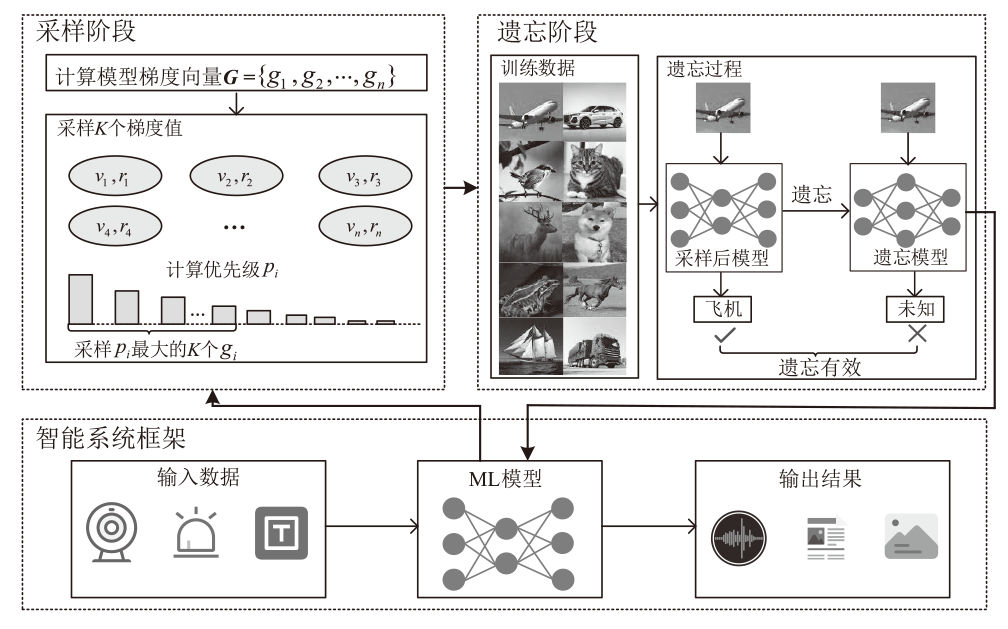
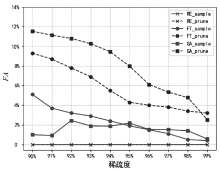
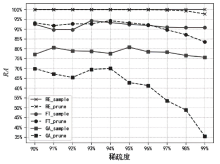
Netinfo Security ›› 2025, Vol. 25 ›› Issue (4): 630-639.doi: 10.3969/j.issn.1671-1122.2025.04.011
Previous Articles Next Articles
Adaptive Sampling-Based Machine Unlearning Method
HE Ke, WANG Jianhua, YU Dan, CHEN Yongle( )
)
- School of Computer Science and Technology, Taiyuan University of Technology, Taiyuan 030024, China
-
Received:2025-01-09Online:2025-04-10Published:2025-04-25
CLC Number:
Cite this article
HE Ke, WANG Jianhua, YU Dan, CHEN Yongle. Adaptive Sampling-Based Machine Unlearning Method[J]. Netinfo Security, 2025, 25(4): 630-639.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.04.011
| [1] | TIAN Zhiyi, CUI Lei, LIANG Jie, et al. A Comprehensive Survey on Poisoning Attacks and Countermeasures in Machine Learning[J]. ACM Computing Surveys, 2023, 55(8): 1-35. |
| [2] | JONAS G, BAUERMEISTER H, DROGE H, et al. Inverting Gradients-How Easy is It to Break Privacy in Federated Learning[J]. Neural Information Processing Systems, 2020, 33: 16937-16947. |
| [3] | ZHAO Wei, REN Xiaoning, XUE Yinxing. Membership Inference Attacks Method Based on Ensemble Learning[J]. Netinfo Security, 2024, 24(8): 1252-1264. |
| 赵伟, 任潇宁, 薛吟兴. 基于集成学习的成员推理攻击方法[J]. 信息网络安全, 2024, 24(8): 1252-1264. | |
| [4] | CHEN Guangke, ZHANG Yedi, SONG Fu. SLMIA-SR: Speaker-Level Membership Inference Attacks against Speaker Recognition Systems[EB/OL]. (2023-11-27)[2024-12-20]. https://arxiv.org/abs/2309.07983. |
| [5] | XIA Hui, QIAN Xiangyun. Invisible Backdoor Attack Based on Feature Space Similarity[J]. Netinfo Security, 2024, 24(8): 1163-1172. |
| 夏辉, 钱祥运. 基于特征空间相似的隐形后门攻击[J]. 信息网络安全, 2024, 24(8): 1163-1172. | |
| [6] | LIU Gaoyang, WU Weiling, ZHANG Jinsheng, et al. Targeted Poisoning Attacks against Multimodal Contrastive Learning[J]. Netinfo Security, 2023, 23(11): 69-83. |
| 刘高扬, 吴伟玲, 张锦升, 等. 多模态对比学习中的靶向投毒攻击[J]. 信息网络安全, 2023, 23(11): 69-83. | |
| [7] | VOIGT P, VON D B A. The EU General Data Protection Regulation (GDPR): A Practical Guide[M]. Heidelberg: Springer, 2024. |
| [8] | PARDAU S L. The California Consumer Privacy ACT: Towards a European-Style Privacy Regime in the United States[EB/OL]. (2018-06-28)[2024-12-20]. https://scholarship.law.ufl.edu/jtlp/vol23/iss1/2/. |
| [9] | WANG Weiqi, TIAN Zhiyi, ZHANG Chenhan, et al. Machine Unlearning: A Comprehensive Survey[EB/OL]. (2024-05-13)[2024-12-20]. https://arxiv.org/abs/2405.07406v2. |
| [10] | CHUNDAWAT V S, TARUN A K, MANDAL M, et al. Zero-Shot Machine Unlearning[J]. IEEE Transactions on Information Forensics and Security, 2023(18): 2345-2354. |
| [11] | CAO Yinzhi, YANG Junfeng. Towards Making Systems Forget with Machine Unlearning[C]// IEEE. 2015 IEEE Symposium on Security and Privacy. New York: IEEE, 2015: 463-480. |
