Netinfo Security ›› 2022, Vol. 22 ›› Issue (5): 1-10.doi: 10.3969/j.issn.1671-1122.2022.05.001
Previous Articles Next Articles
Eff icient Implementation Scheme of Batch Verif ication Based on SM2 Signatures
LI Li( ), BAI Lu, TU Hang, ZHANG Biao
), BAI Lu, TU Hang, ZHANG Biao
- Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
-
Received:2022-02-13Online:2022-05-10Published:2022-06-02 -
Contact:LI Li E-mail:lil@whu.edu.cn
CLC Number:
Cite this article
LI Li, BAI Lu, TU Hang, ZHANG Biao. Eff icient Implementation Scheme of Batch Verif ication Based on SM2 Signatures[J]. Netinfo Security, 2022, 22(5): 1-10.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.05.001
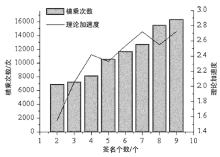
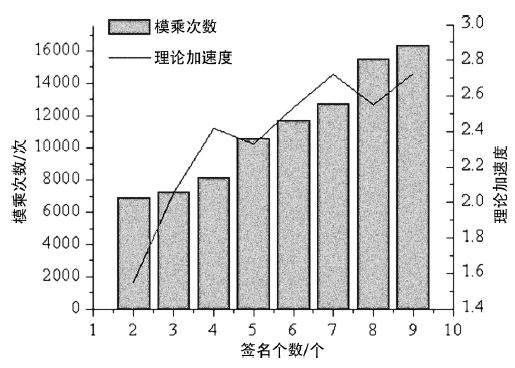
| t | 加速点乘 | 半标量点乘 | 多参数求逆 | 判断批验签 结果 | 总计 算量 | speedupt | ||||
|---|---|---|---|---|---|---|---|---|---|---|
| 计算量 | 占比 | 计算量 | 占比 | 计算量 | 占比 | 计算量 | 占比 | |||
| 2 | 5063M | 0.792 | 1030M | 0.161 | 285M | 0.045 | 12M | 0.002 | 6390M | 1.548 |
| 3 | 5344M | 0.740 | 1545M | 0.214 | 309M | 0.043 | 25M | 0.003 | 7223M | 2.055 |
| 4 | 5657M | 0.692 | 2060M | 0.252 | 357M | 0.044 | 105M | 0.013 | 8179M | 2.419 |
| 5 | 7576M | 0.714 | 2575M | 0.243 | 306M | 0.029 | 154M | 0.015 | 10611M | 2.331 |
| 6 | 7752M | 0.663 | 3090M | 0.264 | 330M | 0.028 | 520M | 0.044 | 11692M | 2.539 |
| 7 | 8138M | 0.638 | 3605M | 0.283 | 354M | 0.028 | 650M | 0.051 | 12747M | 2.717 |
| 8 | 8141M | 0.525 | 4120M | 0.265 | 402M | 0.026 | 2547M | 0.164 | 15210M | 2.550 |
| 9 | 8764M | 0.537 | 4635M | 0.284 | 450M | 0.028 | 2480M | 0.152 | 16329M | 2.727 |
| [1] | WANG Hao, SONG Xiangfu, KE Junming, et al. Blockchain and Privacy Preserving Mechanisms in Cryptocurrency[J]. Netinfo Security, 2017, 17(7): 32-39. |
| 王皓, 宋祥福, 柯俊明, 等. 数字货币中的区块链及其隐私保护机制[J]. 信息网络安全, 2017, 17(7): 32-39. | |
| [2] | WARRAN S, FAN Ziyang, BLAKE M. CBDC Technology Considerations[EB/OL]. (2021-11-09)[2021-12-27]. https://cn.weforum.org/reports/digital-currency-governance-consortium-white-paper-series/cbdc-tech-considerations#report-nav. |
| [3] | GM/T 32918. 2-2016 Information Security Technology-Public Key Cryptographic Algorithms SM2 Based on Elliptic Curves-Part 2: Digital Signature Algorithm[S]. Beijing: Chinese Encryption Administration, 2016. |
| GM/T 32918. 2-2016 信息安全技术SM2椭圆曲线公钥密码算法第2部分:数字签名算法[S]. 北京: 国家密码局, 2016. | |
| [4] |
KOBLITZ N. Elliptic Curve Cryptosystems[J]. Mathematics of Computation, 1987, 48(177): 203-209.
doi: 10.1090/S0025-5718-1987-0866109-5 URL |
| [5] | YAO Qian, LI Huifeng, WEN Xinxiang, et al. Digital Currency System: China, ZL201610179399.3[P]. 2017-10-03. |
| 姚前, 李会锋, 温信祥, 等. 数字货币系统:中国, ZL201610179399.3[P]. 2017-10-03. | |
| [6] | FIAT A. Batch RSA[C]// Springer. Conference on the Theory and Application of Cryptology. Heidelberg: Springer, 1989: 175-185. |
| [7] |
HARN L. Batch Verifying Multiple RSA Digital Signatures[J]. Electronics Letters, 1998, 34(12): 1219-1220.
doi: 10.1049/el:19980833 URL |
| [8] | KARATI S, DAS A, ROYCHOWDHURY D, et al. Batch Verification of ECDSA Signatures[C]// Springer. International Conference on Cryptology in Africa. Heidelberg: Springer, 2012: 1-18. |
| [9] | KARATI S, DAS A. Faster Batch Verification of Standard ECDSA Signatures Using Summation Polynomials[C]// Springer. International Conference on Applied Cryptography and Network Security. Heidelberg: Springer, 2014: 438-456. |
| [10] |
KITTUR A S, PAIS A R. A New Batch Verification Scheme for ECDSA* Signatures[J]. Sādhanā, 2019, 44(7): 1-12.
