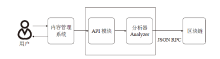
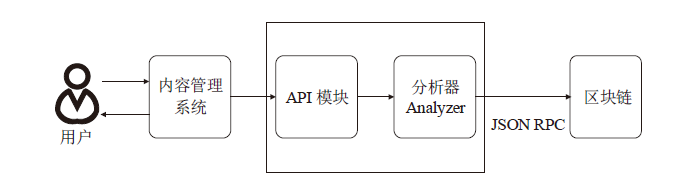
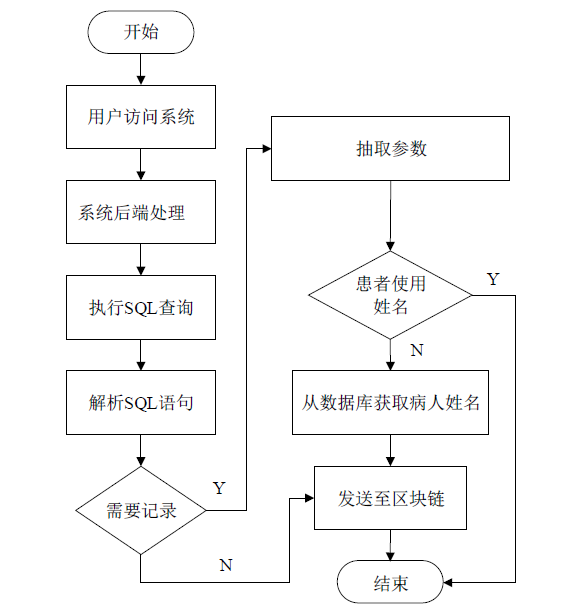
Netinfo Security ›› 2021, Vol. 21 ›› Issue (5): 58-66.doi: 10.3969/j.issn.1671-1122.2021.05.007
Previous Articles Next Articles
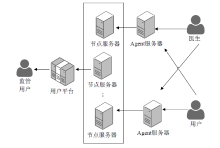
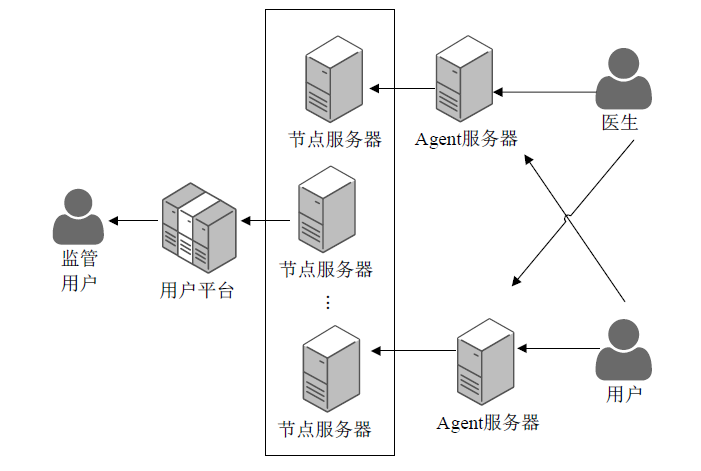
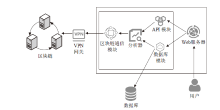
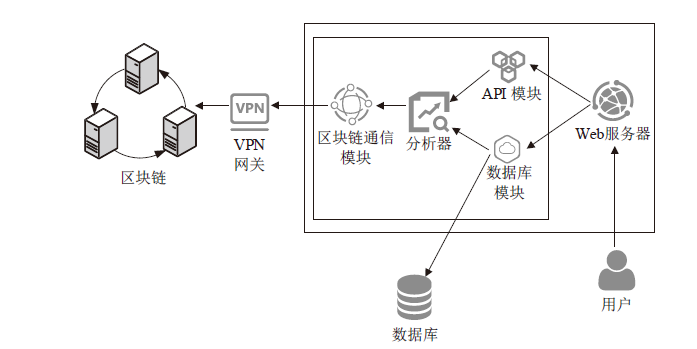
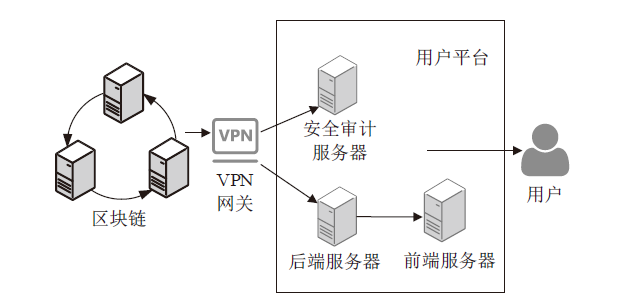
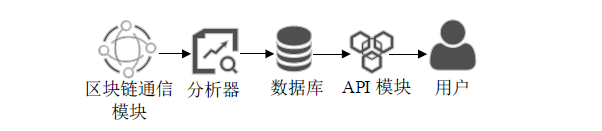
Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain
LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui( )
)
- School of information science and engineering, Lanzhou University, Lanzhou 730000, China
-
Received:2020-01-15Online:2021-05-10Published:2021-06-22 -
Contact:ZHOU Rui E-mail:zr@lzu.edu.cn
CLC Number:
Cite this article
LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain[J]. Netinfo Security, 2021, 21(5): 58-66.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.05.007
| [1] |
YUE Xiao, WANG Huiju, JIN Dawei, et al. Healthcare Data Gateways: Found Healthcare Intelligence on Blockchain with Novel Privacy Risk Control[J]. Journal of Medical Systems, 2016,40(10):1-8.
doi: 10.1007/s10916-015-0365-5 URL |
| [2] | ASHTON K. That ‘Internet of Things’ Thing[J]. RFID Journal, 2009,22(7):97-114. |
| [3] | DANNEN C. Introducing Ethereum and Solidity[M]. Berkeley: Apress, 2017. |
| [4] | METTLER M. Blockchain Technology in Healthcare: The Revolution Starts Here[C]// IEEE. 18th International Conference on E-health Networking, Applications and Services(Healthcom), September 14-17, 2016, Munich, Germany. New Jersey: IEEE, 2016: 1-3. |
| [5] | PRISCO G. The Blockchain for Healthcare: Gem Launches Gem Health Network with Philips Blockchain Lab[EB/OL]. https://bitcoinmagazine.com/articles/the-blockchain-for-heathcare-gem-launches-gem-health-network-with-philips-blockchain-lab-1461674938, 2016-04-26. |
