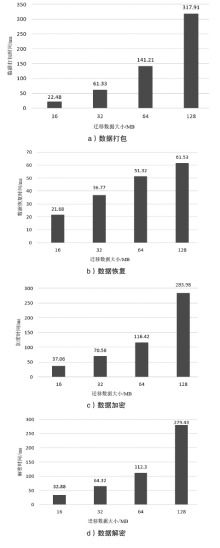
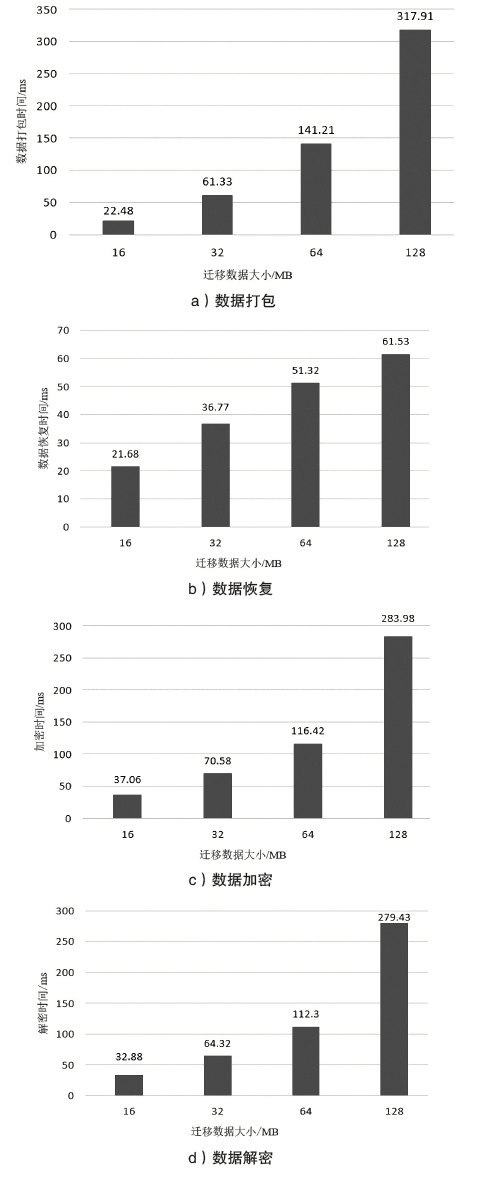
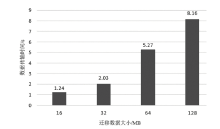
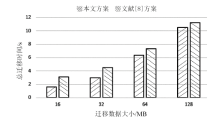
| [1] |
SABT M, ACHEMLAL M, BOUABDALLAH A. Trusted Execution Environment:What It Is, and What It Is Not[C]// IEEE. 2015 IEEE Trustcom/BigDataSE/ISPA. New York: IEEE, 2015: 57-64.
|
| [2] |
SORIENTE C, KARAME G, LI Wenting, et al. Replicatee: Enabling Seamless Replication of SGX Enclaves in the Cloud[C]// IEEE. 2019 IEEE European Symposium on Security and Privacy (EuroS&P). New York:IEEE, 2019: 158-171.
|
| [3] |
OBERHEIDE J, COOKE E, JAHANIAN F. Empirical Exploitation of Live Virtual Machine Migration[EB/OL]. (2008-01-01)[2022-05-13]. https://www.researchgate.net/publication/228752957_Empirical_Exploitation_of_Live_Virtual_Machine_Migration。
|
| [4] |
ANALA M R, SHETTY J, SHOBHA G. A Framework for Secure Live Migration of Virtual Machines[C]// IEEE. 2013 International Conference on Advances in Computing, Communications and Informatics (ICACCI). New York:IEEE, 2013: 243-248.
|
| [5] |
PARK J, PARK S, OH J, et al. Toward Live Migration of SGX-Enabled Virtual Machines[C]// IEEE. 2016 IEEE World Congress on Services. New York: IEEE, 2016: 111-112.
