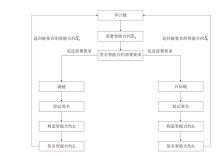
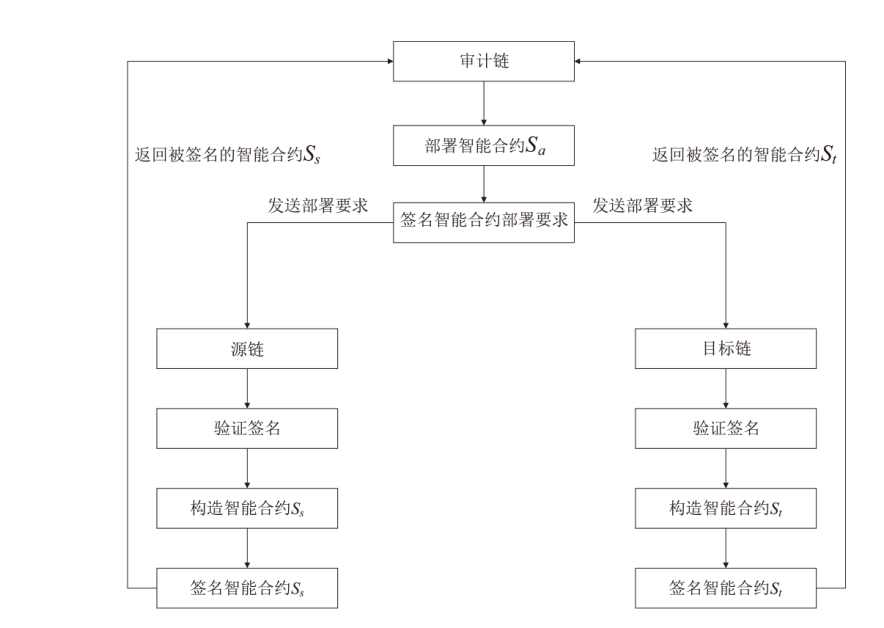
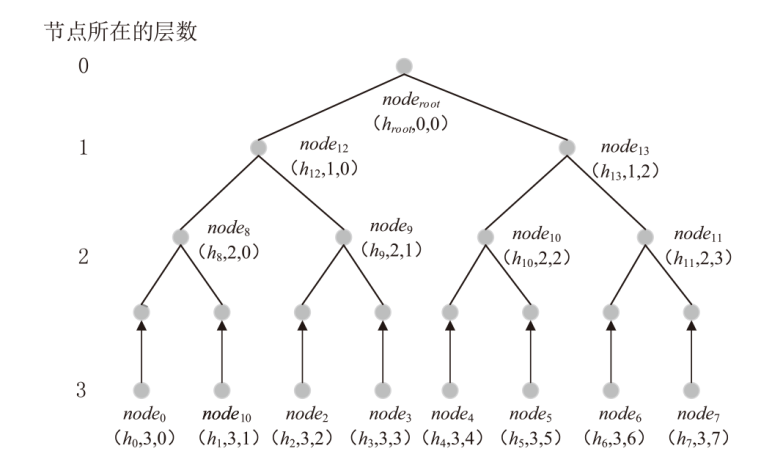
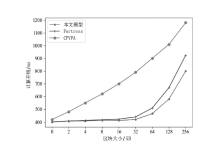
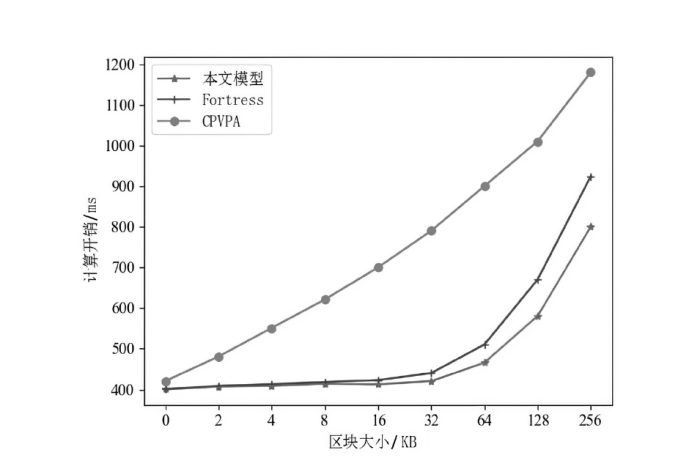
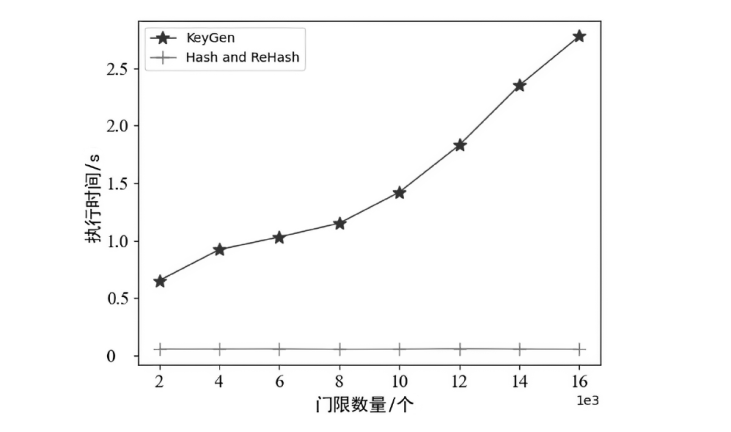
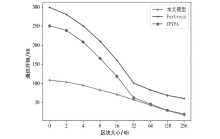
Netinfo Security ›› 2023, Vol. 23 ›› Issue (9): 95-107.doi: 10.3969/j.issn.1671-1122.2023.09.009
Previous Articles Next Articles
Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree
ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu( )
)
- College of Computer Science and Technology, Nanjing University of Aeronautics and Astronautics, Nanjing 211106, China
-
Received:2023-06-27Online:2023-09-10Published:2023-09-18 -
Contact:ZHANG Yushu E-mail:yushu@nuaa.edu.cn
CLC Number:
Cite this article
ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree[J]. Netinfo Security, 2023, 23(9): 95-107.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.09.009
| [1] | CHEN Jing, YAO Shixiong, YUAN Quan, et al. Certchain: Public and Efficient Certificate Audit Based on Blockchain for TLS Connections[C]// IEEE. 37th IEEE Conference on Computer Communications. New York: IEEE, 2018: 2060-2068. |
| [2] |
KUBILAY M Y, KIRAZ M S, MANTAR H A. CertLedger: A New PKI Model with Certificate Transparency Based on Blockchain[J]. Computers & Security, 2019, 85(2): 333-352.
doi: 10.1016/j.cose.2019.05.013 URL |
| [3] | CAI Chengjun, ZHENG Yifeng, DU Yuefeng, et al. Towards Private, Robust, and Verifiable Crowdsensing Systems via Public Blockchains[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(4): 1893-1907. |
