Netinfo Security ›› 2024, Vol. 24 ›› Issue (11): 1731-1738.doi: 10.3969/j.issn.1671-1122.2024.11.012
Previous Articles Next Articles
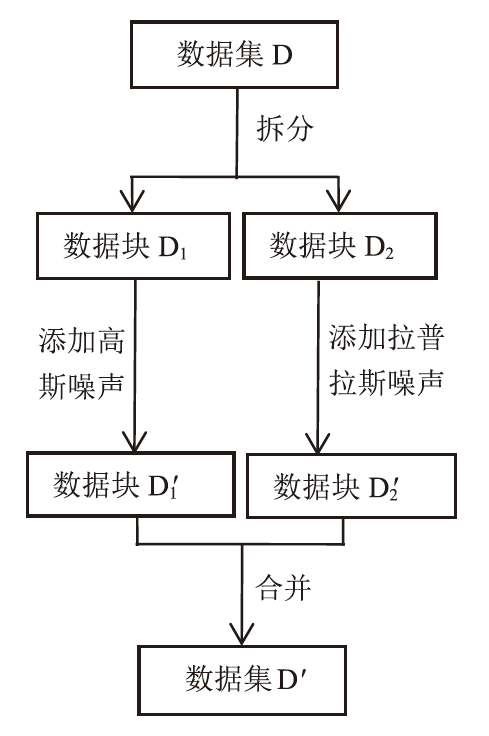
Research on Data Noise Addition Method Based on Availability
GU Haiyan1( ), LIU Qi2, MA Zhuo1, ZHU Tao1, QIAN Hanwei1
), LIU Qi2, MA Zhuo1, ZHU Tao1, QIAN Hanwei1
- 1. Department of Computer Information and Cyber Security, Jiangsu Police Institute, Nanjing 210031, China
2. Nanjing Public Security Bureau Xuanwu Sub-Bureau, Nanjing 210058, China
-
Received:2024-07-05Online:2024-11-10Published:2024-11-21
CLC Number:
Cite this article
GU Haiyan, LIU Qi, MA Zhuo, ZHU Tao, QIAN Hanwei. Research on Data Noise Addition Method Based on Availability[J]. Netinfo Security, 2024, 24(11): 1731-1738.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.11.012
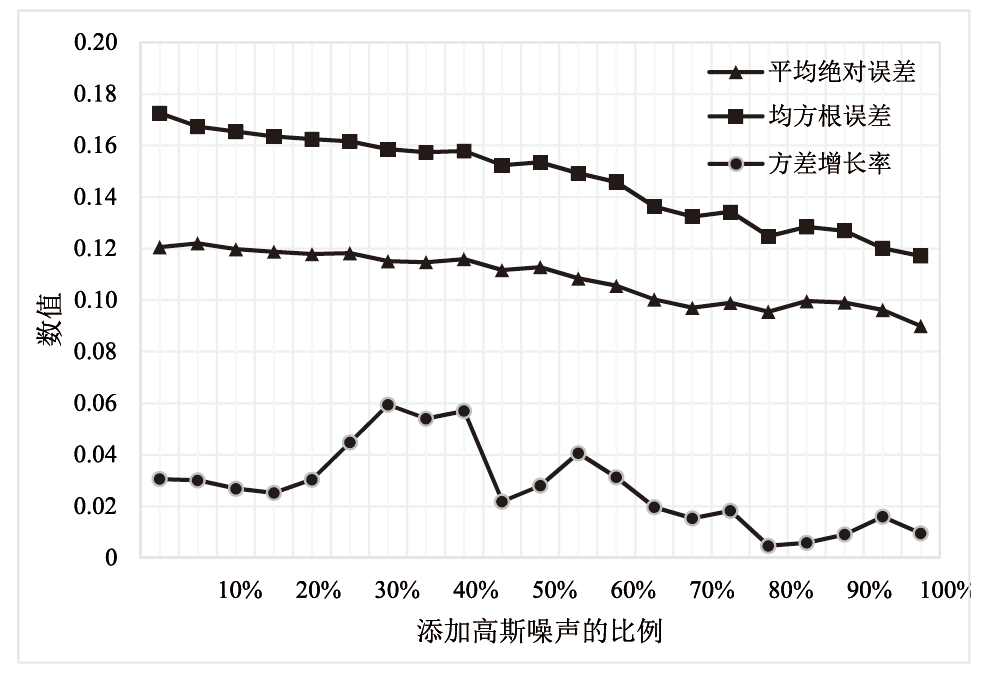
| 添加高斯噪声的比例η | 平均绝对误差 | 均方根误差 | 方差增长率 |
|---|---|---|---|
| 0 | 0.121 | 0.172 | 3.06% |
| 5% | 0.122 | 0.167 | 3.01% |
| 10% | 0.120 | 0.165 | 2.69% |
| 15% | 0.119 | 0.164 | 2.52% |
| 20% | 0.118 | 0.162 | 3.04% |
| 25% | 0.118 | 0.162 | 4.48% |
| 30% | 0.115 | 0.159 | 5.94% |
| 35% | 0.115 | 0.157 | 5.41% |
| 40% | 0.116 | 0.158 | 5.70% |