| [12] | BOURTOULE L, CHANDRASEKARAN V, CHOQUETTE-CHOO C A, et al. Machine Unlearning[C]// IEEE. 2021 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2021: 141-159. |
| [13] | WARNECKE A, PIRCH L, WRESSNEGGER C, et al. Machine Unlearning of Features and Labels[EB/OL]. (2021-08-26)[2024-12-20]. https://arxiv.org/abs/2108.11577v4. |
| [14] | THUDI A, DEZA G, CHANDRASEKARAN V, et al. Unrolling SGD: Understanding Factors Influencing Machine Unlearning[C]// IEEE. 2022 IEEE 7th European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2022: 303-319. |
| [15] | BECKER A, LIEBIG T. Evaluating Machine Unlearning via Epistemic Uncertainty[EB/OL]. (2022-09-19)[2024-12-20]. https://arxiv.org/abs/2208.10836v2. |
| [16] | IZZO Z, SMART M A, CHAUDHURI K, et al. Approximate Data Deletion from Machine Learning Models[C]// PMLR. International Conference on Artificial Intelligence and Statistics. New York: PMLR, 2021: 2008-2016. |
| [17] | GRAVES L, NAGISETTY V, GANESH V. Amnesiac Machine Learning[EB/OL]. (2020-10-21)[2024-12-20]. https://doi.org/10.48550/arXiv.2010.10981. |
| [18] | BROPHY J, LOWD D. Machine Unlearning for Random Forests[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2021: 1092-1104. |
| [19] | GINART A, GUAN M Y, VALIANT G, et al. Making AI Forget You: Data Deletion in Machine Learning[J]. Neural Information Processing Systems, 2019, 316: 3518-3531. |
| [20] | MIRZASOLEIMAN B, KARBASI A, KRAUSE A. Deletion-Robust Submodular Maximization: Data Summarization with “ The Right to be Forgotten”[C]// ACM. The 34th International Conference on Machine Learning. New York: ACM, 2017: 2449-2458. |
| [21] | NGUYEN Q P, LOW B K H, JAILLET P. Variational Bayesian Unlearning[J]. Neural Information Processing Systems, 2020, 33: 16025-16036. |
| [22] | GUO Chuan, GOLDSTEIN T, HANNUN A, et al. Certified Data Removal from Machine Learning Models[C]// ACM. Proceedings of the 37th International Conference on Machine Learning (ICML’20). New York: ACM, 2020: 3832-3842. |
| [23] | MAHADEVAN A, MATHIOUDAKIS M. Certifiable Machine Unlearning for Linear Models[EB/OL]. (2021-06-29)[2024-12-20]. https://arxiv.org/abs/2106.15093v3. |
| [24] | SEKHARI A, ACHARYA J, KAMATH G, et al. Remember What You Want to Forget: Algorithms for Machine Unlearning[J]. Neural Information Processing Systems, 2021, 34: 18075-18086. |
| [25] | LIU Jinghan, RAM P, YAO Yuguang, et al. Model Sparsity Can Simplify Machine Unlearning[C]// ACM. Proceedings of the 37th International Conference on Neural Information Processing Systems(NIPS’23). New York: ACM, 2024, 2246: 51584-51605. |
| [26] | TARUN A K, CHUNDAWAT V S, MANDAL M, et al. Fast Yet Effective Machine Unlearning[J]. IEEE Transactions on Neural Networks and Learning Systems, 2024, 35(9): 13046-13055. |
