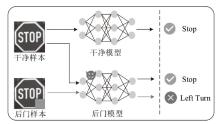
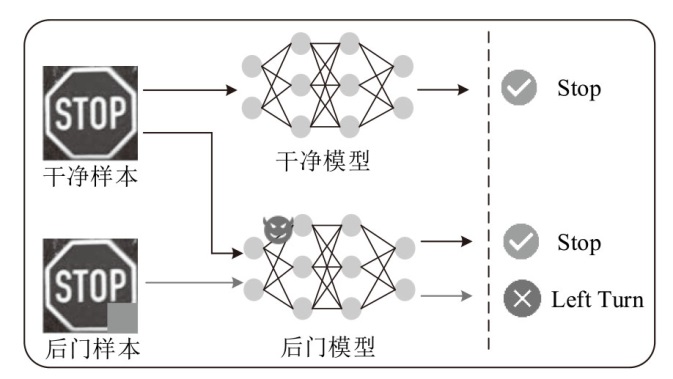
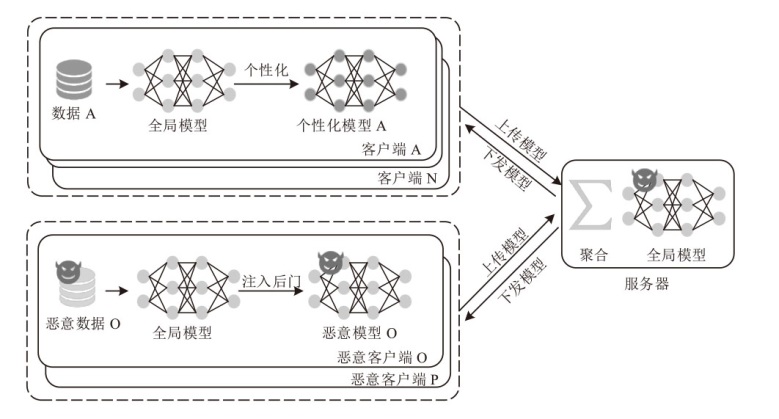
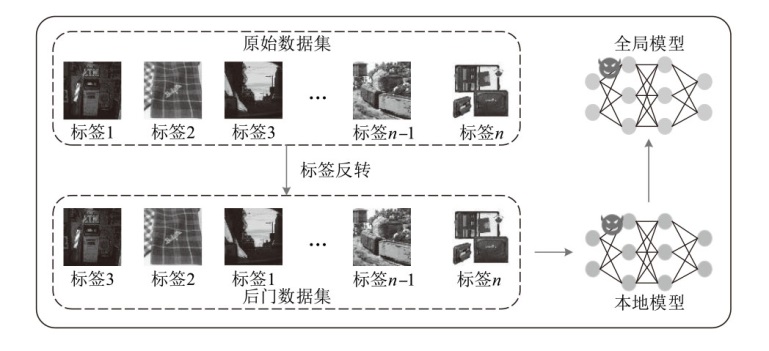
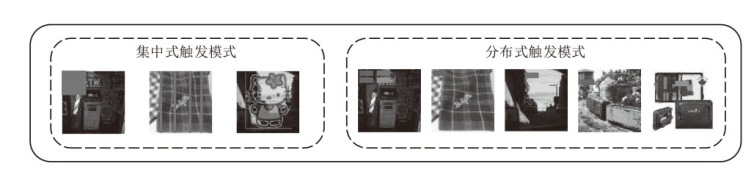
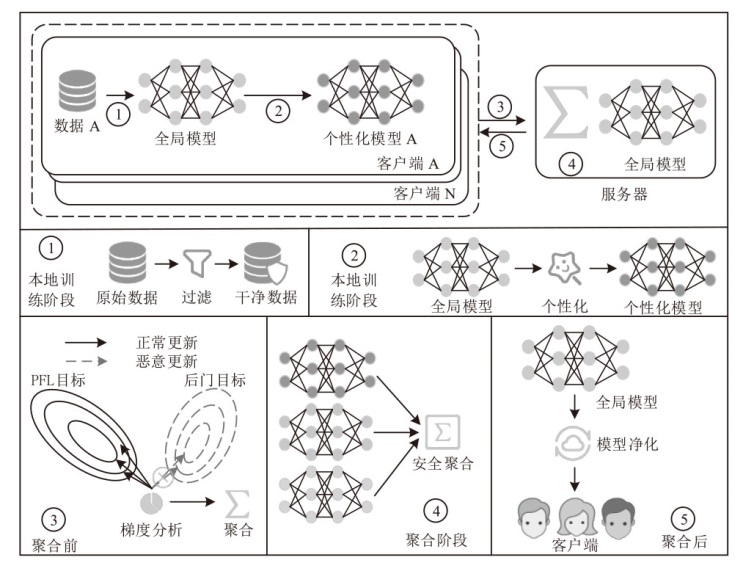
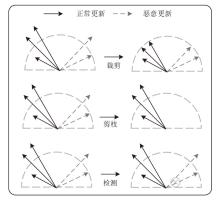
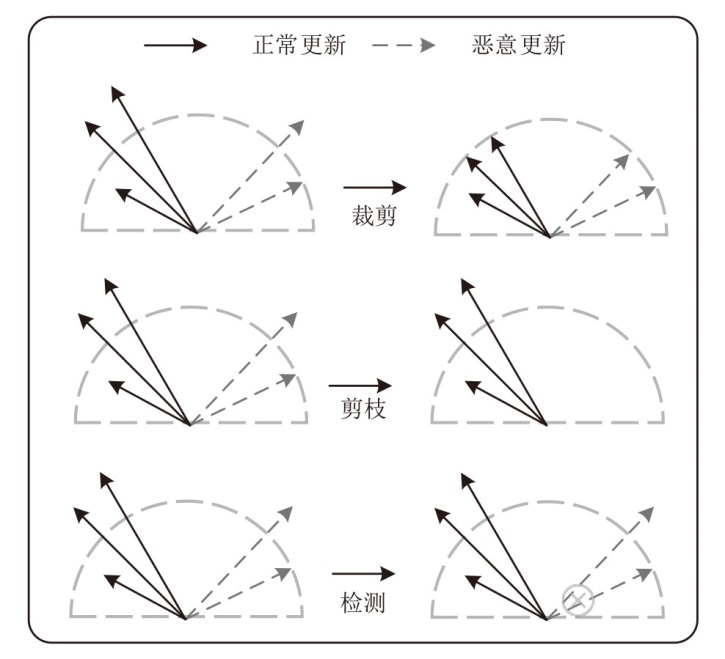
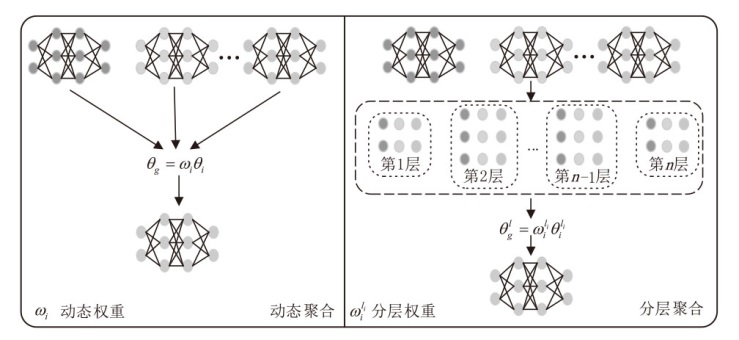
Netinfo Security ›› 2025, Vol. 25 ›› Issue (9): 1418-1438.doi: 10.3969/j.issn.1671-1122.2025.09.010
Previous Articles Next Articles
Overview of Backdoor Attacks and Defenses in Personalized Federated Learning
CHEN Xianyi1,2,3,4, WANG Xuebo2,3, CUI Qi1,2,3, FU Zhangjie1,2,3, WANG Qianqian2,3, ZENG Yifu5,6( )
)
- 1. Engineering Research Center of Digital Forensics Ministry of Education, Nanjing University of Information Science and Technology, Nanjing 210044, China
2. School of Computer Science, Nanjing University of Information Science and Technology, Nanjing 210044, China
3. School of Cyberspace Security, Nanjing University of Information Science and Technology, Nanjing 210044, China
4. Jiangsu Yuchi Blockchain Technology Research Institute Co., Ltd., Nanjing 210000, China
5. The Second Affiliated Hospital of Fujian Medical University, Quanzhou 362100, China
6. The School of Cyber Science and Technology, Guangzhou University, Guangzhou 510006, China
-
Received:2025-06-13Online:2025-09-10Published:2025-09-18
CLC Number:
Cite this article
CHEN Xianyi, WANG Xuebo, CUI Qi, FU Zhangjie, WANG Qianqian, ZENG Yifu. Overview of Backdoor Attacks and Defenses in Personalized Federated Learning[J]. Netinfo Security, 2025, 25(9): 1418-1438.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.09.010
| 名称 | 攻击类型 | 年份 | 数据分布 | 攻击类型 | 攻击适应性 | 应用 场景 | |||
|---|---|---|---|---|---|---|---|---|---|
| 黑盒攻击 | 白盒攻击 | 持续攻击 | 共谋攻击 | 完整模型共享的PFL | 部分模型共享的PFL | ||||
| PFedBA[ | × | √ | 2024 | Non-IID | √ | √ | √ | √ | 图像分类、贷款预测 |
| DBA[ | √ | × | 2020 | Non-IID | × | √ | √ | × | 图像分类 |
| CoBA[ | × | √ | 2024 | Non-IID | × | √ | √ | × | 图像分类、贷款预测 |
| 模型替换攻击[ | × | √ | 2020 | Non-IID | × | × | √ | × | 图像分类 |
| Edge[ | √ | √ | 2020 | Non-IID | √ | × | √ | × | 图像分类、单词分类、情感分析 |
| BadSFL[ | √ | × | 2024 | Non-IID | √ | × | √ | × | 图像分类 |
| FCBA[ | √ | √ | 2024 | Non-IID | × | √ | √ | × | 图像分类 |
| LFA[ | × | √ | 2024 | Non-IID | √ | √ | √ | × | 图像分类 |
| Neurotoxin[ | × | √ | 2022 | IID/Non-IID | √ | × | √ | × | 图像分类、单词分类 |
| BapFL[ | × | √ | 2024 | Non-IID | √ | × | √ | √ | 图像分类 |