doi: 10.1007/s12046-018-0983-y URL |
| [11] | BERNSTEIN D J, DOUMEN J, LANGE T, et al. Faster Batch Forgery Identification[C]// Springer. International Conference on Cryptology in India. Heidelberg: Springer, 2012: 454-473. |
| [12] | LIDL R, NIEDERREITER H. Introduction to Finite Fields and their Applications[M]. Cambridge: Cambridge University Press, 1994. |
| [13] | YANG Yi, HE Debiao, WANG Huaqun, et al. An Efficient Blockchain-Based Batch Verification Scheme for Vehicular Ad Hoc Networks[EB/OL]. (2019-12-27)[2021-11-20]. https://onlinelibrary.wiley.com/doi/abs/10.1002/ett.3857. |
| [14] |
APOSTOL T M. Resultants of Cyclotomic Polynomials[J]. Proceedings of the American Mathematical Society, 1970, 24(3): 457-462.
doi: 10.1090/S0002-9939-1970-0251010-X URL |
| [15] | SEMAEV I A. Summation Polynomials and the Discrete Logarithm Problem on Elliptic Curves[EB/OL]. (2004-02-05)[2021-12-06]. https://www.iacr.org/cryptodb/data/paper.php?pubkey=12007. |
| [16] | KARATI S, DAS A, CHOWDHURY D R. Using Randomizers for Batch Verification of ECDSA Signatures[EB/OL]. (2012-10-13)[2021-11-19]. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.300.7276. |
| [17] |
BRAUER A. On Addition Chains[J]. Bulletin of American Mathematical Society, 1939, 45(10): 736-739.
doi: 10.1090/S0002-9904-1939-07068-7 URL |
| [18] |
KUDITHI T, SAKTHIVEL R. High-Performance ECC Processor Architecture Design for IoT Security Applications[J]. The Journal of Supercomputing, 2019, 75(1): 447-474.
doi: 10.1007/s11227-018-02740-2 URL |
| [1] | XIA Zhe, LUO Bin, XU Guibin, XIAO Xinxiu. Privacy-preserving Data Aggregation with Fine Grained Access Control for Smart Grid [J]. Netinfo Security, 2021, 21(11): 28-39. |
| [2] | HU Jingxiu, YANG Yang, XIONG Lu, WU Jintan. SM Algorithm Analysis and Software Performance Research [J]. Netinfo Security, 2021, 21(10): 8-16. |
| [3] | ZHANG Jianhang, CAO Zeyang, SONG Xiaofeng, XU Qingzheng. Quantum-resistant Efficient Identity-based Signature Scheme with Message Recovery over Primitive Lattices [J]. Netinfo Security, 2020, 20(1): 26-32. |
| [4] | Xuefeng ZHANG, Hua PENG. Blind Signature Scheme Based on SM9 Algorithm [J]. Netinfo Security, 2019, 19(8): 61-67. |
| [5] | Wei HU, Qiuhan WU, Shengli LIU, Wei FU. Design of Secure eID and Identity Authentication Agreement in Mobile Terminal Based on Guomi Algorithm and Blockchain [J]. Netinfo Security, 2018, 18(7): 7-9. |
| [6] | Liming ZUO, Pingping XIA, Zuosong CHEN. Protection Technology of Network Camera Based on SM2 Digital Signature [J]. Netinfo Security, 2018, 18(5): 32-40. |
| [7] | Meng ZHAO, Yong DING, Yujue WANG. Secure Cloud Data Storage with Designated Auditors [J]. Netinfo Security, 2018, 18(11): 66-72. |
| [8] | Hong JIANG, Baoyuan KANG, Chunqing LI. Improved Auditing Schemes with Identity-preserving for the Integrity of Shared Data in the Cloud [J]. Netinfo Security, 2018, 18(10): 85-91. |
| [9] | Yongqiang ZHANG, Weilong LU, Chunming TANG. Research on An Efficient and Practical Cloud-based Digital Signature Scheme [J]. Netinfo Security, 2016, 16(7): 1-6. |
| [10] | Yansheng ZHANG, Xueming WANG, Gege QIU. Research on a New Dynamic Threshold Digital Signature Scheme [J]. Netinfo Security, 2016, 16(6): 62-67. |
| [11] | Guangrong HE, Xueming WANG. A New Ad Hoc Group Key Agreement Scheme Based on HECC [J]. Netinfo Security, 2016, 16(5): 58-63. |
| [12] | Sijia CHENG, Changhong ZHANG, Shuaiqing PAN. Design on Data Access Control Scheme for Cloud Storage Based on CP-ABE Algorithm [J]. Netinfo Security, 2016, 16(2): 1-6. |
| [13] | Jian XU, Ying-nan ZHAO, Yong-chun TIAN, Fu-cai ZHOU. Research on Conference Identity Authentication System Based on Two-dimensional Bar Code and Face Recognition [J]. Netinfo Security, 2015, 15(4): 13-18. |
| [14] | . Reliable Information Transmission Mechanism Research of the Internet of Things Sensing Layer based on the Node Authentication [J]. , 2014, 14(2): 53-. |
| [15] | . The Implementation and Evaluation of SM2 Algorithm in Java [J]. , 2013, 13(8): 0-0. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||