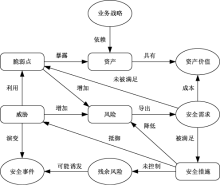
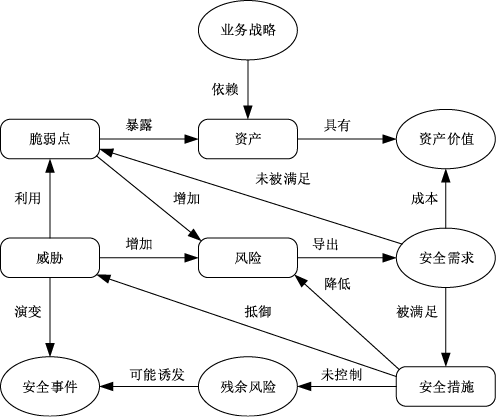
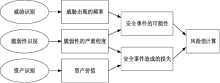
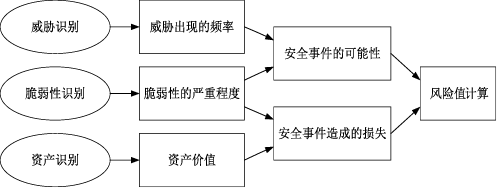
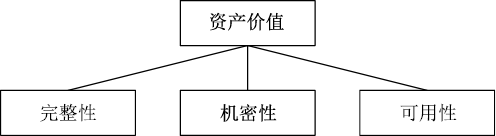
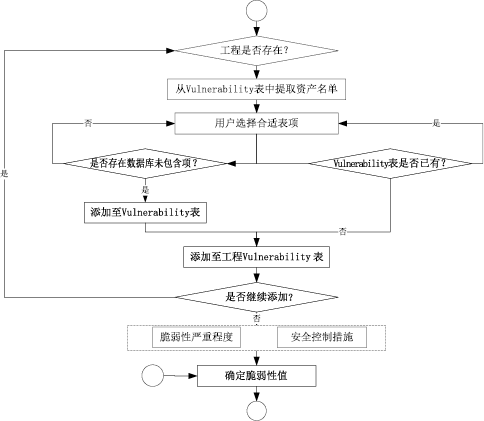
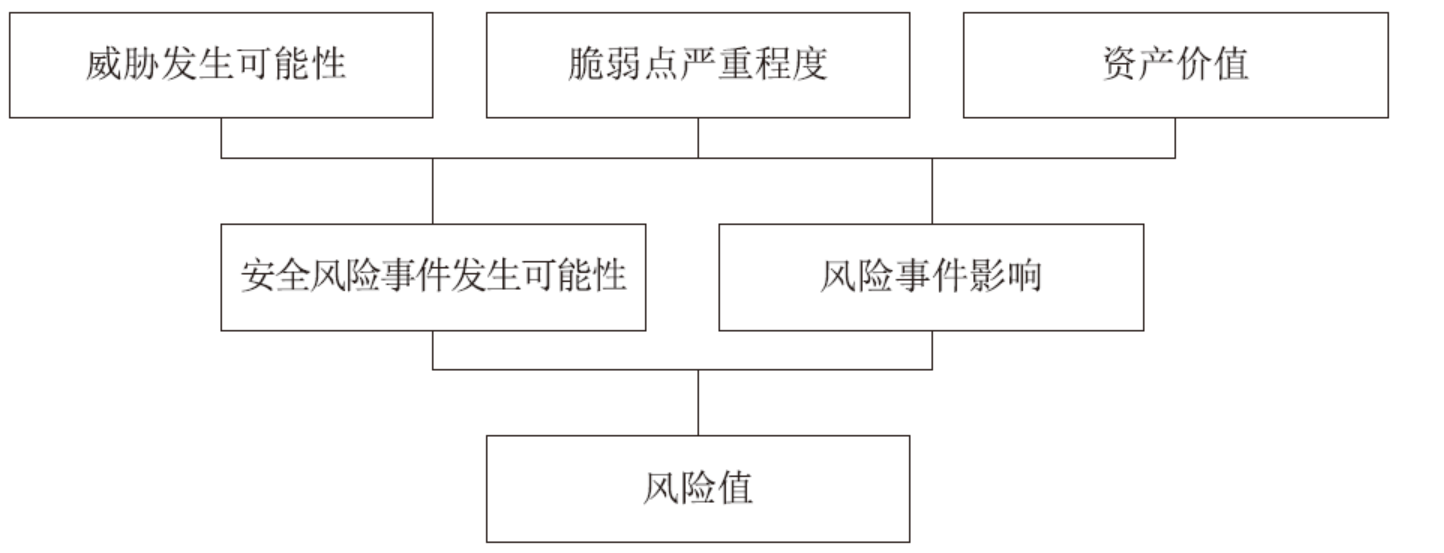
| [1] |
杨继华. 信息安全风险评估模型及方法研究[D].西安:西安电子科技大学,2007.