| Bad-PFL[ | × | √ | 2025 | Non-IID | √ | √ | √ | √ | 图像分类 |
| PoisonGAN[ | √ | × | 2020 | IID | √ | √ | √ | × | 图像分类 |
| Mostly[ | √ | × | 2022 | IID/Non-IID | √ | × | √ | × | 图像分类 |
| Federated- Reverse[ | √ | × | 2021 | IID/Non-IID | √ | × | √ | × | 图像分类 |
| RLBFL[ | × | √ | 2023 | IID | √ | √ | √ | × | 图像分类 |
| 3DFed[ | × | √ | 2023 | Non-IID | √ | √ | √ | × | 图像分类 |
| A3FL[ | × | √ | 2023 | Non-IID | √ | √ | √ | × | 图像分类 |
| IBA[ | × | √ | 2023 | Non-IID | √ | × | √ | × | 图像分类 |
| 防御 阶段 | 名称 | 年份 | 防御策略 | 兼容安全聚合 | 防御位置 | PFL加剧 | 应用场景 | |
|---|---|---|---|---|---|---|---|---|
| 客户端 | 服务器 | |||||||
| 本地训练阶段 | 文献[ 方案 | 2021 | 中毒数据过滤 | √ | √ | × | √ | 图像分类 |
| PFL-ALB[ | 2025 | 分层聚合、个性化分层 | × | √ | √ | √ | 图像分类 | |
| FedNor[ | 2024 | 个性化训练、统计异常检测 | × | √ | √ | √ | 图像分类 | |
| PR-PFL[ | 2024 | 差分隐私、鲁棒聚合、个性化训练 | × | √ | √ | √ | 图像分类 | |
| BDPFL[ | 2025 | 层次化蒸馏、个性化训练 | √ | √ | × | √ | 图像分类 | |
| FedPD[ | 2024 | 交换原型模型 | × | √ | × | √ | 图像分类 | |
| pFedSAM[ | 2024 | 个性化训练 | √ | √ | × | √ | 图像分类 | |
| SARS[ | 2024 | 个性化训练 | √ | √ | × | √ | 图像分类 | |
| 聚合前防御 | FLAME[ | 2022 | 模型聚类、权重衰减、差分隐私 | × | √ | √ | √ | 图像分类、单词预测 |
| 文献[ 方案 | 2019 | 差分隐私 | × | √ | × | √ | 图像分类 | |
| 文献[ 方案 | 2020 | 降维 | × | × | √ | √ | 图像分类、情感分析 | |
| 文献[ 方案 | 2021 | 降维 | × | × | √ | √ | 图像分类 | |
| 聚合阶段防御 | 文献[ 方案 | 2021 | 模型相似度 | × | × | √ | √ | 图像分类、情感分类 |
| FL-PLAS[ | 2018 | 个性化层特性 | × | √ | √ | √ | 图像分类 | |
| 文献[ 方案 | 2023 | 统计方法 | × | × | √ | √ | 图像分类 | |
| 聚合后防御 | FedEraser[ | 2021 | 遗忘学习 | × | × | √ | √ | 图像分类、单词预测 |
| 文献[ 方案 | 2022 | 遗忘学习 | × | × | √ | √ | 图像分类 | |
| Baffle[ | 2021 | 联合测试 | √ | × | √ | √ | 图像分类 | |
| 防御方法 | 攻击方法 | SCAFFOLD[ | PFEDME[ | Ditto[ | FedRep[ | FedALA[ |
|---|---|---|---|---|---|---|
| FLAME[ | Neurotoxin[ | 90.1/8.7 | 98.5/10.4 | 91.3/10.6 | 88.2/13.2 | 89.4/37.0 |
| CerP[ | 91.4/32.9 | 98.5/10.7 | 91.9/9.3 | 87.7/15.9 | 89.0/19.8 | |
| PFedBA [ | 89.2/92.1 | 89.4/98.8 | 91.5/95.9 | 88.7/87.0 | 89.3/99.7 | |
| MKrum[ | Neurotoxin[ | 91.5/9.0 | 90.0/10.4 | 91.9/10.7 | 88.6/11.1 | 89.5/8.8 |
| CerP[ | 92.3/42.5 | 90.0/10.7 | 92.1/9.6 | 88.9/22.7 | 89.6/9.3 | |
| PFedBA [ | 91.3/97.4 | 89.8/99.3 | 91.7/97.4 | 89.1/91.9 | 89.3/99.9 | |
| Trim[ | Neurotoxin[ | 91.3/20.5 | 89.8/11.8 | 91.7/17.0 | 89.0/11.0 | 89.6/27.5 |
| CerP[ | 92.3/48.8 | 89.9/14.0 | 92.0/27.7 | 89.1/18.8 | 89.6/39.4 | |
| PFedBA [ | 91.4/97.1 | 89.7/98.5 | 91.7/95.6 | 89.3/88.8 | 89.7/99.5 | |
| DnC[ | Neurotoxin[ | 91.4/25.9 | 90.0/11.7 | 91.9/20.4 | 88.9/12.0 | 89.3/34.7 |
