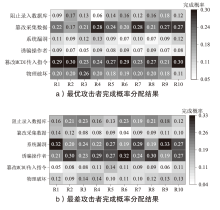
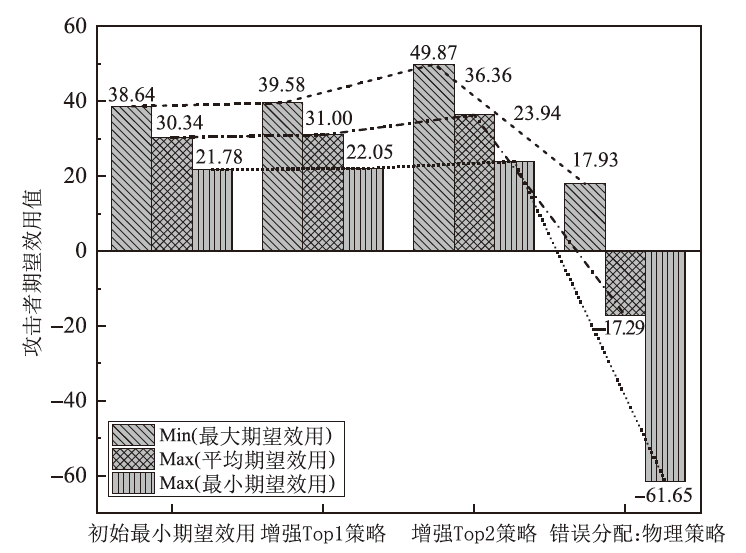
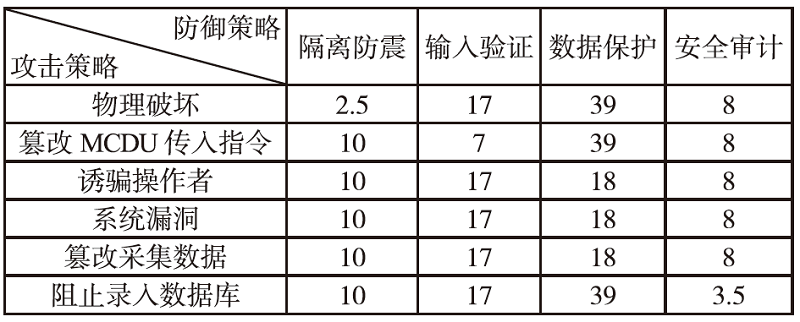
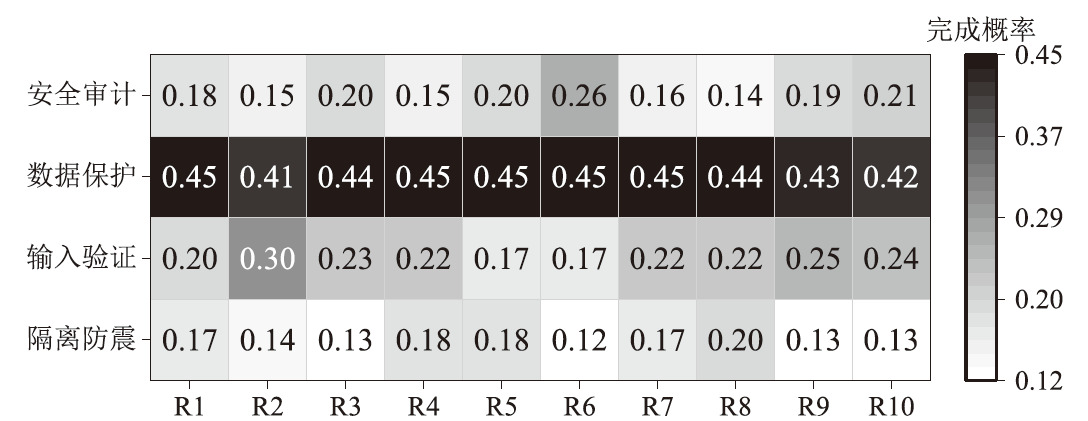
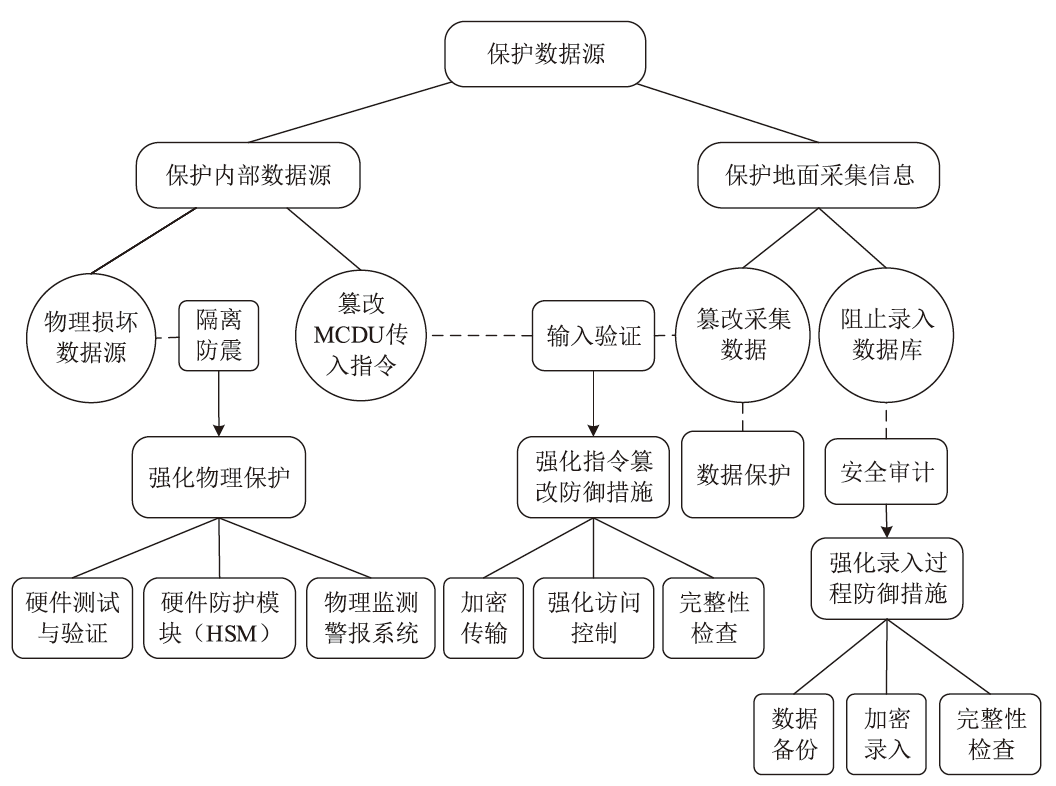
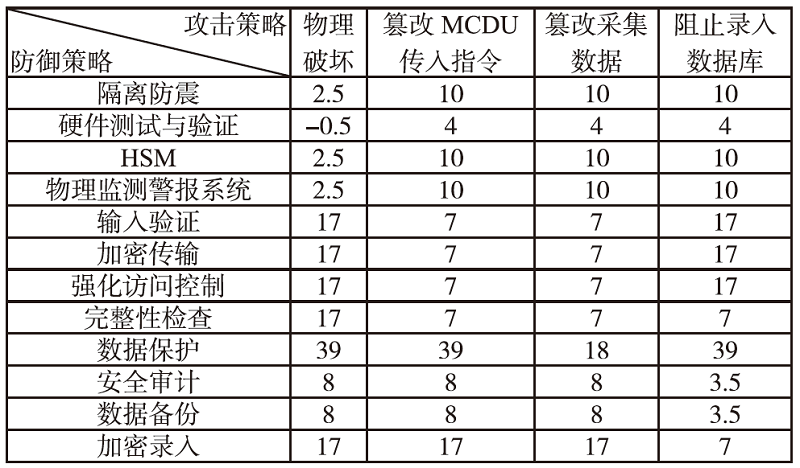
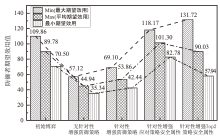
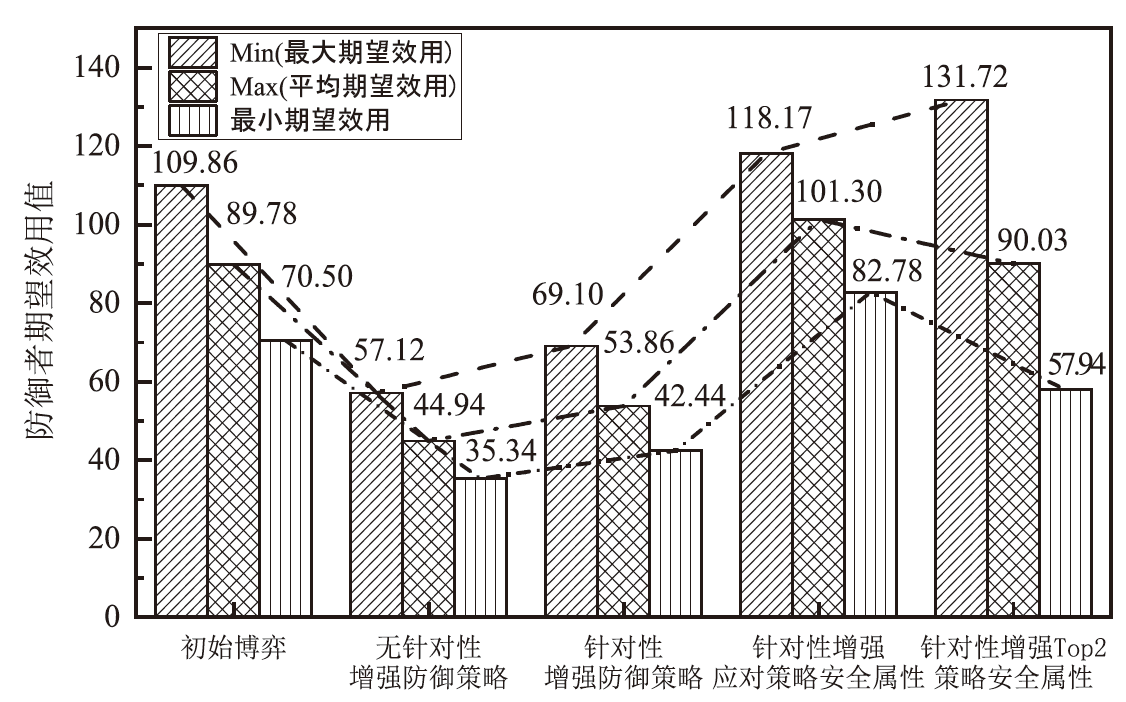
Netinfo Security ›› 2024, Vol. 24 ›› Issue (4): 614-625.doi: 10.3969/j.issn.1671-1122.2024.04.011
Previous Articles Next Articles
A Non-Cooperative Game Model for Optimizing EFIS Data Source Defense Deployment
GU Zhaojun1, ZHANG Yinuo1,2, YANG Xueying1,2, SUI He3( )
)
- 1. Information Security Evaluation Center, Civil Aviation University of China, Tianjin 300300, China
