信息网络安全 ›› 2021, Vol. 21 ›› Issue (11): 58-64.doi: 10.3969/j.issn.1671-1122.2021.11.007
轻量化移动边缘计算双向认证协议
- 1.东北大学计算机科学与工程学院,沈阳 110169
2.国网辽宁省电力有限公司电力科学研究院,沈阳 110003
3.国网辽宁省电力有限公司,沈阳 110003
4.东北大学软件学院,沈阳 110169
-
收稿日期:2021-06-13出版日期:2021-11-10发布日期:2021-11-24 -
通讯作者:周小明 E-mail:271337328@qq.com -
作者简介:李桐(1990—),男,辽宁,工程师,博士,主要研究方向为电力系统网络安全|周小明(1978—),男,黑龙江,高级工程师,博士,主要研究方向为网络安全|任帅(1989—),男,辽宁,工程师,硕士,主要研究方向为信息安全|徐剑(1978—),男,辽宁,副教授,博士,主要研究方向为网络与信息安全 -
基金资助:工信部工业企业网络安全综合防护平台项目-物联网终端虚拟化与安全验证技术研究(TC200H01V)
Light-weight Mutual Authentication Protocol for Mobile Edge Computing
LI Tong1,2, ZHOU Xiaoming3( ), REN Shuai2, XU Jian4
), REN Shuai2, XU Jian4
- 1. School of Computer Science and Engineering, Northeastern University, Shenyang 110169
2. China State Grid Liaoning Electric Power Research Institute, Shenyang 110003, China
3. Grid Liaoning Electric Power Supply Co., LTD, Shenyang 110003, China