| [6] | TAYLOR P. Applying Blockchain Technology to Medicine Traceability[EB/OL]. https://www.securingindustry.com/pharmaceuticals/applying-blockchain-technology-to-medicine-traceability/s40/a2766/, 2016-04-27. |
| [7] |
KUO T T, KIM H E, OHNO-MACHADO L. Blockchain Distributed Ledger Technologies for Biomedical and Health Care Applications[J]. Journal of the American Medical Informatics Association, 2017,24(6):1211-1220.
doi: 10.1093/jamia/ocx068 URL |
| [8] | WILLIAMS-GRUT O. Estonia is Using the Technology behind Bitcoin to Secure 1 Million Health Records[EB/OL]. https://www.businessinsider.in/Estonia-is-using-the-technology-behind-bitcoin-to-secure-1-million-health-records/articleshow/51246942.cms, 2016-03-03. |
| [9] | BAXENDALE G. Can Blockchain Revolutionise EPRs?[J]. ITNow, 2016,58(1):38-39. |
| [10] | ROLSTON M E, FICKLIN J L, NAIRN M A, et al. User-application Interface: U.S. Patent 9, 176, 747[P]. 2015-11-03. |
| [11] | BAKKEN D. Middleware[EB/OL]. http://www.dia.uniroma3.it/~cabibbo/ids/altrui/middleware-bakken.pdf, 2020-12-21. |
| [12] | BRAY T. The JavaScript Object Notation(JSON) Data Interchange Format[EB/OL]. https://tools.ietf.org/id/draft-ietf-jsonbis-rfc7159bis-04.html#:~:text=JavaScript%20Object%20Notation%20(JSON)%20is,portable%20representation%20of%20structured%20data, 2017-07-19. |
| [13] | THURLOW R. RPC: Remote Procedure Call Protocol Specification Version 2[EB/OL]. http://www.ietf.org/rfc/rfc5531.txt, 2020-12-21. |
| [14] | LONEY K. Oracle Database 10g: the Complete Reference[M]. London: McGraw-Hill/Osborne, 2004. |
| [15] | FIELDING R T, KAISER G. The Apache HTTP Server Project[J]. IEEE Internet Computing, 1997,1(4):88-90. |
| [16] | BACUDIO A G, YUAN X, CHU B T B, et al. An Overview of Penetration Testing[J]. International Journal of Network Security & Its Applications, 2011,3(6):19-38. |
| [17] |
LIAO H J, LIN C H R, LIN Y C, et al. Intrusion Detection System: A Comprehensive Review[J]. Journal of Network and Computer Applications, 2013,36(1):16-24.