| 45% | 0.112 | 0.152 | 2.19% |
| 50% | 0.113 | 0.153 | 2.80% |
| 55% | 0.108 | 0.149 | 4.07% |
| 60% | 0.106 | 0.146 | 3.13% |
| 65% | 0.100 | 0.136 | 1.97% |
| 70% | 0.097 | 0.132 | 1.54% |
| 75% | 0.099 | 0.134 | 1.83% |
| 80% | 0.096 | 0.125 | 0.47% |
| 85% | 0.100 | 0.128 | 0.59% |
| 90% | 0.100 | 0.127 | 0.91% |
| 95% | 0.096 | 0.120 | 1.60% |
| 100% | 0.090 | 0.117 | 0.96% |
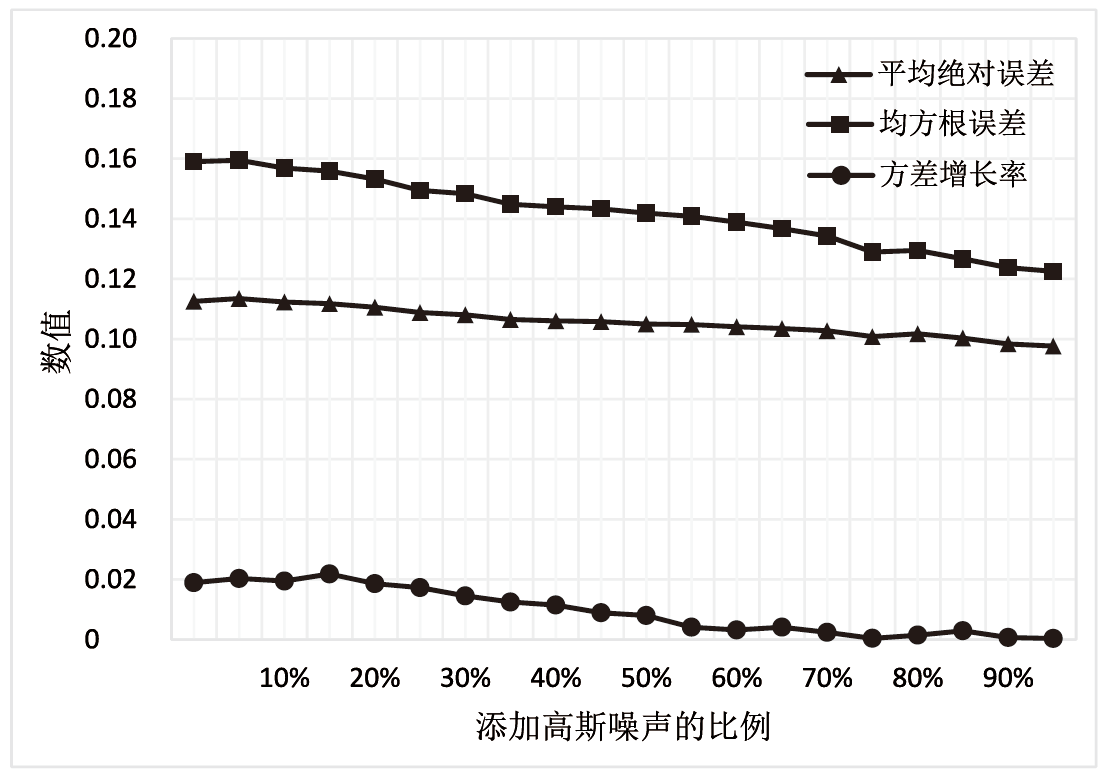
| 高斯噪声比例 | 100个数据 | 500个数据 | ||||
|---|---|---|---|---|---|---|
| 平均绝对误差 | 均方根 误差 | 方差 增长率 | 平均绝对误差 | 均方根 误差 | 方差 增长率 | |
| 0 | 0.121 | 0.172 | 3.06% | 0.112 | 0.112 | 1.41% |
| 20% | 0.118 | 0.162 | 3.04% | 0.110 | 0.109 | 0.28% |
| 40% | 0.116 | 0.158 | 5.70% | 0.107 | 0.104 | 0.29% |
| 60% | 0.106 | 0.146 | 3.13% | 0.102 | 0.093 | 0.52% |
| 80% | 0.096 | 0.125 | 0.47% | 0.101 | 0.090 | 0.80% |
| 100% | 0.090 | 0.117 | 0.96% | 0.097 | 0.084 | 0.51% |
| 高斯噪声比例 | 1000个数据 | 2000个数据 | ||||
| 平均绝对误差 | 均方根 误差 | 方差 增长率 | 平均绝对误差 | 均方根误差 | 方差 增长率 | |
| 0 | 0.113 | 0.160 | 1.86% | 0.123 | 0.176 | 3.48% |
| 20% | 0.112 | 0.156 | 2.18% | 0.118 | 0.167 | 2.52% |
| 40% | 0.106 | 0.143 | 0.89% | 0.112 | 0.157 | 2.27% |
| 60% | 0.105 | 0.141 | 0.41% | 0.107 | 0.145 | 2.25% |
| 80% | 0.101 | 0.129 | 0.04% | 0.101 | 0.133 | 1.48% |
