信息网络安全 ›› 2021, Vol. 21 ›› Issue (5): 58-66.doi: 10.3969/j.issn.1671-1122.2021.05.007
基于区块链的医疗数据滥用监控平台设计与实现
- 兰州大学信息科学与工程学院,兰州 730000
-
收稿日期:2020-01-15出版日期:2021-05-10发布日期:2021-06-22 -
通讯作者:周睿 E-mail:zr@lzu.edu.cn -
作者简介:刘子昂(1995—),男,湖南,博士研究生,主要研究方向为信息安全|黄缘缘(1996—),女,福建,硕士研究生,主要研究方向为信息安全|马佳利(1997—),女,甘肃,硕士研究生,主要研究方向为信息安全|周睿(1981—),男,重庆,副教授,博士,主要研究方向为分布式系统、嵌入式系统、人工智能 -
基金资助:国家重点研发计划(2020YFC0832500);国家自然科学基金(61402210);青海省科技计划(2020-GX-164);教育部-中国移动科研基金(MCM20170206);国家电网公司科技项目(SGGSKY00WYJS2000062)
Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain
LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui( )
)
- School of information science and engineering, Lanzhou University, Lanzhou 730000, China
-
Received:2020-01-15Online:2021-05-10Published:2021-06-22 -
Contact:ZHOU Rui E-mail:zr@lzu.edu.cn
摘要:
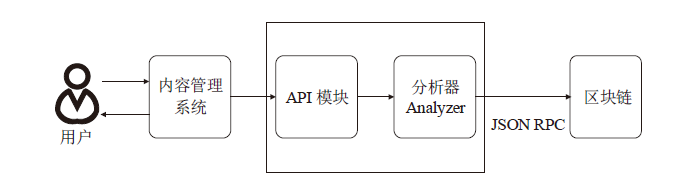
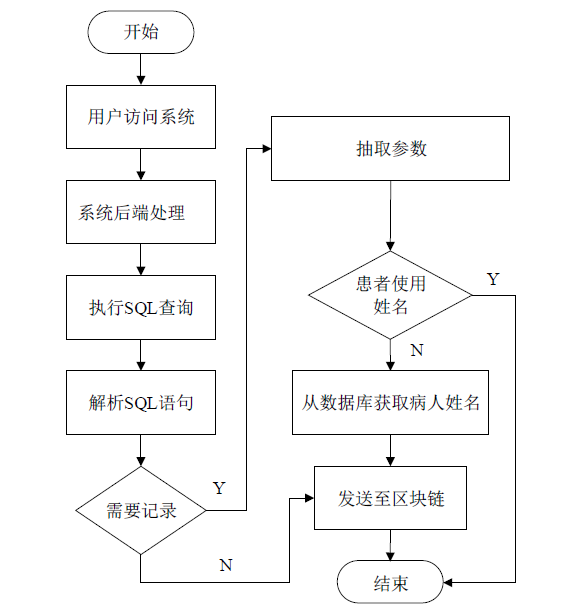
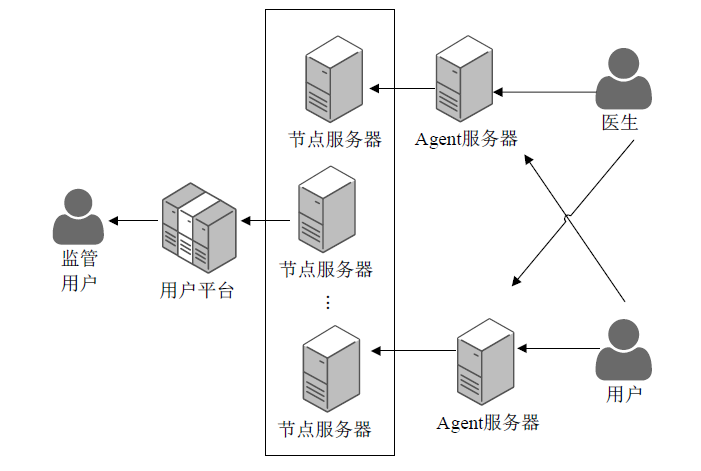
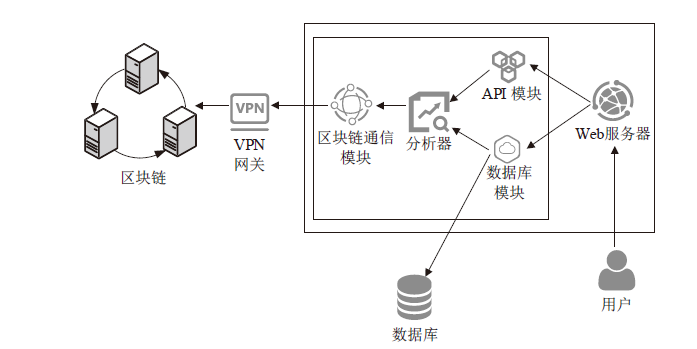
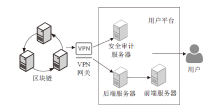
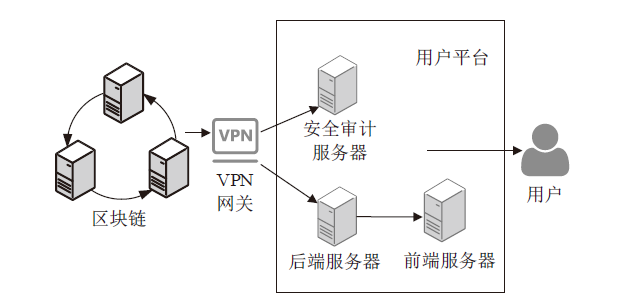
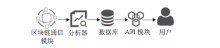
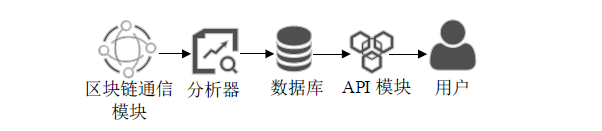
医疗管理系统维护并存储了大量准确且敏感的用户个人信息,具有极高的利用价值,因此这些数据成为了攻击者觊觎的目标。文章提出一种基于区块链技术的医学数据操作记录系统(RecordGuard),该系统可以记录医务人员或患者对医疗数据的使用情况,并通过区块链技术存储数据,帮助监管机构跟踪医疗数据操作记录,从而确保信息的安全。同时,在发生医疗纠纷的情况下,该系统可为仲裁机构验证证据真实性提供证据支撑,从而在一定程度上缓解医患问题中的信任危机。
中图分类号:
引用本文
刘子昂, 黄缘缘, 马佳利, 周睿. 基于区块链的医疗数据滥用监控平台设计与实现[J]. 信息网络安全, 2021, 21(5): 58-66.
LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain[J]. Netinfo Security, 2021, 21(5): 58-66.
表2
数据收集表
| 数据名 | 描述 | 数据类型 |
|---|---|---|
| time | operation time | timestamp |
| op_type | operation type | string |
