信息网络安全 ›› 2020, Vol. 20 ›› Issue (8): 1-8.doi: 10.3969/j.issn.1671-1122.2020.08.001
基于区块链技术的物联网密钥管理方案
- 华北电力大学控制与计算机工程学院,北京 102206
-
收稿日期:2020-05-11出版日期:2020-08-10发布日期:2020-10-20 -
通讯作者:石润华 E-mail:rhshi@ncepu.edu.cn -
作者简介:石润华(1974—),男,安徽,教授,博士,主要研究方向为量子信息安全|石泽(1994—),女,河北,硕士研究生,主要研究方向为区块链、物联网 -
基金资助:国家自然科学基金(61772001)
Key Management Scheme for IoT Based on Blockchain Technology
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2020-05-11Online:2020-08-10Published:2020-10-20 -
Contact:SHI Runhua E-mail:rhshi@ncepu.edu.cn
摘要:
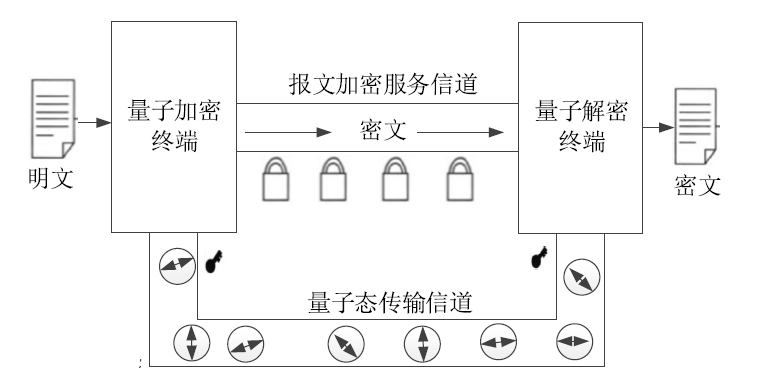
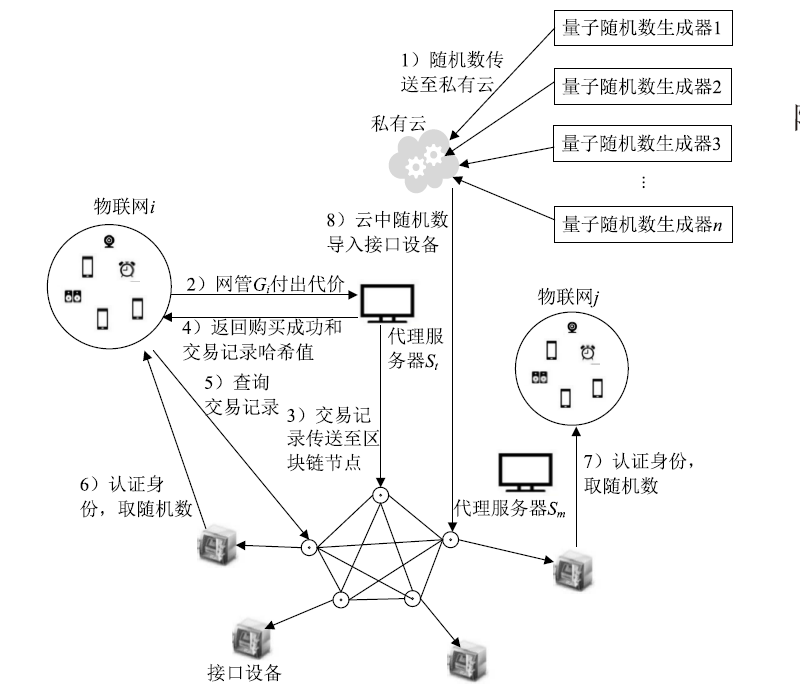
文章提出一种面向物联网的区块链密钥分发方案。利用量子随机数生成器不断地生成量子随机数,并传送至云端存储;发起者根据不同业务的安全需求,选择合理的随机数长度,并向代理服务器付出相关代价;代理服务器将购买记录上传至区块链节点进行验证,并广播至全网;发起者网关根据交易哈希值查询区块链上的交易记录;发起者网关和共享者网关在随机数接口设备进行身份验证;智能合约自动将量子随机数存储在智能卡中,发起者和共享者提取智能卡并获得共享密钥。该方案成本低且能有效解决物联网中密钥分发难的问题,从而实现不同物联子网底层传感设备间的安全通信。
中图分类号:
引用本文
石润华, 石泽. 基于区块链技术的物联网密钥管理方案[J]. 信息网络安全, 2020, 20(8): 1-8.
SHI Runhua, SHI Ze. Key Management Scheme for IoT Based on Blockchain Technology[J]. Netinfo Security, 2020, 20(8): 1-8.