| 100% | 0.098 | 0.123 | 0.03% | 0.097 | 0.126 | 1.35% |
| [1] | SHAO Guosong. Psycho-Graphic Profiling: What Can Be Learned from Cambridge Analytica[J]. Media Observer, 2021, 455(11): 45-49. |
| 邵国松. 心理绘图与用户画像:剑桥分析的兴亡启示录[J]. 传媒观察, 2021, 455(11): 45-49. | |
| [2] | QIAN Wenjun, SHEN Qingni, WU Pengfei, et al. Research Progress on Privacy-Preserving Techniques in Big Data Computing Environment[J]. Chinese Journal of Computers, 2022, 45(4): 669-701. |
| 钱文君, 沈晴霓, 吴鹏飞, 等. 大数据计算环境下的隐私保护技术研究进展[J]. 计算机学报, 2022, 45(4): 669-701. | |
| [3] |
LI Hongtao, REN Xiaoyu, WANG Jie, et al. Continuous Location Privacy Protection Mechanism Based on Differential Privacy[J]. Journal on Communications, 2021, 42(8): 164-175.
doi: 10.11959/j.issn.1000-436x.2021123 |
|
李洪涛, 任晓宇, 王洁, 等. 基于差分隐私的连续位置隐私保护机制[J]. 通信学报, 2021, 42(8): 164-175.
doi: 10.11959/j.issn.1000-436x.2021123 |
|
| [4] | DWORK C. Differential Privacy[C]// Springer. International Colloquium on Automata, Languages, and Programming. Heidelberg: Springer, 2006: 1-12. |
| [5] |
ZHANG Xuejun, YANG Haoying, LI Zhen, et al. Differentially Private Location Privacy-Preserving Scheme with Semantic Location[J]. Computer Science, 2021, 48(8): 300-308.