| [27] | GOLATKAR A, ACHILLE A, SOATTO S. Eternal Sunshine of the Spotless Net: Selective Forgetting in Deep Networks[C]// IEEE. 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2020: 9304-9312. |
| [28] | ZHAO Yikai, ZHANG Yinda, LI Yuanpeng, et al. MinMax Sampling: A Near-Optimal Global Summary for Aggregation in the Wide Area[C]// ACM. Proceedings of the 2022 International Conference on Management of Data. New York: ACM, 2022: 744-758. |
| [29] | THUDI A, DEZA G, CHANDRASEKARAN V, et al. Unrolling SGD: Understanding Factors Influencing Machine Unlearning[C]// IEEE. 2022 IEEE 7th European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2022: 303-319. |
| [1] | HU Yuhan, YANG Gao, CAI Hongye, FU Junsong. Privacy Protection of Data Transmission Paths in 3D Distributed Wireless Intelligent Systems [J]. Netinfo Security, 2025, 25(4): 536-549. |
| [2] | LI Jiadong, ZENG Haitao, PENG Li, WANG Xiaoding. An Anonymous Routing Federated Learning Framework for Data Privacy Protection [J]. Netinfo Security, 2025, 25(3): 494-503. |
| [3] | WEN Jinming, LIU Qing, CHEN Jie, WU Yongdong. Research Current Status and Challenges of Fully Homomorphic Cryptography Based on Learning with Errors [J]. Netinfo Security, 2024, 24(9): 1328-1351. |
| [4] | LIN Zhanhang, XIANG Guangli, LI Zhenpeng, XU Ziyi. Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(9): 1375-1385. |
| [5] | FU Yanming, LU Shenglin, CHEN Jiayuan, QIN Hua. Dynamic Task Allocation for Crowd Sensing Based on Deep Reinforcement Learning and Privacy Protection [J]. Netinfo Security, 2024, 24(3): 449-461. |
| [6] | XU Jianfeng, ZHANG Wei, TU Min, WEI Qingting, LAI Zhanqing, WANG Qianqian. A k-Anonymity Completion Method Generated Based on Semantic Fusion Trajectories [J]. Netinfo Security, 2024, 24(12): 1911-1921. |
| [7] | GU Haiyan, LIU Qi, MA Zhuo, ZHU Tao, QIAN Hanwei. Research on Data Noise Addition Method Based on Availability [J]. Netinfo Security, 2024, 24(11): 1731-1738. |
| [8] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [9] | XU Ke, LI Jiayi, JIANG Xinghao, SUN Tanfeng. A Video Gait Privacy Protection Algorithm Based on Sparse Adversarial Attack on Silhouette [J]. Netinfo Security, 2024, 24(1): 48-59. |
| [10] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [11] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [12] | DU Weidong, LI Min, HAN Yiliang, WANG Xu’an. An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique [J]. Netinfo Security, 2023, 23(4): 51-60. |
| [13] | YIN Shu, CHEN Xingshu, ZHU Yi, ZENG Xuemei. Anonymous Domain Name Algorithm Based on Character Space Construction [J]. Netinfo Security, 2023, 23(4): 80-89. |
| [14] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [15] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||