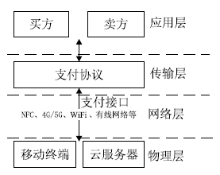
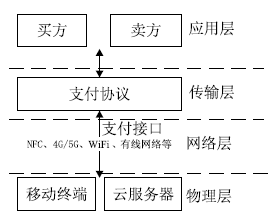
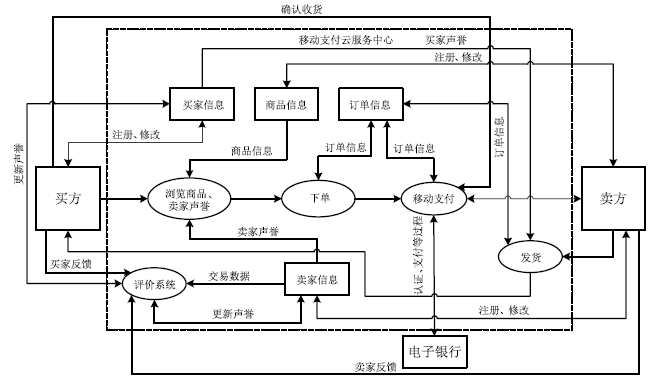
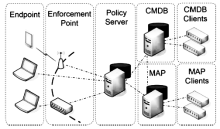
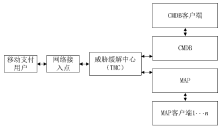
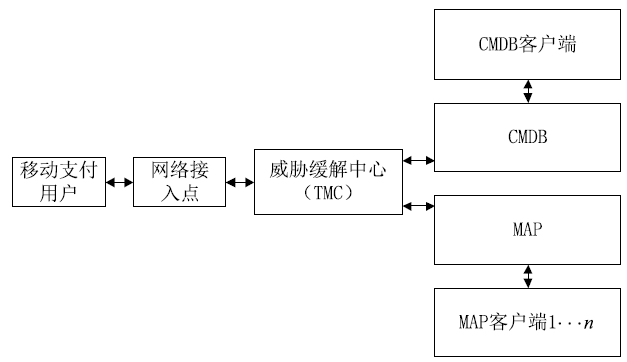
| [1] |
SUN Jing, CHI Ting, Law R.Investigating the Adoption of Apparel M-commerce in the US Market[J]. International Journal of Clothing Science and Technology, 2019, 31(4): 544-563.
|
| [2] |
CHUN S H.E-Commerce Liability and Security Breaches in Mobile Payment for e-Business Sustainability[J]. Sustainability, 2019, 11(3): 715
|
| [3] |
AGHILI S F, MALA H, Security Analysis of An Ultra-lightweight RFID Authentication Protocol for M-commerce[J]. International Journal of Communication Systems, 2019, 32(3): 37-38
|
| [4] |
YANG Wenbo, LI Juanru, ZHANG Yuanyuan, et al. Security Analysis of Third-party in App Payment in Mobile Applications[EB/OL]. , 2019-4-15.
|
| [5] |
OBAID M, BAYRAM Z, SALEH M. Instant Secure Mobile Payment Scheme[EB/OL]. , 2019-4-15.
|
| [6] |
SONG Bo, YAN Wei, ZHANG Tianjiao.Cross-border E-commerce Commodity Risk Assessment Using Text Mining and Fuzzy Rule-based reasoning[J]. Advanced Engineering Informatics, 2019, 40(5): 69-80.
|
| [7] |
ZHANG Xinmin, ZHAO Xumin, WU Na.Credit Risk Assessment Model for Cross-border E-commerce in a BP Neural Network Based on PSO-GA[J]. Agro Food Industry Hi-Tech, 2017, 28(1): 411-414.
|
| [8] |
ZHUANG Zhengyun, LIN Changching, CHEN Chihyung, et al. Rank-Based Comparative Research Flow Benchmarking the Effectiveness of AHP-GTMA on Aiding Decisions of Shredder Selection by Reference to AHP-TOPSIS[EB/OL]. , 2019-4-15.
|
| [9] |
ZHANG Yajuan, DENG Xinyang, WEI Daijun, et al.Assessment of E-Commerce Security Using AHP and Evidential Reasoning[J]. Expert Systems with Applications, 2012, 39(3): 3611-3623.
|
| [10] |
KAROUI Kamel.Security Novel Risk Assessment Framework Based on Reversible Metrics: A Case Study of DDoS Attacks on An E-commerce Web Server[J]. International Journal of Network Management, 2016, 26(6): 553-578.
|
| [11] |
DAI Yue, VIKEN G, JOO E, et al.Risk Assessment in E-commerce: How Sellers’ Photos, Reputation Scores, and the Stake of Atransaction in Fluence Buyers’ Purchase Behavior and Information Processing[J]. Computers in Human Behavior, 2018, 84(5): 342-351.
|
| [12] |
ADAM Shostack.Threat Modeling Designing for Security[M]. Beijng: China Machine Press, 2015.
|
|
亚当·斯塔克.威胁建模设计和交付更安全的软件[M].北京:机械工业出版社,2015.
|
| [13] |
Trusted Computing Group. TCG Guidance for TPM 2.0 Mobile Implementations[EB/OL]. , 2019-4-15.
|
| [14] |
Cloud Security Alliance. The Treacherous 12-Top Threats to Cloud Computing[EB/OL]. , 2019-4-15.
|
| [15] |
XU Junfeng, WU Shizhong, ZHANG Li.Survey on Attack and Defense Technologies of Android Software Security[J]. Transactions of Beijing Institute of Technology, 2017, 37(2): 163-167.
|
|
徐君锋,吴世忠,张利. Android软件安全攻防对抗技术及发展[J]. 北京理工大学学报,2017,37(2):163-167.
|
| [16] |
BARROWCLOUGH J P, ASIF R. Securing Cloud Hypervisors: A Survey of the Threats, Vulnerabilities, and Countermeasures[EB/OL]. , 2019-4-15.
|
| [17] |
JU Pinghua, HUANG Guangquan, XIAO Liming, et al.Optimization Method of Assembly Sequence Based on Multi-objective Fuzzy Comprehensive Evaluation[J]. Journal of Harbin Institute of Technology, 2018, 50(7): 154-163.
|
|
鞠萍华,黄广全,肖莉明,等.多目标模糊综合评价的装配序列优选方法[J]. 哈尔滨工业大学学报,2018,50(7):154-163.
|
| [18] |
WANG Shuang, LI Zhiping, XIN Qian, et al.Overall Safety Assessment of Fuzzy Comprehensive Evaluation Method[J]. Modern Electronics Technique, 2019, 42(11): 82-86.
|
|
王双,李志平,辛倩,等.模糊综合评价法的整体安全评估[J]. 现代电子技术,2019,42(11):82-86.
|
| [19] |
Trusted Computing Group. TCG Trusted Network Communications TNC Architecture for Interoperability Specification Version 2.0[EB/OL]. , 2019-4-15.
|
| [20] |
ZHAO Bo, XIANG Cheng, ZHANG Huanguo.A Trusted Network Connect Protocol for Resisting Man-in-the-Middle Attack[J]. Chinese Journal of Computers, 2019, 42(5): 1137-1148.
|
|
赵波,向程,张焕国.一种抵御中间人攻击的可信网络连接协议[J]. 计算机学报,2019,42(5):1137-1148.
|
 ), JIN Zhigang1, HAO KUN2, ZHANG Weilong3
), JIN Zhigang1, HAO KUN2, ZHANG Weilong3