| CerP[ | 92.2/57.4 | 89.9/13.8 | 92.1/34.0 | 89.2/35.8 | 89.4/47.2 | |
| PFedBA [ | 91.5/97.3 | 89.9/97.9 | 91.9/96.7 | 88.6/91.5 | 89.3/99.8 |
| [1] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[C]// PMLR. Artificial Intelligence and Statistics. New York: PMLR, 2017: 1273-1282. |
| [2] | QIAO Cheng, ZENG Yanqing, LU Hui, et al. An Efficient Incentive Mechanism for Federated Learning in Vehicular Networks[J]. IEEE Network, 2023, 38(5): 189-195. |
| [3] | ZHAO J, BAGCHI S, AVESTIMEHR S, et al. The Federation Strikes Back: A Survey of Federated Learning Privacy Attacks, Defenses, Applications, and Policy Landscape[J]. ACM Computing Surveys, 2025, 57(9): 1-37. |
| [4] | LIU Yang, HUANG Anbu, LUO Yun, et al. Fedvision: An Online Visual Object Detection Platform Powered by Federated Learning[C]// AAAI. The AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2020: 13172-13179. |
| [5] | WANG Qingyong, ZHOU Yun. FedSPL: Federated Self-Paced Learning for Privacy-Preserving Disease Diagnosis[EB/OL]. (2021-12-07)[2025-06-10]. https://doi.org/10.1093/bib/bbab498. |
| [6] | XU An, LI Wenqi, GUO Pengfei, et al. Closing the Generalization Gap of Cross-Silo Federated Medical Image Segmentation[C]// IEEE. The IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2022: 20866-20875. |
| [7] | WAHAB O A, RJOUB G, BENTAHAR J, et al. Federated against the Cold: A Trust-Based Federated Learning Approach to Counter the Cold Start Problem in Recommendation Systems[J]. Information Sciences, 2022, 601: 189-206. |
| [8] | WAN Yichen, QU Youyang, NI Wei, et al. Data and Model Poisoning Backdoor Attacks on Wireless Federated Learning, and the Defense Mechanisms: A Comprehensive Survey[J]. IEEE Communications Surveys & Tutorials, 2024, 26(3): 1861-1897. |
| [9] | QIN Zeyu, YAO Liuyi, CHEN Daoyuan, et al. Revisiting Personalized Federated Learning: Robustness against Backdoor Attacks[C]// ACM. The 29th ACM SIGKDD Conference on Knowledge Discovery and Data Mining. New York: ACM, 2023: 4743-4755. |
| [10] | WANG Kangkang, MATHEWS R, KIDDON C, et al. Federated Evaluation of On-Device Personalization[EB/OL]. (2019-10-22)[2025-06-10]. https://doi.org/10.48550/arXiv.1910.10252. |
| [11] | YANG Chen, WANG Yingchao, LAN Shulin, et al. Cloud-Edge-Device Collaboration Mechanisms of Deep Learning Models for Smart Robots in Mass Personalization[EB/OL]. (2022-03-28)[2025-06-10]. https://doi.org/10.1016/j.rcim.2022.102351. |