2. College of Computer Science and Technology, Civil Aviation University of China, Tianjin 300300, China
3. College of Aeronautical Engineering, Civil Aviation University of China, Tianjin 300300, China
-
Received:2024-01-29Online:2024-04-10Published:2024-05-16
CLC Number:
Cite this article
GU Zhaojun, ZHANG Yinuo, YANG Xueying, SUI He. A Non-Cooperative Game Model for Optimizing EFIS Data Source Defense Deployment[J]. Netinfo Security, 2024, 24(4): 614-625.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.04.011
| [1] | BARON C, LOUIS V. Towards a Continuous Certification of Safety-Critical Avionics Software[EB/OL]. (2021-01-03)[2023-12-22]. https://www.sciencedirect.com/science/article/pii/S0166361520306163. |
| [2] | VILLEGAS J, FORTES S, ESCAÑO V, et al. Verification and Validation Framework for AFDX Avionics Networks[J]. IEEE Access, 2022, 10: 66743-66756. |
| [3] | SUTHAPUTCHAKUN C, SUN Zhili, KAVADIAS C, et al. Performance Analysis of AFDX Switch for Space Onboard Data Networks[J]. IEEE Transactions on Aerospace and Electronic Systems, 2016, 52(4): 1714-1727. |
| [4] | MATTI E, JOHNS O, KHAN S, et al. Aviation Scenarios for 5G and Beyond[C]// IEEE. In 2020 AIAA/IEEE 39th Digital Avionics Systems Conference(DASC). New York: IEEE, 2020: 1-10. |
| [5] |
ZHAO Changxiao, WANG Kenian, ZHANG Wei, et al. Integrated Analysis Method of Functional Safety and Cyber Security of Avionics System for Civil Aircraft[J]. China Safety Science Journal, 2022, 32(9): 49-56.
