Netinfo Security ›› 2023, Vol. 23 ›› Issue (7): 86-97.doi: 10.3969/j.issn.1671-1122.2023.07.009
Previous Articles Next Articles
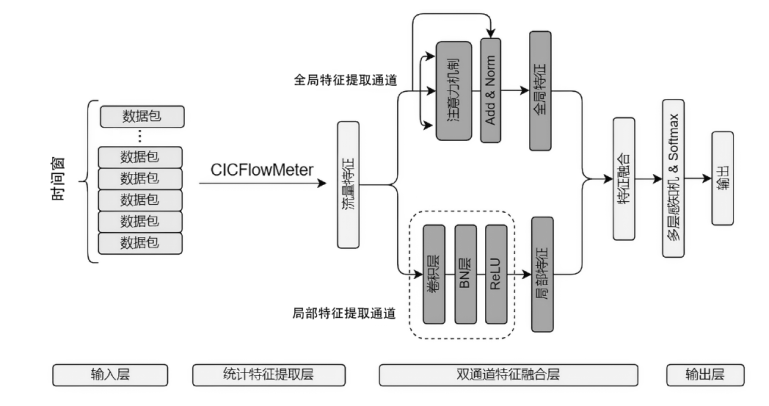
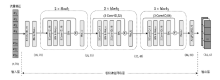
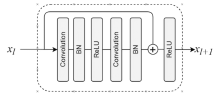
Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion
JIANG Yingzhao, CHEN Lei, YAN Qiao( )
)
- College of Computer Science and Software Engineering, Shenzhen University, Shenzhen 518060, China
-
Received:2023-03-27Online:2023-07-10Published:2023-07-14
CLC Number:
Cite this article
JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion[J]. Netinfo Security, 2023, 23(7): 86-97.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.07.009
| 类别 | 训练集的 数量/个 | 验证集的 数量/个 | 测试集的 数量/个 |
|---|---|---|---|
| benign | 6423367 | 1835248 | 917624 |
| DDoS attack-HOIC | 480208 | 137202 | 68602 |
| DDoS attacks-LOIC-HTTP | 403334 | 115238 | 57619 |
| DoS attacks-Hulk | 323338 | 92382 | 46192 |
| DoS attacks-SlowHTTPTest | 97923 | 27978 | 13989 |
| DoS attacks-GoldenEye | 29056 | 8302 | 4150 |
| DoS attacks-Slowloris | 7693 | 2198 | 1099 |
| DDoS attack-LOIC-UDP | 1211 | 346 | 173 |
| 类别 | 训练集的数量/个 | 验证集的数量/个 | 测试集的数量/个 |
|---|---|---|---|
| benign | 159216 | 45490 | 22746 |
| ntp | 219545 | 62727 | 31364 |
| dns | 219545 | 62727 | 31364 |
| ldap | 219545 | 62727 | 31364 |
| mssql | 219545 | 62727 | 31364 |
| netbios | 219545 | 62727 | 31364 |
| snmp | 219545 | 62727 | 31364 |
| ssdp | 219545 | 62727 | 31364 |
| udp | 219545 | 62727 | 31364 |
| udplag | 219545 | 62727 | 31364 |
| syn | 219545 | 62727 | 31364 |
| tftp | 219545 | 62727 | 31364 |
| [1] | YOACHIMIK O. Mitigating a 754 Million PPS DDoS Attack Automatically[EB/OL]. (2020-07-09) [2022-05-16]. https://blog.cloudflare.com/mitigating-a-754-million-pps-ddos-attack-automatically. |
| [2] | VIJ A, PASHA S. Azure DDoS Protection-2021 Q3 and Q4 DDoS Attack Trends[EB/OL]. (2022-01-25) [2022-05-16]. https://azure.microsoft.com/zh-cn/blog/azure-ddos-protection-2021-q3-and-q4-ddos-attack-trends. |
| [3] | Tencent Cloud T-Sec DDoS Protection Team, Green Alliance Technology Threat Intelligence Team. 2021 Global DDoS Threat Report[EB/OL]. (2022-01-26) [2022-05-16]. https://cloud.tencent.com/developer/article/1936949. |
| 腾讯云T-Sec DDoS防护团队, 绿盟科技威胁情报团队. 2021年全球DDoS威胁报告[EB/OL]. (2022-01-26) [2022-05-16]. https://cloud.tencent.com/developer/article/1936949. | |
