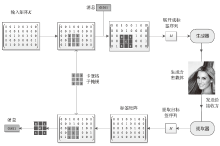
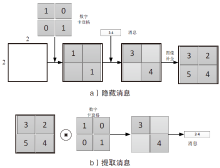
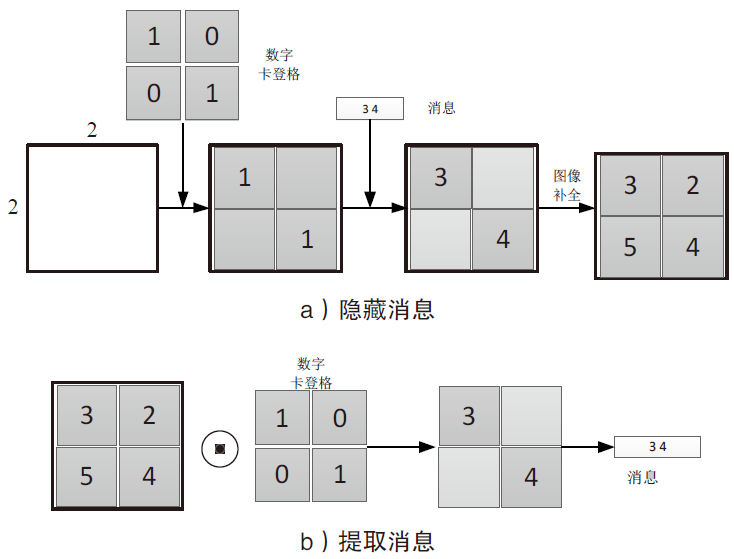
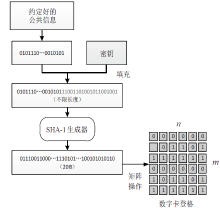
| [1] |
ZHANG Ru, DONG Shiqi, LIU Jianyi. Invisible Steganography Via Generative Adversarial Networks[J]. Multimedia Tools and Applications, 2019,18(2): 34-39.
|
| [2] |
GOODFELLOW I, POUGET-ABADIE J, MIRZA M. Generative Adversarial Networks[EB/OL]. http://arxiv.org/abs/1406.2661, 2014-06-10.
|
| [3] |
LIU Jia, ZHOU Tianping, ZHANG Zhuo, et al. Digital Cardan Grille: A Modern Approach for Information Hiding[EB/OL]. https://arxiv.org/abs/1803.09219.pdf, 2018-03-25.
|
| [4] |
SURHONE L M, TENNOE M T, HENSSONOW S F, et al. Card Catalog (cryptology)[M]. Montana USA: Betascript Publishing, 2010.
|
| [5] |
VOLKHONSKIY D, NAZAROV I, BORISENKO B, et al. Steganographic Generative Adversarial Networks[EB/OL]. http://arxiv.org/abs/1703.05502.pdf, 2017-03-16.
|
| [6] |
WANG Yaojie, NIU Ke, YANG Xiaoyuan. Image Steganography Scheme Based on Generative Adversarial Network[J]. Journal of Computer Applications, 2018,38(10): 177-182.
|
|
王耀杰, 钮可, 杨晓元. 基于生成对抗网络的信息隐藏方案[J]. 计算机应用, 2018,38(10): 177-182.
|
| [7] |
KE Yan, LIU Jia, ZHANG Minqing, et al. Steganography Security: Principle and Practice[J]. IEEE Access, 2018,1(99): 15-19.
|
| [8] |
FRIDRICH J. Steganography in Digital Media: Principles, Algorithms, and Applications[M]. Cambridge: Cambridge University Press, 2010.
|
| [9] |
LIU Mingming, LI Xinchao. Information Hiding Method Based on Cardan Grille[J]. Journal of Engineering University of PAP, 2018. 34(6): 58-62.
