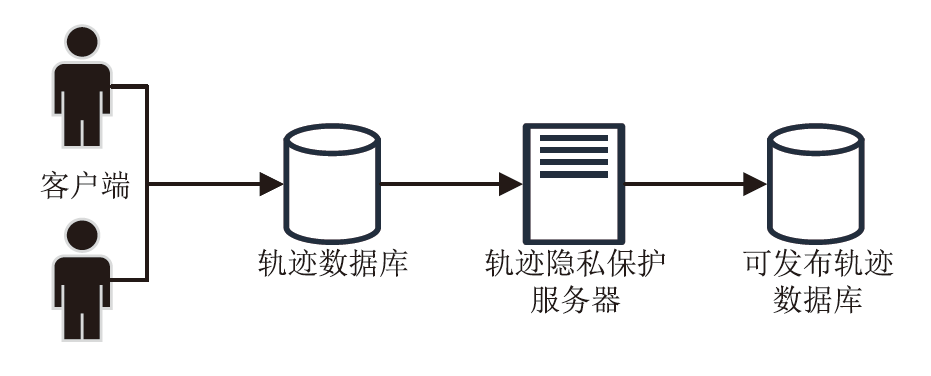
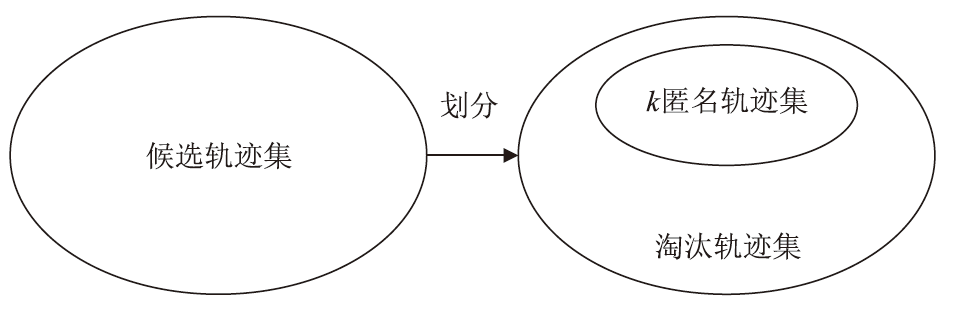
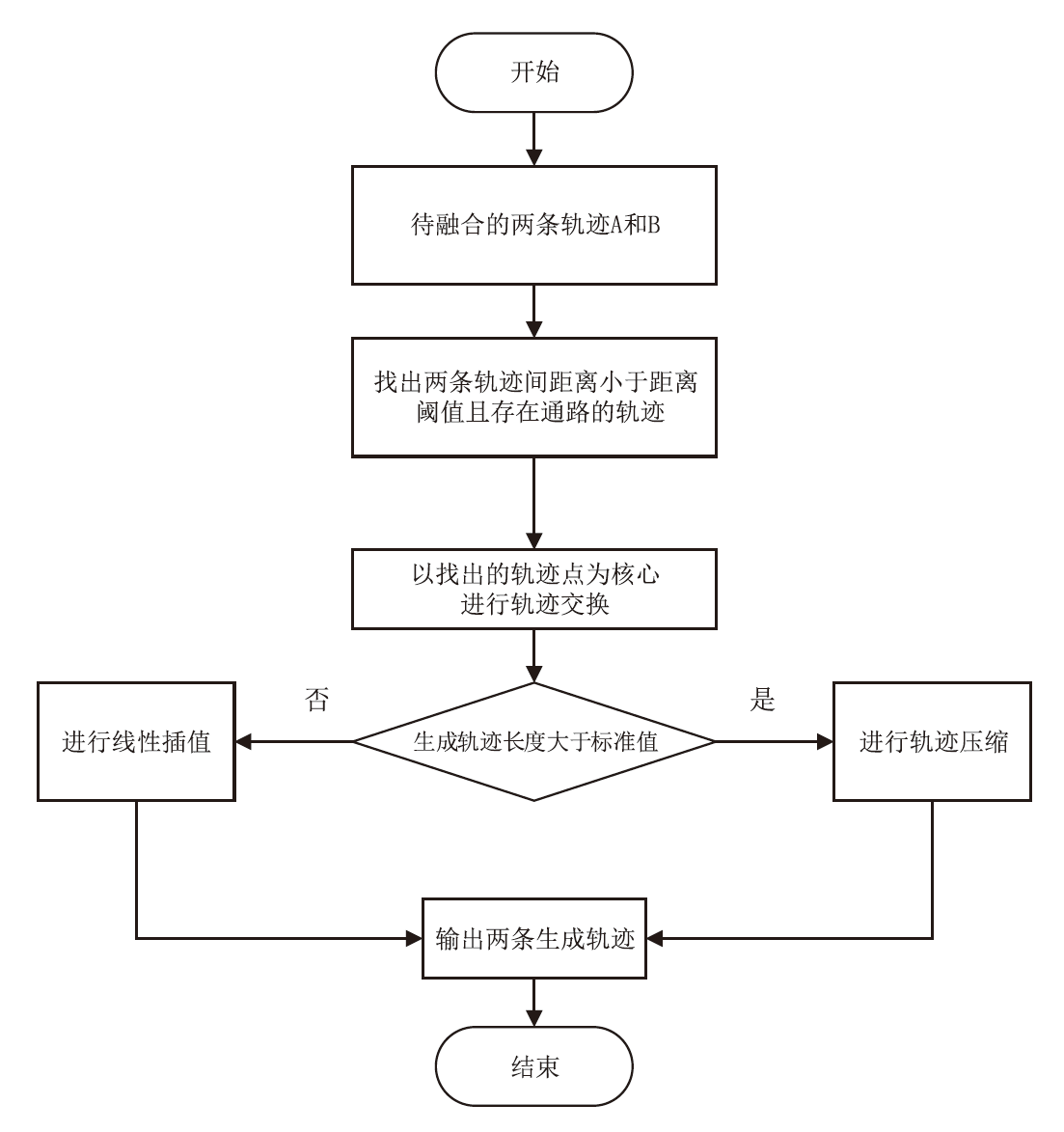
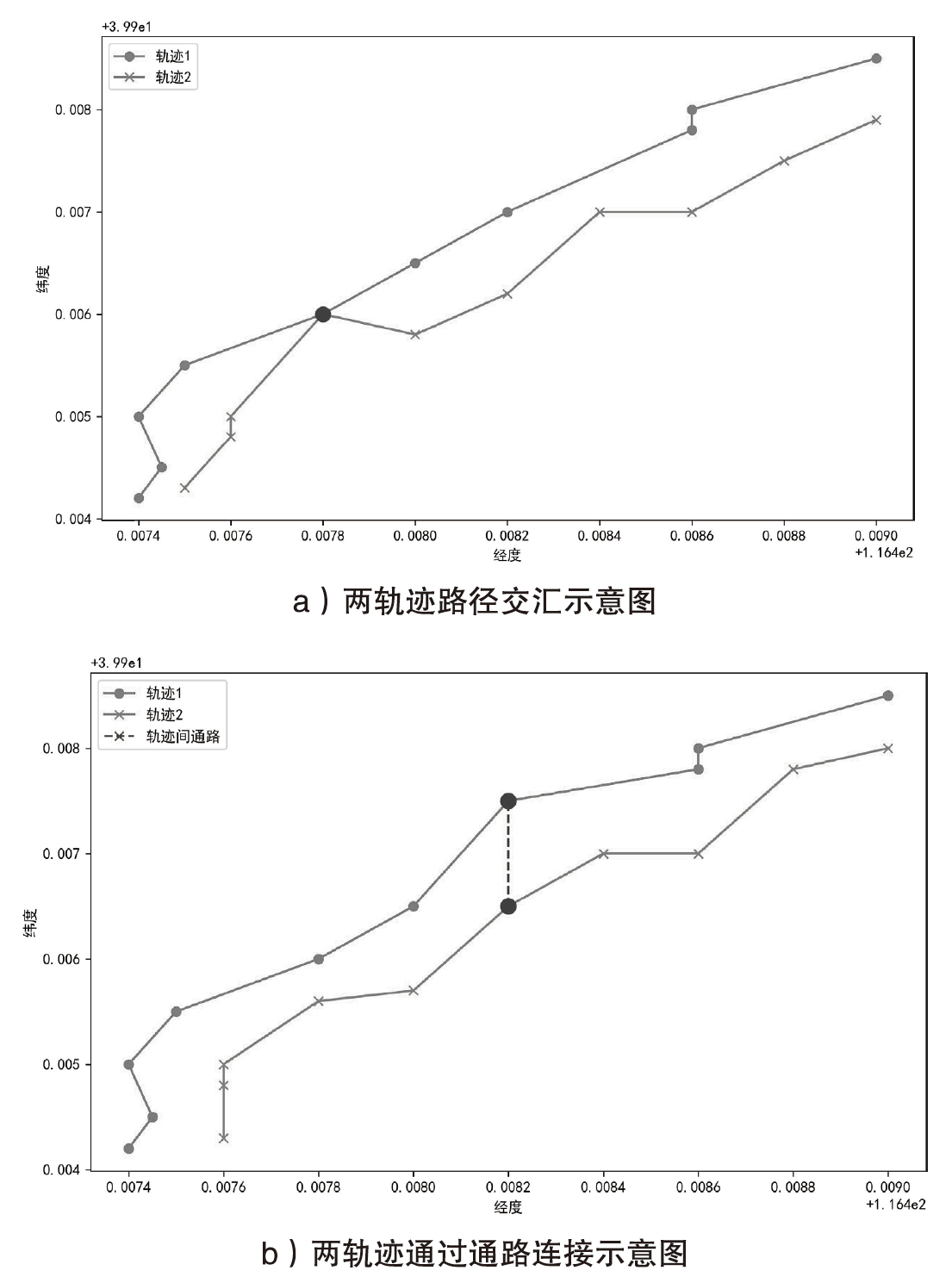
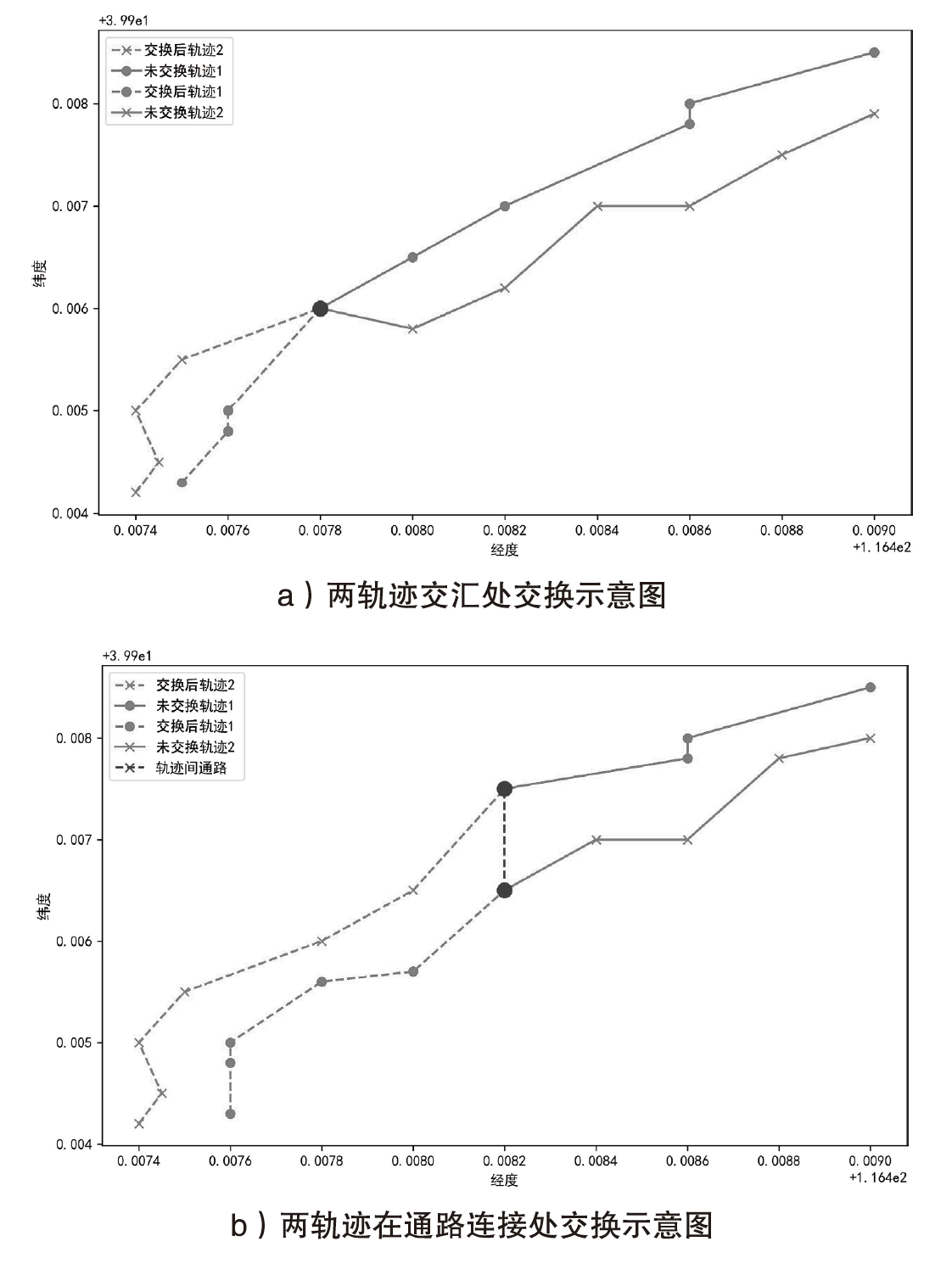
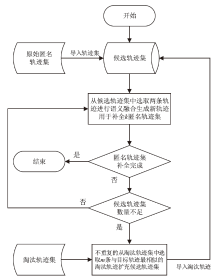
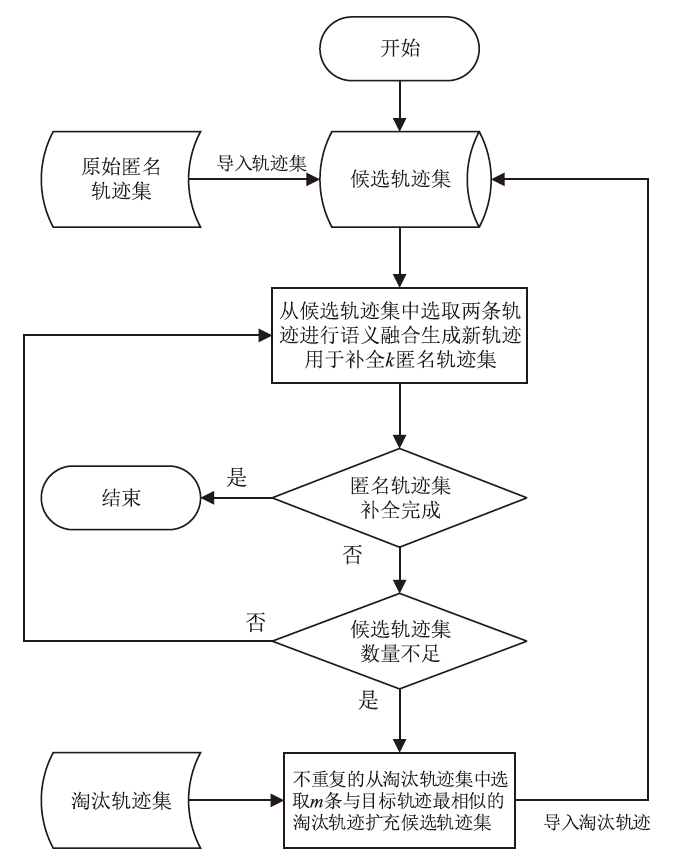
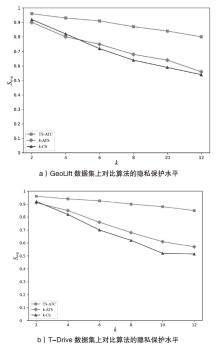
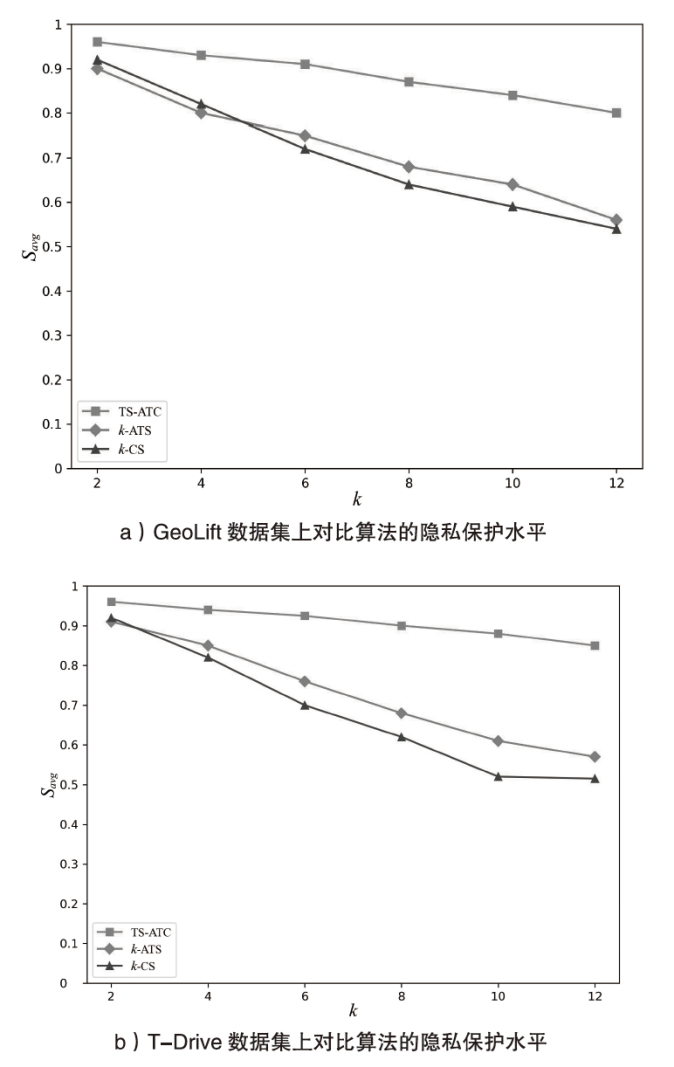
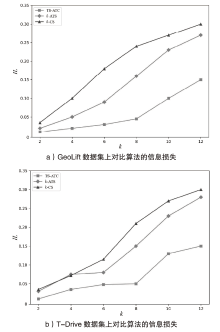
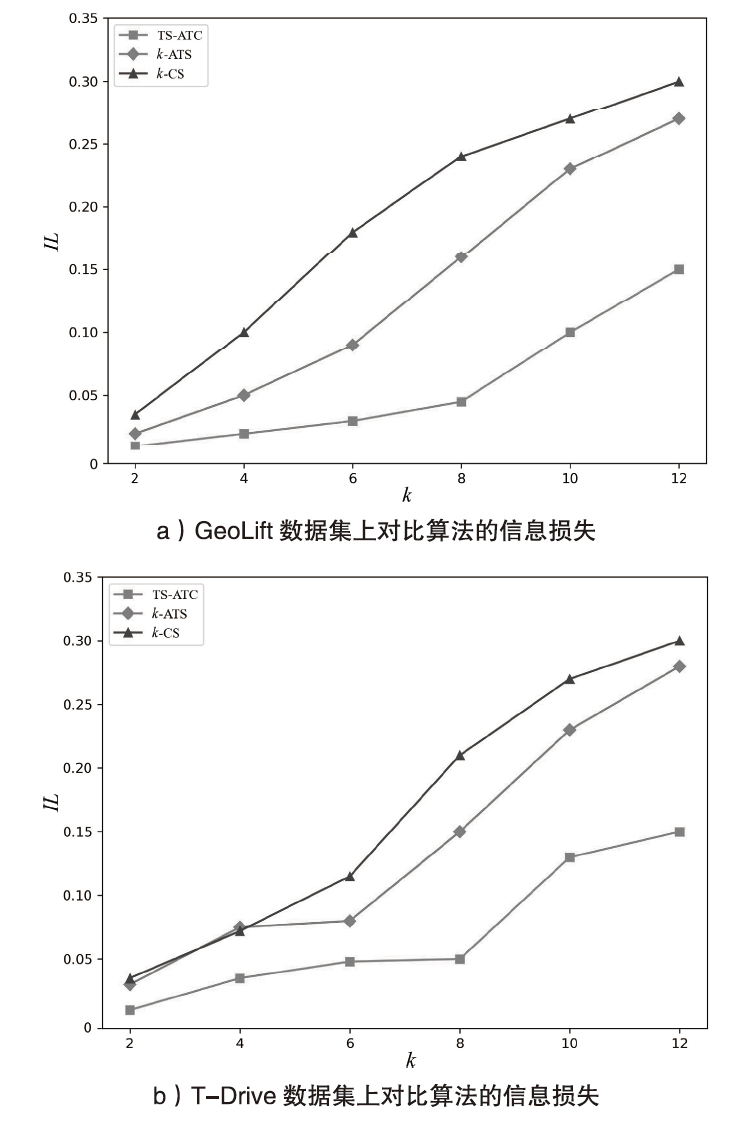
Netinfo Security ›› 2024, Vol. 24 ›› Issue (12): 1911-1921.doi: 10.3969/j.issn.1671-1122.2024.12.009
Previous Articles Next Articles
A k-Anonymity Completion Method Generated Based on Semantic Fusion Trajectories