doi: 10.16265/j.cnki.issn1003-3033.2022.09.2126 |
| 赵长啸, 汪克念, 张伟, 等. 民机航电系统功能安全-信息安全一体化分析方法[J]. 中国安全科学学报, 2022, 32(32):49-56. | |
| [6] | ZIMMER L, YVARS P A, LAFAYE M. Models of Requirements for Avionics Architecture Synthesis: Safety, Capacity and Security[EB/OL]. (2020-12-01)[2023-12-22]. https://hal.science/hal-03957544/. |
| [7] | ATHAVALE J, MARIANI R, PAULITSCH M. Flight Safety Certification Implications for Complex Multi-Core Processor Based Avionics Systems[C]// IEEE. In 2019 IEEE International Reliability Physics Symposium(IRPS). New York: IEEE, 2019: 1-6. |
| [8] | SMITH M, STROHMEIER M, HARMAN J, et al. Safety vs. Security: Attacking Avionic Systems with Humans in the Loop[EB/OL]. (2019-05-20)[2023-12-22]. https://www.researchgate.net/publication/333233094_Safety_vs_Security_Attacking_Avionic_Systems_with_Humans_in_the_Loop. |
| [9] | BEEK M H T, LEGAY A, LAFUENTE AL, et al. Quantitative Security Risk Modeling and Analysis with RisQFLan[EB/OL]. (2021-10-01)[2023-12-22]. https://doi.org/10.1016/j.cose.2021.102381. |
| [10] | JHAWAR R, MAUW S, ZAKIUDDIN I. Automating Cyber Defence Responses Using Attack-Defence Trees and Game Theory[EB/OL]. (2016-01-01)[2023-12-22]. https://research.utwente.nl/en/publications/automating-cyber-defence-responses-using-attack-defence-trees-and. |
| [11] | HUANG Bo, QIN Yuhai, LIU Yang, et al. Research of Vulnerability Assessment and Risk ProbabilityBase on General Attack Tree[J]. Netinfo Security, 2022, 22(10): 39-44. |
| 黄波, 秦玉海, 刘旸, 等. 基于通用攻击树的脆弱性评估与风险概率研究[J]. 信息网络安全, 2022, 22(10):39-44. | |
| [12] | CHEHIDA S, BAOUYA A, BOZGA M, et al. Exploration of Impactful Countermeasures on IoT Attacks[C]// IEEE. 9th Mediterranean Conference on Embedded Computing(MECO). New York: IEEE, 2020: 1-4. |
| [13] | ARIAS J, BUDDE C E, PENCZEK W, et al. Hackers vs. Security: Attack-Defence Trees as Asynchronous Multi-Agent Systems[C]// Springer. In International Conference on Formal Engineering Methods. Heidelberg: Springer, 2020: 3-19 |
| [14] | RIOS E, REGO A, ITURBE E, et al. Continuous Quantitative Risk Management in Smart Grids Using Attack Defense Trees[EB/OL]. (2020-08-07)[2023-12-22]. https://www.mdpi.com/1424-8220/20/16/4404. |
| [15] | PETRUCCI L, KNAPIK M, PENCZEK W, et al. Squeezing State Spaces of (Attack-Defence) Trees[C]// IEEE. 24th International Conference on Engineering of Complex Computer Systems(ICECCS). New York: IEEE, 2019: 71-80. |
| [16] | LIU Guiyun, PENG Baihao, ZHONG Xiaojing. Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack-Defense Game Model[EB/OL]. (2021-01-15)[2023-12-22]. https://www.mdpi.com/1424-8220/21/2/594. |
| [17] | LIU Guiyun, PENG Baihao, ZHONG Xiaojing, et al. Attack-Defense Game between Malicious Programs and Energy-Harvesting Wireless Sensor Networks Based on Epidemic Modeling[J]. Complexity, 2020(1): 1-9. |
| [18] | ZHOU Haiping, SHEN Shigen, LIU Jianhua. Malware Propagation Model in Wireless Sensor Networks under Attack-Defense Confrontation[J]. Computer Communications, 2020, 162: 51-58. |
