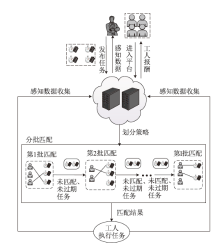
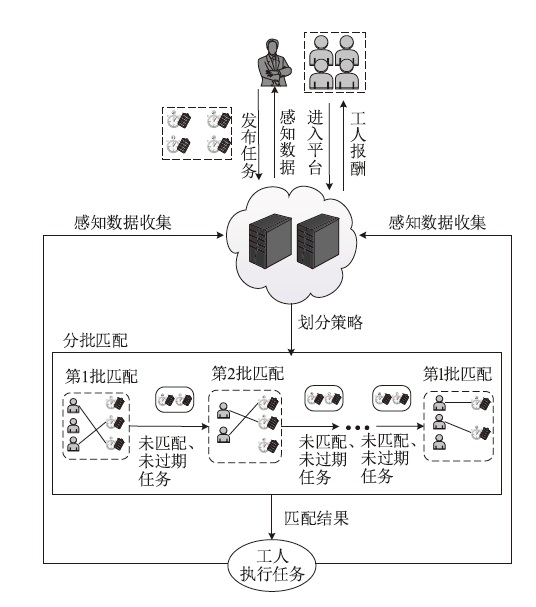
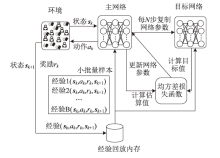
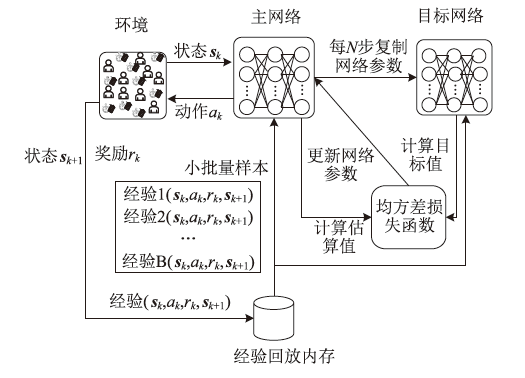
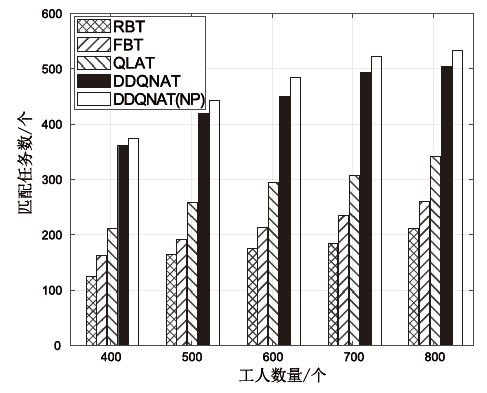
Netinfo Security ›› 2024, Vol. 24 ›› Issue (3): 449-461.doi: 10.3969/j.issn.1671-1122.2024.03.010
Previous Articles Next Articles
Dynamic Task Allocation for Crowd Sensing Based on Deep Reinforcement Learning and Privacy Protection
FU Yanming1,2,3, LU Shenglin1, CHEN Jiayuan1( ), QIN Hua1
), QIN Hua1
- 1. School of Computer, Electronic and Information, Guangxi University, Nanning 530000, China
2. Key Laboratory of Parallel, Distributed and Intelligent Computing(Guangxi), Nanning 530000, China
3. Guangxi Intelligent Digital Services Research Center of Engineering Technology, Nanning 530000, China
-
Received:2024-01-29Online:2024-03-10Published:2024-04-03 -
Contact:CHEN Jiayuan E-mail:ycq_cjy@163.com
CLC Number:
Cite this article
FU Yanming, LU Shenglin, CHEN Jiayuan, QIN Hua. Dynamic Task Allocation for Crowd Sensing Based on Deep Reinforcement Learning and Privacy Protection[J]. Netinfo Security, 2024, 24(3): 449-461.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.03.010
| [1] | GANTI R K, YE Fan, LEI Hui. Mobile Crowdsensing: Current State and Future Challenges[J]. IEEE Communications Magazine, 2011, 49(11): 32-39. |
| [2] | CAPPONI A, FIANDRINO C, KANTARCI B, et al. A Survey on Mobile Crowdsensing Systems: Challenges, Solutions, and Opportunities[J]. IEEE Communications Surveys & Tutorials, 2019, 21(3): 2419-2465. |
| [3] |
ZHENG Zhenzhe, WU Fan, GAO Xiaofeng, et al. A Budget Feasible Incentive Mechanism for Weighted Coverage Maximization in Mobile Crowdsensing[J]. IEEE Transactions on Mobile Computing, 2016, 16(9): 2392-2407.