doi: 10.1016/j.jnca.2012.09.004 URL |
| [18] | MONSHIZADEH M, NALDURG P, VENKATAKRISHNAN V N. Mace: Detecting Privilege Escalation Vulnerabilities in Web Applications[EB/OL]. https://dl.acm.org/doi/pdf/10.1145/2660267.2660337, 2020-05-14. |
| [19] | DigitalOcean. DigitalOcean-The Developer Cloud[EB/OL]. https://www.digitalocean.com/, 2020-12-21. |
| [20] | SUNDARAM R, KANIYAR S N. Measuring Network Jitter on Application Packet Flows: U.S. Patent 6, 928, 473[P]. 2005-08-09. |
| [21] | LARIMER D. Delegated Proof-of-stake (DPOS)[EB/OL]. https://steemit.com/bitshares/@testz/bitshares-history-delegated-proof-of-stake-dpos, 2020-12-21. |
| [22] | BACH L M, MIHALJEVIC B, ZAGAR M. Comparative Analysis of Blockchain Consensus Algorithms[C]// IEEE. 41st International Convention on Information and Communication Technology, Electronics and Microelectronics(MIPRO), May 21-25, 2018, Opatija, Croatia. New Jersey: IEEE, 2018: 1545-1550. |
| [23] | SALEM M B, STOLFO S J. Detecting Masqueraders: A Comparison of One-class Bag-of-words User Behavior Modeling Techniques[EB/OL]. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.180.6427, 2020-05-15. |
| [1] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [2] | ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme [J]. Netinfo Security, 2021, 21(5): 19-30. |
| [3] | WANG Kaixuan, TENG Yajun, WANG Qiongxiao, WANG Wei. Research on the Application of SM Algorithms of Implicit Certificate [J]. Netinfo Security, 2021, 21(5): 74-81. |
| [4] | CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology [J]. Netinfo Security, 2021, 21(4): 39-48. |
| [5] | REN Hang, CHENG Xiangguo, ZHANG Rui, XIA Hui. A Novel Fraud Prevention Strategy Based on Bargaining Bayesian Game Model [J]. Netinfo Security, 2021, 21(4): 81-88. |
| [6] | ZHOU Yousheng, WANG Ming, LIU Yuanni. Privacy Protection Scheme Supporting Interval Query for LBS Outsourced Data [J]. Netinfo Security, 2021, 21(3): 26-36. |
| [7] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [8] | SHANG Wen, WANG Hongxia. Speaker Identity Tracing Scheme in 5G Communication Based on Fingerprint [J]. Netinfo Security, 2021, 21(3): 79-86. |
| [9] | ZHANG Yinghui, ZHU Tian, ZHENG Dong. Multi-keyword Fine-grained Searchable Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2021, 21(2): 34-44. |
| [10] | JIN Zhigang, WANG Xinjian, LI Gen, YUE Shunmin. The Generation Method of Network Defense Strategy Combining with Attack Graph and Game Model [J]. Netinfo Security, 2021, 21(1): 1-9. |
| [11] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDSA for Blockchain Based on Hash Proof Systems [J]. Netinfo Security, 2021, 21(1): 19-26. |
| [12] | DONG Qiang, LUO Guoming, SHI Hongkui, ZHANG Yongyue. Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network [J]. Netinfo Security, 2021, 21(1): 88-96. |
| [13] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| [14] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [15] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||