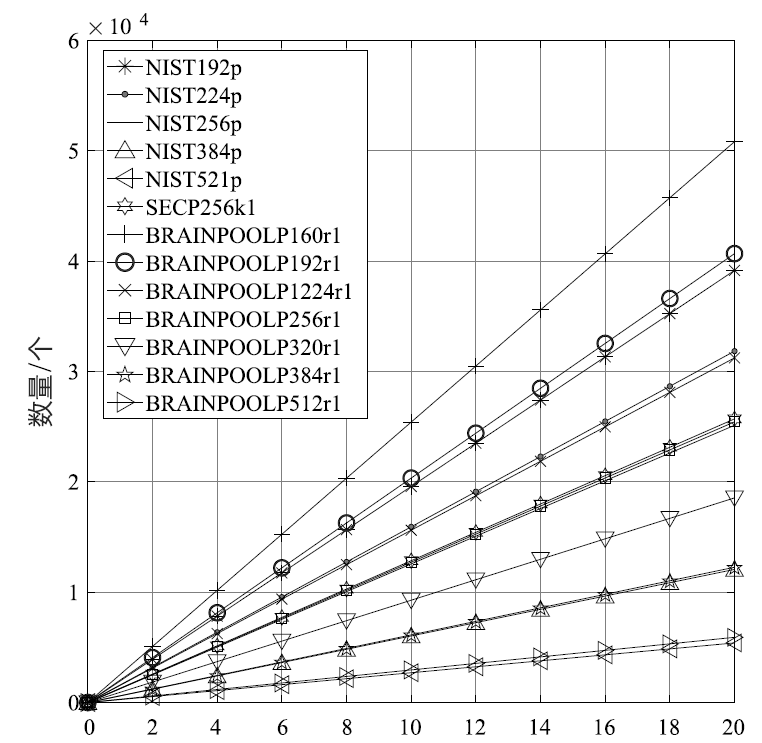
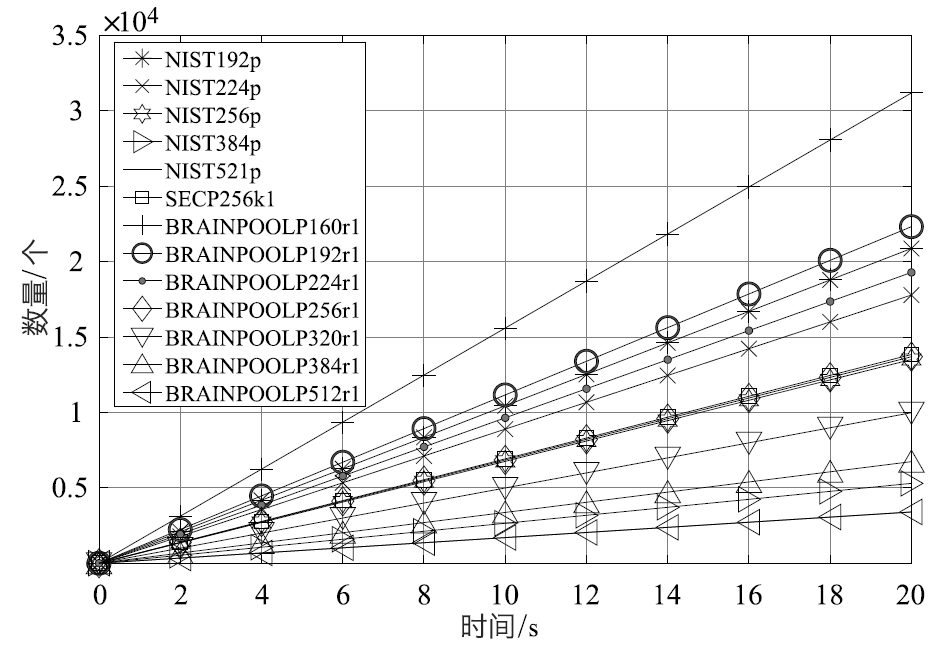
表2
生成密钥对、ECDSA签名和验证时间
| 曲线 | siglen | sign | sign/s | verify | verify/s |
|---|---|---|---|---|---|
| NIST192p | 48 | 0.00051 s | 1958.15 | 0.00096 s | 1043.69 |
| NIST224p | 56 | 0.00063 s | 1592.33 | 0.00112 s | 889.21 |
| NIST256p | 64 | 0.00080 s | 1256.33 | 0.00148 s | 675.38 |
| NIST384p | 96 | 0.00166 s | 603.27 | 0.00378 s | 264.74 |
| NIST521p | 132 | 0.00370 s | 270.07 | 0.00589 s | 169.65 |
| SECP256k1 | 64 | 0.00078 s | 1285.33 | 0.00145 s | 692.02 |
| BRAINPOOLP160r1 | 40 | 0.00039 s | 2541.60 | 0.00064 s | 1559.46 |
| BRAINPOOLP192r1 | 48 | 0.00049 s | 2034.21 | 0.00090 s | 1116.00 |
| BRAINPOOLP224r1 | 56 | 0.00064 s | 1561.74 | 0.00104 s | 964.17 |
| BRAINPOOLP256r1 | 64 | 0.00079 s | 1271.84 | 0.00146 s | 684.67 |
| BRAINPOOLP320r1 | 80 | 0.00108 s | 927.34 | 0.00200 s | 498.99 |
| BRAINPOOLP384r1 | 96 | 0.00163 s | 613.03 | 0.00297 s | 336.76 |
| BRAINPOOLP512r1 | 128 | 0.00338 s | 295.45 | 0.00588 s | 170.02 |
表2
| [1] | WU Hequan. Technology and Application Progress on Internet of Things[J]. Chinese Journal on Internet of Things, 2017,1(1):1-6. |
| [2] | YAQOOB I, HASHEM I A T, AHMED A, et al. Internet of Things Forensics: Recent Advances, Taxonomy, Requirements, and Open Challenges[J]. Future Generation Computer Systems, 2019,92(92):265-275. |
| [3] | ESCHENAUER L, GLIGOR V D. A Key Management Scheme for Distributed Sensor Networks[C]// ACM. 9th ACM Conference on Computer and Communications Security, October 20, 2002, Washington, USA. New York: ACM, 2002:41-47. |
| [4] | CHAN Haowen, PERRIG A, SONG D. Random Key Pre-distribution Scheme for Sensor Networks[C]// IEEE. IEEE on Security and Privacy, May 18, 2003, Berkeley, CA, USA. New York: IEEE, 2003: 197-213. |
| [5] | DU Wenliang, DENG Jing, HAN Yungsiang, et al. A Pairwise Key Pre-distribution Scheme for Wireless Sensor Network[J]. ACM Transactions on Information and System Security, 2005,8(2):42-51. |