| [12] | SHEN Tao, LI Zexi, ZHAO Ziyu, et al. An Adaptive Aggregation Method for Federated Learning via Meta Controller[EB/OL]. (2024-12-26)[2025-06-10]. https://doi.org/10.1145/3700410.3702124. |
| [13] | FALLAH A, MOKHTARI A, OZDAGLAR A. Personalized Federated Learning with Theoretical Guarantees: A Model-Agnostic Meta-Learning Approach[J]. Advances in Neural Information Processing Systems, 2020, 33: 3557-3568. |
| [14] | LI Tian, HU Shengyuan, BEIRAMI A, et al. Ditto: Fair and Robust Federated Learning through Personalization[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2021: 6357-6368. |
| [15] | DINH C T, TRAN N H, NGUYEN J D. Personalized Federated Learning with Moreau Envelopes[J]. Advances in Neural Information Processing Systems, 2020, 33: 21394-21405. |
| [16] | COLLINS L, HASSANI H, MOKHTARI A, et al. Exploiting Shared Representations for Personalized Federated Learning[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2021: 2089-2099. |
| [17] | ARIVAZHAGAN M G, AGGARWAL V, SINGH A K, et al. Federated Learning with Personalization Layers[EB/OL]. (2019-12-02)[2025-06-10]. https://doi.org/10.48550/arXiv.1912.00818. |
| [18] | LI Xiaoxiao, JIANG Meirui, ZHANG Xiaofei, et al. Fedbn: Federated Learning on Non-IId Features via Local Batch Normalization[EB/OL]. (2021-05-11)[2025-06-10]. https://doi.org/10.48550/arXiv.2102.07623. |
| [19] | YANG Zhiqin, ZHANG Yonggang, ZHENG Yu, et al. Fedfed: Feature Distillation against Data Heterogeneity in Federated Learning[J]. Advances in Neural Information Processing Systems, 2023, 36: 60397-60428. |
| [20] | LYU Yangzixing, SHI Wei, ZHANG Weiyong, et al. Do Not Trust the Clouds Easily: The Insecurity of Content Security Policy Based on Object Storage[J]. IEEE Internet of Things Journal, 2023, 10(12): 10462-10470. |
| [21] | LU Hui, JIN Chengjie, HELU Xiaohan, et al. DeepAutoD: Research on Distributed Machine Learning Oriented Scalable Mobile Communication Security Unpacking System[J]. IEEE Transactions on Network Science and Engineering, 2021, 9(4): 2052-2065. |
| [22] | LYU Xiaoting, HAN Yufei, WANG Wei, et al. Lurking in the Shadows: Unveiling Stealthy Backdoor Attacks against Personalized Federated Learning[C]// USENIX. 33rd USENIX Security Symposium. Berkeley: USENIX, 2024: 4157-4174. |
| [23] |
GU Tianyu, LIU Kang, DOLAN-GAVITT B, et al. BadNets: Evaluating Backdooring Attacks on Deep Neural Networks[J]. IEEE Access, 2019, 7: 47230-47244.
