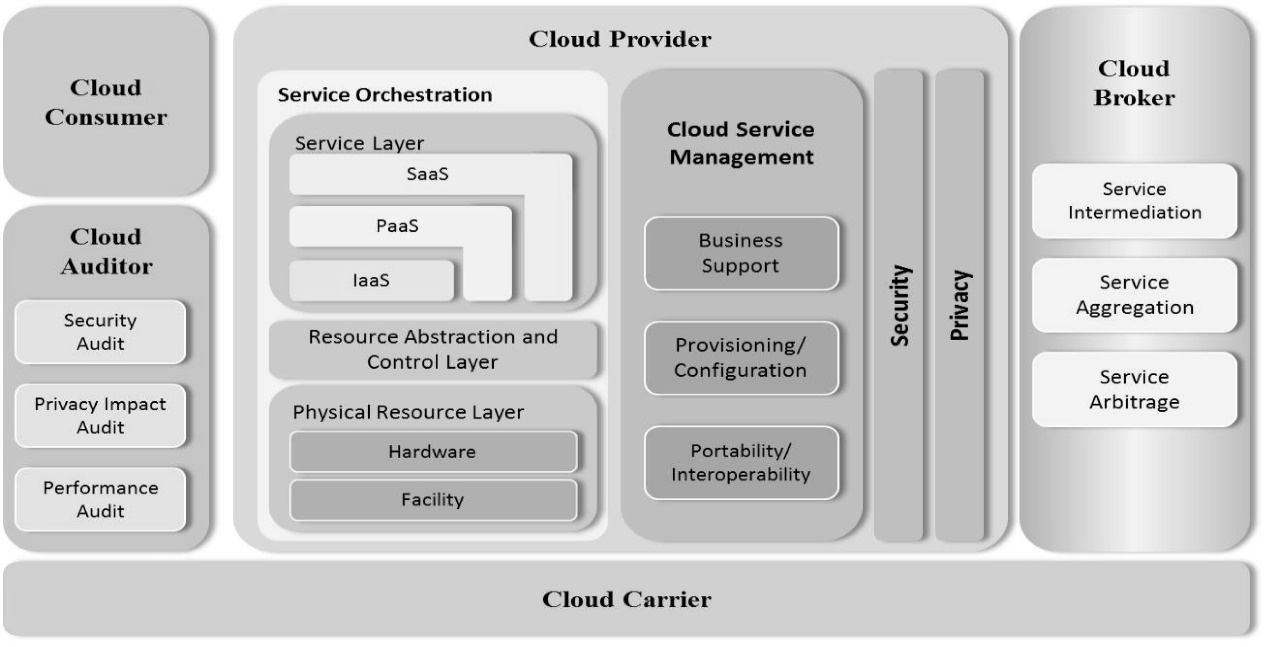
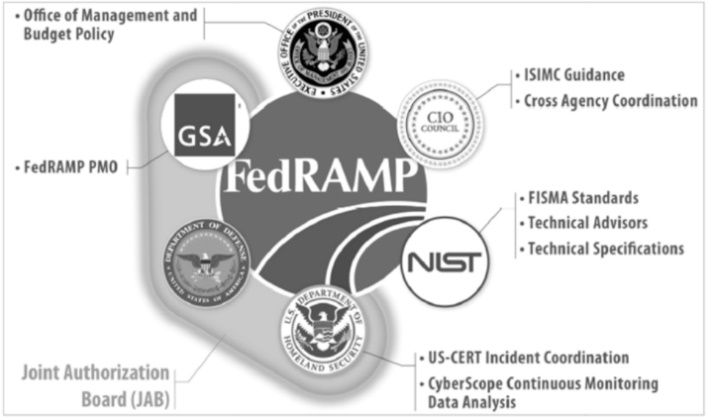
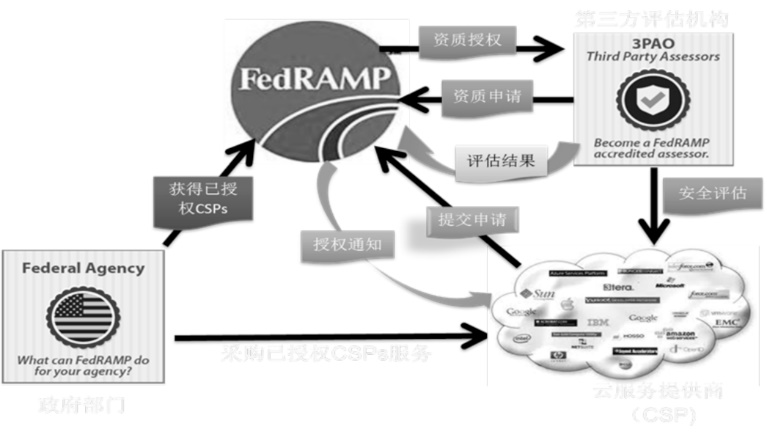
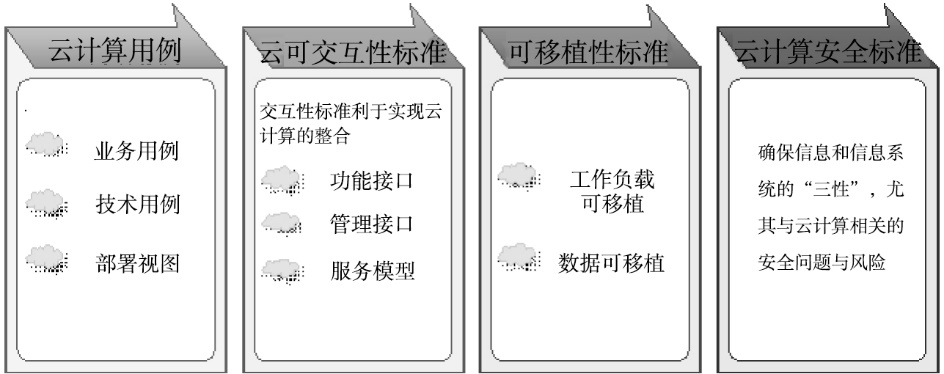
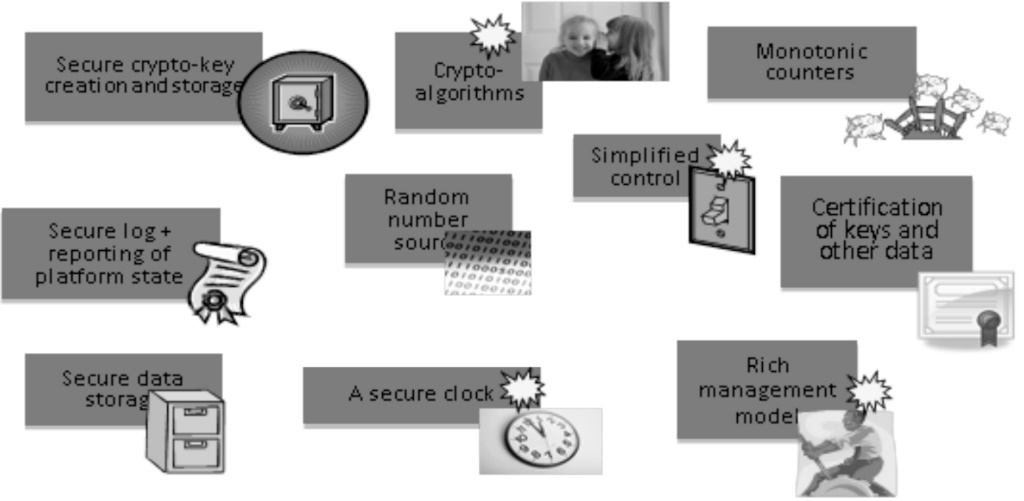
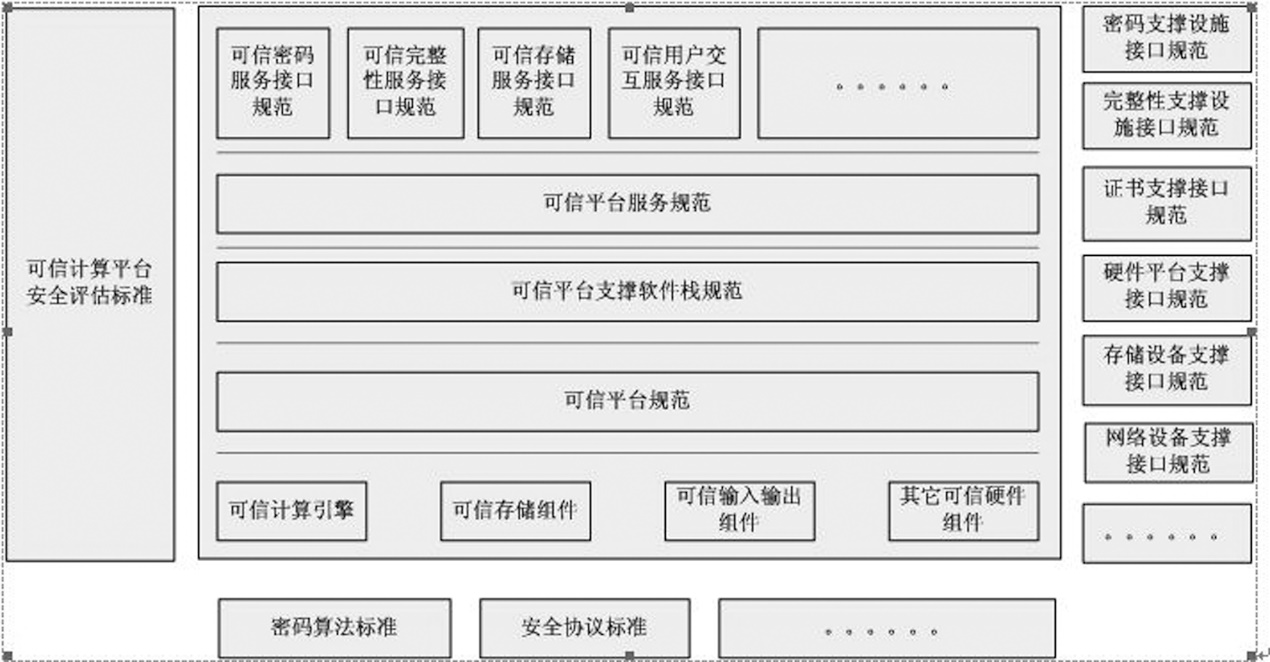
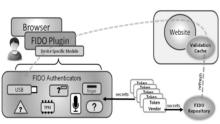
| [1] |
Protecting Whistleblowers with Access to Classified Information[EB/OL]. .
|
| [2] |
Presidential Policy Directive[EB/OL]. , 2015-01-28.
|
| [3] |
IMPROVING CRITICAL INFRASTRUCTURE CYBERSECURITY[EB/OL]., 2013-02-12.
|
| [4] |
Critical Infrastructure Security and Resilience[EB/OL]., 2015-01-28.
