Netinfo Security ›› 2024, Vol. 24 ›› Issue (3): 462-472.doi: 10.3969/j.issn.1671-1122.2024.03.011
Previous Articles Next Articles
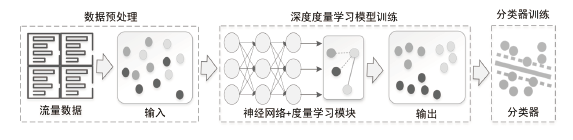
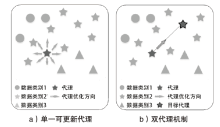
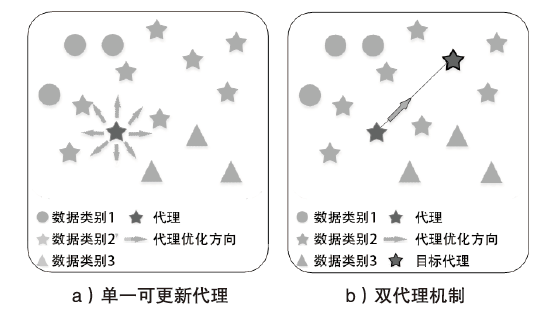
Anomaly Traffic Detection Based on Deep Metric Learning
ZHANG Qiang1, HE Junjiang1( ), LI Wenshan1,2, LI Tao1
), LI Wenshan1,2, LI Tao1
- 1. School of Cyber Science and Engineering, Sichuan University, Chengdu 610065, China
2. School of Cybersecurity, Chengdu University of Information Technology, Chengdu 610225, China
-
Received:2023-07-12Online:2024-03-10Published:2024-04-03 -
Contact:HE Junjiang E-mail:hejunjiang@scu.edu.cn
CLC Number:
Cite this article
ZHANG Qiang, HE Junjiang, LI Wenshan, LI Tao. Anomaly Traffic Detection Based on Deep Metric Learning[J]. Netinfo Security, 2024, 24(3): 462-472.
share this article
| 分类器 | Weighted-Precision | Weighted-Recall | Weighted-F1 | |||
|---|---|---|---|---|---|---|
| 处理前 | 处理后 | 处理前 | 处理后 | 处理前 | 处理后 | |
| KNN | 79.0% | 82.6% | 75.8% | 78.1% | 71.1% | 74.9% |
| SVM | 81.7% | 82.7% | 77.4% | 78.1% | 74.7% | 75.1% |
| DT | 73.2% | 80.0% | 69.6% | 77.7% | 65.4% | 74.4% |
| RF | 72.0% | 82.4% | 57.1% | 78.0% | 52.0% | 74.7% |
| XGBoost | 78.0% | 82.7% | 71.5% | 78.1% | 70.2% | 75.0% |
| 文献[ | 79.2% | 81.7% | 74.1% | 78.2% | 71.1% | 75.1% |
| 文献[ | 81.2% | 82.7% | 75.7% | 78.1% | 72.0% | 75.2% |
| 分类器 | Weighted-Precision | Weighted-Recall | Weighted-F1 | |||
|---|---|---|---|---|---|---|
| 处理前 | 处理后 | 处理前 | 处理后 | 处理前 | 处理后 | |
| KNN | 97.0% | 98.0% | 97.1% | 98.1% | 97.0% | 98.1% |
| SVM | 66.6% | 96.4% | 62.9% | 96.2% | 60.4% | 96.0% |
| DT | 95.4% | 96.2% | 94.7% | 95.8% | 94.1% | 95.7% |
| RF | 97.0% | 97.3% | 97.4% | 97.6% | 97.2% | 97.4% |
| XGBoost | 97.8% | 97.9% | 97.9% | 98.0% | 97.7% | 97.8% |
| 文献[ | 97.3% | 99.1% | 97.4% | 99.0% | 97.2% | 98.8% |
| 文献[ | 91.7% | 96.9% | 90.3% | 96.7% | 88.7% | 96.4% |
| [1] |
YANG Zheng, LIU Xiaodong, LI Tong, et al. A Systematic Literature Review of Methods and Datasets for Anomaly-Based Network Intrusion Detection[J]. Computers & Security, 2022, 116: 102675-102684.
