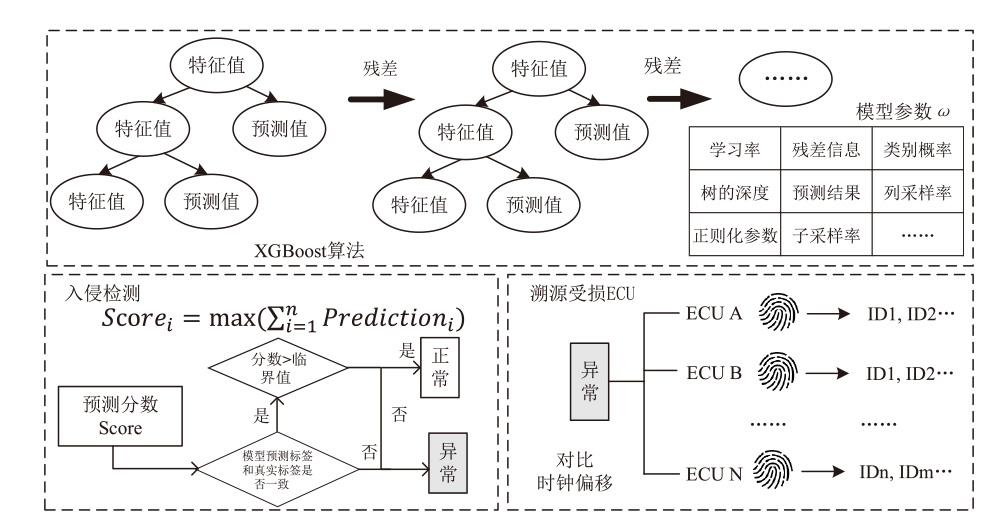
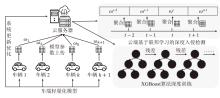
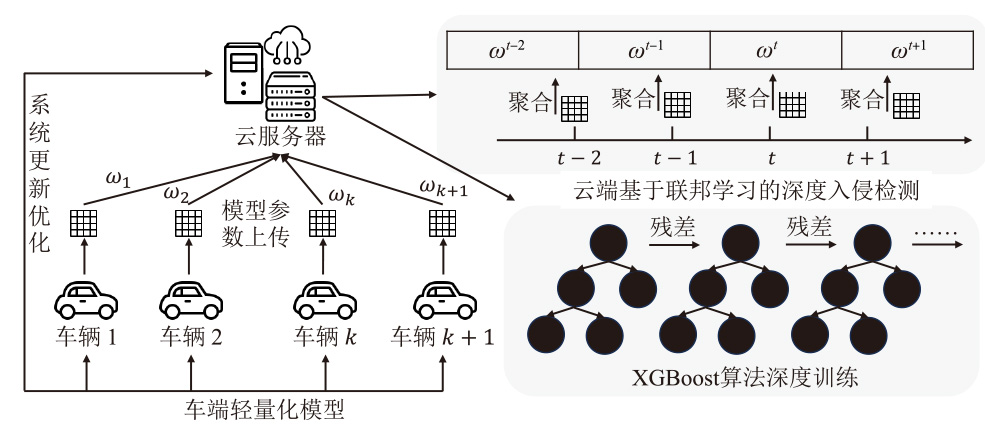
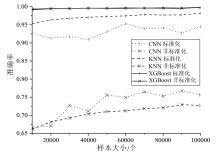
Netinfo Security ›› 2025, Vol. 25 ›› Issue (6): 872-888.doi: 10.3969/j.issn.1671-1122.2025.06.003
Previous Articles Next Articles
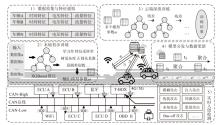
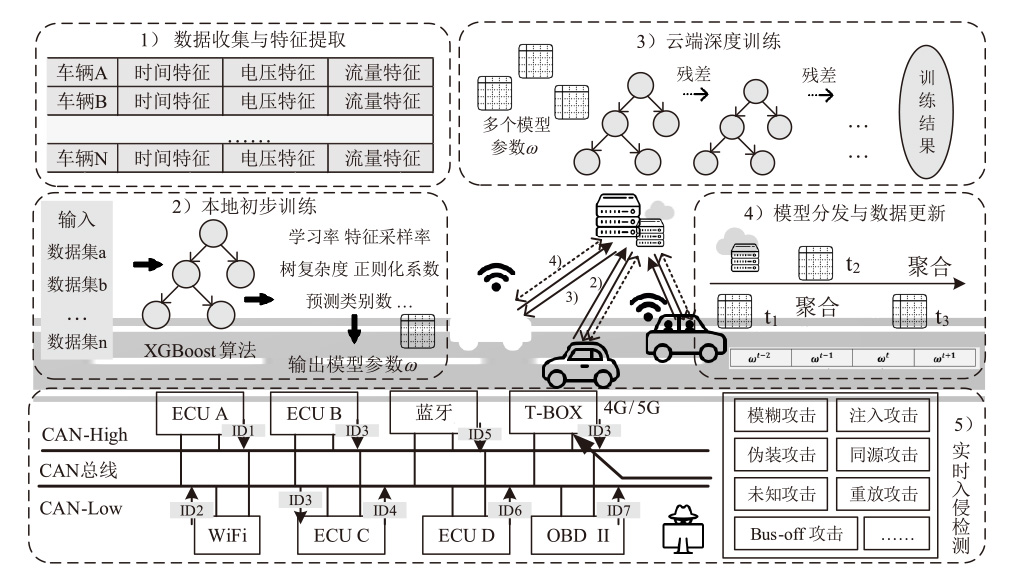
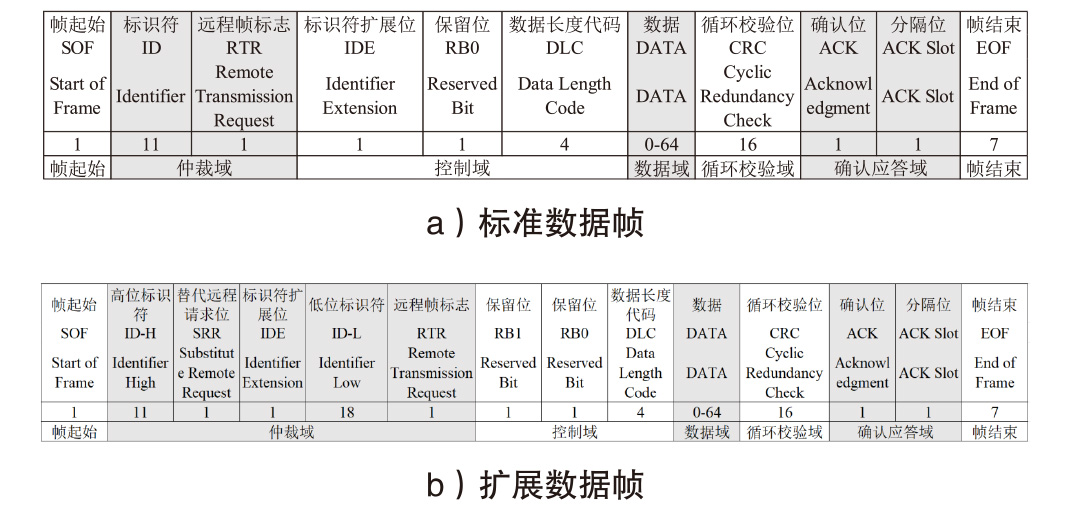
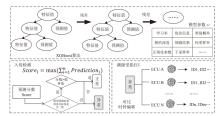
Intrusion Detection System for the Controller Area Network Bus of Intelligent Vehicles Based on Federated Learning
XUN Yijie1,2, CUI Jiarong1,2, MAO Bomin1,2( ), QIN Junman1,2
), QIN Junman1,2
- 1. School of Cybersecurity, Northwestern Polytechnical University, Xi’an 710072, China
2. Research & Development Institute of Northwestern Polytechnical University in Shenzhen, Shenzhen 518057, China
-
Received:2025-02-25Online:2025-06-10Published:2025-07-11
CLC Number:
Cite this article
XUN Yijie, CUI Jiarong, MAO Bomin, QIN Junman. Intrusion Detection System for the Controller Area Network Bus of Intelligent Vehicles Based on Federated Learning[J]. Netinfo Security, 2025, 25(6): 872-888.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.06.003
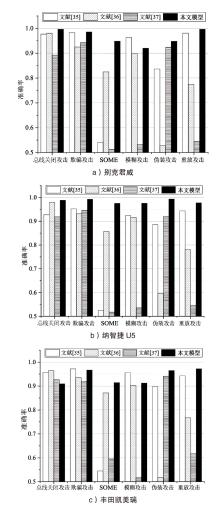
| 车辆 | 指标 | 攻击类型 | |||||
|---|---|---|---|---|---|---|---|
| 总线 关闭 | 欺骗 | SOME | 模糊(Fuzzy) | 伪装(Masquerade) | 重放(Replay) | ||
| 别克 君威 | 准确率 | 0.9966 | 0.9856 | 0.9482 | 0.9199 | 0.9479 | 0.9966 |
| 精确率 | 1 | 0.9756 | 0.9090 | 0.8651 | 0.9090 | 1 | |
| 召回率 | 0.9932 | 0.9960 | 0.9960 | 0.9949 | 0.9955 | 0.9960 | |
| FPR | 0 | 0.0249 | 0.0997 | 0.1551 | 0.0997 | 0 | |
| FNR | 0.0068 | 0.0040 | 0.0040 | 0.0051 | 0.0045 | 0.0040 | |
| 纳智捷U5 | 准确率 | 0.9882 | 0.9923 | 0.9748 | 0.9752 | 0.9931 | 0.9773 |
| 精确率 | 0.9839 | 0.9903 | 0.9584 | 0.9541 | 0.9887 | 0.9593 | |
| 召回率 | 0.9927 | 0.9943 | 0.9927 | 0.9984 | 0.9916 | 0.9968 | |
| FPR | 0.0162 | 0.0097 | 0.0431 | 0.0479 | 0.0114 | 0.0422 | |
| FNR | 0.0073 | 0.0057 | 0.0073 | 0.0016 | 0.0024 | 0.0032 | |
| 丰田 凯美瑞 | 准确率 | 0.9091 | 0.9666 | 0.9140 | 0.9123 | 0.9649 | 0.9718 |
| 精确率 | 0.8449 | 0.9320 | 0.8541 | 0.8517 | 0.9350 | 0.9496 | |
| 召回率 | 1 | 0.9979 | 0.9986 | 0.9993 | 0.9993 | 0.9972 | |
| FPR | 0.0918 | 0.0646 | 0.1706 | 0.0695 | 0.0695 | 0.0530 | |
| FNR | 0 | 0.0021 | 0.0014 | 0.0007 | 0 | 0.0028 | |