| [4] |
AUJLA G S, JINDAL A. A Decoupled Blockchain Approach for Edge-Envisioned IoT-Based Healthcare Monitoring[J]. IEEE Journal on Selected Areas in Communications, 2020, 39(2): 491-499.
doi: 10.1109/JSAC.49 URL |
| [5] | PAN Chen, LIU Zhiqiang, LIU Zhen, et al. Research on Scalability of Blockchain Technology: Problems and Methods[J]. Journal of Computer Research and Development, 2018, 55(10): 2099-2110. |
| 潘晨, 刘志强, 刘振, 等. 区块链可扩展性研究:问题与方法[J]. 计算机研究与发展, 2018, 55(10): 2099-2110. | |
| [6] | BACK A, CORALLO M, DASHJR L, et al. Enabling Blockchain Innovations with Pegged Sidechains[J]. Open Science Review, 2014, 72(3): 201-224. |
| [7] | WOOD G. Polkadot: Vision for a Heterogeneous Multi-Chain Framework[J]. White Paper, 2016, 21: 2327-4662. |
| [8] | ZHANG Shitong, QIN Bo, ZHENG Haibin. Research on the Protocol of Multiple Cross-Chains Based on the Hash Lock[J]. Cyberspace Security, 2018, 9(11): 57-62, 67. |
| 张诗童, 秦波, 郑海彬. 基于哈希锁定的多方跨链协议研究[J]. 网络空间安全, 2018, 9(11): 57-62,67. | |
| [9] | ATZEI N, BARTOLETTI M, CIMOLI T. A Survey of Attacks on Ethereum Smart Contracts (SoK)[C]// Springer. 4th International Conference on Principles of Security and Trust. Berlin: Springer, 2017: 164-186. |
| [10] |
SHEN Jian, SHEN Jun, CHEN Xiaofeng, et al. An Efficient Public Auditing Protocol with Novel Dynamic Structure for Cloud Data[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(10): 2402-2415.
