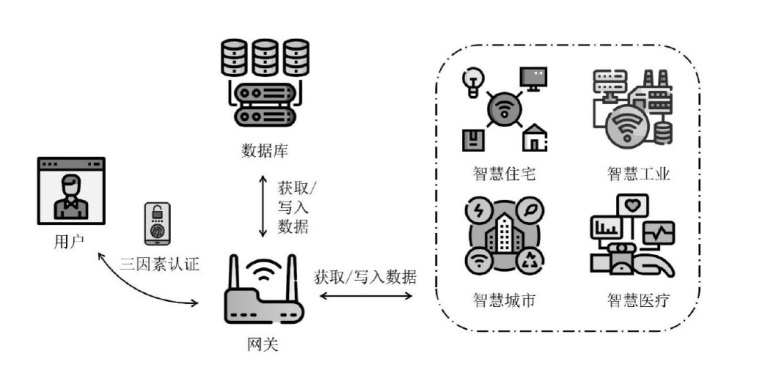
Netinfo Security ›› 2025, Vol. 25 ›› Issue (9): 1407-1417.doi: 10.3969/j.issn.1671-1122.2025.09.009
Previous Articles Next Articles
Dynamic Three-Factor Authentication Key Agreement Protocol for IoT Scenarios
YANG Yukun, XIAO Weien, LIANG Boxuan, HUANG Xin( )
)
- Department of Computer Science and Technology (College of Data Science), Taiyuan University of Technology, Taiyuan 030024, China
-
Received:2025-03-25Online:2025-09-10Published:2025-09-18
CLC Number:
Cite this article
YANG Yukun, XIAO Weien, LIANG Boxuan, HUANG Xin. Dynamic Three-Factor Authentication Key Agreement Protocol for IoT Scenarios[J]. Netinfo Security, 2025, 25(9): 1407-1417.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.09.009
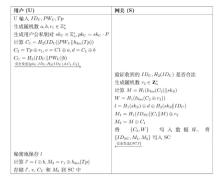
| 符号 | 描述 |
|---|---|
| 定义在有限素数域 | |
| 用户的身份标识和密码 | |
| 拥有一定存储和计算能力的智能卡 | |
| 用户输入的生物特征 | |
| 用户注册时录入的生物特征模板 | |
| 无碰撞哈希函数 | |
| 生物哈希函数 | |
| 异或操作 | |
| 连接操作 | |
| 会话密钥 |
| [1] | XIE Qi, WONG D S, WANG Guilin, et al. Provably Secure Dynamic ID-Based Anonymous Two-Factor Authenticated Key Exchange Protocol with Extended Security Model[J]. IEEE Transactions on Information Forensics & Security, 2017, 12(6): 1382-1392. |
| [2] | GOPE P. PMAKE: Privacy-Aware Multi-Factor Authenticated Key Establishment Scheme for Advance Metering Infrastructure in Smart Grid[J]. Computer Communications, 2020, 152: 338-344. |
| [3] | ZHOU Lu, GE Chunpeng, SU Chunhua. A Privacy Preserving Two-Factor Authentication Protocol for the Bitcoin SPV Nodes[J]. Science China Information Sciences, 2020, 63(3): 34-48. |
| [4] | HAQ I U, WANG Jian. Secure Two-Factor Lightweight Authentication Protocol Using Self-Certified Public Key Cryptography for Multi-Server 5G Networks[EB/OL]. (2020-07-01)[2025-03-21]. https://www.sciencedirect.com/science/article/abs/pii/S108480452030134X. |
| [5] | BADAR H M S, QADRI S, SHAMSHAD S, et al. An Identity Based Authentication Protocol for Smart Grid Environment Using Physical Uncloneable Function[J]. IEEE Transactions on Smart Grid, 2021, 12(5): 4426-4434. |
| [6] | ZHANG Xin, HUANG Xin, YIN Haotian, et al. LLAKEP: A Low-Latency Authentication and Key Exchange Protocol for Energy Internet of Things in the Metaverse Era[EB/OL]. (2022-07-21)[2025-03-21]. https://www.mdpi.com/2227-7390/10/14/2545. |
| [7] | QI Mingping. An Improved Three-Factor Authentication and Key Agreement Protocol for Smart Grid[J]. Journal of Ambient Intelligence and Humanized Computing, 2023, 14(12): 16465-16476. |
| [8] | MEHTA P J, PARNE B L, PATEL S J. MAKA: Multi-Factor Authentication and Key Agreement Scheme for LoRa-Based Smart Grid Communication Services[J]. IETE Journal of Research, 2023, 70(5): 4989-5005. |
| [9] | SHUKLA S, PATEL S J. A Novel ECC-Based Provably Secure and Privacy-Preserving Multi-Factor Authentication Protocol for Cloud Computing[J]. Computing, 2022, 104(5): 1173-1202. |
