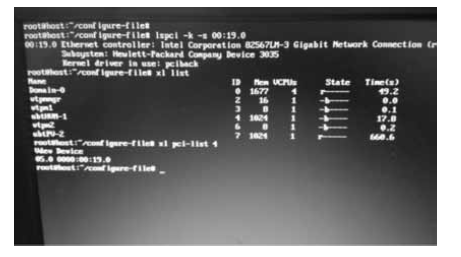
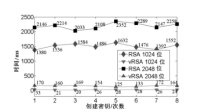
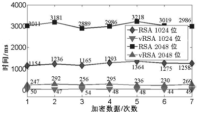
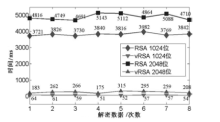
Netinfo Security ›› 2015, Vol. 15 ›› Issue (11): 7-8.doi: 10.3969/j.issn.1671-1122.2015.11.002
Previous Articles Next Articles
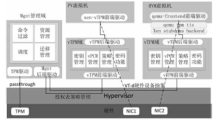
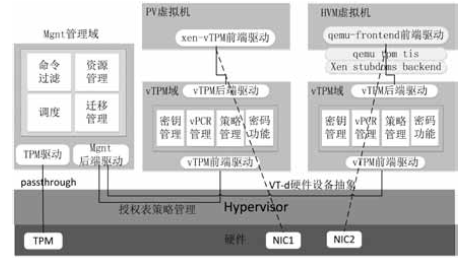
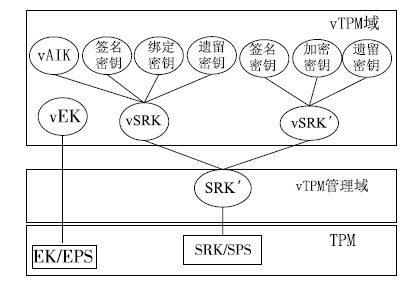
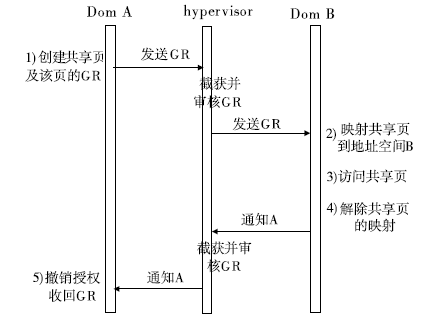
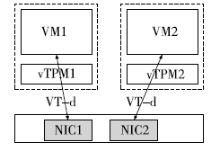
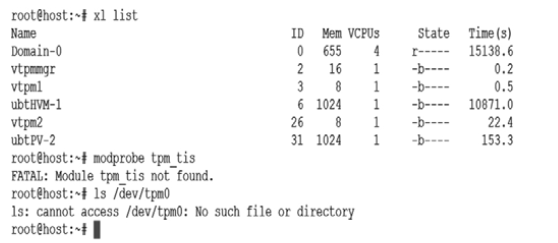
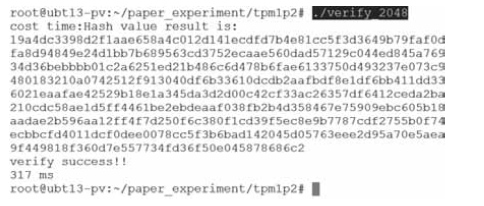
Research on VT-d based Virtual Machine Isolation Framework
YANG Yong-jiao1, YAN Fei2,3, YU Zhao2,3, ZHANG Huan-guo2,3
- 1. Guangdong Power Grid Co., Ltd., Information Center, Guangzhou Guangdong 510080, China
2.School of Computer, Wuhan University, Wuhan Hubei 430072, China
3.Key Laboratory of Aerospace Information Security and Trusted Computing Ministry of Education, Wuhan University , Wuhan Hubei 430072, China
-
Received:2015-09-07Online:2015-11-25Published:2015-11-20
CLC Number:
Cite this article
YANG Yong-jiao, YAN Fei, YU Zhao, ZHANG Huan-guo. Research on VT-d based Virtual Machine Isolation Framework[J]. Netinfo Security, 2015, 15(11): 7-8.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2015.11.002
| [1] | 陈刚. 面向云计算的软件可用性机制研究[D]. 武汉:华中科技大学, 2013. |
| [2] | 武越,刘向东. 涉密环境桌面虚拟化多级安全系统设计与实现[J]. 信息网络安全,2014,(9):101-104. |
| [3] | Chen X.Overshadow: a virtualization-based approach to retrofitting protection in commodity operating systems[C]//ACM SIGOPS Operating Systems Review. ACM, 2008, 42(2): 2-13. |
| [4] | Champagne D.Scalable architectural support for trusted software[C]//High Performance Computer Architecture (HPCA), 2010 IEEE 16th International Symposium on. IEEE, 2010: 1-12. |
| [5] | Chhabra S, Rogers B.SecureME: a hardware-software approach to full system security[C]//Proceedings of the international conference on Supercomputing. ACM, 2011: 108-119. |
| [6] | Wang Z.Hypersafe: A lightweight approach to provide lifetime hypervisor control-flow integrity[C]//Security and Privacy (SP), 2010 IEEE Symposium on. IEEE, 2010: 380-395. |
| [7] | Zhang F, Chen J.Cloudvisor: Retrofitting protection of virtual machines in multi-tenant cloud with nested virtualization[C] //Proceedings of the Twenty-Third ACM Symposium on Operating Systems Principles. New York :ACM, 2011: 203-216. |
| [8] | Azab A M, Ning P, Zhang X.Sice: a hardware-level strongly isolated computing environment for x86 multi-core platforms[C]//Proceedings of the 18th ACM conference on Computer and communications security. ACM, 2011: 375-388. |