doi: 10.1109/ACCESS.2019.2909068 |
| [24] | GU Zhaoquan, HU Weixiong, ZHANG Chuanjing, et al. Gradient Shielding: Towards Understanding Vulnerability of Deep Neural Networks[J]. IEEE Transactions on Network Science and Engineering, 2020, 8(2): 921-932. |
| [25] | SABAH F, CHEN Yuwen, YANG Zhen, et al. Model Optimization Techniques in Personalized Federated Learning: A Survey[EB/OL]. (2024-06-01)[2025-06-10]. https://doi.org/10.1016/j.eswa.2023.122874. |
| [26] | RODRÍGUEZ-BARROSO N, MARTÍNEZ-CÁMARA E, LUZÓN M V, et al. Backdoor Attacks-Resilient Aggregation Based on Robust Filtering of Outliers in Federated Learning for Image Classification[EB/OL]. (2022-04-07)[2025-06-10]. https://doi.org/10.1016/j.knosys.2022.108588. |
| [27] | NGUYEN T D, RIEGER P, DE V R, et al. FLAME: Taming Backdoors in Federated Learning[C]// USENIX. 31st USENIX Security Symposium. Berkeley: USENIX, 2022: 1415-1432. |
| [28] | HOU Boyu, GAO Jiqiang, GUO Xiaojie, et al. Mitigating the Backdoor Attack by Federated Filters for Industrial IoT Applications[J]. IEEE Transactions on Industrial Informatics, 2021, 18(5): 3562-3571. |
| [29] | KARIMIREDDY S P, KALE S, MOHRI M, et al. SCAFFOLD: Stochastic Controlled Averaging for Federated Learning[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2020: 5132-5143. |
| [30] | SCHWARZSCHILD A, GOLDBLUM M, GUPTA A, et al. Just How Toxic Is Data Poisoning? A Unified Benchmark for Backdoor and Data Poisoning Attacks[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2021: 9389-9398. |
| [31] | YERLIKAYA F A, BAHTIYAR Ş. Data Poisoning Attacks against Machine Learning Algorithms[EB/OL]. (2022-12-01)[2025-06-10]. https://doi.org/10.1016/j.eswa.2022.118101. |
| [32] | XIE Chulin, HUANG Keli, CHEN P, et al. DBA: Distributed Backdoor Attacks against Federated Learning[EB/OL]. (2020-04-26)[2025-06-10]. https://research.ibm.com/publications/dba-distributed-backdoor-attacks-against-federated-learning. |
| [33] | LYU Xiaoting, HAN Yufei, WANG Wei, et al. CoBA: Collusive Backdoor Attacks with Optimized Trigger to Federated Learning[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 22(2): 1506-1518. |
| [34] | BAGDASARYAN E, VEIT A, HUA Yiqing, et al. How to Backdoor Federated Learning[C]// PMLR. International Conference on Artificial Intelligence and Statistics. New York: PMLR, 2020: 2938-2948. |
| [35] | VARMA K, ZHOU Yi, BARACALDO N, et al. LEGATO: A Layerwise Gradient Aggregation Algorithm for Mitigating Byzantine Attacks in Federated Learning[C]// IEEE. 2021 IEEE 14th International Conference on Cloud Computing. New York: IEEE, 2021: 272-277. |
| [36] | GOUISSEM A, ABUALSAUD K, YAACOUB E, et al. Federated Learning Stability under Byzantine Attacks[C]// IEEE. 2022 IEEE Wireless Communications and Networking Conference. New York: IEEE, 2022: 572-577. |
| [37] | MA Xindi, JIANG Qi, SHOJAFAR M, et al. DisBezant: Secure and Robust Federated Learning against Byzantine Attack in IoT-Enabled MTS[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 24(2): 2492-2502. |
| [38] | SHEN Guangyu, LIU Yingqi, TAO Guanhong, et al. Backdoor Scanning for Deep Neural Networks through K-Arm Optimization[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2021: 9525-9536. |
| [39] | XIE Chulin, CHEN Minghao, CHEN P, et al. CRFL: Certifiably Robust Federated Learning against Backdoor Attacks[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2021: 11372-11382. |
| [40] | ZHANG Kai, ZHANG Yanjun, SUN Ruoxi, et al. Bounded and Unbiased Composite Differential Privacy[C]// IEEE. 2024 IEEE Symposium on Security and Privacy. New York: IEEE, 2024: 972-990. |
| [41] | WANG Hongyi, SREENIVASAN K, RAJPUT S, et al. Attack of the Tails: Yes, You Really Can Backdoor Federated Learning[J]. Advances in Neural Information Processing Systems, 2020, 33: 16070-16084. |
| [42] | HAN Xingshuo, ZHANG Xuanye, LAN Xiang, et al. BadSFL: Backdoor Attack against Scaffold Federated Learning[EB/OL]. (2024-11-26)[2025-06-10]. https://arxiv.org/html/2411.16167v2. |