doi: 10.1109/TMC.2016.2632721 URL |
| [4] |
WANG Xiong, ZHANG Jinbei, TIAN Xiaohua, et al. Crowdsensing-Based Consensus Incident Report for Road Traffic Acquisition[J]. IEEE Transactions on Intelligent Transportation Systems, 2017, 19(8): 2536-2547.
doi: 10.1109/TITS.2017.2750169 URL |
| [5] |
BALLESTEROS J, CARBUNAR B, RAHMAN M, et al. Towards Safe Cities: A Mobile and Social Networking Approach[J]. IEEE Transactions on Parallel and Distributed Systems, 2013, 25(9): 2451-2462.
doi: 10.1109/TPDS.2013.190 URL |
| [6] |
ALEMDAR H, ERSOY C. Wireless Sensor Networks for Healthcare: A Survey[J]. Computer Networks, 2010, 54(15): 2688-2710.
doi: 10.1016/j.comnet.2010.05.003 URL |
| [7] | JIANG Weijin, CHEN Junpeng, LIU Xiaoliang, et al. Participant Recruitment Method Aiming at Service Quality in Mobile Crowd Sensing[J]. Wireless Communications and Mobile Computing, 2021(3): 1-14. |
| [8] |
WANG Jiangtao, WANG Yasha, ZHANG Daqing, et al. Multi-Task Allocation in Mobile Crowd Sensing with Individual Task Quality Assurance[J]. IEEE Transactions on Mobile Computing, 2018, 17(9): 2101-2113.
doi: 10.1109/TMC.7755 URL |
| [9] | WU Shengnan, WANG Yingjie, TONG Xiangrong. Multi-Objective Task Assignment for Maximizing Social Welfare in Spatio-Temporal Crowdsourcing[J]. China Communications, 2021, 18(11): 11-25. |
| [10] |
LI Xin, ZHANG Xinglin. Multi-Task Allocation under Time Constraints in Mobile Crowdsensing[J]. IEEE Transactions on Mobile Computing, 2019, 20(4): 1494-1510.
doi: 10.1109/TMC.7755 URL |
| [11] |
TAO Xi, SONG Wei. Profit-Oriented Task Allocation for Mobile Crowdsensing with Worker Dynamics: Cooperative Offline Solution and Predictive Online Solution[J]. IEEE Transactions on Mobile Computing, 2020, 20(8): 2637-2653.
doi: 10.1109/TMC.2020.2983688 URL |
| [12] |
SONG Tianshu, XU Ke, LI Jiangneng, et al. Multi-Skill Aware Task Assignment in Real-Time Spatial Crowdsourcing[J]. GeoInformatica, 2020, 24: 153-173.
doi: 10.1007/s10707-019-00351-4 |
| [13] |
XIAO Mingjun, WU Jie, HUANG Liusheng, et al. Online Task Assignment for Crowdsensing in Predictable Mobile Social Networks[J]. IEEE Transactions on Mobile Computing, 2016, 16(8): 2306-2320.
