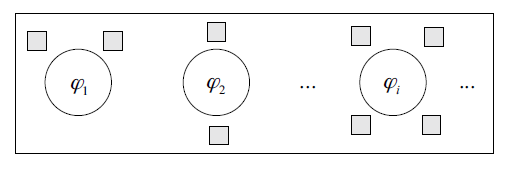
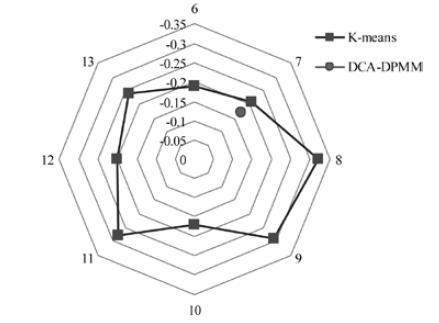
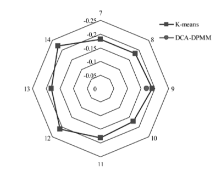
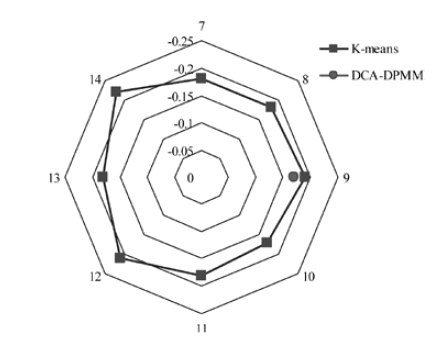
Netinfo Security ›› 2015, Vol. 15 ›› Issue (11): 60-65.doi: 10.3969/j.issn.1671-1122.2015.11.010
Previous Articles Next Articles
A Document Clustering Algorithm Based on Dirichlet Process Mixture Model
GAO Yue1, WANG Wen-xian1,2, YANG Shu-xian3
- 1. Network and Trusted Computing Institute, College of Computer, Sichuan University, Chengdu Sichuan 610065, China
2. Cyberspace Security Research Institute, of Sichuan University, Chengdu Sichuan 610065, China
3. The Superme People's Procuratorate of the People's Republie of China, Beijing 100726, China
-
Received:2015-10-12Online:2015-11-25Published:2015-11-20
CLC Number:
Cite this article
GAO Yue, WANG Wen-xian, YANG Shu-xian. A Document Clustering Algorithm Based on Dirichlet Process Mixture Model[J]. Netinfo Security, 2015, 15(11): 60-65.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2015.11.010
| [1] | Jiawei H, Kamber M.Data Mining Concepts and Techniques (Third Edition)[M]. San Francisco: Morgan Kaufmann, 2011. |
| [2] | Hartigan J A, Wong M A.Algorithm AS 136: A k-means Clustering Algorithm[J]. Applied Statistics, 1979, 28(1): 100-108. |
| [3] | Bouman C A, Shapiro M, Cook G W, et al. Cluster: An Unsupervised Algorithm for Modeling Gaussian Mixtures [EB/OL].Online available 2015-8-16. |
| [4] | Sharif-Razavian N, Zollmann A. An Overview of Nonparametric Bayesian Models and Applications to Natural Language Processing [EB/OL]. Online available: 2015-8-16. |
| [5] | Teh Y W, Jordan M I, Beal M J, et al.Hierarchical Dirichlet Processes[J]. Journal of the American Statistical Association, 2006, 101(476): 1566-1581. |
| [6] | Vlachos A, Korhonen A, Ghahramani Z.Unsupervised and Constrained Dirichlet Process Mixture Models for Verb Clustering[C]//Proceedings of the Workshop on Geometrical Models of Natural Language Semantics. Association for Computational Linguistics, 2009: 74-82. |
| [7] | Fox E B, Choi D S, Willsky A S.Nonparametric Bayesian Methods for Large Scale Multi-target Tracking[C]//ACSSC'06. Fortieth Asilomar Conference on Signals, Systems and Computers. IEEE, 2006: 2009-2013. |
| [8] | Zhang Z H, Dai G, Jordan M I.Matrix-variate Dirichlet Process Mixture Models[C]// Proceedings of the 13th International Conference on Artificial Intelligence and Statistics. Sardinia, Italy: The MIT Press, 2010:980-987 |
| [9] | Ferguson T S.A Bayesian Analysis of Some Nonparametric Problems[J]. The Annals of Statistics, 1973, 1(2): 209-230. |
| [10] | Teh Y W.Dirichlet Process[M]. Springer US, 2010. |
| [11] | Pitman J.Poisson-Dirichlet and GEM Invariant Distributions for Split-and-merge Transformation of an Interval Partition[J]. Combinatorics, Probability and Computing, 2002, 11(5): 501-514. |
| [12] | Blackwell D, MacQueen J B. Ferguson Distributions via Polya Urn Schemes[J]. The Annals of Statistics, 1973, 1(2): 353-355. |
| [13] | Pitman J.Combinatorial Stochastic Processes[R]. California: UC Berkeley, Lecture notes for St. Flour course, 2002. |
| [14] | Neal R M.Bayesian Mixture Modeling Maximum Entropy and Bayesian Methods[M].Springer Netherlands, 1992. |
| [15] | 孙兴东,李爱平,李树栋. 一种基于聚类的微博关键词提取方法的研究与实现[J]. 信息网络安全,2014,(12):27-31. |
| [16] | John M.Inference for Dirichlet-Multinomials and Dirichlete Processes [R].Sydney: Macquarie University, 2011. |
| [17] | 曹彬,顾怡立,谢珍真,等. 一种基于大数据技术的舆情监控系统[J]. 信息网络安全,2014,(12):32-36. |
| [18] | Neal R M.Markov Chain Sampling Methods for Dirichlet Process Mixture Models[J]. Journal of Computational and Graphical Statistics, 2000, 9(2): 249-265. |
| [19] | 陈晓,赵晶玲. 大数据处理中混合型聚类算法的研究与实现[J]. 信息网络安全,2015,(4):45-49. |
| [20] | Moh'd B A Z, Rawi M. An Efficient Approach for Computing Silhouette Coefficients[J]. Journal of Computer Science, 2008, 4(3): 252-255. |
| [21] | Blei D M, Ng A Y, Jordan M I.Latent Dirichlet Allocation[J]. Journal of Machine Learning Research, 2003, 4(3): 993-1022. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems [J]. Netinfo Security, 2024, 24(7): 1015-1026. |
| [3] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [4] | ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies [J]. Netinfo Security, 2024, 24(7): 1038-1049. |
| [5] | DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism [J]. Netinfo Security, 2024, 24(7): 1050-1061. |
| [6] | ZHOU Shucheng, LI Yang, LI Chuanrong, GUO Lulu, JIA Xinhong, YANG Xinghua. Context-Based Abnormal Root Cause Algorithm [J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| [7] | REN Changyu, ZHANG Ling, JI Hangyuan, YANG Liqun. Research on TTP Extraction Method Based on Pre-Trained Language Model and Chinese-English Threat Intelligence [J]. Netinfo Security, 2024, 24(7): 1076-1087. |
| [8] | CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website [J]. Netinfo Security, 2024, 24(7): 1088-1097. |
| [9] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [10] | SHEN Xiuyu, JI Weifeng. Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security [J]. Netinfo Security, 2024, 24(7): 1110-1121. |
| [11] | ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery [J]. Netinfo Security, 2024, 24(7): 1122-1128. |
| [12] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [13] | LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET [J]. Netinfo Security, 2024, 24(7): 983-992. |
| [14] | LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication [J]. Netinfo Security, 2024, 24(7): 993-1005. |
| [15] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||