| [43] | LIU Tao, ZHANG Yuhang, FENG Zhu, et al. Beyond Traditional Threats: A Persistent Backdoor Attack on Federated Learning[C]// AAAI. The AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2024: 21359-21367. |
| [44] | ZHUANG Haomin, YU Mingxian, WANG Hao, et al. Backdoor Federated Learning by Poisoning Backdoor-Critical Layers[EB/OL]. (2024-12-31)[2025-06-10]. https://doi.org/10.3390/electronics14010129. |
| [45] | ZHANG Zhengming, PANDA A, SONG Linyue, et al. Neurotoxin: Durable Backdoors in Federated Learning[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2022: 26429-26446. |
| [46] | YE Tiandi, CHEN Cen, WANG Yinggui, et al. BapFL: You Can Backdoor Personalized Federated Learning[J]. ACM Transactions on Knowledge Discovery from Data, 2024, 18(7): 1-17. |
| [47] | LYU Xiaoting, HAN Yufei, WANG Wei, et al. Poisoning with Cerberus: Stealthy and Colluded Backdoor Attack against Federated Learning[C]// AAAI. The AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2023: 9020-9028. |
| [48] | FAN Mingyuan, HU Zhanyi, WANG Fuyi, et al. Bad-PFL: Exploring Backdoor Attacks against Personalized Federated Learning[EB/OL]. (2025-01-22)[2025-06-10]. https://doi.org/10.48550/arXiv.2501.12736. |
| [49] | JEBREEL N M, DOMINGO-FERRER J. FL-Defender: Combating Targeted Attacks in Federated Learning[EB/OL]. (2022-07-02)[2025-06-10]. https://doi.org/10.48550/arXiv.2207.00872. |
| [50] | CHEN Congcong, WEI Lifei, ZHANG Lei, et al. DeepGuard: Backdoor Attack Detection and Identification Schemes in Privacy-Preserving Deep Neural Networks[EB/OL]. (2022-01-01)[2025-06-10]. https://doi.org/10.1155/2022/298530. |
| [51] | ZHANG Jiale, CHEN Bing, CHENG Xiang, et al. PoisonGAN: Generative Poisoning Attacks against Federated Learning in Edge Computing Systems[J]. IEEE Internet of Things Journal, 2020, 8(5): 3310-3322. |
| [52] | XU Jing, WANG Rui, KOFFAS S, et al. More Is Better (Mostly): On the Backdoor Attacks in Federated Graph Neural Networks[C]// IEEE. The 38th Annual Computer Security Applications Conference. New York: IEEE, 2022: 684-698. |
| [53] | ZHAO Chen, WEN Yu, LI Shuailou, et al. Federatedreverse: A Detection and Defense Method against Backdoor Attacks in Federated Learning[C]// ACM. The 2021 ACM Workshop on Information Hiding and Multimedia Security. New York: ACM, 2021: 51-62. |
| [54] | LI Henger, WU Chen, ZHU Sencun, et al. Learning to Backdoor Federated Learning[EB/OL]. (2023-05-28)[2025-06-10]. https://doi.org/10.48550/arXiv.2303.03320. |
| [55] | LI Haoyang, YE Qingqing, HU Haibo, et al. 3DFed: Adaptive and Extensible Framework for Covert Backdoor Attack in Federated Learning[C]// IEEE. 2023 IEEE Symposium on Security and Privacy. New York: IEEE, 2023: 1893-1907. |
| [56] | ZHANG Hangfan, JIA Jinyuan, CHEN Jinghui, et al. A3FL: Adversarially Adaptive Backdoor Attacks to Federated Learning[J]. Advances in Neural Information Processing Systems, 2023, 36: 61213-61233. |
| [57] | NGUYEN T D, NGUYEN T A, TRAN A, et al. IBA: Towards Irreversible Backdoor Attacks in Federated Learning[J]. Advances in Neural Information Processing Systems, 2023, 36: 66364-66376. |
| [58] | WANG Bolun, YAO Yuanshun, SHAN S, et al. Neural Cleanse: Identifying and Mitigating Backdoor Attacks in Neural Networks[C]// IEEE.2019 IEEE Symposium on Security and Privacy. New York: IEEE, 2019: 707-723. |
| [59] | LI Yige, LYU Xixiang, KOREN N, et al. Neural Attention Distillation: Erasing Backdoor Triggers from Deep Neural Networks[EB/OL]. (2021-01-27)[2025-06-10]. https://doi.org/10.48550/arXiv.2101.05930. |
| [60] | QIU Han, ZENG Yi, GUO Shangwei, et al. DeepSweep: An Evaluation Framework for Mitigating DNN Backdoor Attacks Using Data Augmentation[C]// ACM. The 2021 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021: 363-377. |
| [61] | WANG He, XU Zhen, ZHANG Yan, et al. Adaptive Layered-Trust Robust Defense Mechanism for Personalized Federated Learning[C]// IEEE. ICASSP 2025-2025 IEEE International Conference on Acoustics, Speech and Signal Processing. New York: IEEE, 2025: 1-5. |