| [1] | Editorial Department of China Journal of Highway and Transport. Review on China’s Automotive Engineering Research Progress: 2023[J]. China Journal of Highway and Transport, 2023, 36(11): 1-192. |
|
《中国公路学报》编辑部. 中国汽车工程学术研究综述·2023[J]. 中国公路学报, 2023, 36(11): 1-192.
doi: 10.19721/j.cnki.1001-7372.2023.11.001 |
|
| [2] | MILLER C, VALASEK C. Remote Exploitation of an Unaltered Passenger Vehicle[J]. Black Hat USA, 2015, (S91): 1-91. |
| [3] | BARAN G. Vulnerabilities in Skoda & Volkswagen Cars Let Hackers Remotely Track Users[EB/OL]. (2024-12-12)[2025-02-23]. https://cybersecuritynews.com/vulnerabilities-skoda-volkswagen-cars. |
| [4] | YAN Minrui, LI Jiahao. Security Research on Mercedes-Benz: From Hardware to Car Control[J]. Black Hat USA, 2020, 2020: 1-81. |
| [5] | GB/T 38628-2020 Information Security Technology Cybersecurity Guide for Automotive Electronics Systems[S]. Beijing: Standards Press of China, 2020. |
| GB/T 38628-2020 信息安全技术汽车电子系统网络安全指南[S]. 北京: 中国标准出版社, 2020. | |
| [6] | GB/T 45181-2024 Security-Related Misbehavior Detection Mechanism for Connected Vehicles[S]. Beijing: Standards Press of China, 2024. |
| GB/T 45181-2024 车联网网络安全异常行为检测机制[S]. 北京: 中国标准出版社, 2024. | |
| [7] | JOHANSSON K H, TÖRNGREN M, NIELSEN L. Vehicle Applications of Controller Area Network[M]. Boston: Birkhäuser Boston, 2005. |
| [8] | DU Xinying, HE Mingshu, WANG Xiaojuan. A Feature Fusion-Based Controller Area Network Intrusion Detection Method[J]. Journal of Beijing University of Posts and Telecommunications, 2025, 48(2): 1-7. |
| 杜欣颖, 何明枢, 王小娟. 基于特征融合的控制器局域网入侵检测方法[J]. 北京邮电大学学报, 2025, 48(2): 1-7. | |
| [9] | CAI Zhiqiang, WANG Aohui, ZHANG Wenkai. 0-Days & Mitigations: Roadways to Exploit and Secure Connected BMW Cars[J]. Black Hat USA, 2019, 2019(39): 6-37. |
| [10] | KIM J H, SEO S H, HAI N T, et al. Gateway Framework for In-Vehicle Networks Based on CAN, FlexRay, and Ethernet[J]. IEEE transactions on vehicular technology, 2014, 64(10): 4472-4486. |
| [11] | WANG Wenwei, GUO Kaidi, CAO Wanke, et al. Review of Electrical and Electronic Architectures for Autonomous Vehicles: Topologies, Networking and Simulators[J]. Automotive Innovation, 2024, 7(1): 82-101. |
| [12] | LENARD T, BOLBOACA R. A Statefull Firewall and Intrusion Detection System Enforced with Secure Logging for Controller Area Network[C]// ACM. Proceedings of the 2021 European Interdisciplinary Cybersecurity Conference. New York: ACM, 2021: 39-45. |