| op_sys | medical data management system name | string |
| op_institution | op_sys’s institution | string |
| data_type | type of user data accessed | string |
| operator | person made this operation | string |
| patient | patient name in this operation | string |
| [1] |
YUE Xiao, WANG Huiju, JIN Dawei, et al. Healthcare Data Gateways: Found Healthcare Intelligence on Blockchain with Novel Privacy Risk Control[J]. Journal of Medical Systems, 2016,40(10):1-8.
doi: 10.1007/s10916-015-0365-5 URL |
| [2] | ASHTON K. That ‘Internet of Things’ Thing[J]. RFID Journal, 2009,22(7):97-114. |
| [3] | DANNEN C. Introducing Ethereum and Solidity[M]. Berkeley: Apress, 2017. |
| [4] | METTLER M. Blockchain Technology in Healthcare: The Revolution Starts Here[C]// IEEE. 18th International Conference on E-health Networking, Applications and Services(Healthcom), September 14-17, 2016, Munich, Germany. New Jersey: IEEE, 2016: 1-3. |
| [5] | PRISCO G. The Blockchain for Healthcare: Gem Launches Gem Health Network with Philips Blockchain Lab[EB/OL]. https://bitcoinmagazine.com/articles/the-blockchain-for-heathcare-gem-launches-gem-health-network-with-philips-blockchain-lab-1461674938, 2016-04-26. |
| [6] | TAYLOR P. Applying Blockchain Technology to Medicine Traceability[EB/OL]. https://www.securingindustry.com/pharmaceuticals/applying-blockchain-technology-to-medicine-traceability/s40/a2766/, 2016-04-27. |
| [7] |
KUO T T, KIM H E, OHNO-MACHADO L. Blockchain Distributed Ledger Technologies for Biomedical and Health Care Applications[J]. Journal of the American Medical Informatics Association, 2017,24(6):1211-1220.