doi: 10.1109/TMC.2016.2616473 URL |
| [14] | MIAO Xin, KANG Yanrong, MA Qiang, et al. Quality-Aware Online Task Assignment in Mobile Crowdsourcing[J]. ACM Transactions on Sensor Networks, 2020, 16(3): 1-21. |
| [15] | ZHAO Pengcheng, LI Xiang, GAO Shang, et al. Cooperative Task Assignment in Spatial Crowdsourcing via Multi-Agent Deep Reinforcement Learning[EB/OL]. (2022-05-23)[2023-12-12]. https://doi.org/10.1016/j.sysarc.2022.102551. |
| [16] |
PAN Qingxian, PAN Tingwei, DONG Hongbin, et al. An Online Task Assignment Based on Quality Constraint for Spatio-Temporal Crowdsourcing[J]. IEEE Access, 2019, 7: 170292-170303.
doi: 10.1109/ACCESS.2019.2942155 |
| [17] |
ZHAO Bingxu, DONG Hongbin, WANG Yingjie, et al. A Task Allocation Algorithm Based on Reinforcement Learning in Spatio-Temporal Crowdsourcing[J]. Applied Intelligence, 2023, 53(11): 13452-13469.
doi: 10.1007/s10489-022-04151-6 |
| [18] | TO H, SHAHABI C, KAZEMI L. A Server-Assigned Spatial Crowdsourcing Framework[J]. ACM Transactions on Spatial Algorithms and Systems, 2015, 1(1): 1-28. |
| [19] | WANG Mingze, WANG Yingjie, SAI A, et al. Task Assignment for Hybrid Scenarios in Spatial Crowdsourcing: A Q-Learning-Based Approach[EB/OL]. (2022-11-04)[2023-12-12]. https://doi.org/10.1016/j.asoc.2022.109749. |
| [20] |
SUN Lijun, YU Xiaojie, GUO Jiachen, et al. Deep Reinforcement Learning for Task Assignment in Spatial Crowdsourcing and Sensing[J]. IEEE Sensors Journal, 2021, 21(22): 25323-25330.
doi: 10.1109/JSEN.2021.3057376 URL |
| [21] | YANG Hai, QIN Xiaoran, KE Jintao, et al. Optimizing Matching Time Interval and Matching Radius in on-Demand Ride-Sourcing Markets[J]. Transportatio Research Part B: Met-Hodological, 2020, 131: 84-105. |
| [22] | WANG Yansheng, TONG Yongxin, LONG Cheng, et al. Adaptive Dynamic Bipartite Graph Matching: A Reinforcement Learning Approach[C]// IEEE. 2019 IEEE 35th International Conference on Data Engineering(ICDE). New York: IEEE, 2019: 1478-1489. |
| [23] |
SUN Yong, TAN Wenan. A Trust-Aware Task Allocation Method Using Deep Q-Learning for Uncertain Mobile Crowdsourcing[J]. Human-Centric Computing and Information Sciences, 2019, 9: 1-27.
doi: 10.1186/s13673-018-0162-5 |
| [24] |
LIU Chi, DAI Zipeng, ZHAO Yinuo, et al. Distributed and Energy-Efficient Mobile Crowdsensing with Charging Stations by Deep Reinforcement Learning[J]. IEEE Transactions on Mobile Computing, 2019, 20(1): 130-146.
doi: 10.1109/TMC.7755 URL |
| [25] | YAO Changhua, XU Hao, FU Shu, et al. Fast Multi-Agent Collaborative Exploration Algorithm Based on Boundary Point Filtering[J]. Netinfo Security, 2023, 23(11): 58-68. |
| 姚昌华, 许浩, 付澍, 等. 基于边界点过滤的多智能体快速协同探索算法[J]. 信息网络安全, 2023, 23(11):58-68. | |
| [26] | TAO Xi, SONG Wei. Task Allocation for Mobile Crowdsensing with Deep Reinforcement Learning[C]// IEEE. 2020 IEEE Wireless Communications and Networking Conference(WCNC). New York: IEEE, 2020: 1-7. |
| [27] | DWORK C. Differential Privacy[C]// Springer. International Colloquium on Automata, Languages, and Programming. Heidelberg: Springer, 2006: 1-12. |
| [28] |
TO H, GHINITA G, SHAHABI C. Framework for Protecting Worker Location Privacy in Spatial Crowdsourcing[J]. Proceedings of the VLDB Endowment, 2014, 7(10): 919-930.