| [6] | LIU Donggang, NING Ping. Establishing Pairwise Keys in Distributed Sensor Networks[C]// Association for Computing Machinery. CCS03: Tenth ACM Conference on Computer and Communications Security, October 21-23, 2003, Washington DC, USA. New York: ACM, 2003: 52-61. |
| [7] | LIU Donggang, NING Ping. Establishing Pairwise Keys in Distributed Sensor Networks[J]. ACM Transactions on Information and System Security, 2005,8(1):72-82. |
| [8] | MAURER U M. Secret Key Aggreement by Public Discussion from Common Information[J]. IEEE Transactions on Information Theory, 1993,39(3):733-742. |
| [9] | XUE Kaiping, MA Changsha, HONG Peilin, et al. A Temporal-credential-based Mutual Authentication and Key Agreement Scheme for Wireless Sensor Networks[J]. Journal of Network and Computer Applications, 2013,36(1):316-323. |
| [10] | VAIDYA B, MAKRAKIS D, MOUFTAH H T. Improved Two-factor User Authentication in Wireless Sensor Networks[C]// IEEE. 6th IEEE International Conference on Wireless and Mobile Computing, October 11-13, 2010, Niagara Falls, Canada. New York: IEEE, 2010: 600-606. |
| [11] | HE Daojing, GAO Yi, CHAN S, et al. An Enhanced Two-factor User Authentication Scheme in Wireless Sensor Networks[J]. International Journal of Ad Hoc & Sensor Wireless Networks, 2010,10(4):361-371. |
| [12] | TURKANOVIC M, HOLBL M. An Improved Dynamic Password-based User Authentication Scheme for Hierarchical Wireless Sensor Networks[J]. Elektronika Ir Elektrotechnika, 2013,19(6):109-116. |
| [13] | BENNETT C H, BRASSARD G. Quantum Cryptography: Public Key Distribution and Coin Tossing[C]// IEEE. International Conference on Computers Systems and Signal Processing, September 12, 1984, Bangalore, India. New York: IEEE, 1984: 175-179. |
| [14] | ELKOUSS D, MARTINEZ-MATEO J, CIURANA A, et al. Secure Optical Networks Based on Quantum Key Distribution and Weakly Trusted Repeaters[J]. Journal of Optical Communications & Networking, 2013,5(4):316-328. |
| [15] |
LO H K, CHAU H F. Unconditional Security of Quantum Key Distribution over Arbitrarily Long Distances[J]. Science, 1999,283(5410):2050-2056.
