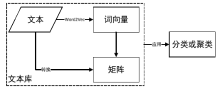
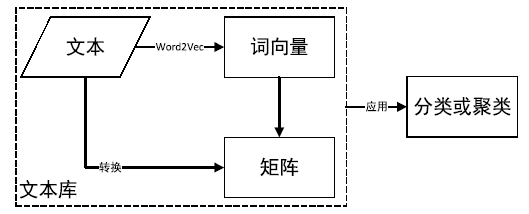
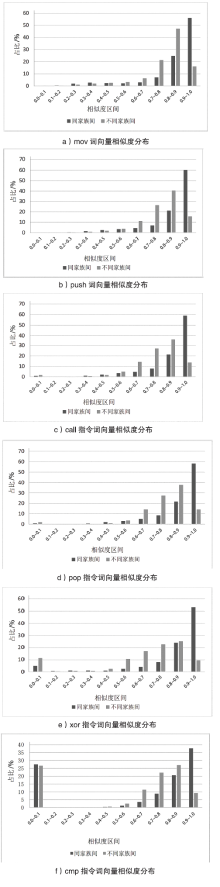
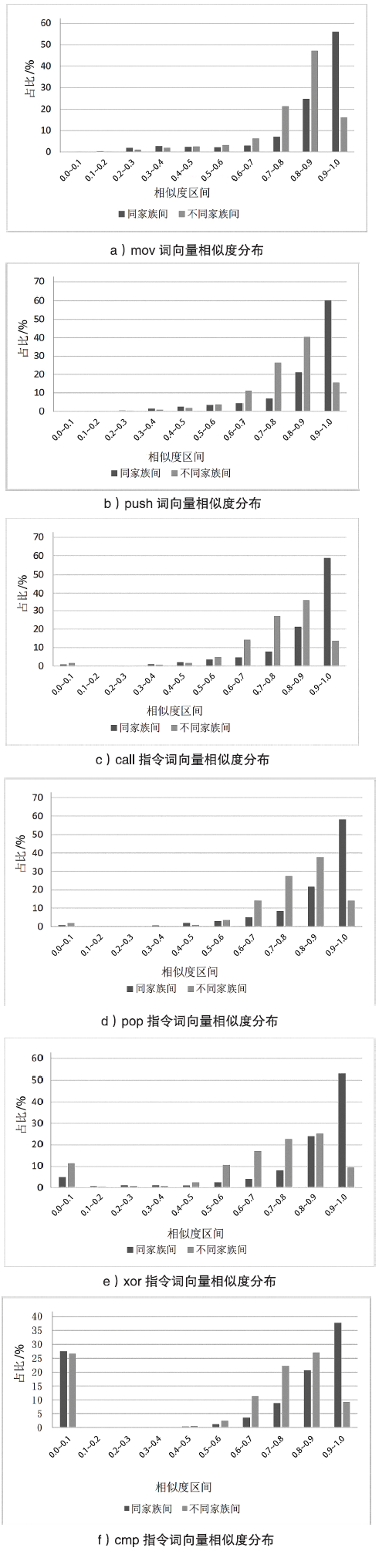
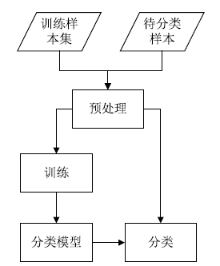
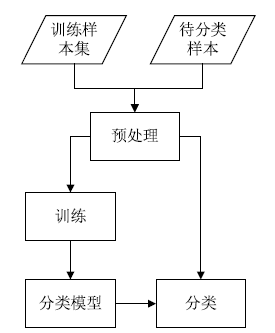
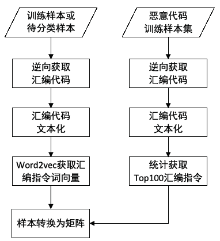
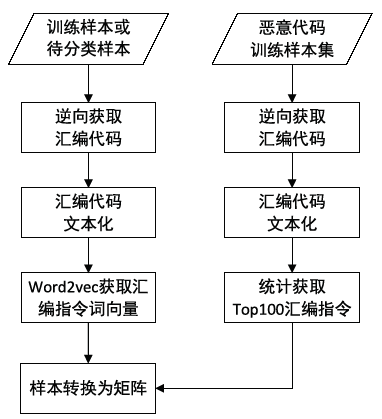
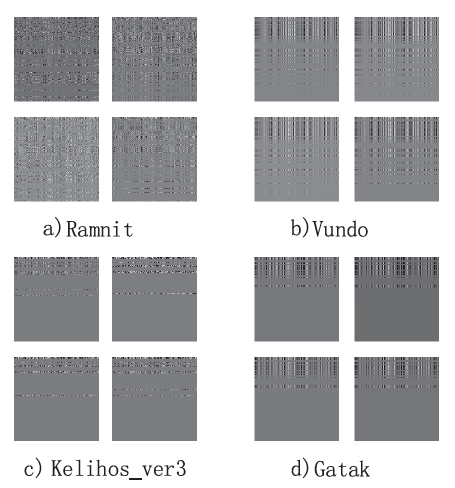
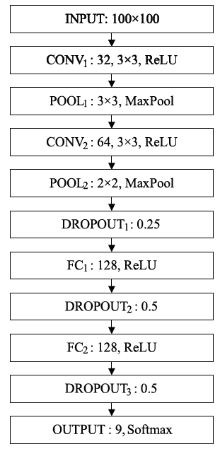
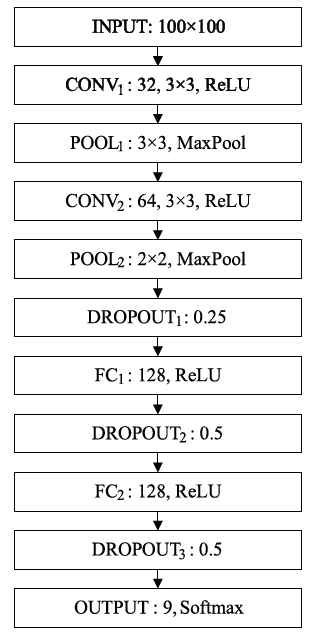
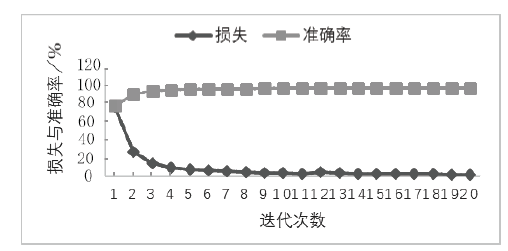
Netinfo Security ›› 2019, Vol. 19 ›› Issue (4): 20-28.doi: 10.3969/j.issn.1671-1122.2019.04.003
Previous Articles Next Articles
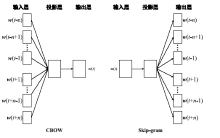
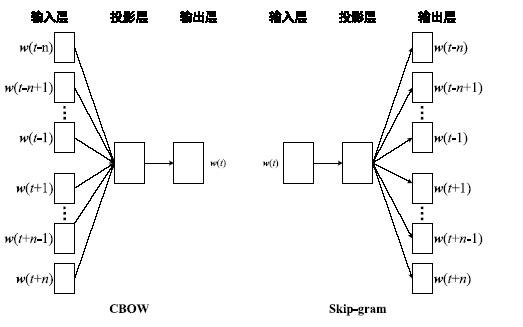
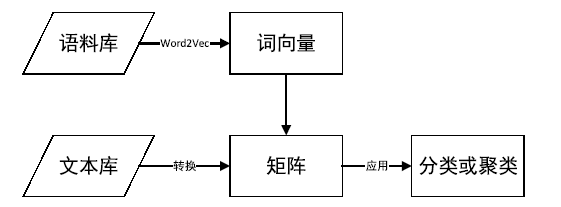
Malware Classification Method Based on Word Vector of Assembly Instruction and CNN
Yanchen QIAO1,2( ), Qingshan JIANG1, Liang GU2, Xiaoming WU3
), Qingshan JIANG1, Liang GU2, Xiaoming WU3
- 1. Shenzhen Institutes of Advanced Technology, Chinese Academy of Science, Shenzhen Guangdong 518000, China
2. Sangfor Technologies Inc, Shenzhen Guangdong 518000, China
3. Unit 31436 of PLA, Shenyang Liaoning 110001, China
-
Received:2018-12-10Online:2019-04-10Published:2020-05-11
CLC Number:
Cite this article
Yanchen QIAO, Qingshan JIANG, Liang GU, Xiaoming WU. Malware Classification Method Based on Word Vector of Assembly Instruction and CNN[J]. Netinfo Security, 2019, 19(4): 20-28.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2019.04.003
| [1] | AV-TEST INSTITUTE. Malware Statistics & Trends Report[EB/OL]..2018-6-15. |
| [2] | MIKOLOV T, CHEN K, CORRADO G, et al. Efficient Estimation of Word Representations in Vector Space[EB/OL].arXiv preprint arXiv:13013781, 2013-5-5. |
| [3] | RONEN R, RADU M, FEUERSTEIN C, et al. Microsoft Malware Classification Challenge[EB/OL].arXiv preprint arXiv:180210135, 2018-6-15. |
| [4] | SCHULTZ M G, ESKIN E, ZADOK F, et al.Data Mining Methods for Detection of New Malicious Executables[C]//IEEE. 2001 IEEE Symposium on Security and Privacy, May 14-16, 2001, Oakland, California, USA. New York: IEEE, 2001: 38-49. |
