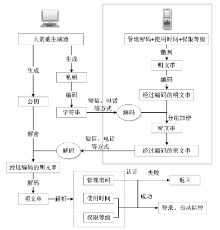
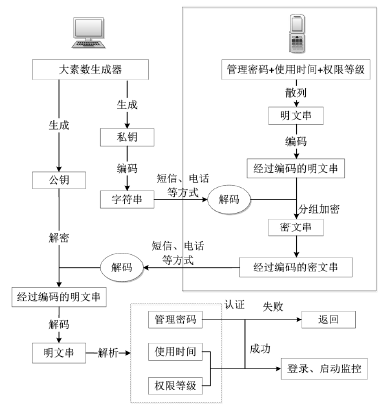
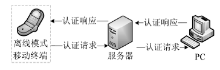
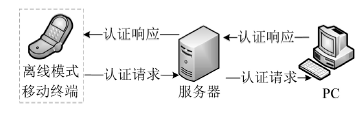
| [1] |
HARN L.A public-key based dynamic password scheme[C]//Proc. Symp. Applied Computing.USA,1991: 430-435.
|
| [2] |
CHEN C Y, GUN C Y, LIN H F.A fair and dynamic password authentication system[C]//AIMSEC, 2011 2nd International Conference on. Deng Leng, 2011: 4505-4509.
|
| [3] |
LIAO I E, LEE C C, HWANG M S.A password authentication scheme over insecure networks[J]. Journal of Computer and System Sciences, 2006, 72(4): 727-740.
|
| [4] |
DIFFIE W, HELLMAN M E.New directions in cryptography[J]. Information Theory, IEEE Transactions, 1976, 22(6): 644-654.
|
| [5] |
HAN D, ZHANG Q, LI J.The Dynamic key and implementation of Rijndael algorithm[C]//2011 International Conference on Multimedia Technology. 2011:5610-5613.
|
| [6] |
CHANG C C, TSU S M, CHEN C Y.Remote scheme for password authentication based on theory of quadratic residues[J]. Computer Communications, 1995,18(12): 936-942.
|
| [7] |
DAS A K, SHARMA P, CHATTERJEE S, et al.A dynamic password-based user authentication scheme for hierarchical wireless sensor networks[J]. Journal of Network and Computer Applications, 2012, 35(5): 1646-1656.
|
| [8] |
TURKANOVIC M, HOLBL M.An Improved Dynamic Password-based User Authentication Scheme for Hierarchical Wireless Sensor Networks[J]. Elektronika ir Elektrotechnika, 2013, 19(6): 109-116.
|
| [9] |
WANG Y, LIU J, XIAO F, et al.A more efficient and secure dynamic ID-based remote user authentication scheme[J]. Computer communications, 2009, 32(4): 583-585.
|
| [10] |
刘智伟,孙其博. 基于权限管理的Android应用行为检测[J]. 信息网络安全,2014,(6):72-77.
|
| [11] |
谢新勤. 基于访问控制列表的权限管理模型研究[J]. 信息网络安全,2011,(5):54-57.
|
 ), YANG Yang1,2, CHENG Jiu-jun1,2, LIAO Jing-xue1,2
), YANG Yang1,2, CHENG Jiu-jun1,2, LIAO Jing-xue1,2