| [62] | XU Shuo, XIA Hui, ZHANG Rui, et al. FedNor: A Robust Training Framework for Federated Learning Based on Normal Aggregation[EB/OL]. (2024-08-08)[2025-06-10]. https://doi.org/10.1016/j.ins.2024.121274. |
| [63] | YANG Ruiguang, SHEN Xiaodong, XU Chang, et al. PR-PFL: A Privacy-Preserving and Robust Personalized Federated Learning Framework[C]// IEEE. 2024 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery. New York: IEEE, 2024: 163-170. |
| [64] | ZHU Chengcheng, ZHANG Jiale, WU Di, et al. BDPFL: Backdoor Defense for Personalized Federated Learning via Explainable Distillation[EB/OL]. (2025-05-31)[2025-06-10]. https://doi.org/10.48550/arXiv.2503.06554. |
| [65] | TAN Zhuo, CAI Jianping, LI De, et al. FedPD: Defending Federated Prototype Learning against Backdoor Attacks[EB/OL]. (2024-12-20)[2025-06-10]. https://doi.org/10.1016/j.neunet.2024.107016. |
| [66] | ZHANG Zhenxiao, GUO Yuanxiong, GONG Yanmin. pFedSAM: Secure Federated Learning against Backdoor Attacks via Personalized Sharpness-Aware Minimization[EB/OL]. (2024-05-26)[2025-06-10]. https://openreview.net/forum?id=cz0kQD95o4. |
| [67] | ZHANG Weibin, LI Youpeng, AN Lingling, et al. SARS: A Personalized Federated Learning Framework Towards Fairness and Robustness against Backdoor Attacks[C]// ACM. The ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies, New York: ACM, 2024: 1-24. |
| [68] | SUN Ziteng, KAIROUZ P, SURESH A T, et al. Can You Really Backdoor Federated Learning[EB/OL]. (2019-12-02)[2025-06-10]. https://doi.org/10.48550/arXiv.1911.07963. |
| [69] | HUANG Tiansheng, HU Sihao, CHOW K H, et al. Lockdown: Backdoor Defense for Federated Learning with Isolated Subspace Training[J]. Advances in Neural Information Processing Systems, 2023, 36: 10876-10896. |
| [70] | ZUKAIB U, CUI Xiaohui. Mitigating Backdoor Attacks in Federated Learning Based Intrusion Detection Systems through Neuron Synaptic Weight Adjustment[EB/OL].(2025-04-08)[2025-06-10]. https://doi.org/10.1016/j.knosys.2025.113167. |
| [71] | LI Suyi, CHENG Yong, WANG Wei, et al. Learning to Detect Malicious Clients for Robust Federated Learning[EB/OL]. (2020-02-01)[2025-06-10]. https://doi.org/10.48550/arXiv.2002.00211. |
| [72] | GU Zhipin, YANG Yuexiang. Detecting Malicious Model Updates from Federated Learning on Conditional Variational Autoencoder[C]// IEEE. 2021 IEEE International Parallel and Distributed Processing Symposium. New York: IEEE, 2021: 671-680. |
| [73] | ZHANG Zaixi, CAO Xiaoyu, JIA Jinyuan, et al. FLDetector: Defending Federated Learning against Model Poisoning Attacks via Detecting Malicious Clients[C]// ACM. The 28th ACM SIGKDD Conference on Knowledge Discovery and Data Mining. New York: ACM, 2022: 2545-2555. |
| [74] | KUMARI K, RIEGER P, FEREIDOONI H, et al. BayBFed: Bayesian Backdoor Defense for Federated Learning[C]// IEEE. 2023 IEEE Symposium on Security and Privacy. New York: IEEE, 2023: 737-754. |
| [75] | ZHANG Zhiyuan, CHEN Deli, ZHOU Hao, et al. Fed-FA: Theoretically Modeling Client Data Divergence for Federated Language Backdoor Defense[J]. Advances in Neural Information Processing Systems, 2023, 36: 62006-62031. |
| [76] | KRAUß T, DMITRIENKO A. Mesas: Poisoning Defense for Federated Learning Resilient against Adaptive Attackers[C]// ACM. The 2023 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2023: 1526-1540. |
| [77] | HUANG Siquan, LI Yijiang, CHEN Chong, et al. Multi-Metrics Adaptively Identifies Backdoors in Federated Learning[C]// IEEE. The IEEE/CVF International Conference on Computer Vision. New York: IEEE, 2023: 4652-4662. |
| [78] | LI Yilong, ZHANG Jianyi, ZHOU Ziyin, et al. D2FL: Dimensional Disaster-Oriented Backdoor Attack Defense Of Federated Learning[C]// IEEE. 2024 IEEE 23rd International Conference on Trust, Security and Privacy in Computing and Communications. New York: IEEE, 2024: 1790-1796. |
| [79] | ARAMOON O, CHEN P, QU Gang, et al. Meta-Federated Learning[M]. Amsterdam: Academic Press, 2024. |