| [9] | Hua J, Sakurai K.Barrier: a lightweight hypervisor for protecting kernel integrity via memory isolation[C]//Proceedings of the 27th Annual ACM Symposium on Applied Computing. ACM, 2012: 1470-1477. |
| [10] | Pan W, Zhang Y.Improving virtualization security by splitting hypervisor into smaller components[C]//Data and Applications Security and Privacy XXVI. Springer Berlin Heidelberg, 2012: 298-313. |
| [11] | Jin S, Ahn J.Architectural support for secure virtualization under a vulnerable hypervisor[C]//Proceedings of the 44th Annual IEEE/ACM International Symposium on Microarchitecture.ACM, 2011: 272-283. |
| [12] | Silakov D V.Using virtualization to protect application address space inside untrusted environment[J]. Programming and Computer Software, 2012, 38(1): 24-33. |
| [13] | Jayaram Masti R, Marforio C, Capkun S.An architecture for concurrent execution of secure environments in clouds[C]//Proceedings of the 2013 ACM workshop on Cloud computing security workshop. ACM, 2013: 11-22. |
| [14] | Butterworth J.Bios chronomancy: Fixing the core root of trust for measurement[C]//Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security. ACM, 2013: 25-36. |
| [15] | Garfinkel T, Pfaff B, Chow J, et al.Terra: A virtual machine-based platform for trusted computing[C]//ACM SIGOPS Operating Systems Review. ACM, 2003, 37(5): 193-206. |
| [16] | Berger S, Caceres R.VTPM: Virtualizing the Trusted Platform Module[C]//Proceedings of the 15th USENIX Security Symposium, Canada: Vancouver , 2006: 305-320. |
| [17] | Krautheim F J, Phatak D S, Sherman A T.Introducing the trusted virtual environment module: a new mechanism for rooting trust in cloud computing[C]//Trust and Trustworthy Computing. Springer Berlin Heidelberg, 2010: 211-227. |
| [18] | Intel Corporation,Intel.Virtualization Technology for Directed I/O Architecture Specification[R].October 2014. |
| [19] | Gordon A, Amit N, Har'El N, et al. ELI: bare-metal performance for I/O virtualization[J]. ACM SIGARCH Computer Architecture News, 2012, 40(1): 411-422. |
| [20] | Willmann P, Rixner S, Cox A L.Protection Strategies for Direct Access to Virtualized I/O Devices[C]//USENIX Annual Technical Conference. 2008: 15-28. |
| [21] | Malka M, Amit N, Ben-Yehuda M, et al.rIOMMU: Efficient IOMMU for I/O devices that employ ring buffers[C]//Proceedings of the Twentieth International Conference on Architectural Support for Programming Languages and Operating Systems. ACM, 2015: 355-368. |
| [22] | 李海威,范博,李文锋. 一种可信虚拟平台构建方法的研究和改进[J]. 信息网络安全,2015,(1):1-5. |