4. Software College, Northeastern University, Shenyang 110169, China
-
Received:2021-06-13Online:2021-11-10Published:2021-11-24 -
Contact:ZHOU Xiaoming E-mail:271337328@qq.com
摘要:
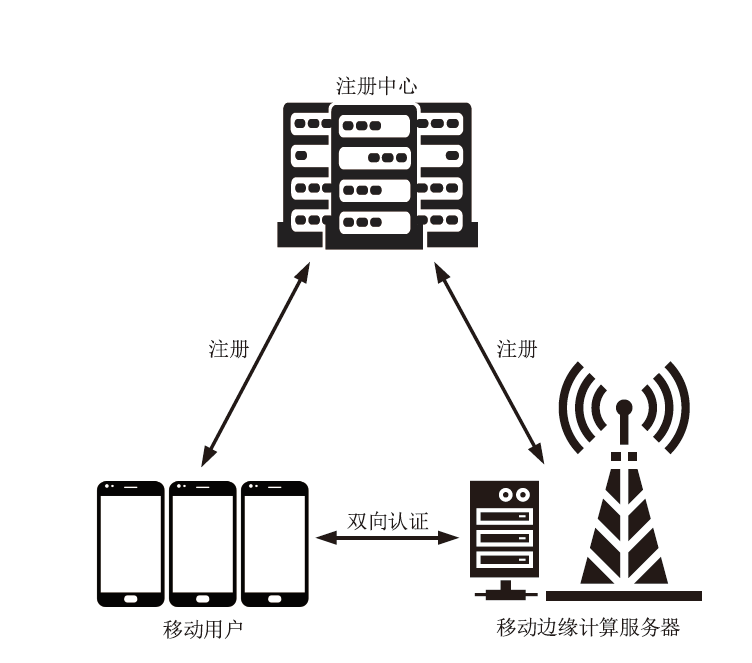
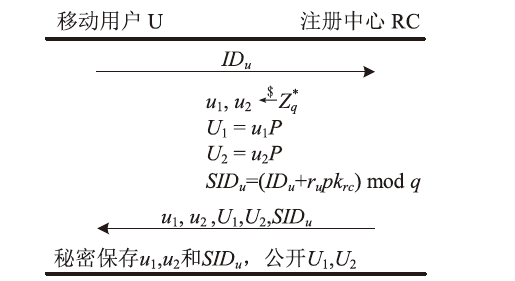
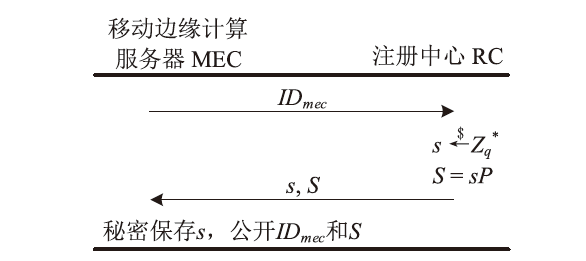
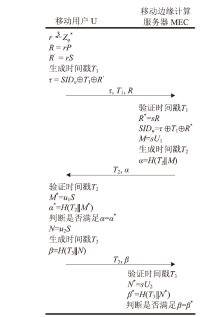
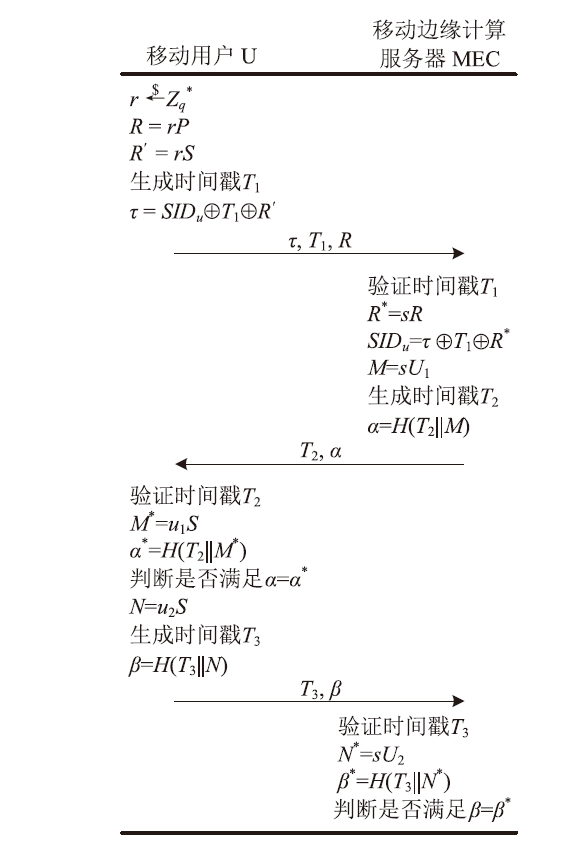
移动边缘计算是一种新型计算模式,通过部署靠近数据源头的移动边缘计算服务器,可以满足移动智能设备的实时业务、数据优化、应用智能等需求。文章针对移动边缘计算场景中移动设备和移动边缘计算服务器之间的安全身份认证问题,提出了一种基于椭圆曲线加密的轻量化移动边缘计算双向认证协议。该协议使用椭圆曲线加密和哈希函数构建,满足双向认证、移动用户匿名保护、移动用户不可追踪等特性,同时可以抵抗重放攻击和中间人攻击等多种攻击手段。通过性能分析及与同类协议的对比表明,协议的整体计算开销较低,适用于计算资源受限的移动智能设备。
中图分类号:
引用本文
李桐, 周小明, 任帅, 徐剑. 轻量化移动边缘计算双向认证协议[J]. 信息网络安全, 2021, 21(11): 58-64.
LI Tong, ZHOU Xiaoming, REN Shuai, XU Jian. Light-weight Mutual Authentication Protocol for Mobile Edge Computing[J]. Netinfo Security, 2021, 21(11): 58-64.
