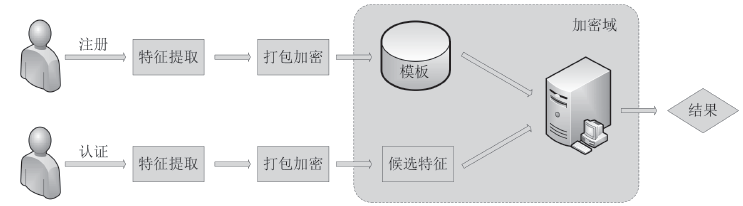
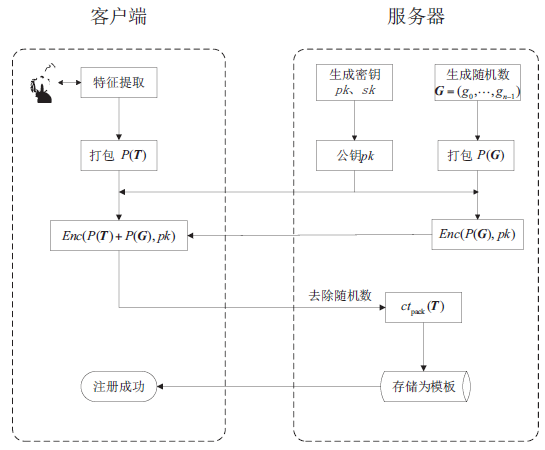
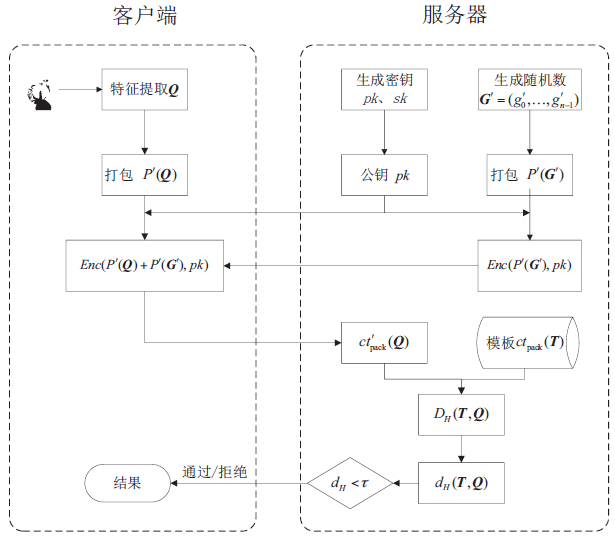
| [1] |
ZHOU Liansong, YANG Jie, TAN Pingzhang, et al.Identity Authentication Technology and Its Development Trend[J]. Communications Technology, 2009,42(10):183-185.
|
|
周楝淞,杨洁, 谭平嶂, 等. 身份认证技术及其发展趋势[J]. 通信技术, 2009,42(10):183-185.
|
| [2] |
FENG Quan.Privacy-protection Authentication Based on Fingerprint [D]. Beijing: Beijing University of Posts and Telecommunications, 2010.
|
|
冯全. 基于指纹的隐私保护型身份认证技术 [D]. 北京:北京邮电大学,2010.
|
| [3] |
WANG Yuna, LV Qiuyun.A New Network Authentication Scheme Based on Biometric Recognition[J]. Netinfo Security, 2014(8):1-5.
|
|
王毓娜, 吕秋云. 基于生物识别的网络身份认证新方案[J]. 信息网络安全, 2014(8):1-5.
|
| [4] |
JAIN A K, NANDAKNMAR K, NAGAR A.Biometric Template Security[J]. EURASIP Journal on Advances in Signal Processing, 2008(1): 1-17.
|
| [5] |
RIVEST R L, ADLEMAN L, DERTOUZOS M L.On Data Banks and Privacy Homomorphisms[J]. Foundations of Secure Computations, 1978,4(11):169-180.
|
| [6] |
ELGAMAL T.A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms[J]. IEEE Trans.inf.theory, 1985, 31(4):469-472.
|
| [7] |
PAILLIER P.Public-key Cryptosystems Based on Composite Degree Residuosity Classes[C]// EUROCRYPT. the 17th Internatinal Conference on Theory and Application of Cryptographic Techniques, May 2-6, 1999, Prague, Czech Republic. Heidelberg: Springer Berlin Heidelberg, 1999, 547(1):223-238.
|
| [8] |
BONEH D, GOH E J, NISSIM K.Evaluating 2-DNF Formulas on Ciphertexts[C]// TCC. the Second International Conference on Theory of Cryptography, February 10 - 12, 2005. Cambridge, MA,USA.Heidelberg: Springer Berlin Heidelberg, 2005:325-341.
|
| [9] |
GENTRY C.A Fully Homomorphic Encryption Scheme [D]. Palo Alto :Stanford University, 2009.