| [23] | Software Freedom Conservancy.Qemu Source[EB/OL].. |
| [24] | Xen community.Xen Security Modules,XEN[EB/OL].. |
| [25] | 黄强,张德华,汪伦伟. 可信计算硬件设备虚拟化关键保障机制研究[J]. 信息网络安全,2015,(9):70-73. |
| [26] | Xen community.Xen Source[EB/OL].. |
| [27] | Trust Computing Group.TCG Software Stack(TSS) Specification[R].Version 1.2 ,March 7. |
| [1] | YANG Zhipeng, WANG Juan, MA Chenjun, KANG Yunfeng. Python Sandbox Escape Defense Mechanism Based on Third-Party Library Isolation [J]. Netinfo Security, 2024, 24(5): 682-693. |
| [2] | WANG Wei, HU Yongtao, LIU Qingtao, WANG Kailun. Research on Softwaization Techniques for ERT Trusted Root Entity in Railway Operation Environment [J]. Netinfo Security, 2024, 24(5): 794-801. |
| [3] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [4] | QIN Zhongyuan, GE Zhenwei, PAN Jingwei, CHEN Liquan. Research on Integrity Measurement Scheme Based on Virtual Trusted Platform Module [J]. Netinfo Security, 2023, 23(2): 11-18. |
| [5] | XING Lingkai, ZHANG Jian. Research and Implementation on Abnormal Behavior Detection Technology of Virtualization Platform Based on HPC [J]. Netinfo Security, 2023, 23(10): 64-69. |
| [6] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [7] | LIN Faxin, ZHANG Jian. Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform [J]. Netinfo Security, 2022, 22(11): 62-67. |
| [8] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [9] | BIAN Manlin, WANG Liming. Analysis and Research on Vulnerability of Docker Container Isolation in Cloud Environment [J]. Netinfo Security, 2020, 20(7): 85-95. |
| [10] | RAN Jinpeng, WANG Xiang, ZHAO Shanghong, GAO Hanghang. Virtual SDN Network Embedding Algorithm Based on Fruit Fly Optimization [J]. Netinfo Security, 2020, 20(6): 65-74. |
| [11] | CHEN Lu, SUN Yajie, ZHANG Liqiang, CHEN Yun. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [12] | WANG Xiao, ZHAO Jun, ZHANG Jianbiao. Research on Dynamic Monitoring Mechanism for Virtual Machine Based on Trusted Software Base [J]. Netinfo Security, 2020, 20(2): 7-13. |
| [13] | FAN Bo, GONG Gangjun, SUN Shuxian. Research on Dynamic Security System of Distribution IoT Based on Classified Protection of Cybersecurity 2.0 [J]. Netinfo Security, 2020, 20(11): 10-14. |
| [14] | BAI Jiameng, KOU Yingshuai, LIU Zeyi, ZHA Daren. Docker-based RBAC Task Management System [J]. Netinfo Security, 2020, 20(1): 75-82. |
| [15] | WU Hongsheng. Intelligent Government System Based on Trusted Computing and UEBA [J]. Netinfo Security, 2020, 20(1): 89-93. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||