| [80] | WAN C P, CHEN Qifeng. Robust Federated Learning with Attack-Adaptive Aggregation[EB/OL]. (2021-08-06)[2025-06-10]. https://doi.org/10.48550/arXiv.2102.05257. |
| [81] | FAN Tingyu, CHEN Xiaojun, DONG Ye, et al. Lightweight Secure Aggregation for Personalized Federated Learning with Backdoor Resistance[C]// IEEE. 2024 Annual Computer Security Applications Conference. New York: IEEE, 2024: 810-825. |
| [82] | ZHANG Jianyi, ZHOU Ziyin, LI Yilong, et al. FL-PLAS: Federated Learning with Partial Layer Aggregation for Backdoor Defense against High-Ratio Malicious Clients[EB/OL]. (2025-05-17)[2025-06-10]. https://doi.org/10.48550/arXiv.2505.12019. |
| [83] | LIU Gaoyang, MA Xiaoqiang, YANG Yang, et al. FedEraser: Enabling Efficient Client-Level Data Removal from Federated Learning Models[C]// IEEE. 2021 IEEE/ACM 29th International Symposium on Quality of Service. New York: IEEE, 2021: 1-10. |
| [84] | WU Chen, ZHU Sencun, MITRA P. Federated Unlearning with Knowledge Distillation[EB/OL]. (2022-01-24)[2025-06-10]. https://doi.org/10.48550/arXiv.2201.09441. |
| [85] | ZHANG Yijian, ZHANG Tianxing, LIU Qi, et al. Increasing Depth, Distribution Distillation, and Model Soup: Erasing Backdoor Triggers for Deep Neural Networks[EB/OL]. (2022-11-08)[2025-06-10].https://doi.org/10.1117/1.JEI.31.6.063005. |
| [86] | ANDREINA S, MARSON G A, MÖLLERING H, et al. BaFFLE: Backdoor Detection via Feedback-Based Federated Learning[C]// IEEE. 2021 IEEE 41st International Conference on Distributed Computing Systems. New York: IEEE, 2021: 852-863. |
| [87] | DASHDONDOV K, KIM M H. Mahalanobis Distance Based Multivariate Outlier Detection to Improve Performance of Hypertension Prediction[J]. Neural Processing Letters, 2023, 55(1): 265-277. |
| [88] | TOLPEGIN V, TRUEX S, GURSOY M E, et al. Data Poisoning Attacks against Federated Learning Systems[C]// Springer. Computer Security-ESORICs 2020: 25th European Symposium on Research in Computer Security. Heidelberg: Springer, 2020: 480-501. |
| [89] | ZHANG Jianqing, YANG Hua, WANG Hao, et al. FedALA: Adaptive Local Aggregation for Personalized Federated Learning[C]// AAAI. The AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2023: 11237-11244. |
| [90] | BLANCHARD P, EL M E M, GUERRAOUI R, et al. Machine Learning with Adversaries: Byzantine Tolerant Gradient Descent[C]// NIPS. The 31st International Conference on Neural Information Processing Systems. Canbridge: MIT Press, 2017: 118-128. |
| [91] | YIN Dong, CHEN Yudong, KANNAN R, et al. Byzantine-Robust Distributed Learning: Towards Optimal Statistical Rates[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2018: 5650-5659. |
| [92] | SHEJWALKAR V, HOUMANSADR A. Manipulating the Byzantine: Optimizing Model Poisoning Attacks and Defenses for Federated Learning[EB/OL].[2025-06-10]. https://doi.org/10.14722/ndss.2021.24498. |
| [1] | YAN Yukun, TANG Peng, CHEN Rui, DU Ruochen, HAN Qilong. A Randomness Enhanced Bi-Level Optimization Defense Method against Data Poisoning Backdoor Attacks [J]. Netinfo Security, 2025, 25(7): 1074-1091. |
| [2] | DENG Dongshang, WANG Weiye, ZHANG Weidong, WU Xuangou. Layered Personalized Federated Learning Guided by Model Feature Orientation [J]. Netinfo Security, 2025, 25(6): 889-897. |
| [3] | GU Huanhuan, LI Qianmu, LIU Zhen, WANG Fangyuan, JIANG Yu. Research on Hidden Backdoor Prompt Attack Methods Based on False Demonstrations [J]. Netinfo Security, 2025, 25(4): 619-629. |
| [4] | XIA Hui, QIAN Xiangyun. Invisible Backdoor Attack Based on Feature Space Similarity [J]. Netinfo Security, 2024, 24(8): 1163-1172. |
| [5] | LIN Yihang, ZHOU Pengyuan, WU Zhiqian, LIAO Yong. Federated Learning Backdoor Defense Method Based on Trigger Inversion [J]. Netinfo Security, 2024, 24(2): 262-271. |
| [6] | REN Shixuan, WANG Maoyu, ZHAO Hui. An Improved Method of Backdoor Attack in DNN [J]. Netinfo Security, 2021, 21(5): 82-89. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||