|
| [6] |
ALDER F, KURNIKOV A, PAVERD A, et al. Migrating SGX Enclaves with Persistent State[C]// IEEE. 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks. New York: IEEE, 2018: 195-206.
|
| [7] |
SWAMI Y. SGX Remote Attestation Is Not Sufficient[EB/OL]. (2017-08-01)[2022-05-13]. https://eprint.iacr.org/2017/736.
|
| [8] |
GUERREIRO J, MOURA R, SILVA J N. TEEnder: SGX Enclave Migration Using HSMs[EB/OL]. (2020-06-07)[2022-05-13]. https://www.sciencedirect.com/science/article/pii/S0167404820301474.
|
| [9] |
ABD K, KHALID A, JABER M, et al. Using Energy Efficient Security Technique to Protect Live Virtual Machine Migration in Cloud Computing Infrastructure[J]. Journal of Engineering Science and Technology, 2021, 16(3): 2629-2651.
|
| [10] |
NAGIN K, HADAS D, DUBITZKY Z, et al. Inter-Cloud Mobility of Virtual Machines[C]// ACM. 4th Annual International Conference on Systems and Storage. New York: ACM, 2011: 1-12.
|
| [11] |
PATIL V P, PATIL G A. Migrating Process and Virtual Machine in the Cloud: Load Balancing and Security Perspectives[J]. International Journal of Advanced Computer Science & Information Technology, 2012, 1(1): 11-19.
|
| [12] |
COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2016-08-06)[2022-05-13]. https://eprint.iacr.org/2016/086.pdf. .
|
| [13] |
SHI Yuan, ZHANG Huanguo, ZHAO Bo, et al. Security-Enhanced Live Migration Based on SGX for Virtual Machine[J]. Journal on Communications, 2017, 38(9): 65-75.
doi: 10.11959/j.issn.1000-436x.2017183
|
|
石源, 张焕国, 赵波, 等. 基于SGX的虚拟机动态迁移安全增强方法[J]. 通信学报, 2017, 38(9): 65-75.
doi: 10.11959/j.issn.1000-436x.2017183
|
| [14] |
GB/T 32918. 3-2016 Information Security Technology SM2 Elliptic Curve Public Key Cryptographic Algorithm Part 3: Key Exchange Protocol[S]. Beijing: Standards Press of China, 2016.
|
|
GB/T 32918. 3-2016 信息安全技术SM2椭圆曲线公钥密码算法3部分:密钥交换协议[S]. 北京: 中国标准出版社, 2016.
|
| [15] |
ZHANG Jian, WANG Wenxu, GONG Liangyi, et al. CloudI: Cloud Security Based on Cloud Introspection[C]// ACM. 2018 10th International Conference on Machine Learning and Computing. New York: ACM, 2018: 341-346.
|
| [16] |
GU Jinyu, HUA Zhichao, XIA Yubin, et al. Secure Live Migration of SGX Enclaves on Untrusted Cloud[C]// IEEE. 2017 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York: IEEE, 2017: 225-236.
|
| [17] |
HOU Jie, XUE Liang, WANG Yang. Trusted Migration Method for Virtual Machine Based on Trusted Chain[J]. Command Control and Simulation, 2019, 41(6): 120-124.
doi: 10.3969/j.issn.1673-3819.2019.06.022
|
|
侯婕, 薛亮, 王阳. 基于可信链的虚拟机可信迁移方法[J]. 指挥控制与仿真, 2019, 41(6):120-124.
doi: 10.3969/j.issn.1673-3819.2019.06.022
|
| [18] |
YU Zhilou. Cloud Security Based on Server Simulated Trusted Platform Module[D]. Nanjing: Southeast University, 2019.
|
|
于治楼. 基于服务器虚拟可信计算平台模块的云安全研究[D]. 南京: 东南大学, 2019.
|
 ), GUO Kaiyuan1,2, TU Hang1,2
), GUO Kaiyuan1,2, TU Hang1,2