doi: 10.1093/jamia/ocx068 URL |
| [8] | WILLIAMS-GRUT O. Estonia is Using the Technology behind Bitcoin to Secure 1 Million Health Records[EB/OL]. https://www.businessinsider.in/Estonia-is-using-the-technology-behind-bitcoin-to-secure-1-million-health-records/articleshow/51246942.cms, 2016-03-03. |
| [9] | BAXENDALE G. Can Blockchain Revolutionise EPRs?[J]. ITNow, 2016,58(1):38-39. |
| [10] | ROLSTON M E, FICKLIN J L, NAIRN M A, et al. User-application Interface: U.S. Patent 9, 176, 747[P]. 2015-11-03. |
| [11] | BAKKEN D. Middleware[EB/OL]. http://www.dia.uniroma3.it/~cabibbo/ids/altrui/middleware-bakken.pdf, 2020-12-21. |
| [12] | BRAY T. The JavaScript Object Notation(JSON) Data Interchange Format[EB/OL]. https://tools.ietf.org/id/draft-ietf-jsonbis-rfc7159bis-04.html#:~:text=JavaScript%20Object%20Notation%20(JSON)%20is,portable%20representation%20of%20structured%20data, 2017-07-19. |
| [13] | THURLOW R. RPC: Remote Procedure Call Protocol Specification Version 2[EB/OL]. http://www.ietf.org/rfc/rfc5531.txt, 2020-12-21. |
| [14] | LONEY K. Oracle Database 10g: the Complete Reference[M]. London: McGraw-Hill/Osborne, 2004. |
| [15] | FIELDING R T, KAISER G. The Apache HTTP Server Project[J]. IEEE Internet Computing, 1997,1(4):88-90. |
| [16] | BACUDIO A G, YUAN X, CHU B T B, et al. An Overview of Penetration Testing[J]. International Journal of Network Security & Its Applications, 2011,3(6):19-38. |
| [17] |
LIAO H J, LIN C H R, LIN Y C, et al. Intrusion Detection System: A Comprehensive Review[J]. Journal of Network and Computer Applications, 2013,36(1):16-24.
doi: 10.1016/j.jnca.2012.09.004 URL |
| [18] | MONSHIZADEH M, NALDURG P, VENKATAKRISHNAN V N. Mace: Detecting Privilege Escalation Vulnerabilities in Web Applications[EB/OL]. https://dl.acm.org/doi/pdf/10.1145/2660267.2660337, 2020-05-14. |
| [19] | DigitalOcean. DigitalOcean-The Developer Cloud[EB/OL]. https://www.digitalocean.com/, 2020-12-21. |
| [20] | SUNDARAM R, KANIYAR S N. Measuring Network Jitter on Application Packet Flows: U.S. Patent 6, 928, 473[P]. 2005-08-09. |
| [21] | LARIMER D. Delegated Proof-of-stake (DPOS)[EB/OL]. https://steemit.com/bitshares/@testz/bitshares-history-delegated-proof-of-stake-dpos, 2020-12-21. |
| [22] | BACH L M, MIHALJEVIC B, ZAGAR M. Comparative Analysis of Blockchain Consensus Algorithms[C]// IEEE. 41st International Convention on Information and Communication Technology, Electronics and Microelectronics(MIPRO), May 21-25, 2018, Opatija, Croatia. New Jersey: IEEE, 2018: 1545-1550. |
| [23] | SALEM M B, STOLFO S J. Detecting Masqueraders: A Comparison of One-class Bag-of-words User Behavior Modeling Techniques[EB/OL]. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.180.6427, 2020-05-15. |
| [1] | 李鹏, 郑田甜, 徐鹤, 朱枫. 基于区块链技术的RFID安全认证协议[J]. 信息网络安全, 2021, 21(5): 1-11. |
| [2] | 周由胜, 钟天琦. 基于区块链的公平交换方案[J]. 信息网络安全, 2021, 21(5): 19-30. |
| [3] | 王健, 赵曼莉, 陈志浩, 石波. 基于假名的智能交通条件隐私保护认证协议[J]. 信息网络安全, 2021, 21(4): 49-61. |
| [4] | 任航, 程相国, 张睿, 夏辉. 基于议价贝叶斯博弈模型的防欺诈策略[J]. 信息网络安全, 2021, 21(4): 81-88. |
| [5] | 周由胜, 王明, 刘媛妮. 支持区间查询的基于位置服务外包数据隐私保护方案[J]. 信息网络安全, 2021, 21(3): 26-36. |
| [6] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [7] | 芦效峰, 付淞兵. 属性基加密和区块链结合的可信数据访问控制方案[J]. 信息网络安全, 2021, 21(3): 7-8. |
| [8] | 张应辉, 朱甜, 郑东. 基于区块链的多关键字细粒度可搜索加密方案[J]. 信息网络安全, 2021, 21(2): 34-44. |
| [9] | 储志强, 仵冀颖, 徐磊, 杜聪. 基于区块链的分布式离链存储框架设计[J]. 信息网络安全, 2021, 21(2): 87-93. |
| [10] | 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. |
| [11] | 韩磊, 陈武平, 曾志强, 曾颖明. 区块链层级网络结构与应用研究[J]. 信息网络安全, 2020, 20(9): 112-116. |
| [12] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [13] | 石润华, 石泽. 基于区块链技术的物联网密钥管理方案[J]. 信息网络安全, 2020, 20(8): 1-8. |
| [14] | 李莉, 曾庆贤, 文义红, 王士成. 基于区块链与代理重加密的数据共享方案[J]. 信息网络安全, 2020, 20(8): 16-24. |
| [15] | 李宁波, 周昊楠, 车小亮, 杨晓元. 云环境下基于多密钥全同态加密的定向解密协议设计[J]. 信息网络安全, 2020, 20(6): 10-16. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||