XU Jianfeng1, ZHANG Wei1, TU Min2,3( ), WEI Qingting1, LAI Zhanqing1, WANG Qianqian1
), WEI Qingting1, LAI Zhanqing1, WANG Qianqian1
- 1. School of Software, Nanchang University, Nanchang 330031, China
2. Jiangxi Police Academy Network Security College, Nanchang 330103, China
3. Key Laboratory of Electronic Data Control and Evidence Collection, Nanchang 330103, China
-
Received:2024-06-11Online:2024-12-10Published:2025-01-10
CLC Number:
Cite this article
XU Jianfeng, ZHANG Wei, TU Min, WEI Qingting, LAI Zhanqing, WANG Qianqian. A k-Anonymity Completion Method Generated Based on Semantic Fusion Trajectories[J]. Netinfo Security, 2024, 24(12): 1911-1921.
share this article
| [1] | MA Chunguang, ZHANG Lei, YANG Songtao. A Review of Research on Location Trajectory Privacy Protection[J]. Netinfo Security, 2015, 15(10): 24-31. |
| 马春光, 张磊, 杨松涛. 位置轨迹隐私保护研究综述[J]. 信息网络安全, 2015, 15(10): 24-31 | |
| [2] | ZHU Lei, WU Shutan, LIU Haoyu, et al. Spatio-Temporal Load Migration Potential of Data Centers: Evaluation and Application[J]. Frontiers in Energy Research, 2023, 11: 1-14. |
| [3] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain[J]. Netinfo Security, 2024, 24(2): 229-238. |
| 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. | |