doi: 10.1109/TIFS.2017.2705620 URL |
| [11] | HE Kun, CHEN Jing, YUAN Quan, et al. Dynamic Group-Oriented Provable Data Possession in the Cloud[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(3): 1394-1408. |
| [12] | PATIL J, CHAUDHARI S. Privacy Preserving and Dynamic Audit Service for Secure Cloud Storage[C]// IEEE. 7th International Conference on Smart City and Emerging Technology (ICSCET). New York: IEEE, 2018: 1-6. |
| [13] | ZHANG Yushu, JIANG Jiajia, DONG Xuewen, et al. BeDCV: Blockchain-Enabled Decentralized Consistency Verification for Cross-Chain Calculation[J]. IEEE Transactions on Cloud Computing, 2022, 28(2): 1-12. |
| [14] |
JIANG Jiajia, ZHANG Yushu, ZHU Youwen, et al. DCIV: Decentralized Cross-Chain Data Integrity Verification with Blockchain[J]. Journal of King Saud University-Computer and Information Sciences, 2022, 34(10): 7988-7999.
doi: 10.1016/j.jksuci.2022.07.015 URL |
| [15] |
JIA Meng, CHEN Jing, HE Kun, et al. Redactable Blockchain from Decentralized Chameleon Hash Functions[J]. IEEE Transactions on Information Forensics and Security, 2022, 17(6): 2771-2783.
doi: 10.1109/TIFS.2022.3192716 URL |
| [16] | SYTA E, TAMAS I, VISHER D, et al. Keeping Authorities "Honest or Bust" with Decentralized Witness Cosigning[C]// IEEE. 37th IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2016: 526-545. |
| [17] | LI Dawei, LIU Jianwei, TANG Zongxun, et al. AgentChain: A Decentralized Cross-Chain Exchange System[C]// IEEE. 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications. New York: IEEE, 2019: 491-498. |
| [18] | TSAI W T, BLOWER R, ZHU Yan, et al. A System View of Financial Blockchains[C]// IEEE. 10th IEEE Symposium on Service-Oriented System Engineering. New York: IEEE, 2016: 450-457. |
| [19] | HE Yunhua, ZHANG Cui, WU Bin, et al. Cross-Chain Trusted Service Quality Computing Scheme for Multi-Chain Model-Based 5G Network Slicing SLA[J]. IEEE Internet of Things Journal, 2021, 14(10): 12126-12139. |
| [20] | ATENIESE G, PIETRO D R, MANCINI L V, et al. Scalable and Efficient Provable Data Possession[C]// ACM. 4th International Conference on Security and Privacy in Communication Netowrks. New York: ACM, 2008: 1-10. |
| [21] |
TIAN Hui, CHEN Yuxiang, CHANG C C, et al. Dynamic-Hash-Table Based Public Auditing for Secure Cloud Storage[J]. IEEE Transactions on Services Computing, 2015, 10(5): 701-714.
doi: 10.1109/TSC.2015.2512589 URL |
| [22] | ERWAY C C, KUPCU A, PAPAMANTHOU C, et al. Dynamic Provable Data Possession[J]. ACM Transactions on Information and System Security (TISSEC), 2015, 17(4): 1-29. |
| [23] |
WANG Cong, WANG Qian, REN Kui, et al. Toward Secure and Dependable Storage Services in Cloud Computing[J]. IEEE Transactions on Services Computing, 2012, 5(2): 220-232.
doi: 10.1109/TSC.2011.24 URL |
| [24] | CAMENISCH J, DERLER D, KRENN S, et al. Chameleon-Hashes with Ephemeral Trapdoors[C]// Springer. Public Key Cryptography. Berlin:Springer, 2017: 152-182. |
| [25] | BELLARE M, NEVEN G. Multi-Signatures in the Plain Public-Key Model and a General Forking Lemma[C]// ACM. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 390-399. |
| [26] | LYNN B. The Pairing-Based Cryptography (PBC) Library[EB/OL]. (2010-06-05)[2023-06-10]. http://crypto.stanford.edu/pbc/. |
| [1] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [2] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [3] | SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System [J]. Netinfo Security, 2023, 23(8): 109-120. |
| [4] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [5] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [6] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [7] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [8] | LI Chunxiao, WANG Yaofei, XU Enliang, ZHAO Yu. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings [J]. Netinfo Security, 2023, 23(3): 22-34. |
| [9] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [10] | WANG Jingyu, MA Zhaofeng, XU Danheng, DUAN Pengfei. Blockchain Transaction Data Privacy-Preserving Scheme Supporting National Cryptographic Algorithm [J]. Netinfo Security, 2023, 23(3): 84-95. |
| [11] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [12] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [13] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [14] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| [15] | KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX [J]. Netinfo Security, 2022, 22(7): 73-83. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||