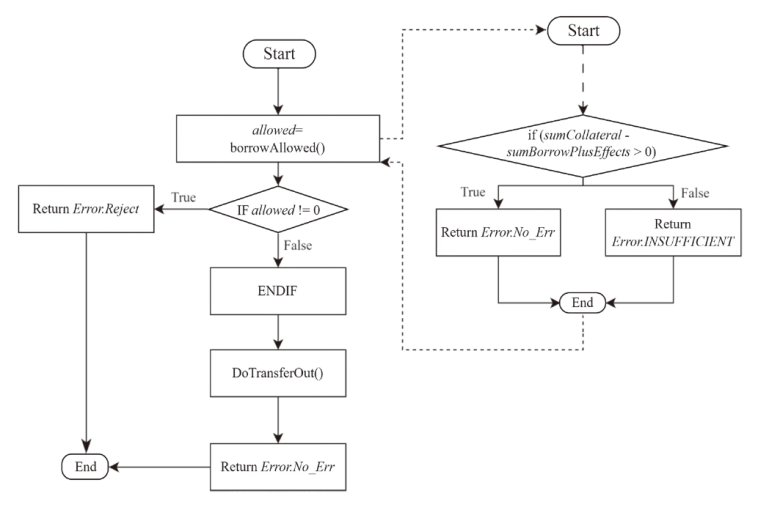
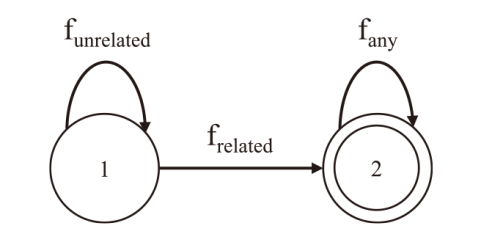
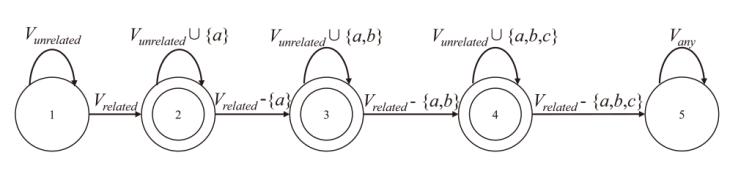
针对智能合约的价格预言机操纵攻击问题,文章提出一种基于静态分析的价格预言机操纵源代码检测方法。该方法首先根据用户输入的函数调用关系,建立调用者函数的变量和被调函数的参数之间的对应关系,以及被调函数返回值和调用者函数的变量之间的对应关系。其次,对被测函数的源代码及其实际运行时涉及的其他合约源代码进行静态分析,获取每个合约的数据流和控制流信息。然后,通过整合单个合约的数据流信息、控制流信息以及函数调用关系,构建跨合约的数据流图和控制流图,从而获取变量的数据依赖和控制依赖关系。最后,通过检测转账操作中的转账金额以及转账操作中存在控制依赖的控制语句是否使用少量容易被操纵的信息,来判断被测合约是否存在价格预言机操纵风险。实验结果表明,该方法能有效检测智能合约中的价格预言机操纵攻击,具有较高的精确率和召回率。
中图分类号:
引用本文
叶佳骏, 高翠凤, 薛吟兴. 基于静态分析的价格预言机操纵源代码检测方法研究[J]. 信息网络安全, 2025, 25(5): 732-746.
YE Jiajun, GAO Cuifeng, XUE Yinxing. Research on Price Oracle Manipulation Source Code Detection Method Based on Static Analysis[J]. Netinfo Security, 2025, 25(5): 732-746.
| [1] | BUTERIN V. A Next-Generation Smart Contract and Decentralized Application Platform[J]. White Paper, 2014, 3(37): 1-36. |
| [2] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. [2024-04-10]. https://bitcoin.org/en/bitcoin-paper. |
| [3] | DefiLlama. DeFi Dashboard[EB/OL]. (2024-03-20)[2024-04-10]. https://defillama.com/. |
| [4] | SZABO N. Formalizing and Securing Relationships on Public Networks[J]. First Monday, 1997, 2(9): 1-25. |
| [5] | BARTOLETTI M, POMPIANU L. An Empirical Analysis of Smart Contracts:Platforms, Applications, and Design Patterns[C]// Springer. Financial Cryptography and Data Security. Heidelberg: Springer, 2017: 494-509. |
| [6] | MEHAR M I, SHIER C L, GIAMBATTISTA A, et al. Understanding a Revolutionary and Flawed Grand Experiment in Blockchain[J]. Journal of Cases on Information Technology, 2019, 21(1): 19-32. |
| [7] | QIAN Peng, LIU Zhenguang, HE Qinming, et al. Smart Contract Vulnerability Detection Technique: A Survey[J]. Journal of Software, 2022, 33(8): 3059-3085. |
| 钱鹏, 刘振广, 何钦铭, 等. 智能合约安全漏洞检测技术研究综述[J]. 软件学报, 2022, 33(8):3059-3085. | |
| [8] | ZHANG Zhuo, ZHANG B, XU Wen, et al. Demystifying Exploitable Bugs in Smart Contracts[C]// IEEE. 2023 IEEE/ACM 45th International Conference on Software Engineering (ICSE). New York: IEEE, 2023: 615-627. |
| [9] | WU Siwei, WANG Dabao, HE Jianting, et al. DeFiRanger: Detecting Price Manipulation Attacks on DeFi Applications[EB/OL]. (2021-04-30)[2024-04-10]. https://arxiv.org/abs/2104.15068v1. |
| [10] | ZHANG Wuqi, WEI Lili, CHEUNG S C, et al. Combatting Front-Running in Smart Contracts: Attack Mining, Benchmark Construction and Vulnerability Detector Evaluation[J]. IEEE Transactions on Software Engineering, 2023, 49(6): 3630-3646. |
| [11] | QIN Kaihua, ZHOU Liyi, LIVSHITS B, et al. Attacking the DeFi Ecosystem with Flash Loans for Fun and Profit[C]// Springer. Financial Cryptography and Data Security. Heidelberg: Springer, 2021: 3-32. |
| [12] | DONG Weiliang, LIU Zhe, LIU Kui, et al. Survey on Vulnerability Detection Technology of Smart Contracts[J]. Journal of Software, 2024, 35(1): 38-62. |
| 董伟良, 刘哲, 刘逵, 等. 智能合约漏洞检测技术综述[J]. 软件学报, 2024, 35(1): 38-62. | |
| [13] | ALMAKHOUR M, SLIMAN L, SAMHAT A E, et al. Verification of Smart Contracts: A Survey[EB/OL]. (2019-06-10)[2024-04-10]. https://doi.org/10.1016/j.pmcj.2020.101227. |
| [14] | LUU L, CHU D H, OLICKEL H, et al. Making Smart Contracts Smarter[C]// ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 254-269. |