使用本文
| [1] | XU Jia, WEI Laiwen, WU Wei, et al. Privacy-preserving Data Integrity Verification by Using Lightweight Streaming Authenticated Data Structures For Healthcare Cyber-physical System[J]. Future Generation Computer Systems, 2020, 36(108):1287-1296. |
| [2] |
ZHAO Zichao, ZHAO Rui, XIA Junjuan, et al. A Novel Framework of Three-hierarchical Offloading Optimization for MEC in Industrial IoT Networks[J]. IEEE Transactions on Industrial Informatics, 2020, 16(8):5424-5434.
doi: 10.1109/TII.9424 URL |
| [3] | SHI Weisong, SUN Hui, CAO Jie, et al. Edge Computing: An Emerging Computing Model for the Internet of Everything Era[J]. Journal of Computer Research and Development, 2017, 54(5):907-924. |
| 施巍松, 孙辉, 曹杰, 等. 边缘计算:万物互联时代新计算模型[J]. 计算机研究与发展, 2017, 54(5):907-924. | |
| [4] | CAMHI J. Former Cisco CEO John Chambers Predicts 500 Billion Connected Devices by 2015[EB/OL]. https://www.cisco.com, 2020-07-20. |
| [5] | XU Xiaolong, LIU Qingxiang, LUO Yun, et al. A Computation Offloading Method over Big Data for IoT-enabled Cloud-edge Computing[J]. Future Generation Computer Systems, 2019, 35(95):522-533. |
| [6] |
CHETTRI L, BERA R. A Comprehensive Survey on Internet of Things (IoT) Toward 5G Wireless Systems[J]. IEEE Internet of Things Journal, 2020, 7(1):16-32.
doi: 10.1109/JIoT.6488907 URL |
| [7] |
LI Zhenlong, YANG Chaowei, HU Fei, et al. Big Data and Cloud Computing: Innovation Opportunities and Challenges[J]. International Journal of Digital Earth, 2017, 10(1):13-53.
doi: 10.1080/17538947.2016.1239771 URL |
| [8] |
WANG Tian, QIU Lei, SANGAIAH A K, et al. Edge-computing-based Trustworthy Data Collection Model in the Internet of Things[J]. IEEE Internet of Things Journal, 2020, 7(5):4218-4227.
doi: 10.1109/JIoT.6488907 URL |
| [9] | KHAN WZ, AHMED E, HAKAK S, et al. Edge Computing: A Survey[J]. Future Generation Computer Systems. 2019, 35(97):219-235. |
| [10] | LÜ Huazhang, CHEN Dan, FAN Bin, et al. Standardization Progress and Case Analysis of Edge Computing[J]. Journal of Computer Research and Development, 2018, 55(3):487-511. |
| 吕华章, 陈丹, 范斌, 等. 边缘计算标准化进展与案例分析[J]. 计算机研究与发展, 2018, 55(3):487-511. | |
| [11] |
ABBAS N, ZHANG Yan, TAHERKORDI A, et al. Mobile Edge Computing: A Survey[J]. IEEE Internet of Things Journal, 2018, 5(1):450-465.
doi: 10.1109/JIOT.2017.2750180 URL |
| [12] | ZHOU Yuezhi, ZHANG Di. Near-end Cloud Computing: Opportunities and Challenges in the Post-cloud Computing Era[J]. Chinese Journal of Computers, 2019, 42(4):677-700. |
| 周悦芝, 张迪. 近端云计算:后云计算时代的机遇与挑战[J]. 计算机学报, 2019, 42(4):677-700. | |
| [13] | ZHOU Jun, SHEN Huajie, LIN Zhongyun, et al. Research Advances on Privacy Preserving in Edge Computing[J]. Journal of Computer Research and Development, 2020, 57(10):2027-2051. |
| 周俊, 沈华杰, 林中允, 等. 边缘计算隐私保护研究进展[J]. 计算机研究与发展, 2020, 57(10):2027-2051. | |
| [14] | MILLER V S. Use of Elliptic Curves in Cryptography[C]// Springer. Conference on the Theory and Application of Cryptographic Techniques, August 18-22, Santa Barbara, CA, USA. Berlin: Springer, 1985: 417-426. |
| [15] | ZHAO Guanglei, SI Xianping, WANG Jingchang, et al. A Novel Mutual Authentication Scheme for Internet of Things[C]// IEEE. International Conference on Modelling, Identification and Control, Identification and Control, June 26-29, 2011, Shanghai, China. CA, USA: IEEE, 2011: 563-566. |
| [16] | SHEN Guicheng, YU Zhen. Application of Elliptic Curve Cryptography in Node Authentication of Internet of Things[C]// IEEE. Ninth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, October 16-18, 2013, Beijing, China. CA, USA: IEEE, 2013: 452-455. |
| [17] |
TSAI J L, LO N W. A Privacy-aware Authentication Scheme for Distributed Mobile Cloud Computing Services[J]. IEEE Systems Journal, 2015, 9(3):805-815.