| [13] | LUO Feng, HOU Shuo. Security Mechanisms Design of Automotive Gateway Firewall[R]. Detroit: SAE International, No. 2019-01-0481, 2019. |
| [14] | RATHORE M S, POONGODI M, SAURABH P, et al. A Novel Trust-Based Security and Privacy Model for Internet of Vehicles Using Encryption and Steganography[J]. Computers and Electrical Engineering, 2022, 102: 1-18. |
| [15] | AKIB A, ANIKA A, MOUKAHAL L, et al. Security Assessment of In-Vehicle Communication Protocols[J]. Vehicular Communications, 2023, 44: 1-20. |
| [16] | CHO K T, SHIN K G. Fingerprinting Electronic Control Units for Vehicle Intrusion Detection[C]// USENIX. 25th USENIX Security Symposium (USENIX Security 16). Berkeley: USENIX, 2016: 911-927. |
| [17] | YOUNG C, OLUFOWOBI H, BLOOM G, et al. Automotive Intrusion Detection Based on Constant can Message Frequencies across Vehicle Driving Modes[C]// ACM. Proceedings of the ACM Workshop on Automotive Cybersecurity. New York: ACM, 2019: 9-14. |
| [18] | TAYLOR A, JAPKOWICZ N, LEBLANC S. Frequency-Based anomaly Detection for the Automotive CAN Bus[C]// IEEE. 2015 World Congress on Industrial Control Systems Security (WCICSS). New York: IEEE, 2015: 45-49. |
| [19] | CHOI W, JOO K, JO H J, et al. VoltageIDS: Low-Level Communication Characteristics for Automotive Intrusion Detection System[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(8): 2114-2129. |
| [20] | KNEIB M, HUTH C. Scission: Signal Characteristic-Based Sender Identification and Intrusion Detection in Automotive Networks[C]// ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 787-800. |
| [21] | WU Wufei, HUANG Yizhi, KURACHI R, et al. Sliding Window Optimized Information Entropy Analysis Method for Intrusion Detection on In-Vehicle Networks[J]. IEEE Access, 2018, 6: 45233-45245. |
| [22] | LI Yang, MOUBAYED A, HAMIEH I, et al. Tree-Based Intelligent Intrusion Detection System in Internet of Vehicles[C]// IEEE. 2019 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2019: 1-6. |
| [23] | SONG H M, WOO J, KIM H K. In-Vehicle Network Intrusion Detection Using Deep Convolutional Neural Network[J]. Vehicular Communications, 2020, 21: 1-13. |
| [24] | DAVIS R I, BURNS A, BRIL R J, et al. Controller Area Network (CAN) Schedulability Analysis: Refuted, Revisited and Revised[J]. Real-Time Systems, 2007, 35: 239-272. |
| [25] | KUANG Boyu, LI Yuze, GU Fangming, et al. Review of Internet of Vehicle Security Research: Threats, Countermeasures, and Future Prospects[J]. Journal of Computer Research and Development, 2023, 60(10): 2304-2321. |