| [5] | KOLTER J Z, MALOOF M A.Learning to Detect Malicious Executables in the Wild[C]//ACM. Proceedings of the 10th ACM SIGMOD International Conference on Knowledge Discovery and Data Mining, June 13-18, 2004, Paris, France. New York: ACM, 2004: 470-478. |
| [6] | TIAN R, BATTEN L M, VERSTEEG S.Function Length as a Tool for Malware Classification[C]//IEEE. IEEE 3rd International Conference on Malicious and Unwanted Software, October 7-8, 2008, Alexandria, Virginia, USA. New York: IEEE, 2008: 69-76. |
| [7] | SALEHI Z, GHIASI M, SAMI A.A Miner for Malware Detection Based on API Function Calls and Their Arguments[C]//IEEE. The 16th CSI International Symposium on Artificial Intelligence and Signal Processing (AISP 2012), May 2-3, 2012, Shiraz, Fars, Iran. New York: IEEE, 2012: 563-568. |
| [8] | DAHL G E, STOKES J W, DENG L, et al.Large-scale Malware Classification Using Random Projections and Neural Networks[C]//IEEE. Proceedings of the 2013 IEEE International Conference on Acoustics, Speech and Signal Processing, May 26-31, 2013, Vancouver, BC, Canada. New York: IEEE, 2013: 3422-3426. |
| [9] | SAXE J, BERLIN K.Deep Neural Network Based Malware Detection Using two Dimensional Binary Program Features[C]//IEEE. IEEE 10th International Conference on Malicious and Unwanted Software, October 20-22, 2015, Fajardo, PR, USA. New York: IEEE, 2015: 11-20. |
| [10] | NARI S, GHORBANI A A.Automated Malware Classification Based on Network Behavior[C]//IEEE. Proceedings of the 2013 International Conference on Computing, Networking and Communications (ICNC), January 28-31, 2013, San Diego, California, USA. New York: IEEE, 2013: 642-647. |
| [11] | PARK Y, REEVES D S, STAMP M.Deriving Common Malware Behavior through Graph Clustering[J]. Computers & Security, 2013, 39(6): 419-430. |
| [12] | PASCANU R, STOKES J W, SANOSSIAN H, et al.Malware Classification with Recurrent networks[C]//IEEE. Proceedings of the 2015 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Apirl 19-24, 2015, South Brisbane, Queensland, Australia. New York: IEEE, 2015: 1916-1920. |
| [13] | GIANNELLA C, BLOEDORN E.Spectral Malware Behavior Clustering[C]//IEEE. 2015 IEEE International Conference on Intelligence and Security Informatics (ISI), May 27-29, 2015, Baltimore, MD, USA. New York: IEEE, 2015: 7-12. |