| [4] | SONG Shuang, WANG Yizhen, CHAUDHURI K. Pufferfish Privacy Mechanisms for Correlated Data[C]// ACM. The 2017 ACM International Conference on Management of Data. New York: ACM, 2017: 1291-1306. |
| [5] |
LIU Yang, WANG Hongsheng, PENG Mugen, et al. DeePGA: A Privacy-Preserving Data Aggregation Game in Crowdsensing via Deep Reinforcement Learning[J]. IEEE Internet of Things Journal, 2020, 7(5): 4113-4127.
doi: 10.1109/JIOT.2019.2957400 |
| [6] | FREUDIGER J, MANSHAEI M H, HUBAUX J P, et al. Non-Cooperative Location Privacy[J]. IEEE Transactions on Dependable and Secure Computing, 2013, 10(2): 84-98. |
| [7] | SUN Yiping, LU Ronxing, LIN Xiaodong, et al. A Secure and Efficient Revocation Scheme for Anonymous Vehicular Communications[C]// IEEE. 2010 IEEE International Conference on Communications. New York: IEEE, 2010: 1-6. |
| [8] | ZHU Xiaoling, LU Yang, ZHANG Benhong, et al. A Distributed Pseudonym Management Scheme in VANETs[EB/OL]. (2023-04-01)[2024-05-30]. https://api.semanticscholar.org/CorpusID:44902238. |
| [9] | SAZDAR M A, GHORASHI A S, MOGHTADAIEE V, et al. A Low-Complexity Trajectory Privacy Preservation Approach for Indoor Fingerprinting Positioning Systems[J]. Journal of Information Security and Applications, 2020, 53: 1-9. |
| [10] | WANG Jiabo, ZHAO Zemao, LI Lin. A Trajectory Privacy Protection Method Based on Fake Trajectories in Location Services[J]. Netinfo Security, 2014, 14(3): 62-67. |
| 王家波, 赵泽茂, 李林. 位置服务中一种基于假轨迹的轨迹隐私保护方法[J]. 信息网络安全, 2014, 14(3): 62-67. | |
| [11] | MA Tinghuai, SONG Fagen. A Trajectory Privacy Protection Method Based on Random Sampling Differential Privacy[J]. ISPRS International Journal of Geo-Information, 2021, 10(7): 1-22. |
| [12] |
WANG Hao, XU Zhengquan, XIONG Lizhi, et al. CLM: Differential Privacy Protection Method for Trajectory Publishing[J]. Journal on Communications, 2017, 38(6): 85-96.