| 况博裕, 李雨泽, 顾芳铭, 等. 车联网安全研究综述:威胁、对策与未来展望[J]. 计算机研究与发展, 2023, 60(10): 2304-2321. | |
| [26] | ZHOU Chuanxin, SUN Yi, WANG Degang, et al. Survey of Federated Learning Research[J]. Chinese Journal of Network and Information Security, 2021, 7(5): 77-92. |
| 周传鑫, 孙奕, 汪德刚, 等. 联邦学习研究综述[J]. 网络与信息安全学报, 2021, 7(5): 77-92. | |
| [27] | IEHIRA K, INOUE H, ISHIDA K. Spoofing Attack Using Bus-Off Attacks against a Specific ECU of the CAN Bus[C]// IEEE. 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC). New York: IEEE, 2018: 1-4. |
| [28] | YANG Yun, DUAN Zongtao, TEHRANIPOOR M. Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal[J]. Smart Cities, 2020, 3(1): 17-30. |
| [29] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[C]// PMLR. Proceedings of the 20th International Conference on Artificial Intelligence and Statistics. New York: PMLR, 2017: 1273-1282. |
| [30] | LI Tian, SAHU A K, ZAHEER M, et al. Federated Optimization in Heterogeneous Networks[J]. Proceedings of Machine Learning and Systems, 2020, 2: 429-450. |
| [31] | XIE Cong, KOYEJO S, GUPTA I. Asynchronous Federated Optimization[EB/OL]. (2019-04-10)[2025-02-23]. https://arxiv.org/abs/1903.03934. |
| [32] | MIRZAEE P H, SHOJAFAR M, CRUICKSHANK H, et al. CHFL: A Collaborative Hierarchical Federated Intrusion Detection System for Vehicular Networks[C]// IEEE. 2022 IEEE Symposium on Computers and Communications (ISCC). New York: IEEE, 2022: 1-7. |
| [33] | DRISS M, ALMOMANI I, HUMA Z E, et al. A Federated Learning Framework for Cyberattack Detection in Vehicular Sensor Networks[J]. Complex & Intelligent Systems, 2022, 8(5): 4221-4235. |
| [34] | MUZUN A, JAVED A, RANA O. A Robust Multi-Stage Intrusion Detection System for In-Vehicle Network Security Using Hierarchical Federated Learning[J]. Vehicular Communications, 2024, 49: 1-15. |
| [35] | LEE S, CHOI W, JO H J, et al. ErrIDS: An Enhanced Cumulative Timing Error-Based Automotive Intrusion Detection System[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(11): 12406-12421. |
| [36] | HOSSAIN M D, INOUE H, OCHIAI H, et al. LSTM-Based Intrusion Detection System for In-Vehicle Can Bus Communications[J]. IEEE Access, 2020, 8: 185489-185502. |
| [37] | SCHELL O, KNEIB M. VALID: Voltage-Based Lightweight Intrusion Detection for the Controller Area Network[C]// IEEE. 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). New York: IEEE, 2021: 225-232. |