| [19] | WU Yingfu, KANG Bingyi, WU Hao. Strategies of Attack-Defense Game for Wireless Sensor Networks Considering the Effect of Confidence Level in Fuzzy Environment[EB/OL]. (2021-04-12)[2023-12-22]. https://www.sciencedirect.com/science/article/pii/S0952197621000853. |
| [20] | ZHANG Zhimei, HUANG Shaowei, CHEN Ying, et al. Cyber-Physical Coordinated Risk Mitigation in Smart Grids Based on Attack-Defense Game[J]. IEEE Transactions on Power Systems, 2021, 37(1): 530-542. |
| [21] | PENG Rui, WU Di, SUN Mengyao, et al. An Attack-Defense Game on Interdependent Networks[J]. Journal of the Operational Research Society, 2021, 72(10): 2331-2341. |
| [1] | ZHANG Hao, XIE Dazhi, HU Yunsheng, YE Junwei. A Review of Network Anomaly Detection Based on Semi-Supervised Learning [J]. Netinfo Security, 2024, 24(4): 491-508. |
| [2] | WANG Jian, CHEN Lin, WANG Kailun, LIU Jiqiang. Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network [J]. Netinfo Security, 2024, 24(4): 509-519. |
| [3] | TU Xiaohan, ZHANG Chuanhao, LIU Mengran. Design and Implementation of Malicious Traffic Detection Model [J]. Netinfo Security, 2024, 24(4): 520-533. |
| [4] | LIU Sinuo, RUAN Shuhua, CHEN Xingshu, ZHENG Tao. An eBPF-Based Threat Observability System for Cloud-Oriented Environment [J]. Netinfo Security, 2024, 24(4): 534-544. |
| [5] | ZHANG Guanghua, LIU Yichun, WANG He, HU Boning. Defense Scheme for Removing Deep Neural Network Backdoors Based on JSMA Adversarial Attacks [J]. Netinfo Security, 2024, 24(4): 545-554. |
| [6] | ZHANG Xuefeng, CHEN Tingting, MIAO Meixia, CHENG Yexia. Multi-Receiver Chaotic Key Generation Scheme Based on SM9 [J]. Netinfo Security, 2024, 24(4): 555-563. |
| [7] | ZHANG Yanshuo, YUAN Yuqi, LI Liqiu, YANG Yatao, QIN Xiaohong. Periodically Deniable Ring Signature Scheme Based on SM2 Digital Signature Algorithm [J]. Netinfo Security, 2024, 24(4): 564-573. |
| [8] | SUN Junfeng, LI Chenghai, SONG Yafei. ACCQPSO: An Improved Quantum Particle Swarm Optimization Algorithm and Its Applications [J]. Netinfo Security, 2024, 24(4): 574-586. |
| [9] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [10] | YIN Chunyong, JIA Xukang. Research on 3D-Location Privacy Publishing Algorithm Based on Policy Graph [J]. Netinfo Security, 2024, 24(4): 602-613. |
| [11] | HU Haiyang, LIU Chang, WANG Dong, WEI Xu. Clean Energy Data Traceability Mechanism Based on Blockchain [J]. Netinfo Security, 2024, 24(4): 626-639. |
| [12] | XU Zirong, GUO Yanping, YAN Qiao. Malicious Software Adversarial Defense Model Based on Feature Severity Ranking [J]. Netinfo Security, 2024, 24(4): 640-649. |
| [13] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [14] | ZHANG Qiang, HE Junjiang, LI Wenshan, LI Tao. Anomaly Traffic Detection Based on Deep Metric Learning [J]. Netinfo Security, 2024, 24(3): 462-472. |
| [15] | FU Yanming, LU Shenglin, CHEN Jiayuan, QIN Hua. Dynamic Task Allocation for Crowd Sensing Based on Deep Reinforcement Learning and Privacy Protection [J]. Netinfo Security, 2024, 24(3): 449-461. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||