| [14] | HUANG Wenyi, STOKES J W.MtNet: A Multi-Task Neural Network for Dynamic Malware Classification[C]//Springer. Proceedings of the 13th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, July 7-8, 2016, San Sebastián, Spain. New York: Springer, 2016: 399-418. |
| [15] | GAO Jin, HE Yahao, ZHANG Xiaoyan, et al.Duplicate Short Text Detection Based on Word2vec[C]//IEEE. Proceedings of 2017 IEEE 8th International Conference on Software Engineering and Service Science, November 24-26, 2017, Beijing, China. New York: IEEE, 2017: 53-57. |
| [16] | ZHANG Dongwen, XU Hua, SU Zengcai, et al.Chinese Comments Sentiment Classification Based on Word2vec and SVM Perf[J].Expert Systems With Applications, 2015, 42(4): 1857-1863. |
| [17] | POPOV I.Malware Detection Using Machine Learning Based on Word2vec Embeddings of Machine Code Instructions[C]//IEEE. IEEE 2017 Siberian Symposium on Data Science and Engineering (SSDSE), Apirl 12-13, 2017, Novosibirsk, Russia. New York: IEEE, 2017: 1-4. |
| [18] | TRAN T K, SATO H.NLP-based Approaches for Malware Classification from API Sequences[C]//IEEE. The 21st Asia Pacific Symposium on Intelligent and Evolutionary Systems (IES 2017), November 15-17, 2017, Hanoi, Vietnam. New York: IEEE, 2017: 101-105. |
| [19] | LE Q, MIKOLOV T.Distributed Representations of Sentences and Documents[C]//JMLR. The 31th International Conference on Machine Learning, June 21-26, 2014, Beijing, China. New York: JMLR, 2017: 1188-1196. |
| [20] | CAKIR B, DOGDU E.Malware Classification Using Deep Learning Methods[C]//ACM. 2nd Annual Conference on Material Science and Engineering (ACMSE 2018), November 12-14, 2018, Dubai, United Arab Emirates. New York: ACM, 2018: 1-5. |
| [21] | FRIEDMAN J H.Greedy Function Approximation: A Gradient Boosting Machine[J]. Annals of Statistics, 2001, 29(5): 1189-1232. |
| [22] | SHANKARAPANI M K, RAMAMOORTHY S, MOVVA R S, et al.Malware Detection Using Assembly and API Call Sequences[J].Journal in Computer Virology, 2011, 7(2): 107-119. |
| [23] | FUKUSHIMA K.Neocognitron: A Hierarchical Neural Network Capable of Visual Pattern Recognition[J]. Neural Networks, 1988, 1(2): 119-130. |