| [1] | DENG Dongshang, WANG Weiye, ZHANG Weidong, WU Xuangou. Layered Personalized Federated Learning Guided by Model Feature Orientation [J]. Netinfo Security, 2025, 25(6): 889-897. |
| [2] | ZHU Shuaishuai, LIU Keqian. A Masking-Based Selective Federated Distillation Scheme [J]. Netinfo Security, 2025, 25(6): 920-932. |
| [3] | LIU Chenfei, WAN Liang. CAN Bus Intrusion Detection Method Based on Spatio-Temporal Graph Neural Networks [J]. Netinfo Security, 2025, 25(3): 478-493. |
| [4] | LI Jiadong, ZENG Haitao, PENG Li, WANG Xiaoding. An Anonymous Routing Federated Learning Framework for Data Privacy Protection [J]. Netinfo Security, 2025, 25(3): 494-503. |
| [5] | XU Ruzhi, TONG Yumeng, DAI Lipeng. Research on Federated Learning Adaptive Differential Privacy Method Based on Heterogeneous Data [J]. Netinfo Security, 2025, 25(1): 63-77. |
| [6] | GUO Qian, ZHAO Jin, GUO Yi. Hierarchical Clustering Federated Learning Framework for Personalized Privacy-Preserving [J]. Netinfo Security, 2024, 24(8): 1196-1209. |
| [7] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [8] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [9] | LIN Yihang, ZHOU Pengyuan, WU Zhiqian, LIAO Yong. Federated Learning Backdoor Defense Method Based on Trigger Inversion [J]. Netinfo Security, 2024, 24(2): 262-271. |
| [10] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [11] | HE Zeping, XU Jian, DAI Hua, YANG Geng. A Review of Federated Learning Application Technologies [J]. Netinfo Security, 2024, 24(12): 1831-1844. |
| [12] | LAN Haoliang, WANG Qun, XU Jie, XUE Yishi, ZHANG Bo. Review of Research on Blockchain-Based Federated Learning [J]. Netinfo Security, 2024, 24(11): 1643-1654. |
| [13] | SA Qirui, YOU Weijing, ZHANG Yifei, QIU Weiyang, MA Cunqing. A Survey of Ownership Protection Schemes for Federated Learning Models [J]. Netinfo Security, 2024, 24(10): 1553-1561. |
| [14] | CHEN Jing, ZHANG Jian. A Data-Free Personalized Federated Learning Algorithm Based on Knowledge Distillation [J]. Netinfo Security, 2024, 24(10): 1562-1569. |
| [15] | WU Lizhao, WANG Xiaoding, XU Tian, QUE Youxiong, LIN Hui. Defense Strategies against Poisoning Attacks in Semi-Asynchronous Federated Learning [J]. Netinfo Security, 2024, 24(10): 1578-1585. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||