doi: 10.11896/jsjkx.200900198 |
|
张学军, 杨昊英, 李桢, 等. 融合语义位置的差分私有位置隐私保护方法[J]. 计算机科学, 2021, 48(8): 300-308.
doi: 10.11896/jsjkx.200900198 |
|
| [6] |
HUANG Haiping, WANG Kai, TANG Xiong, et al. Differential Privacy Protection Scheme Based on Edge Betweenness Model[J]. Journal on Communications, 2019, 40(5): 88-97.
doi: 10.11959/j.issn.1000-436x.2019095 |
|
黄海平, 王凯, 汤雄, 等. 基于边介数模型的差分隐私保护方案[J]. 通信学报, 2019, 40(5): 88-97.
doi: 10.11959/j.issn.1000-436x.2019095 |
|
| [7] |
WANG Li’e, LI Xiaocong, LIU Hongyi. News Recommendation Method with Knowledge Graph and Differential Privacy[J]. Journal of Computer Applications, 2022, 42(5): 1339-1346.
doi: 10.11772/j.issn.1001-9081.2021030527 |
|
王利娥, 李小聪, 刘红翼. 融合知识图谱和差分隐私的新闻推荐方法[J]. 计算机应用, 2022, 42(5): 1339-1346.
doi: 10.11772/j.issn.1001-9081.2021030527 |
|
| [8] | LIU Kai, HAN Yiliang, GUO Kaiyang, et al. Differential Privacy Trajectory Protection Mechanism Based on DBSCAN Clustering Algorithm[J]. Science Technology and Engineering, 2022, 22(25): 11091-11096. |
| 刘凯, 韩益亮, 郭凯阳, 等. 基于密度的噪声应用空间聚类算法的差分隐私轨迹保护机制[J]. 科学技术与工程, 2022, 22(25): 11091-11096. | |
| [9] | WEI Kang, LI Jun, DING Ming, et al. Federated Learning with Differential Privacy: Algorithms and Performance Analysis[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 3454-3469. |
| [10] | SONG Cheng, CHENG Daochen, NI Shuiping. k Anonymous Trajectory Privacy Protection Scheme of Personalized Differential Privacy[J]. Journal of Beijing University of Posts and Telecommunications, 2023, 46(3): 109-114. |
| 宋成, 程道晨, 倪水平. 个性化差分隐私的k匿名轨迹隐私保护方案[J]. 北京邮电大学学报, 2023, 46(3): 109-114. | |
| [11] |
LI Kejia, HU Xuexian, CHEN Yue, et al. Differential Privacy Linear Regression Algorithm Based on Principal Component Analysis and Functional Mechanism[J]. Computer Science, 2023, 50(8): 342-351.
doi: 10.11896/jsjkx.220800255 |
|
李可佳, 胡学先, 陈越, 等. 基于主成分分析和函数机制的差分隐私线性回归算法[J]. 计算机科学, 2023, 50(8): 342-351.