| [10] | SHUKLA S, PATEL S J. A Design of Provably Secure Multi-Factor ECC-Based Authentication Protocol in Multi-Server Cloud Architecture[J]. Cluster Computing, 2024, 27(2): 1559-1580. |
| [11] | BRAEKEN A. Highly Efficient Bidirectional Multifactor Authentication and Key Agreement for Real-Time Access to Sensor Data[J]. IEEE Internet of Things Journal, 2023, 10(23): 21089-21099. |
| [12] | ZHANG Shiwen, YAN Ziwei, LIANG Wei, et al. BAKA: Biometric Authentication and Key Agreement Scheme Based on Fuzzy Extractor for Wireless Body Area Networks[J]. IEEE Internet of Things Journal, 2023, 11(3): 5118-5128. |
| [13] | MALL P, AMIN R, DAS A K, et al. PUF-Based Authentication and Key Agreement Protocols for IoT, WSNs, and Smart Grids: A Comprehensive Survey[J]. IEEE Internet of Things Journal, 2022, 9(11): 8205-8228. |
| [14] | DEVANAPALLI S, PHANEENDRA K. Security Analysis of Three-Factor Authentication Protocol Based on Extended Chaotic-Maps[C]// IEEE. 2022 OPJU International Technology Conference on Emerging Technologies for Sustainable Development (OTCON). New York: IEEE, 2023: 1-6. |
| [15] | QIU Shuming, WANG Ding, XU Guoai, et al. Practical and Provably Secure Three-Factor Authentication Protocol Based on Extended ChaoticMmaps for Mobile Lightweight Devices[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 19(2): 1338-1351. |
| [16] | LEE J, YU S, KIM M, et al. On the Design of Secure and Efficient Three-Factor Authentication Protocol Using Honey List for Wireless Sensor Networks[J]. IEEE Access, 2020, 8: 107046-107062. |
| [17] | CHAKRABORTY N, LI Jiangqiang, LEUNG V C M, et al. Honeyword-Based Authentication Techniques for Protecting Passwords: A Survey[J]. ACM Computing Surveys, 2022, 55(8): 1-37. |
| [18] | HUANG Zonghao, BAUER L, REITER M K. The Impact of Exposed Passwords on Honeyword Efficacy[C]// USENIX. 33th USENIX Security Symposium. Berkeley:USENIX,2024: 559-576. |
| [19] | FAN C, LIN Yihui. Provably Secure Remote Truly Three-Factor Authentication Scheme with Privacy Protection on Biometrics[J]. IEEE Transactions on Information Forensics and Security, 2009, 4(4): 933-945. |
| [20] | ZHANG Liping, ZHANG Yixin, TANG Shanyu, et al. Privacy Protection for E-Health Systems by Means of Dynamic Authentication and Three-Factor Key Agreement[J]. IEEE Transactions on Industrial Electronics, 2017, 65(3): 2795-2805. |
| [21] | KOBLITZ N. Elliptic Curve Cryptosystems[J]. Mathematics of Computation, 1987, 48(177): 203-209. |
| [22] | MILLER V S. Use of Elliptic Curves in Cryptography[C]// Springer. Conference on the Theory and Application of Cryptographic Techniques. Heidelberg: Springer, 1985: 417-426. |
| [23] | JIN A T B, LING D N C, GOH A. Biohashing: Two Factor Authentication Featuring Fingerprint Data and Tokenised Random Number[J]. Pattern Recognition, 2004, 37(11): 2245-2255. |
