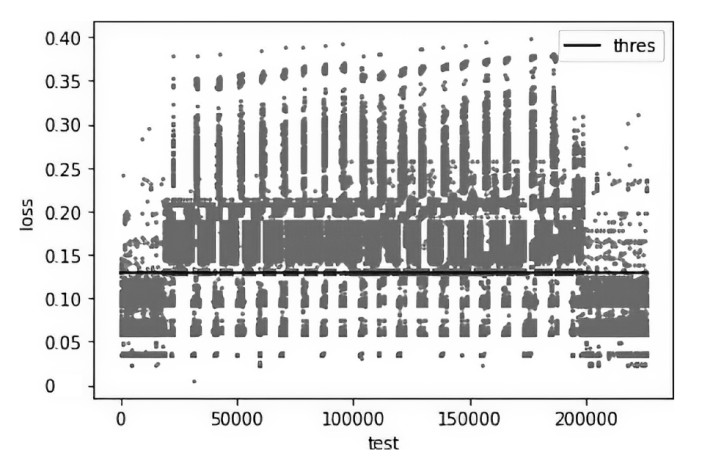
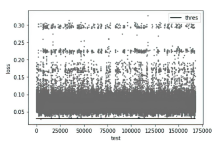
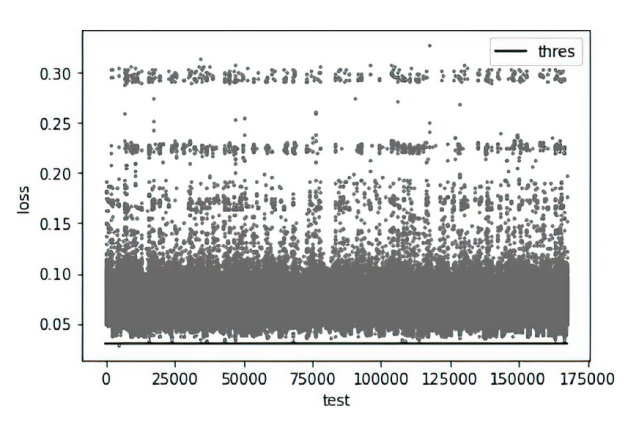
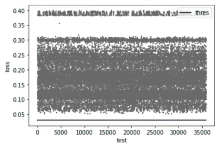
Netinfo Security ›› 2023, Vol. 23 ›› Issue (7): 74-85.doi: 10.3969/j.issn.1671-1122.2023.07.008
Previous Articles Next Articles
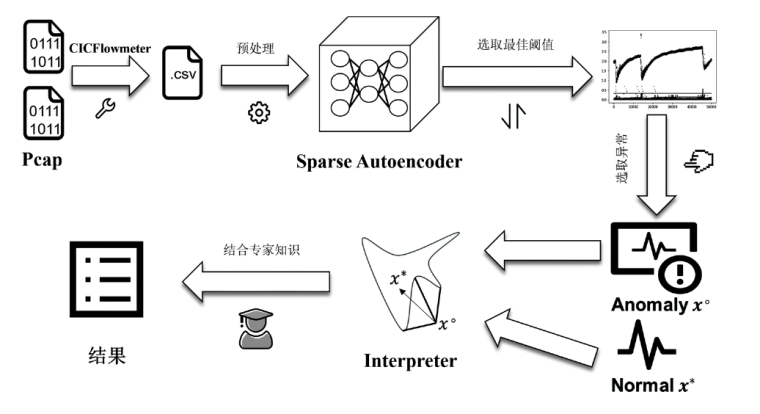
Explainable Anomaly Traffic Detection Based on Sparse Autoencoders
LIU Yuxiao, CHEN Wei( ), ZHANG Tianyue, WU Lifa
), ZHANG Tianyue, WU Lifa
- School of Computer Science, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
-
Received:2022-12-20Online:2023-07-10Published:2023-07-14
CLC Number:
Cite this article
LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders[J]. Netinfo Security, 2023, 23(7): 74-85.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.07.008
| 编号 | 特征名字 | 信息增益率 |
|---|---|---|
| 1 | min_seg_size_forward | 41.9% |
| 2 | Init_Win_bytes_backward | 41.2% |
| 3 | Init_Win_bytes_forward | 41.1% |
| 4 | Bwd Packet Length Min | 40.4% |
| 5 | Total Length of Bwd Packets | 40.4% |
| 6 | Subflow Bwd Bytes | 39.9% |
| 7 | Bwd Header Length | 39.5% |
| 8 | Fwd Header Length | 39.2% |
| 9 | Fwd Header Length.1 | 38.2% |
| 10 | Fwd PSH Flags | 35.6% |
| 11 | SYN Flag Count | 35.6% |
| 12 | Max Packet Length | 34.8% |
| 13 | Bwd Packet Length Mean | 34.6% |
| 14 | Avg Bwd Segment Size | 34.4% |
| 15 | Bwd Packet Length Max | 33.8% |
| 16 | FIN Flag Count | 33.5% |
| 17 | Total Backward Packets | 32.0% |
| 18 | Subflow Bwd Packets | 32.0% |
| 19 | ACK Flag Count | 31.7% |
| 20 | Destination Port | 29.9% |
| 21 | Total Fwd Packets | 29.7% |
| 22 | Subflow Fwd Packets | 29.1% |
| 23 | act_data_pkt_fwd | 25.4% |
| 24 | Min Packet Length | 25.4% |
| 25 | Fwd Packet Length Min | 25.2% |
| 26 | Fwd Packet Length Max | 25.1% |
| 27 | Total Length of Fwd Packets | 24.7% |
| 28 | Subflow Fwd Bytes | 23.4% |
| 29 | PSH Flag Count | 23.3% |
| 30 | Down/Up Ratio | 23.1% |
| 31 | Bwd Packet Length Std | 21.9% |
| 32 | Average Packet Size | 21.8% |
| 33 | Packet Length Mean | 21.5% |
| 34 | Packet Length Std | 21.4% |
| [1] | MIRSKY Y, DOITSHMAM T, ELOVICI Y, et al. Kitsune: An Ensemble of Autoencoders for Online Network Intrusion Detection[J]. Machine Learning, 2018, 5: 2-8. |
| [2] | DU Min, LI Feifei, ZHENG Guineng, et al. Deeplog: Anomaly Detection and Diagnosis from System Logs Through Deep Learning[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1285-1298. |