|
| [5] |
Signals Intelligence Activities[EB/OL]. , 2014-01-17.
|
| [6] |
Framework for Improving Critical Infrastructure Cybersecurity[EB/OL]. , 2014-02-12.
|
| [7] |
NATIONAL CYBER SECURITY FRAMEWORK MANUAL[EB/OL]. , 2015-01-28.
|
| [8] |
世界互联网大会—乌镇峰会[EB/OL]. , 2014-11-19.
|
| [9] |
Windows[EB/OL]. , 2015-01-28.
|
| [10] |
What is Data Execution Prevention?[EB/OL]. , 2015-01-28.
|
| [11] |
Windows ISV Software Security Defenses[EB/OL]. , 2015-01-28.
|
| [12] |
ZHANG Q, CHENG L, BOUTABA R.Cloud computing: state-of-the-art and research challenges[J]. Journal of Internet Services and Applications, 2010, 1(1): 7-18.
|
| [13] |
The NIST Definition of Cloud Computing[EB/OL]. , 2011-09.
|
| [14] |
Gartner. Seven cloud-computing security risks[EB/OL]. , 2015-01-28.
|
| [15] |
CSA. Top Threats to Cloud Computing[EB/OL]., 2010-03.
|
| [16] |
Federal Risk and Authorization Management Program[EB/OL]. , 2015-01-30.
|
| [17] |
NIST. NIST Cloud Computing Program[EB/OL]. , 2014-12-16.
|
| [18] |
TPM 2.0[EB/OL]. , 2015-01-28.
|
| [19] |
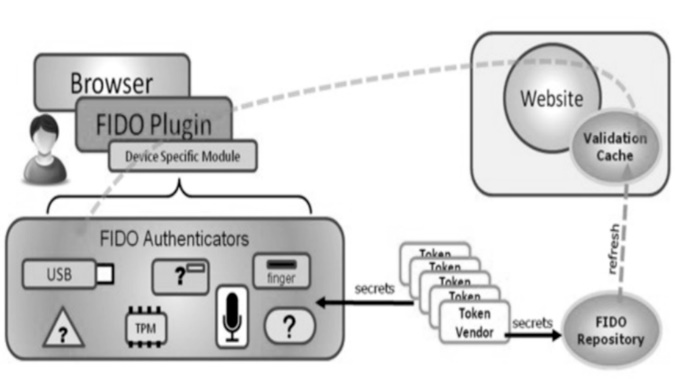
FIDO Alliance[EB/OL]. , 2015-01-28.
|