doi: 10.11959/j.issn.1000-436x.2017119 |
|
王豪, 徐正全, 熊礼治, 等. CLM: 面向轨迹发布的差分隐私保护方法[J]. 通信学报, 2017, 38(6):85-96.
doi: 10.11959/j.issn.1000-436x.2017119 |
|
| [13] | GUO Junqi, YANG Minghui, WAN Boxin. A Practical Privacy-Preserving Publishing Mechanism Based on Personalized k-Anonymity and Temporal Differential Privacy for Wearable IoT Applications[J]. Symmetry, 2021, 13(6): 85-96. |
| [14] | YOU T, PENG W, LEE W. Protecting Moving Trajectories with Dummies[C]// IEEE. 2007 International Conference on Mobile Data Management. New York: IEEE, 2007: 278-282. |
| [15] |
LI Fenghua, ZHANG Cui, NIU Ben, et al. Efficient Scheme for User’s Trajectory Privacy[J]. Journal on Communications, 2015, 36(12): 114-123.
doi: 10.11959/j.issn.1000-436x.2015320 |
|
李凤华, 张翠, 牛犇, 等. 高效的轨迹隐私保护方案[J]. 通信学报, 2015, 36(12):114-123.
doi: 10.11959/j.issn.1000-436x.2015320 |
|
| [16] | SWEENEY L. k-Anonymity: A Model for Protecting Privacy[J]. International Journal of Uncertainty, Fuzziness and Knowledge-Based Systems, 2002, 10(5): 557-570. |
| [17] | GRUTESER M, GRUNWALD D. Anonymous Usage of Location-Based Services through Spatial and Temporal Cloaking[C]// ACM. The 1st International Conference on Mobile Systems, Applications and Services. New York: ACM, 2003: 31-42. |
| [18] | ABUL O, BONCHI F, NANNI M. Anonymization of Moving Objects Databases by Clustering and Perturbation[J]. Information Systems, 2010, 35(8): 884-910. |
| [19] |
XU Huajie, WU Qinghua, HU Xiaoming. Privacy Protection Algorithm Based on Multi-Characteristics of Trajectory[J]. Computer Science, 2019, 46(1): 190-195.
doi: 10.11896/j.issn.1002-137X.2019.01.029 |
|
许华杰, 吴青华, 胡小明. 基于轨迹多特性的隐私保护算法[J]. 计算机科学, 2019, 46(1):190-195.