| [3] | BOWMAN B, LAPRADE C, JI Yuede, et al. Detecting Lateral Movement in Enterprise Computer Networks with Unsupervised Graph[C]// RAID. 23rd International Symposium on Research in Attacks, Intrusions and Defenses(RAID 2020). New York: ACM, 2020: 257-268. |
| [4] | SIDI L, MIRSKY Y, NADLER A, et al. Helix: DGA Domain Embeddings for Tracking and Exploring Botnets[C]// ACM. Proceedings of the 29th ACM International Conference on Information& Knowledge Management. New York: ACM, 2020: 2741-2748. |
| [5] | LIU Ninghao, SHIN D, HU Xia. Contextual Outlier Interpretation[C]// IJCAI. Proceedings of the 27th International Joint Conference on Artificial Intelligence. New York: ACM, 2018: 2461-2467. |
| [6] | GUO Wenbo, MU Dongliang, XU Jun, et al. Lemna: Explaining Deep Learning Based Security Applications[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 364-379. |
| [7] | RIBEIRO M T, SINGH S, GUESTRIN C. “ Why Should I Trust You?” Explaining the Predictions of Any Classifier[C]// ACM. Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2016: 1135-1144. |
| [8] | YANG Limin, GUO Wenbo, HAO Qingying, et al. {CADE}: Detecting and Explaining Concept Drift Samples for Security Applications[C]// USENIX. 30th USENIX Security Symposium(USENIX Security 21). New York: ACM, 2021: 2327-2344. |
| [9] | ANTWARG L, MILLER R M, SHAPIRA B, et al. Explaining Anomalies Detected by Autoencoders Using SHAP[EB/OL]. [2022-06-17]. https://arxiv.org/pdf/1903.02407.pdf. |
| [10] | HAN Dongqi, WANG Zhiliang, CHEN Wenqi, et al. DeepAID: Interpreting and Improving Deep Learning-Based Anomaly Detection in Security Applications[C]// ACM. Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 3197-3217. |
| [11] | LI Xukui, CHEN Wei, ZHANG Qianru, et al. Building Auto-Encoder Intrusion Detection System Based on Random Forest Feature Selection[J]. Computers& Security, 2020, 95: 851-859. |
| [12] | ZONG Bo, SONG Qi, MIN Martin, et al. Deep Autoencoding Gaussian Mixture Model for Unsupervised Anomaly Detection[EB/OL]. [2022-11-22]. https://openreview.net/forum?id=BJJLHbb0-. |
| [13] |
BINBUSAYYIS A, VAIYAPURI T. Unsupervised Deep Learning Approach for Network Intrusion Detection Combining Convolutional Autoencoder and One-Class SVM[J]. Applied Intelligence, 2021, 51(10): 7094-7108.