| [15] | GRIECO G, SONG W, CYGAN A, et al. Echidna:Effective, Usable, and Fast Fuzzing for Smart Contracts[C]// ACM. Proceedings of the 29th ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2020: 557-560. |
| [16] | CHESS B, MCGRAW G. Static Analysis for Security[J]. IEEE Security & Privacy, 2004, 2(6): 76-79. |
| [17] | SCHNEIDEWIND C, GRISHCHENKO I, SCHERER M, et al. EThor: Practical and Provably Sound Static Analysis of Ethereum Smart Contracts[C]// ACM. Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2020: 621-640. |
| [18] | TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I, et al. SmartCheck: Static Analysis of Ethereum Smart Contracts[C]// IEEE. 2018 IEEE/ACM 1st International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB). New York: IEEE, 2018: 9-16. |
| [19] | FEIST J, GRIECO G, GROCE A. Slither: A Static Analysis Framework for Smart Contracts[C]// IEEE. 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB). New York: IEEE, 2019: 8-15. |
| [20] | CYTRON R, FERRANTE J, ROSEN B K, et al. Efficiently Computing Static Single Assignment Form and the Control Dependence Graph[J]. ACM Transactions on Programming Languages and Systems, 1991, 13(4): 451-490. |
| [21] | ABDELAZIZ T, HOBOR A. Smart Learning to Find Dumb Contracts (Extended Version)[EB/OL]. (2023-06-27)[2024-04-10]. https://arxiv.org/abs/2304.10726v2. |
| [22] | TJIAM K, WANG Rui, CHEN Huanhuan, et al. Your Smart Contracts are Not Secure: Investigating Arbitrageurs and Oracle Manipulators in Ethereum[C]// ACM. Proceedings of the 3rd Workshop on Cyber-Security Arms Race. New York: ACM, 2021: 25-35. |
| [23] | WANG S H, WU C C, LIANG Yuchuan, et al. ProMutator: Detecting Vulnerable Price Oracles in DeFi by Mutated Transactions[C]// IEEE. 2021 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW). New York: IEEE, 2021: 380-385. |
| [24] | DENG Xun, BEILLAHI S M, MINWALLA C, et al. Safeguarding DeFi Smart Contracts against Oracle Deviations[C]// ACM. Proceedings of the IEEE/ACM 46th International Conference on Software Engineering. New York: ACM, 2024: 1-12. |
| [25] | Tintinweb. Smart Contract Sanctuary[EB/OL]. (2024-03-20)[2024-04-10]. https://github.com/tintinweb/smart-contract-sanctuary.git/. |
| [1] | 杨亚涛, 丁渝诚, 刘培鹤, 桑鹏. 基于区块链的隐私保护和数字认证研究[J]. 信息网络安全, 2025, 25(4): 640-653. |
| [2] | 张雨轩, 黄诚, 柳蓉, 冷涛. 结合提示词微调的智能合约漏洞检测方法[J]. 信息网络安全, 2025, 25(4): 664-673. |
| [3] | 张立强, 路梦君, 严飞. 一种基于函数依赖的跨合约模糊测试方案[J]. 信息网络安全, 2024, 24(7): 1038-1049. |
| [4] | 刘峰, 江佳齐, 黄灏. 面向加密货币交易介质及过程的安全综述[J]. 信息网络安全, 2024, 24(3): 330-351. |
| [5] | 许良晨, 孟昭逸, 黄文超, 熊焰. 面向程序可达性验证的数组处理循环压缩方法[J]. 信息网络安全, 2024, 24(3): 374-384. |
| [6] | 李鹏超, 张全涛, 胡源. 基于双注意力机制图神经网络的智能合约漏洞检测方法[J]. 信息网络安全, 2024, 24(11): 1624-1631. |
| [7] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [8] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [9] | 陈星任, 熊焰, 黄文超, 付贵禄. 一种基于静态分析的多视图硬件木马检测方法[J]. 信息网络安全, 2023, 23(10): 48-57. |
| [10] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [11] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [12] | 张玉健, 刘代富, 童飞. 基于局部图匹配的智能合约重入漏洞检测方法[J]. 信息网络安全, 2022, 22(8): 1-7. |
| [13] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [14] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [15] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||