| [24] | YAN Zhicheng, JAGADEESH V, DECOSTE D, et al.HD-CNN: Hierarchical Deep Convolutional Neural Network for Image Classification[C]//IEEE. Proceedings of the 2015 IEEE International Conference on Computer Vision (ICCV 2015), December 7-13, 2015, Santiago, Chile. New York: IEEE, 2015: 2740-2748. |
| [25] | KULKARNI P, ZEPEDA J, JURIE F, et al.Hybrid Multi-layer Deep CNN/Aggregator Feature for Image Classification[C]//IEEE. 2015 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), April 19-24, 2015, Brisbane, QLD, Australia. New York: IEEE, 2015: 1379-1383. |
| [26] | WANG Jiang, YANG Yi, MAO Junhua, et al.CNN-RNN: A Unified Framework for Multi-label Image Classification[C]//IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), June 27-30, 2016, Las Vegas, NV, USA. New York: IEEE, 2016: 2285-2294. |
| [27] | WEI Yunchao, XIA Wen, LIN Min, et al.HCP: A Flexible CNN Framework for Multi-label Image Classification[J]. IEEE Transactions on Pattern Analysis & Machine Intelligence, 2016, 38(9): 1901-1907. |
| [28] | LECUN Y, BOTTOU L, BENGIO Y, et al.Gradient-based Learning Applied to Document Recognition[J]. Proceedings of the IEEE, 1998, 86(11): 2278-2324. |
| [29] | KRIZHEVSKY A, SUTSKEVER I, HINTON G E.ImageNet Classification with Deep Convolutional Neural Networks[C]//Springer. Proceedings of the 19th International Conference on Neural Information Processing, November 12-15, 2012, Doha, Qatar. New York: Springer, 2012: 1097-1105. |
| [30] | SIMONYAN K, ZISSERMAN A. Very Deep Convolutional Networks for Large-Scale Image Recognition[EB/OL]. arXiv preprint arXiv:1409.1556, 2014-3-15. |
| [31] | SZEGEDY C, LIU W, JIA Y, et al.Going Deeper with Convolutions[C]//IEEE. 2015 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), June 7-12, 2015, Boston, MA, USA. New York: IEEE, 2015: 1-9. |
| [32] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al.Deep Residual Learning for Image Recognition[C]//IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), June 27-30, 2016, Las Vegas, NV, USA. New York: IEEE, 2016: 770-778. |
| [33] | LECUN Y, BOSER B, DENKER J S, et al.Backpropagation Applied to Handwritten Zip Code Recognition[J]. Neural Comput, 1989, 1(4): 541-551. |
| [1] | Chun GUO, Changqing CHEN, Guowei SHEN, Chaohui JIANG. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [2] | Liuyang HOU, Senlin LUO, Limin PAN, Ji ZHANG. Multi-feature Android Malware Detection Method [J]. Netinfo Security, 2020, 20(1): 67-74. |