|
| [2] |
刘莹,顾卫东.信息安全风险评估研究综述[J].青岛大学学报. 2008,23(2):37-43.
|
| [3] |
Common Criteria for Information Technology Security Evaluation[S]. ISO/IEC 15408: 1999.
|
| [4] |
范红,冯登国,吴亚非.信息安全风险评估方法与应用[M]. 北京:清华大学出版社,2006.
|
| [5] |
GB/T20984-2007.信息安全风险管理规范[S].
|
| [6] |
GB/Z 24364-2009.信息安全风险管理指南[S].
|
| [7] |
岳芳. 网络安全的标准与组织[J].网络安全技术与应用,2004,(5):74-75.
|
| [8] |
聂晓伟,张玉清,杨鼎才,等.一个基于BS7799标准的风险分析方法[C]//中国计算机安全学会2004年会论文集,2004:67-69.
|
| [9] |
李杨,聂晓伟,杨鼎才. 基于BS7799标准风险评估实施性研究[J].计算机应用研究,2005,22(7):42-44, 62.
|
| [10] |
陈光,匡兴华.信息系统安全风险评估研究[J].网络安全技术与应用,2004,(7):62-64.
|
| [11] |
高建新,舒首衡,伭剑辉,等.大型活动信息系统网络安全监控研究[J].信息网络安全. 2010.(1):41-43.
|
| [12] |
范并思. 20世纪西方与中国的图书馆学——基于德尔斐法测评的理论史纲[M].北京:北京图书馆出版社,2004.
|
| [13] |
苏忠,林繁,陈厚金,等.网络安全态势感知系统的构建与应用[J].信息网络安全,2014,(5):73-77.
|
| [14] |
孙鹏鹏, 张玉清, 韩臻. 信息安全风险评估工具的设计与实现[J] . 计算机工程与应用, 2007 , 43(9) : 95-98.
|
| [15] |
卫成业. 信息安全风险评估模型[J].网络安全技术与应用,2002,(4):10-15.
|
| [16] |
李平安. 信息网络安全及风险防范措施分析[J].信息网络安全,2013,(7):15-17.
|
| [17] |
Zhang Y Z, Fang B X, Chi Y, et al.Research on network node correlation in network risk assessment[J]. Chinese Journal of Computers, 2007, 30(2): 234-240.
|
| [18] |
Zhang Y Z, Fang B X, Chi Y, et al.Risk propagation model for assessing network information systems[J]. Journal of Software, 2007,18(1):137-145.
|
| [19] |
Mohammad Salim Ahmed, Ehab Al-Shaer, Mohamed Taibah, et al.Objective risk evaluation for automated security management[J]. Journal of Network and Systems Management, Sep. 2011, (19):343-366.
|
| [20] |
Lu Jiayuan.Research on network system risk assessment using risk transmission[C]// Internet Technology and Applications, 2010 International Conference on.Wuhan, 2010:1-5.
|
| [21] |
Chen T P, Qiao X D, Zheng L Q, et al.Application of graph theory in treat situation analysis of network security[J]. Journal of Beijing university of posts and telecommunications, 2009, 32(1):113-117.
|
| [22] |
Young-Gab Kim, Dongwon Jeong, Soo-Hyun Park, et al.Simulation of risk propagation model in information systems[C] // Computational Intelligence and Security,Guangzhou, 2006, (2):1555-1558.
|
 ), GUO Rong-hua2, MENG Zheng1, BAI Xiao1
), GUO Rong-hua2, MENG Zheng1, BAI Xiao1