doi: 10.1016/j.cose.2022.102675 URL |
| [2] | ROSHAN K, ZAFAR A. Deep Learning Approaches for Anomaly and Intrusion Detection in Computer Network: A Review[J]. Cyber Security and Cyber Security and Digital Forensics, 2022, 73: 551-563. |
| [3] | AZAB A, KHASAWNEH M, ALRABAEE S, et al. Network Traffic Classification: Techniques, Datasets, and Challenges[EB/OL]. (2022-09-18) [2023-06-20]. https://doi.org/10.1016/j.dcan.2022.09.009. |
| [4] | SEN S, SPATSCHECK O, WANG Dongmei. Accurate, Scalable in-Network Identification of P2P Traffic Using Application Signatures[C]// ACM. Proceedings of the 13th International Conference on World Wide Web. New York: ACM, 2004: 512-521. |
| [5] | MOORE A W, PAPAGIANNAKI K. Toward the Accurate Identification of Network Applications[C]// Springer. 6th International Workshop on Passive and Active Network Measurement. Heidelberg: Springer, 2005: 41-54. |
| [6] |
PARVAT T J, CHANDRA P. A Novel Approach to Deep Packet Inspection for Intrusion Detection[J]. Procedia Computer Science, 2015, 45: 506-513.
doi: 10.1016/j.procs.2015.03.091 URL |
| [7] |
ZHANG Chunying, JIA Donghao, WANG Liya, et al. Comparative Research on Network Intrusion Detection Methods Based on Machine Learning[J]. Computers & Security, 2022, 121: 102861-102873.
doi: 10.1016/j.cose.2022.102861 URL |
| [8] | HEARST M A, DUMAIS S T, OSUNA E, et al. Support Vector Machines[J]. IEEE Intelligent Systems and Their Applications, 1998, 13(4): 18-28. |
| [9] |
SONG Yanyan, YING Lu. Decision Tree Methods: Applications for Classification and Prediction[J]. Shanghai Archives of Psychiatry, 2015, 27(2): 130-135.
doi: 10.11919/j.issn.1002-0829.215044 pmid: 26120265 |
| [10] | LAAKSONEN J, OJA E. Classification with Learning K-Nearest Neighbors[C]// IEEE. Proceedings of International Conference on Neural Networks (ICNN’96). New York: IEEE, 1996, 3: 1480-1483. |
| [11] |
BREIMAN L. Random Forests[J]. Machine Learning, 2001, 45: 5-32.
doi: 10.1023/A:1010933404324 URL |
| [12] | CHEN T, GUESTRIN C. XGBoost: A Scalable Tree Boosting System[C]// ACM. Proceedings of the 22nd ACM Sigkdd International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2016: 785-794. |
| [13] | WANG Wei, ZHU Ming, WANG Jinlin, et al. End-to-End Encrypted Traffic Classification with One-Dimensional Convolution Neural Networks[C]// IEEE. 2017 IEEE International Conference on Intelligence and Security Informatics (ISI). New York: IEEE, 2017: 43-48. |
| [14] |
YAO Haipeng, LIU Chong, ZHANG Peiying, et al. Identification of Encrypted Traffic through Attention Mechanism Based Long Short Term Memory[J]. IEEE Transactions on Big Data, 2019, 8(1): 241-252.