doi: 10.11896/jsjkx.220800255 |
|
| [12] | XU Yahong, YANG Geng, BAI Yunlu, et al. Differential Privacy Data Publish Algorithm for Principal Component Analysis[J]. Cyberspace Security, 2018, 9(10): 74-82. |
| 徐亚红, 杨庚, 白云璐, 等. 面向主成分分析的差分隐私数据发布算法[J]. 网络空间安全, 2018, 9(10): 74-82. | |
| [13] | YANG Jun, ZHOU Juling. Restore of Mathematical Detail: The Process of Gauss Deriving the Probability Density Function of Normal Distribution[J]. Journal of Statistics and Information, 2019, 34(6): 17-21. |
| 杨军, 周菊玲. 还原数学细节:高斯推导正态分布概率密度函数的过程[J]. 统计与信息论坛, 2019, 34(6): 17-21. | |
| [14] | ROY I, SETTY S T V, KILZER A, et al. Airavat:Security and Privacy for MapReduce[C]// USENIX. Proceedings of the 7th USENIX Symposium on Networked Systems Design and Implementation. Berkeley: USENIX, 2010: 297-312. |
| [15] | BAO Ting, XU Lei, ZHU Liehuang, et al. Optimized Setting of Privacy Budget in a Recommendation System with Local Differential Privacy[J]. Scientia Sinica (Informationis), 2022, 52(8): 1481-1499. |
| 暴婷, 徐蕾, 祝烈煌, 等. 满足本地化差分隐私的推荐系统中隐私预算的优化设置[J]. 中国科学:信息科学, 2022, 52(8): 1481-1499. | |
| [16] | YAN Yan, ZHANG Xiong, FENG Tao. Proportional Differential Privacy Budget Allocation Method for Partition and Publishing of Statistical Big Data[J]. Netinfo Security, 2022, 22(11): 24-35. |
| 晏燕, 张雄, 冯涛. 大数据统计划分发布的等比差分隐私预算分配方法[J]. 信息网络安全, 2022, 22(11): 24-35. | |
| [17] |
ZHANG Xing, ZHANG Xing, WANG Qingyang. DP-IMKP: Data Publishing Protection Method for Personalized Differential Privacy[J]. Computer Engineering and Applications, 2023, 59(10): 288-298.
doi: 10.3778/j.issn.1002-8331.2201-0457 |
|
张星, 张兴, 王晴阳. DP-IMKP:满足个性化差分隐私的数据发布保护方法[J]. 计算机工程与应用, 2023, 59(10): 288-298.
doi: 10.3778/j.issn.1002-8331.2201-0457 |
|
| [18] | WANG Chao. Personalized Recommendation Techniques and Applications Based on User Decision-Making Behaviors[D]. Hefei: University of Science and Technology of China, 2022. |
| 王超. 基于用户决策行为的个性化推荐方法及应用研究[D]. 合肥: 中国科学技术大学, 2022. | |
| [19] | DWORK C, ROTH A. The Algorithmic Foundations of Differential Privacy[J]. Foundations and Trends in Theoretical Computer Science, 2013(9): 211-407. |
| [1] | WEN Jinming, LIU Qing, CHEN Jie, WU Yongdong. Research Current Status and Challenges of Fully Homomorphic Cryptography Based on Learning with Errors [J]. Netinfo Security, 2024, 24(9): 1328-1351. |
| [2] | LIN Zhanhang, XIANG Guangli, LI Zhenpeng, XU Ziyi. Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(9): 1375-1385. |
| [3] | FU Yanming, LU Shenglin, CHEN Jiayuan, QIN Hua. Dynamic Task Allocation for Crowd Sensing Based on Deep Reinforcement Learning and Privacy Protection [J]. Netinfo Security, 2024, 24(3): 449-461. |
| [4] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [5] | XU Ke, LI Jiayi, JIANG Xinghao, SUN Tanfeng. A Video Gait Privacy Protection Algorithm Based on Sparse Adversarial Attack on Silhouette [J]. Netinfo Security, 2024, 24(1): 48-59. |
| [6] | XU Ruzhi, DAI Lipeng, XIA Diya, YANG Xin. Research on Centralized Differential Privacy Algorithm for Federated Learning [J]. Netinfo Security, 2024, 24(1): 69-79. |
| [7] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [8] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [9] | DU Weidong, LI Min, HAN Yiliang, WANG Xu’an. An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique [J]. Netinfo Security, 2023, 23(4): 51-60. |
| [10] | YIN Shu, CHEN Xingshu, ZHU Yi, ZENG Xuemei. Anonymous Domain Name Algorithm Based on Character Space Construction [J]. Netinfo Security, 2023, 23(4): 80-89. |
| [11] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [12] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [13] | LI Jiahui, QIN Sujuan, GAO Fei, SUN Dongxu. Controllable and Supervised Privacy Protection Scheme for Blockchain Organization Transaction Based on Attribute Encryption [J]. Netinfo Security, 2023, 23(12): 103-112. |
| [14] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [15] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||