| [4] | Wangsu Science&Technology. China Internet Security Report for the First Half of 2021[EB/OL]. (2021-11-23) [2022-05-16]. https://www.vzkoo.com/document/992eef6bb162171fd39d55876bf3f19b.html. |
| 网宿科技. 2021年上半年中国互联网安全报告[EB/OL]. (2021-11-23) [2022-05-16]. https://www.vzkoo.com/document/992eef6bb162171fd39d55876bf3f19b.html. | |
| [5] | LIU Ying, ZHI Ting, SHEN Ming, et al. Software-Defined DDoS Detection with Information Entropy Analysis and Optimized Deep Learning[J]. Future Generation Computer Systems, 2022(129): 99-114. |
| [6] | LIU Zhen, HU Changzhen, SHAN Chun. Riemannian Manifold on Stream Data: Fourier Transform and Entropy-Based DDoS Attacks Detection Method[J]. Computers & Security, 2021(109): 102392-102407. |
| [7] | KOAY A, CHEN A, WELCH I, et al. A New Multi Classifier System Using Entropy-Based Features in DDoS Attack Detection[C]// IEEE. 2018 International Conference on Information Networking (ICOIN). New York: IEEE, 2018: 162-167. |
| [8] | IDHAMMAD M, AFDEL K, BELOUCH M. Detection System of HTTP DDoS Attacks in a Cloud Environment Based on Information Theoretic Entropy and Random Forest[J]. Security and Communication Networks, 2018(2): 1-13. |
| [9] | YE Jin, CHENG Xiangyang, ZHU Jian, et al. A DDoS Attack Detection Method Based on SVM in Software Defined Network[EB/OL]. (2018-01-01) [2022-05-16]. https://dl.acm.org/doi/10.1155/2018/9804061. |
| [10] |
TUAN N N, HUNG P H, NGHIA N D, et al. A DDoS Attack Mitigation Scheme in ISP Networks Using Machine Learning Based on SDN[J]. Electronics, 2020, 9(3): 413-432.
doi: 10.3390/electronics9030413 URL |
| [11] | DE-MIRANDA V R, INÁCIO P R M, MAGONI D, et al. Detection of Reduction-of-Quality DDoS Attacks Using Fuzzy Logic and Machine Learning Algorithms[J]. Computer Networks, 2021(186): 107792-107811. |
| [12] | MIN Erxue, CHEN Wei, LONG Jun, et al. TR-IDS: Anomaly-Based Intrusion Detection Through Text-Convolutional Neural Network and Random Forest[EB/OL]. (2018-12-16) [2023-01-13]. https://dl.acm.org/doi/10.1155/2018/4943509. |
| [13] | CHOLLET F. Xception: Deep Learning with Depthwise Separable Convolutions[C]// IEEE. 2017 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2017: 1251-1258. |
| [14] | GIRSHICK R. Fast R-CNN[C]// IEEE. Proceedings of the IEEE International Conference on Computer Vision. New York: IEEE, 2015: 1440-1448. |
| [15] |
REN A, LI Zhe, DING Caiwen, et al. SC-DCNN: Highly-Scalable Deep Convolutional Neural Network Using Stochastic Computing[J]. ACM SIGPLAN Notices, 2017, 52(4): 405-418.