|
| [10] |
SMART N P, VERCAUTEREN F.Fully Homomorphic Encryption with Relatively Small Key and Ciphertext Sizes[C]// PKC. the 13th International Conference on Practice and Theory in Public Key Cryptography, May 26 - 28, 2010, Paris, France. Heidelberg: Springer Berlin Heidelberg, 2010:420-443.
|
| [11] |
EL-YAHYAOUI A.A Verifiable Fully Homomorphic Encryption Scheme to Secure Big Data in Cloud Computing[C]// IEEE. the International Conference on Wireless Networks and Mobile Communications, November 1-4, 2017,Rabat, Morocco.NJ: IEEE,2017:1-5.
|
| [12] |
ZHU Zhengyang, LIU Qiang, TANG Chunming, et al.Electronic Voting Scheme based on LWE Homomorphic Encryption[J]. Netinfo Security, 2013(5):8-11.
|
|
朱正阳, 刘镪, 唐春明,等. 基于LWE同态加密的电子投票方案[J]. 信息网络安全, 2013(5):8-11.
|
| [13] |
UPMANYU M, NAMBOODIRI A M, SRINATHAN K, et al.Blind Authentication: a Secure Crypto-biometric Verification Protocol[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(2): 255-268.
|
| [14] |
BARNI M, BIANCHI T, CATALANO D.et al.A Privacy-compliant Fingerprint Recognition System Based on Homomorphic Encryption and Fingercode Template[C]// IEEE. Fourth IEEE International Conference on Biometrics: Theory Applications and Systems, September 27-29, 2010, Washington, DC, USA.NJ: IEEE, 2010:1-7.
|
| [15] |
SARIER N D.Practical Multi-factor Biometric Remote Authentication[C]// IEEE. Fourth IEEE International Conference on Biometric: Theory Application & Systems, September 27-29, 2010, Washington, DC, USA.NJ: IEEE,2010:1-6.
|
| [16] |
HIRANO T, HATTORI M, ITO T, et al.Homomorphic Encryption-based Cancelable Biometrics Secure against Replay and Its Related Attack[C]//IEEE. International Symposium on Information Theory and Its Application(ISITA), October 28-31, 2012, Honolulu, HI, USA. NJ: IEEE, 2012:421-425.
|
| [17] |
BRINGER J, CHABANNE H, PATEY A.Privacy-preserving Biometric Identification Using Secure Multiparty Computation: An Overview and Recent Trends[J]. IEEE Signal Processing Magazine, 2013, 30(2):42-52.
|
| [18] |
ABDULJABBAR Z A, JIN Hai, IBRAHIM A, et al.Secure Biometric Image Retrieval in IoT-cloud[C]//IEEE. IEEE International Conference on Signal Processing, Communications and Computing, August 5-8, 2016, Hong Kong, China.NJ: IEEE, 2016:1-6.
|
| [19] |
HAHN C, HUR J.Efficient and Privacy-preserving Biometric Identification in Cloud[J]. ICT Express, 2016, 2(3):135-139.
|
| [20] |
YASUDA M.Secure Hamming Distance Computation for Biometrics Using Ideal-lattice and Ring-LWE Homomorphic Encryption[J]. Information Systems Security,2017, 26(2):85-103.
|
| [21] |
WANG Yongjian, ZHANG Jian, CHENG Shaoyu, et al.An Improved Design of Homomorphic Encryption for Cloud Computing[J]. Netinfo Security, 2017(3):21-26.
|
|
王永建, 张健, 程少豫,等. 面向云计算的同态加密改进设计[J]. 信息网络安全, 2017(3):21-26.
|
| [22] |
LAUTER K, NAEHRIG M, VAIKUNTANATHAN V.Can Homomorphic Encryption Be Practical?[C]//ACM. Proceedings of 3rd ACM Cloud Computing Security Workshop, CCSW 2011, October 21-21,2011, Chicago, Ilinois, USA.New York: ACM, 2011:113-124.
|
| [23] |
YASUDA M, SHIMOYAMA T, KOGURE J, et al.Practical Packing Method in Somewhat Homomorphic Encryption[M]. Heidelberg :Springer Berlin Heidelberg, 2014.
|
| [24] |
OSADCHY M, PINKAS B, JARROUS A, et al.SCiFI- a System for Secure Face Identification[C]//IEEE. Proceedings of the 2010 IEEE Symposium on Security and Privacy. May 16-19, 2010, Washington, DC, USA. NJ:IEEE Computer Society, 2010:239-254.
|
| [25] |
MITSUHIRO H, NORI M, TAKASHI I, et al.Provably-secure Cancelable Biometric Using 2-DNF Evaluation[J]. Journal of information Processing, 2012,20(2):496-507.
|