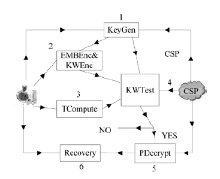
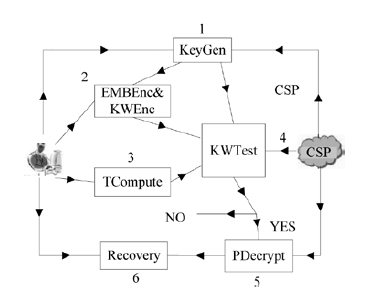
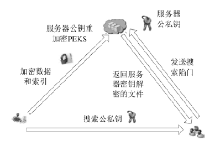
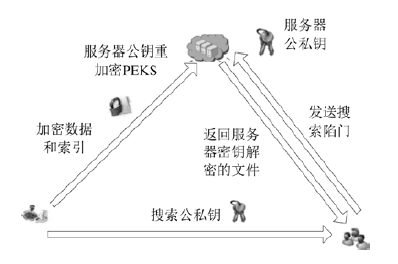
| [1] |
LI J, WANG Q, WANG C, et al.Fuzzy Keyword Search over Encrypted Data in Cloud Computing[J]. Computer Science & Information Systems, 2013, 2009, (2): 1-5.
|
| [2] |
BONEH D, DI CRESCENZO G, OSTROVSKY R, et al.Public Key Encryption with Keyword Search[C]//Advances in Cryptology-Eurocrypt 2004, Springer Berlin Heidelberg, 2004: 506-522.
|
| [3] |
WATERS B R, BALFANZ D, DURFEE G, et al.Building an Encrypted and Searchable Audit Log[C]//The Network and Distributed System Security Symposium, NDSS, California, 2004: 5-6.
|
| [4] |
GOLLE P, STADDON J, WATERS B.Secure conjunctive keyword search over encrypted data[C]// Second International Conference, ACNS, Springer Berlin Heidelberg, 2004: 31-45.
|
| [5] |
PARK D J, KIM K, LEE P J.Public key encryption with conjunctive field keyword search[C]// 5th International Workshop, WISA 2004, Springer Berlin Heidelberg, 2004: 73-86.
|
| [6] |
BONEH D, WATERS B.Conjunctive, subset, and range queries on encrypted data[C]// 4th Theory of Cryptography Conference, TCC 2007, Springer Berlin Heidelberg, 2007: 535-554.
|
| [7] |
ZHANG B, ZHANG F.An efficient public key encryption with conjunctive-subset keywords search[J]. Journal of Network and Computer Applications, 2011, 34(1): 262-267.
|
| [8] |
BAEK J, SAFAVI-NAINI R, SUSILO W.Public Key Encryption with Keyword Search Revisited[C]//Computational Science and Its Applications-ICCSA 2008, Perugia, Italy, 2008: 1249-1259.
|
| [9] |
VALLENT T F, KIM H.A Pairing-Free Public Key Encryption with Keyword Searching for Cloud Storage Services[C]//5th International Conference, AFRICOMM 2013, Springer International Publishing, 2014: 70-78.
|
| [10] |
LIU Q, WANG G, WU J.Secure and privacy preserving keyword searching for cloud storage services[J]. Journal of network and computer applications, 2012, 35(3): 927-933.
|
| [11] |
BYUN J W, RHEE H S, PARK H A, et al.Off-line keyword guessing attacks on recent keyword search schemes over encrypted data[C]//Third VLDB Workshop, SDM 2006, Springer Berlin Heidelberg, 2006: 75-83.
|
| [12] |
YAU W C, HENG S H, GOI B M.Off-line keyword guessing attacks on recent public key encryption with keyword search schemes[C]//5th International Conference, ATC 2008, Springer Berlin Heidelberg, 2008: 100-105.
|
| [13] |
LEVENSTEIN V.Binary Codes Capable of Correcting Spurious Insertions and Deletions Of Ones[J]. Problems of Information Transmission, 1965, 1(1): 8-17.
|
| [14] |
DODIS Y, YAMPOLSKIY A.A verifiable random function with short proofs and keys[C]//8th International Workshop on Theory and Practice in Public Key Cryptography, Switzerland, 2005: 416-431.
|
| [15] |
秦志光,吴世坤,熊虎. 云存储服务中数据完整性审计方案综述[J]. 信息网络安全,2014,(7):1-6.
|
| [16] |
FIAT A, SHAMIR A.How to prove yourself: Practical solutions to identification and signature problems[C]//Advances in Cryptology-Crypto’86, Berlin, Springer-Verlag, 1986: 186-194.
|
| [17] |
BELLARE M, ROGAWAY P.Random oracles are practical: A paradigm for designing efficient protocols[C]//First ACM Conference on Computer and Communications Security, ACM Press, New York, USA, 1993: 62-73.
|