doi: 10.1007/s10489-021-02205-9 |
| [14] | JAFAR M T, AL-FAWA'REH M, AL-HRAHSHEH Z, et al. Analysis and Investigation of Malicious DNS Queries Using CIRA-CIC-DoHBrw-2020 Dataset[EB/OL]. [2022-11-17]. https://mjaias.co.uk/mj-en/article/view/24. |
| [15] | SAMMOUR M, HUSSIN B, OTHMAN F I. Comparative Analysis for Detecting DNS Tunneling Using Machine Learning Techniques[J]. International Journal of Applied Engineering Research, 2017, 12(22): 12762-12766. |
| [16] | AIELLO M, MONGELLI M, PAPALEO G. Basic Classifiers for DNS Tunneling Detection[C]// IEEE. 2013 IEEE Symposium on Computers and Communications(ISCC). New York: IEEE, 2013: 880-885. |
| [17] | ZHAO Hong, CHANG Zhaobin, BAO Guangbin, et al. Malicious Domain Names Detection Algorithm Based on N-gram[EB/OL]. [2022-11-17]. https://www.hindawi.com/journals/jcnc/2019/4612474/. |
| [18] | ALLARD F, DUBOIS R, GOMPEL P, et al. Tunneling Activities Detection Using Machine Learning Techniques[J]. Journal of Telecommunications and Information Technology, 2011: 37-42. |
| [19] |
BANADAKI Y M. Detecting Malicious DNS over Https Traffic in Domain Name System Using Machine Learning Classifiers[J]. Journal of Computer Sciences and Applications, 2020, 8(2): 46-55.
doi: 10.12691/jcsa-8-2-2 URL |
| [20] | IMAN S, ARASH H, ALI A. CIRA-CIC-DoHBrw-2020[EB/OL]. [2022-11-29]. https://www.unb.ca/cic/datasets/dohbrw-2020.html |
| [21] | IMAN SHARAFALDIN, ARASH Habibi Lashkari, ALI A. Ghorba-ni, Intrusion Detection Evaluation Dataset(CICIDS2017)[EB/OL]. [2022-11-29]. http://www.unb.ca/cic/datasets/ids2017.html. |
| [22] | ZHAO Ruijie, HUANG Yiteng, DENG Xianwen, et al. A Novel Traffic Classifier with Attention Mechanism for Industrial Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2023: 1-12. |
| [23] | DU Min, CHEN Zhi, LIU Chang, et al. Lifelong Anomaly Detection through Unlearning[C]// ACM. Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 1283-1297. |
| [24] | YAN Yu, QI Lin, WANG Jie, et al. A Network Intrusion Detection Method Based on Stacked Autoencoder and LSTM[C]// IEEE.ICC 2020-2020 IEEE International Conference on Communications(ICC). New York: IEEE, 2020: 1-6. |
| [25] | KINGMA D P, BA J. Adam: A Method for Stochastic Optimization[EB/OL]. [2022-12-17]. https://arxiv.org/pdf/1412.6980.pdf. |
| [26] | ZENATI H, ROMAIN M, FOO C S, et al. Adversarially Learned Anomaly Detection[C]// IEEE. 2018 IEEE International Conference on Data Mining(ICDM). New York: IEEE, 2018: 727-736. |
| [27] | XU Haowen, CHEN Wenxiao, ZHAO Nengwen, et al. Unsupervised Anomaly Detection via Variational Auto-Encoder for Seasonal KPIS in Web Applications[C]// IEEE. Proceedings of the 2018 World Wide Web Conference. New York: IEEE, 2018: 187-196. |
| [28] | BACH S, BINDER A, MONTAVON G, et al. On Pixel-Wise Explanations for Non-Linear Classifier Decisions by Layer-Wise Relevance Propagation[J]. PLOS ONE, 2015, 10(7): 1-46. |
| [1] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [2] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [3] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| [4] | XU Zhanyang, CHENG Luofei, CHENG Jianchun, XU Xiaolong. A Scheme of Optimizing Deep Learning Model Using Bi-ADMM [J]. Netinfo Security, 2023, 23(2): 54-63. |
| [5] | CHEN Depeng, LIU Xiao, CUI Jie, ZHONG Hong. Research on Membership Inference Attack Method Based on Double Threshold Function [J]. Netinfo Security, 2023, 23(2): 64-75. |
| [6] | JIA Fan, KANG Shuya, JIANG Weiqiang, WANG Guangtao. Vulnerability Similarity Algorithm Evaluation Based on NLP and Feature Fusion [J]. Netinfo Security, 2023, 23(1): 18-27. |
| [7] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [8] | ZHENG Yaohao, WANG Liming, YANG Jing. A Defense Method against Adversarial Attacks Based on Neural Architecture Search [J]. Netinfo Security, 2022, 22(3): 70-77. |
| [9] | GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder [J]. Netinfo Security, 2022, 22(12): 7-15. |
| [10] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [11] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [12] | ZHU Xintong, TANG Yunqi, GENG Pengzhi. Detection Algorithm of Tamper and Deepfake Image Based on Feature Fusion [J]. Netinfo Security, 2021, 21(8): 70-81. |
| [13] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [14] | MA Rui, CAI Manchun, PENG Shufan. A Deep Forgery Video Detection Model Based on Improved Xception Network [J]. Netinfo Security, 2021, 21(12): 109-117. |
| [15] | PAN Xiaoqin, DU Yanhui. Forged Voice Identification Method Based on Feature Fusion and Multi-channel GRU [J]. Netinfo Security, 2021, 21(10): 1-7. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||