doi: 10.1145/3093336.3037746 URL |
| [16] | SHAHRIAR M H, HAQUE N I, RAHMAN M A, et al. G-IDS: Generative Adversarial Networks Assisted Intrusion Detection System[C]// IEEE. 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC). New York: IEEE, 2020: 376-385. |
| [17] | AHUJA N, SINGAL G, MUKHOPADHYAY D. DLSDN: Deep Learning for DDoS Attack Detection in Software Defined Networking[C]// IEEE. 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence). New York: IEEE, 2021: 683-688. |
| [18] | YANG Kun, ZHANG Junjie, XU Yang, et al. DDoS Attacks Detection with Autoencoder[C]// IEEE. NOMS 2020-2020 IEEE/IFIP Network Operations and Management Symposium. New York: IEEE, 2020: 1-9. |
| [19] | SALAHUDDIN M A, BARI M F, ALAMEDDINE H A, et al. Time-Based Anomaly Detection Using Autoencoder[C]// IEEE. 2020 16th International Conference on Network and Service Management (CNSM). New York: IEEE, 2020: 1-9. |
| [20] | AMAIZU G C, NWAKANMA C I, BHARDWAJ S, et al. Composite and Efficient DDoS Attack Detection Framework for B5G Networks[J]. Computer Networks, 2021(188): 107871-107881. |
| [21] | MA Li, CHAI Ying, CUI Lei, et al. A Deep Learning-Based DDoS Detection Framework for Internet of Things[C]// IEEE. ICC 2020-2020 IEEE International Conference on Communications (ICC). New York: IEEE, 2020: 1-6. |
| [22] |
DORIGUZZI-CORIN R, MILLAR S, SCOTT-HAYWARD S, et al. LUCID: A Practical, Lightweight Deep Learning Solution for DDoS Attack Detection[J]. IEEE Transactions on Network and Service Management, 2020, 17(2): 876-889.
doi: 10.1109/TNSM.4275028 URL |
| [23] | LASHKARI A H, DRAPER-GIL G, MAMUN M S I, et al. Characterization of Tor Traffic Using Timebased Features[C]// SciTePress. Proceedings of the 3rd International Conference on Information Systems Security and Privacy. San Francisco: SciTePress, 2017: 253-262. |
| [24] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 770-778. |
| [25] | VASWANI A, SHAZEER N, PARMAR N, et al. Attention Is All You Need[EB/OL]. (2017-06-12) [2023-01-17]. https://arxiv.org/abs/1706.03762. |
| [26] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[J]. ICISSP, 2018(1): 108-116. |
| [27] | SHARAFALDIN I, LASHKARI A H, HAKAK S, et al. Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy[C]// IEEE. 2019 International Carnahan Conference on Security Technology (ICCST). New York: IEEE, 2019: 1-8. |
| [1] | LIU Gang, YANG Wenli, WANG Tongli, LI Yang. Differential Privacy-Preserving Dynamic Recommendation Model Based on Cloud Federation [J]. Netinfo Security, 2023, 23(7): 31-43. |
| [2] | YUAN Wenxin, CHEN Xingshu, ZHU Yi, ZENG Xuemei. HTTP Payload Covert Channel Detection Method Based on Deep Learning [J]. Netinfo Security, 2023, 23(7): 53-63. |
| [3] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| [4] | ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning [J]. Netinfo Security, 2023, 23(5): 1-10. |
| [5] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [6] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| [7] | XU Zhanyang, CHENG Luofei, CHENG Jianchun, XU Xiaolong. A Scheme of Optimizing Deep Learning Model Using Bi-ADMM [J]. Netinfo Security, 2023, 23(2): 54-63. |
| [8] | CHEN Depeng, LIU Xiao, CUI Jie, ZHONG Hong. Research on Membership Inference Attack Method Based on Double Threshold Function [J]. Netinfo Security, 2023, 23(2): 64-75. |
| [9] | JIA Fan, KANG Shuya, JIANG Weiqiang, WANG Guangtao. Vulnerability Similarity Algorithm Evaluation Based on NLP and Feature Fusion [J]. Netinfo Security, 2023, 23(1): 18-27. |
| [10] | LI Jiyu, FU Zhangjie, ZHANG Yubin. An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation [J]. Netinfo Security, 2023, 23(1): 93-102. |
| [11] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [12] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [13] | GU Zhaojun, LIU Tingting, GAO Bing, SUI He. Anomaly Detection of Imbalanced Data in Industrial Control System Based on GAN-Cross [J]. Netinfo Security, 2022, 22(8): 81-89. |
| [14] | FAN Mingyu, LI Ke. A Method to Distinguish DDoS Attack Types Based on RNN [J]. Netinfo Security, 2022, 22(7): 1-8. |
| [15] | LIU Guangjie, DUAN Kun, ZHAI Jiangtao, QIN Jiayu. Mobile Traffic Application Recognition Based on Multi-Feature Fusion [J]. Netinfo Security, 2022, 22(7): 18-26. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||