|
|
刘明明, 李新超. 基于卡登格子的信息隐藏方法[J]. 武警工程大学学报, 2018,34(6): 58-62.
|
| [10] |
ODENA A, OLAH C, SHLENS J. Conditional Image Synjournal with Auxiliary Classifier GANs[J]. Computer Science, 2016,18(1): 14-20.
|
| [11] |
CUI Zhongli, WANG Jiazhen. Generalizable Steganography Algorithm Based on DCT Domain[J]. Computer Engineering and Design, 2006,27(13): 2449-2451.
|
|
崔忠立, 王嘉祯. 可泛化的基于DCT域的隐写术算法[J]. 计算机工程与设计, 2006,27(13): 2449-2451.
|
| [12] |
NOVOTNY M A. Matrix Products with Applications to Classical Statistical Mechanics[J]. Journal of Biomedical Materials Research, 1978,56(3): 452-458.
doi: 10.1002/1097-4636(20010905)56:3<452::aid-jbm1115>3.0.co;2-1
URL
pmid: 11372064
|
| [13] |
RAGAB A H M, ISMAIL N A, ALLAH O S F. AN Efficient Message Digest Algorithm (MD) for Data Security[C]//IEEE. 2001 Tencon IEEE Region 10th International Conference on Electrical & Electronic Technology, November 8-12, 2001, Seattle, USA. New York: IEEE, 2001: 723-734.
|
| [14] |
ZHANG Hongying, PENG Qizong. Overview of Digital Image Restoration Technology[J]. Journal of Image and Graphics, 2007,1(1): 1-10.
|
|
张红英, 彭启琮. 数字图像修复技术综述[J]. 中国图象图形学报, 2007,1(1): 1-10.
|
| [15] |
LIU Jia, KE Yan, LEI Yu, et al. The Reincarnation of Grille Cipher: A Generative Approach[EB/OL]. https://arxiv.org/abs/1804.06514.pdf, 2018-04-15.
|
| [16] |
YEH R A, CHEN C, LIM T Y, et al. Semantic Image Inpainting with Deep Generative Models[J]. IEEE Computer Society, 2016,16(7): 83-88.
|
| [17] |
RADFORD A, METZ L, CHINTALA S. Unsupervised Representation Learning with Deep Convolutional Generative Adversarial Networks[J]. Computer Science, 2015,34(8): 127-131.
|
| [18] |
HOU Xuedong. Image Translation Based on Generative Adversarial Networks[D]. Nanjing: Nanjing University of Posts and Telecommunications, 2018.
|
|
候学东. 基于生成对抗网络的图像翻译[D]. 南京: 南京邮电大学, 2018.
|
| [19] |
AMOS B. Image Completion with Deep Learning in TensorFlow[EB/OL]. https://github.com/bamos/dcgan-completion.tensorflow, 2018-09-23.
|
| [20] |
MANDGAONKAR V S, KULKARNI C V. No Reference Image Quality Assessment[C]// IEEE. 2014 Annual IEEE India Conference (INDICON), November 8-12, 2014, New York, USA. New York: IEEE, 2015: 1241-1248.
|
| [21] |
SURYAWANSHI G R, MALI S N. Study of Effect of DCT Domain Steganography Techniques in Spatial Domain for JPEG Images Steganalysis[J]. International Journal of Computer Applications, 2015,127(6): 16-20.
|
| [22] |
ZHEN Yu, CHEN Kefei. Analysis and Improvement on RS Detection Algorithm[J]. Computer Engineering, 2008,34(8): 168-170.
|
| [23] |
YAN Huijuan, QIN Jie. Trojan Horse Detection Method Based on Nonlinear SVM Model[J]. Computer Engineering, 2011,11(2): 134-137.
|
| [24] |
CHEN Tao, LU Shijian, FAN Jiayuan. S-CNN: Subcategory-aware Convolutional Networks for Object Detection[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2017,16(4): 12-17.
|
 )
)