doi: 10.1109/TBDATA.2019.2940675 URL |
| [15] | ZHANG Wenming. Abnormal Network Traffic Detection Based on Deep Metric Learning[D]. Xi’an: Xidian University, 2021. |
| 张文铭. 基于深度度量学习的异常网络流量检测[D]. 西安: 西安电子科技大学, 2021. | |
| [16] | XUE Jingliang. Research on Network Traffic Identificaiton Technology Based on Deep Metric Learning[D]. Zhengzhou: PLA Strategic Support Force Information Engineering University, 2021. |
| 薛靖靓. 基于深度度量学习的网络流量识别技术研究[D]. 郑州: 战略支援部队信息工程大学, 2021. | |
| [17] | CHOPRA S, HADSELL R, LECUN Y. Learning a Similarity Metric Discriminatively, with Application to Face Verification[C]// IEEE. 2005 IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR’05). New York: IEEE, 2005: 539-546. |
| [18] | SCHROFF F, KALENICHENKO D, PHILBIN J. Facenet: A Unified Embedding for Face Recognition and Clustering[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2015: 815-823. |
| [19] | SONG O H, XIANG Yu, JEGELKA S, et al. Deep Metric LEARNING via Lifted Structured Feature Embedding[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 4004-4012. |
| [20] | CHEN Weihua, CHEN Xiaotang, ZHANG Jianguo, et al. Beyond Triplet Loss: A Deep Quadruplet Network for Person Re-Identification[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2017: 403-412. |
| [21] | SOHN K. Improved Deep Metric Learning with Multi-Class N-Pair Loss Objective[J]. Advances in Neural Information Processing Systems, 2016, 8: 29-37. |
| [22] | MOVSHOVITZ-ATTIAS Y, TOSHEV A, LEUNG T K, et al. No Fuss Distance Metric Learning Using Proxies[C]// IEEE. Proceedings of the IEEE International Conference on Computer Vision. New York: IEEE, 2017: 360-368. |
| [23] | KIM S, KIM D, CHO M, et al. Proxy Anchor Loss for Deep Metric Learning[C]// IEEE. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2020: 3238-3247. |
| [24] | WANG Yifan, LIU Pingping, LANG Yijun, et al. Learnable Dynamic Margin in Deep Metric Learning[J]. Pattern Recognition, 2022, 132: 128-140. |
| [25] | LOKOČ J, KOHOUT J, ČECH P, et al. K-NN Classification of Malware in HTTPS Traffic Using the Metric Space Approach[C]// Springer. Intelligence and Security Informatics:11th Pacific Asia Workshop. Heidelberg: Springer, 2016: 131-145. |
| [26] |
DI M M, DI S C. Improving SIEM Capabilities through an Enhanced Probe for Encrypted Skype Traffic Detection[J]. Journal of Information Security and Applications, 2018, 38: 85-95.
doi: 10.1016/j.jisa.2017.12.001 URL |
| [27] |
LOTFOLLAHI M, JAFARI S M, SHIRALI H Z R, et al. Deep Packet: A Novel Approach for Encrypted Traffic Classification Using Deep Learning[J]. Soft Computing, 2020, 24(3): 1999-2012.
doi: 10.1007/s00500-019-04030-2 |
| [28] |
ZENG Yi, GU Huaxi, WEI Wenting, et al. Deep-Full-Range: A Deep Learning Based Network Encrypted Traffic Classification and Intrusion Detection Framework[J]. IEEE Access, 2019, 7: 45182-45190.
doi: 10.1109/Access.6287639 URL |
| [29] | LIU Chang, HE Longtao, XIONG Gang, et al. FS-Net: A Flow Sequence Network for Encrypted Traffic Classification[C]// IEEE. IEEE INFOCOM 2019-IEEE Conference On Computer Communications. New York: IEEE, 2019: 1171-1179. |
| [30] | WANG Xin, CHENShuhui, SUJinshu. App-Net: A Hybrid Neural Network for Encrypted Mobile Traffic Classification[C]// IEEE. IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2020: 424-429. |
| [31] |
TANG Chaofei, LUKTARHAN N, ZHAO Yuxin. SAAE-DNN: Deep Learning Method on Intrusion Detection[J]. Symmetry, 2020, 12(10): 1695-1699.
doi: 10.3390/sym12101695 URL |
| [32] | LIN Kunda, XU Xiaolong, XIAO Fu. MFFusion: A Multi-Level Features Fusion Model for Malicious Traffic Detection Based on Deep Learning[J]. Computer Networks, 2022, 22: 108658-108665. |
| [33] |
LAN Jinghong, LIU Xudong, LI Bo, et al. MEMBER: A Multi-Task Learning Model with Hybrid Deep Features for Network Intrusion Detection[J]. Computers & Security, 2022, 123: 102919-102925.