doi: 10.1126/science.283.5410.2050 URL pmid: 10092221 |
| [16] | WANG Yunxiao. Research on Mobile Application of Smart Grid Based on Quantum Communication Technology[EB/OL]. http://cpfd.cnki.com.cn/Article/CPFDTOTAL-GWDT201910001061.htm, 2020-2-11. |
| 王云霄. 智能电网基于量子通信技术的移动应用研究[EB/OL]. http://cpfd.cnki.com.cn/Article/CPFDTOTAL-GWDT201910001061.htm, 2020-2-11. | |
| [17] | LI Hongwei, CHEN Wei, HUANG Jingzheng, et al. Security of Quantum Key Distribution[J]. SCIENTIA SINICA Physica, Mechanica & Astronomica, 2012,42(11):1237-1255. |
| 李宏伟, 陈巍, 黄靖正, 等. 量子密码安全性研究[J]. 中国科学:物理学力学天文学, 2012,42(11):1237-1255. | |
| [18] | ZHANG Ziping, LIU Guojun, DONG Kai, et al. Key Pool Construction of Quantum Key Distribution Optical Network[J]. Laser & Optoelectronics Progress, 2019,56(21):231-237. |
| 张梓平, 刘国军, 董凯, 等. 量子密钥分发光网络密钥池构建方法[J]. 激光与光电子学进展, 2019,56(21):231-237. | |
| [19] | LIN Jingming. Development of Trng for Quantum Key Communication[D]. Harbin: Harbin Institute of Technology, 2017. |
| 林景明. 面向量子密钥通信的真随机数生成器研制[D]. 哈尔滨:哈尔滨工业大学, 2017. | |
| [20] | YANG Chao. Research on Model and Routing Technology in Wide-area Quantum Key[D]. Zhengzhou: Strategic Support Force Information Engineering University, 2018. |
| 杨超. 广域量子密钥网络模型及路由技术研究[D]. 郑州:战略支援部队信息工程大学, 2018. | |
| [21] | YUAN Cao, ZHAO Yongli, Colman Meixner Carlos, et al. Key on Demand(KoD) for Software-defined Optical Networks Secured by Quantum Key Distribution(QKD)[J]. Optics Expres, 2017,25(22):26453-26467. |
| [22] | YUAN Cao, ZHAO Yongli. Time-scheduled Quantum Key Distribution(QKD) over WDM Networks[J]. Journal of Lightwave Technology, 2018,36(16):3382-3395. |
| [23] | ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends[C]// IEEE. 2017 IEEE International Congress on Big Data(Big Data Congress), June 25-30, 2017, Honolulu, HI, USA. New York: IEEE, 2017: 557-564. |
| [24] | SZABO N. Formalizing and Securing Relationships on Public Networks[EB/OL]. http://ojphi.org/ojs/index.php/fm/article/view/548/469, 2017-4-7. |
| [1] | 韩磊, 陈武平, 曾志强, 曾颖明. 区块链层级网络结构与应用研究[J]. 信息网络安全, 2020, 20(9): 112-116. |
| [2] | 徐绘凯, 刘跃, 马振邦, 段海新. MQTT安全大规模测量研究[J]. 信息网络安全, 2020, 20(9): 37-41. |
| [3] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [4] | 李莉, 曾庆贤, 文义红, 王士成. 基于区块链与代理重加密的数据共享方案[J]. 信息网络安全, 2020, 20(8): 16-24. |
| [5] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [6] | 陈璐, 孙亚杰, 张立强, 陈云. 物联网环境下基于DICE的设备度量方案[J]. 信息网络安全, 2020, 20(4): 21-30. |
| [7] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [8] | 毛志来, 刘亚楠, 孙惠平, 陈钟. 区块链性能扩展与安全研究[J]. 信息网络安全, 2020, 20(3): 56-64. |
| [9] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [10] | 姚萌萌, 唐黎, 凌永兴, 肖卫东. 基于串空间的安全协议形式化分析研究[J]. 信息网络安全, 2020, 20(2): 30-36. |
| [11] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [12] | 周艺华, 吕竹青, 杨宇光, 侍伟敏. 基于区块链技术的数据存证管理系统[J]. 信息网络安全, 2019, 19(8): 8-14. |
| [13] | 叶阿勇, 金俊林, 孟玲玉, 赵子文. 面向移动终端隐私保护的访问控制研究[J]. 信息网络安全, 2019, 19(8): 51-60. |
| [14] | 路爱同, 赵阔, 杨晶莹, 王峰. 区块链跨链技术研究[J]. 信息网络安全, 2019, 19(8): 83-90. |
| [15] | 郑敏, 王虹, 刘洪, 谭冲. 区块链共识算法研究综述[J]. 信息网络安全, 2019, 19(7): 8-24. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||