doi: 10.11896/j.issn.1002-137X.2019.01.029 |
|
| [20] | DOMINGO-FERRER J, TRUJILLO-RASUA R. Microaggregation-and Permutation-Based Anonymization of Movement Data[J]. Information Sciences, 2012, 208: 55-80. |
| [21] | HUO Zheng, MENG Xiaofeng, HU Haibo, et al. You Can Walk Alone: Trajectory Privacy-Preserving through Significant Stays Protection[C]// Springer. Lecture Notes in Computer Science. Heidelberg: Springer, 2012: 351-366. |
| [22] | YANG Jing, ZHANG Bing, ZHANG Jianpei, et al. Personalized Trajectory Privacy Preserving Method Based on Graph Partition[J]. Journal on Communications, 2015, 36(3): 5-15. |
| 杨静, 张冰, 张健沛, 等. 基于图划分的个性化轨迹隐私保护方法[J]. 通信学报, 2015, 36(3):5-15. | |
| [23] | WANG Chao, YANG Jing, ZHANG Jianpei. Research on Trajectory Privacy Preserving Method Based on Trajectory Characteristics and Dynamic Proximity[J]. Acta Automatica Sinica, 2015, 41(2): 330-341. |
| 王超, 杨静, 张健沛. 基于轨迹特征及动态邻近性的轨迹匿名方法研究[J]. 自动化学报, 2015, 41(2):330-341. | |
| [24] | HUO Zheng, WANG Teng. A Trajectory Privacy Protection Technology in Road Network Environment[J]. Computer Applications and Software, 2017, 34(7): 308-313. |
| 霍峥, 王腾. 一种路网环境中的轨迹隐私保护技术[J]. 计算机应用与软件, 2017, 34(7): 308-313. | |
| [25] | ZHOU Kexin, WANG Jian. Trajectory Protection Scheme Based on Fog Computing and k-Anonymity in IoT[C]// IEEE. 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS). New York: IEEE, 2019: 1-6. |
| [26] | PAN Xiao, MENG Xiaofeng, XU Jianliang. Distortion-Based Anonymity for Continuous Queries in Location-Based Mobile Services[C]// ACM. The 17th ACM SIGSPATIAL International Conference on Advances in Geographic Information Systems. New York: ACM, 2009: 256-265. |
| [27] | POULIS G, SKIADOPOULOS S, LOUKIDES G, et al. Distance-Based k^m-Anonymization of Trajectory Data[C]// IEEE. 2013 IEEE 14th International Conference on Mobile Data Management. New York: IEEE, 2013: 57-62. |
| [28] | LEI P, PENG W, SU I, et al. Dummy-Based Schemes for Protecting Movement Trajectories[J]. Journal of Information Science and Engineering, 2012, 28(2): 335-350. |
| [29] | DAI Jiazhu, HUA Liang. A Method for the Trajectory Privacy Protection Based on the Segmented Fake Trajectory under Road Networks[C]// IEEE. 2015 2nd International Conference on Information Science and Control Engineering. New York: IEEE, 2015: 13-17. |
| [30] | KONG Xiangjie, CHEN Qiao, HOU Mingliang, et al. Mobility Trajectory Generation: A Survey[J]. Artificial Intelligence Review, 2023, 56: 3057-3098. |
| [31] |
SONG Fagen, MA Tinghuai, TIAN Yuan, et al. A New Method of Privacy Protection: Random k-Anonymous[J]. IEEE Access, 2019, 7: 75434-75445.
doi: 10.1109/ACCESS.2019.2919165 |
| [1] | WEN Jinming, LIU Qing, CHEN Jie, WU Yongdong. Research Current Status and Challenges of Fully Homomorphic Cryptography Based on Learning with Errors [J]. Netinfo Security, 2024, 24(9): 1328-1351. |
| [2] | LIN Zhanhang, XIANG Guangli, LI Zhenpeng, XU Ziyi. Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(9): 1375-1385. |
| [3] | FU Yanming, LU Shenglin, CHEN Jiayuan, QIN Hua. Dynamic Task Allocation for Crowd Sensing Based on Deep Reinforcement Learning and Privacy Protection [J]. Netinfo Security, 2024, 24(3): 449-461. |
| [4] | GU Haiyan, LIU Qi, MA Zhuo, ZHU Tao, QIAN Hanwei. Research on Data Noise Addition Method Based on Availability [J]. Netinfo Security, 2024, 24(11): 1731-1738. |
| [5] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [6] | XU Ke, LI Jiayi, JIANG Xinghao, SUN Tanfeng. A Video Gait Privacy Protection Algorithm Based on Sparse Adversarial Attack on Silhouette [J]. Netinfo Security, 2024, 24(1): 48-59. |
| [7] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [8] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [9] | DU Weidong, LI Min, HAN Yiliang, WANG Xu’an. An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique [J]. Netinfo Security, 2023, 23(4): 51-60. |
| [10] | YIN Shu, CHEN Xingshu, ZHU Yi, ZENG Xuemei. Anonymous Domain Name Algorithm Based on Character Space Construction [J]. Netinfo Security, 2023, 23(4): 80-89. |
| [11] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [12] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [13] | LI Jiahui, QIN Sujuan, GAO Fei, SUN Dongxu. Controllable and Supervised Privacy Protection Scheme for Blockchain Organization Transaction Based on Attribute Encryption [J]. Netinfo Security, 2023, 23(12): 103-112. |
| [14] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [15] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||