doi: 10.1016/j.cose.2022.102919 URL |
| [34] | TAVALLAEE M, BAGHERI E, LU Wei, et al. A Detailed Analysis of the KDD CUP 99 Data Set[C]// IEEE. 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications. New York: IEEE, 2009: 1-6. |
| [35] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[J]. International Conference on Information Systems Security and Privacy, 2018, 1: 108-116. |
| [36] | KESKES N, FAKHFAKH S, KANOUN O, et al. High Performance Oversampling Technique Considering Intra-Class and Inter-Class Distances[EB/OL]. (2022-11-02)[2023-06-20]. https://doi.org/10.1002/cpe.6753. |
| [37] |
LOPEZ-MARTIN M, CARRO B, SANCHEZ-ESGUEVILLAS A, et al. Network Traffic Classifier with Convolutional and Recurrent Neural Networks for Internet of Things[J]. IEEE Access, 2017, 5: 18042-18050.
doi: 10.1109/Access.6287639 URL |
| [38] | SINHA J, MANOLLAS M. Efficient Deep CNN-BiLSTM Model for Network Intrusion Detection[C]// ACM. Proceedings of the 2020 3rd International Conference on Artificial Intelligence and Pattern Recognition. New York: ACM, 2020: 223-231. |
| [1] | YANG Zhipeng, LIU Daidong, YUAN Junyi, WEI Songjie. Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism [J]. Netinfo Security, 2024, 24(3): 398-410. |
| [2] | ZHANG Xinyou, SUN Feng, FENG Li, XING Huanlai. Multi-View Representations for Fake News Detection [J]. Netinfo Security, 2024, 24(3): 438-448. |
| [3] | YU Shangrong, XIAO Jingbo, YIN Qilin, LU Wei. A Social Heterophily Focused Framework for Social Bot Detection [J]. Netinfo Security, 2024, 24(2): 319-327. |
| [4] | QIN Zhongyuan, MA Nan, YU Yacong, CHEN Liquan. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders [J]. Netinfo Security, 2023, 23(9): 1-11. |
| [5] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [6] | XU Chungen, XUE Shaokang, XU Lei, ZHANG Pan. Efficient Neural Network Inference Protocol Based on Secure Two-Party Computation [J]. Netinfo Security, 2023, 23(7): 22-30. |
| [7] | YUAN Wenxin, CHEN Xingshu, ZHU Yi, ZENG Xuemei. HTTP Payload Covert Channel Detection Method Based on Deep Learning [J]. Netinfo Security, 2023, 23(7): 53-63. |
| [8] | LI Chenwei, ZHANG Hengwei, GAO Wei, YANG Bo. Transferable Image Adversarial Attack Method with AdaN Adaptive Gradient Optimizer [J]. Netinfo Security, 2023, 23(7): 64-73. |
| [9] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [10] | JIANG Zenghui, ZENG Weijun, CHEN Pu, WU Shitao. Review of Adversarial Samples for Modulation Recognition [J]. Netinfo Security, 2023, 23(6): 74-90. |
| [11] | ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning [J]. Netinfo Security, 2023, 23(5): 1-10. |
| [12] | CHEN Zitong, JIA Peng, LIU Jiayong. Identification Method of Malicious Software Hidden Function Based on Siamese Architecture [J]. Netinfo Security, 2023, 23(5): 62-75. |
| [13] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [14] | QIN Yifang, ZHANG Jian, LIANG Chen. Research on Feature Extraction Technology of Electronic Medical Record Data Based on Neural Networks [J]. Netinfo Security, 2023, 23(10): 70-76. |
| [15] | ZHANG Yujian, LIU Daifu, TONG Fei. Reentrancy Vulnerability Detection in Smart Contracts Based on Local Graph Matching [J]. Netinfo Security, 2022, 22(8): 1-7. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||