doi: 10.1109/JSYST.2014.2322973 URL |
| [18] | IRSHAD A, SHER M, AHMAD H F, et al. An improved Multi-server Authentication Scheme for Distributed Mobile Cloud Computing Services[J]. TIIS, 2016, 10(12):5529-5552. |
| [19] | AMAN M N, CHUA K C, SIKDAR B. A Light-weight Mutual Authentication Protocol for IoT Systems[C]// IEEE. IEEE Global Communications Conference, December 4-8, 2017, Singapore, Institute of Electrical and Electronics Engineers Inc. CA, USA: IEEE, 2017: 1-6. |
| [1] | 陈庆港, 杜彦辉, 韩奕, 刘翔宇. 基于深度可分离卷积的物联网设备识别模型[J]. 信息网络安全, 2021, 21(9): 67-73. |
| [2] | 吴克河, 程瑞, 郑碧煌, 崔文超. 电力物联网安全通信协议研究[J]. 信息网络安全, 2021, 21(9): 8-15. |
| [3] | 路宏琳, 王利明, 杨婧. 一种新的参数掩盖联邦学习隐私保护方案[J]. 信息网络安全, 2021, 21(8): 26-34. |
| [4] | 靳姝婷, 何泾沙, 朱娜斐, 潘世佳. 基于本体推理的隐私保护访问控制机制研究[J]. 信息网络安全, 2021, 21(8): 52-61. |
| [5] | 李群, 董佳涵, 关志涛, 王超. 一种基于聚类分类的物联网恶意攻击检测方法[J]. 信息网络安全, 2021, 21(8): 82-90. |
| [6] | 刘忻, 杨浩睿, 郭振斌, 王家寅. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7): 1-9. |
| [7] | 刘忻, 郭振斌, 宋宇宸. 一种基于SGX的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(6): 1-10. |
| [8] | 沈卓炜, 高鹏, 许心宇. 基于安全协商的DDS安全通信中间件设计[J]. 信息网络安全, 2021, 21(6): 19-25. |
| [9] | 刘子昂, 黄缘缘, 马佳利, 周睿. 基于区块链的医疗数据滥用监控平台设计与实现[J]. 信息网络安全, 2021, 21(5): 58-66. |
| [10] | 王开轩, 滕亚均, 王琼霄, 王伟. 隐式证书的国密算法应用研究[J]. 信息网络安全, 2021, 21(5): 74-81. |
| [11] | 张昱, 孙光民, 李煜. 基于SM9算法的移动互联网身份认证方案研究[J]. 信息网络安全, 2021, 21(4): 1-9. |
| [12] | 王健, 赵曼莉, 陈志浩, 石波. 基于假名的智能交通条件隐私保护认证协议[J]. 信息网络安全, 2021, 21(4): 49-61. |
| [13] | 任航, 程相国, 张睿, 夏辉. 基于议价贝叶斯博弈模型的防欺诈策略[J]. 信息网络安全, 2021, 21(4): 81-88. |
| [14] | 周由胜, 王明, 刘媛妮. 支持区间查询的基于位置服务外包数据隐私保护方案[J]. 信息网络安全, 2021, 21(3): 26-36. |
| [15] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 149
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 382
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||