doi: 10.14778/2732951.2732966 URL |
| [29] | YAN Yan, ZHANG Xiong, FENG Tao. Proportional Differential Privacy Budget Allocation Method for Partition and Publishing of Statistical Big Data[J]. Netinfo Security, 2022, 22(11): 24-35. |
| 晏燕, 张雄, 冯涛. 大数据统计划分发布的等比差分隐私预算分配方法[J]. 信息网络安全, 2022, 22(11):24-35. | |
| [30] |
WANG Leye, YANG Dingqi, HAN Xiao, et al. Mobile Crowdsourcing Task Allocation with Differential-and-Distortion Geo-Obfuscation[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(2): 967-981.
doi: 10.1109/TDSC.8858 URL |
| [31] | ANDRÉS M E, BORDENABE N E, CHATZIKOKOLAKIS K, et al. Geo-Indistinguishability: Differential Privacy for Location-Based Systems[C]// ACM. The 2013 ACM SIGSAC Conference on Computer & Communications Security. New York: ACM, 2013: 901-914. |
| [32] |
ZHANG Qi, WANG Yingjie, CAI Zhipeng, et al. Multi-Stage Online Task Assignment Driven by Offline Data under Spatio-Temporal Crowdsourcing[J]. Digital Communications and Networks, 2022, 8(4): 516-530.
doi: 10.1016/j.dcan.2021.10.005 URL |
| [33] | SONG Tianshu, TONG Yongxin, WANG Libin, et al. Trichromatic Online Matching in Real-Time Spatial Crowdsourcing[C]// IEEE. 2017 IEEE 33rd International Conference on Data Engineering(ICDE). New York: IEEE, 2017: 1009-1020. |
| [1] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [2] | XU Ke, LI Jiayi, JIANG Xinghao, SUN Tanfeng. A Video Gait Privacy Protection Algorithm Based on Sparse Adversarial Attack on Silhouette [J]. Netinfo Security, 2024, 24(1): 48-59. |
| [3] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [4] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [5] | DU Weidong, LI Min, HAN Yiliang, WANG Xu’an. An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique [J]. Netinfo Security, 2023, 23(4): 51-60. |
| [6] | YIN Shu, CHEN Xingshu, ZHU Yi, ZENG Xuemei. Anonymous Domain Name Algorithm Based on Character Space Construction [J]. Netinfo Security, 2023, 23(4): 80-89. |
| [7] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [8] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [9] | LI Jiahui, QIN Sujuan, GAO Fei, SUN Dongxu. Controllable and Supervised Privacy Protection Scheme for Blockchain Organization Transaction Based on Attribute Encryption [J]. Netinfo Security, 2023, 23(12): 103-112. |
| [10] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [11] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [12] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 22(3): 78-84. |
| [13] | LIANG Guangjun, XIN Jianfang, NI Xueli, MA Zhuo. Research on Smart Speaker Security and Forensics [J]. Netinfo Security, 2022, 22(10): 108-113. |
| [14] | GU Haiyan, JIANG Tong, MA Zhuo, ZHU Jipeng. Research of Improved k-Anonymity Algorithm and Its Application in Privacy Protection [J]. Netinfo Security, 2022, 22(10): 52-58. |
| [15] | XU Shuo, ZHANG Rui, XIA Hui. Privacy-preserving Strategies for Federated Learning Based on Data Attribute Modification [J]. Netinfo Security, 2022, 22(1): 55-63. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||