| [24] | RATHA N, CONNELL J, BOLLE R M, et al. Cancelable Biometrics: A Case Study in Fingerprints[C]// IEEE.18th International Conference on Pattern Recognition (ICPR’06). New York: IEEE, 2006: 370-373. |
| [25] | LUMINI A, NANNI L. An Improved Biohashing for Human Authentication[J]. Pattern Recognition, 2007, 40(3): 1057-1065. |
| [26] | TEOH A B J, KUAN Y W, LEE S. Cancellable Biometrics and Annotations on Biohash[J]. Pattern Recognition, 2008, 41(6): 2034-2044. |
| [27] | HANKERSON D, MENEZES A. NIST Elliptic Curves[M]. Heidelberg: Springer, 2025. |
| [1] | WANG Mei, YANG Xiaoran, LI Zengpeng. Research on Simple and Low Interaction Authentication Protocols for IoT Devices [J]. Netinfo Security, 2025, 25(7): 1032-1043. |
| [2] | ZHANG Xuewang, CHEN Siyu, LUO Xinyue, LEI Zhitao, XIE Haofei. Efficient Searchable Attribute-Based Encryption Scheme for Cloud-Assisted Industrial IoT [J]. Netinfo Security, 2024, 24(9): 1352-1363. |
| [3] | LI Zhihua, CHEN Liang, LU Xulin, FANG Zhaohui, QIAN Junhao. Lightweight Detection Method for IoT Mirai Botnet [J]. Netinfo Security, 2024, 24(5): 667-681. |
| [4] | YIN Jie, CHEN Pu, YANG Guinian, XIE Wenwei, LIANG Guangjun. Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence [J]. Netinfo Security, 2024, 24(11): 1615-1623. |
| [5] | ZHANG Min, FENG Yongqiang, XU Chunxiang, ZHANG Jianhua. Research on Multi-Factor Authenticated Key Agreement Protocol for Smart Home Networks [J]. Netinfo Security, 2024, 24(1): 133-142. |
| [6] | YIN Chunyong, JIANG Yiyang. Differential Privacy Trajectory Protection Model Based on Personalized Spatiotemporal Clustering [J]. Netinfo Security, 2024, 24(1): 80-92. |
| [7] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [8] | ZHANG Min, XU Chunxiang, ZHANG Jianhua. Research on Authentication Key Agreement Protocol Based on Multi-Factor in Internet of Drones [J]. Netinfo Security, 2022, 22(9): 21-30. |
| [9] | LIU Qin, ZHANG Biao, TU Hang. Certificateless Blind Signature Scheme Based on twisted Edwards Curve [J]. Netinfo Security, 2022, 22(8): 19-25. |
| [10] | WU Kehe, CHENG Rui, JIANG Xiaochen, ZHANG Jiyu. Security Protection Scheme of Power IoT Based on SDP [J]. Netinfo Security, 2022, 22(2): 32-38. |
| [11] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [12] | LIU Xin, YANG Haorui, GUO Zhenbin, WANG Jiayin. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(7): 1-9. |
| [13] | WANG Kaixuan, TENG Yajun, WANG Qiongxiao, WANG Wei. Research on the Application of SM Algorithms of Implicit Certificate [J]. Netinfo Security, 2021, 21(5): 74-81. |
| [14] | XU Huikai, LIU Yue, MA Zhenbang, DUAN Haixin. A Large-scale Measurement Study of MQTT Security [J]. Netinfo Security, 2020, 20(9): 37-41. |
| [15] | SHI Runhua, SHI Ze. Key Management Scheme for IoT Based on Blockchain Technology [J]. Netinfo Security, 2020, 20(8): 1-8. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||