| [3] | SONG Xin, ZHAO Kai, ZHANG Linlin, FANG Wenbo. Research on Android Malware Detection Based on Random Forest [J]. Netinfo Security, 2019, 19(9): 1-5. |
| [4] | LI Hui, NI Shice, XIAO Jia, ZHAO Tianzhong. Emotion Classification Technology for Online Video Comments on the Internet [J]. 信息网络安全, 2019, 19(5): 61-68. |
| [5] | Xuruirui FENG, Jiayong LIU, Pengsen CHENG. Analyzing Malware Behavior and Capability Related Text Based on Feature Extraction [J]. Netinfo Security, 2019, 19(12): 72-78. |
| [6] | Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis [J]. Netinfo Security, 2019, 19(10): 24-31. |
| [7] | CHEN Hongsong, WANG Gang, SONG Jianlin. Research on Anomaly Behavior Classification Algorithm of Internal Network User Based on Cloud Computing Intrusion Detection Data Set [J]. 信息网络安全, 2018, 18(3): 1-7. |
| [8] | LI Yunchun, LU Wentao, LI Wei. Malware Detection Method Based on Shapelet [J]. 信息网络安全, 2018, 18(3): 70-77. |
| [9] | WEI Shuning, CHEN Xingru, TANG Yong, LIU Hui. Research on the Application of AR-HELM Algorithm in Network Traffic Classifi cation [J]. 信息网络安全, 2018, 18(1): 9-14. |
| [10] | CHEN Xu, LI Yukun, YUAN Huaping, LIU Wenyin. Phishing Detection System Based on Classification Confidence and Website Features [J]. 信息网络安全, 2017, 17(9): 111-114. |
| [11] | JIANG Zhuojian, WU Chunhua, XIA Ming. Research and Implementation on Multi-Layer User Classification Method Based on Cloud System [J]. 信息网络安全, 2017, 17(8): 69-75. |
| [12] | REN Hao, LUO Senlin, PAN Limin, GAO Junfeng. Research on the Algorithm of Short Text Representation Based on Graph Structure [J]. 信息网络安全, 2017, 17(3): 46-52. |
| [13] | ZHANG Tengfei, ZHANG Qian, LIU Jiayong. URL Classification Method Based on AdaBoost and Bayes Algorithm [J]. 信息网络安全, 2017, 17(3): 66-71. |
| [14] | WANG Bo, WANG Huaibin. Research on Imbalanced Abnormal Data Classification Algorithm Based on Active Learning [J]. 信息网络安全, 2017, 17(10): 42-49. |
| [15] | ZHANG Qian, GAO Zhangmin, LIU Jiayong. Research of Weibo Short Text Classification Based on Word2vec [J]. 信息网络安全, 2017, 17(1): 57-62. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||