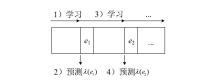
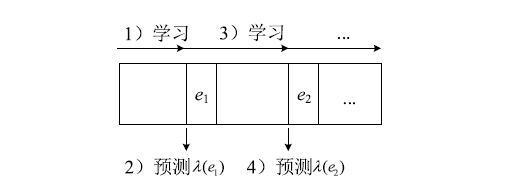
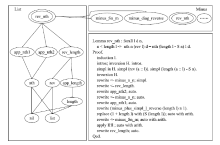
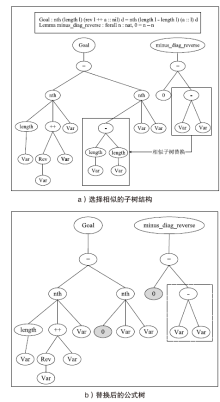
Netinfo Security ›› 2021, Vol. 21 ›› Issue (11): 9-16.doi: 10.3969/j.issn.1671-1122.2021.11.002
Previous Articles Next Articles
Research on Premise Selection Technology Based on Machine Learning Classification Algorithm
XIONG Yan1, CHENG Chuanhu2( ), WU Jianshuang3, HUANG Wenchao1
), WU Jianshuang3, HUANG Wenchao1
- 1. Department of Computer Science and Technology, University of Science and Technology of China, Hefei 230026, China
2. Department of Cyberspace Security, University of Science and Technology of China, Hefei 230026, China
3. Hefei Tianwei Information Security Technology Co., Ltd, Hefei 230009, China
-
Received:2021-06-21Online:2021-11-10Published:2021-11-24 -
Contact:CHENG Chuanhu E-mail:cchpersonal@163.com
CLC Number:
Cite this article
XIONG Yan, CHENG Chuanhu, WU Jianshuang, HUANG Wenchao. Research on Premise Selection Technology Based on Machine Learning Classification Algorithm[J]. Netinfo Security, 2021, 21(11): 9-16.
share this article
| [1] | BLANCHETTE J C, KALISZYK C, PAULSON L C, et al. Hammering Towards QED[J]. Journal of Formalized Reasoning, 2016, 9(1):101-148. |
| [2] | BARRETT C, TINELLI C. Satisfiability Modulo Theories[M]. Cham: Springer, 2018. |
| [3] | ZHANG Hengruo, FU Ming. Design and Implementation of CoQ Automatic Proof Strategy Based on Z3[J]. Journal of Software, 2017, 28(4):819-826. |
| 张恒若, 付明. 基于Z3的Coq自动证明策略的设计和实现[J]. 软件学报, 2017, 28(4):819-826. | |
| [4] |
MENG Jia, PAULSON L C. Lightweight Relevance Filtering for Machine-generated Resolution Problems[J]. Journal of Applied Logic, 2009, 7(1):41-57.
doi: 10.1016/j.jal.2007.07.004 URL |
| [5] |
JONES K S. A Statistical Interpretation of Term Specificity and Its Application in Retrieval[J]. Journal of Documentation, 1972, 28(1):11-21.
doi: 10.1108/eb026526 URL |
| [6] | ROEDERER A, PUZIS Y, SUTCLIFFE G. Divvy: An ATP Meta-system Based on Axiom Relevance Ordering[C]// Springer. International Conference on Automated Deduction, August 2-7, 2009, Montreal, QC, Canada. Heidelberg: Springer, 2009: 157-162. |
| [7] | JAKUBŮV J, URBAN J. Hammering Mizar by Learning Clause Guidance[EB/OL]. https://arxiv.org/pdf/1904.01677.pdf, 2019-04-02. |
| [8] | FÄRBER M, KALISZYK C. Random Forests for Premise Selection[C]// Springer. International Symposium on Frontiers of Combining Systems, September 21-24, 2015, Wroclaw, Poland. Cham: Springer, 2015: 325-340. |
| [9] | PIOTROWSKI B, URBAN J. ATPboost: Learning Premise Selection in Binary Setting with ATP Feedback[C]// Springer. International Joint Conference on Automated Reasoning, July 14-17, 2018, Oxford, UK. Cham: Springer, 2018: 566-574. |
| [10] | KÜHLWEIN D, VAN LAARHOVEN T, TSIVTSIVADZE E, et al. Overview and Evaluation of Premise Selection Techniques for Large Theory Mathematics[C]// Springer. International Joint Conference on Automated Reasoning, June 26-29, 2012, Manchester, UK. Heidelberg: Springer, 2012: 378-392. |
| [11] |
KALISZYK C, URBAN J. Mizar 40 for Mizar 40[J]. Journal of Automated Reasoning, 2015, 55(3):245-256.
doi: 10.1007/s10817-015-9330-8 URL |
| [12] | URBAN J, SUTCLIFFE G, PUDLÁK P, et al. MaLARea SG1-machine Learner for Automated Reasoning with Semantic Guidance[C]// Springer. International Joint Conference on Automated Reasoning, August 12-15, 2008, Sydney, Australia. Heidelberg: Springer, 2008: 441-456. |
| [13] | PIOTROWSKI B, URBAN J. Stateful Premise Selection by Recurrent Neural Networks[EB/OL]. https://arxiv.org/abs/2004.08212, 2020-03-11. |
| [14] | CHVALOVSKÝ K, JAKUBŮV J, SUDA M, et al. ENIGMA-NG: Efficient Neural and Gradient-boosted Inference Guidance for E[C]// Springer. International Conference on Automated Deduction, August 27-30, 2019, Natal, Brazil. Cham: Springer, 2019: 197-215. |
| [15] | FERREIRA D, FREITAS A. Premise Selection in Natural Language Mathematical Texts[EB/OL]. https://www.researchgate.net/publication/343296926_Premise_Selection_in_Natural_Language_Mathematical_ Texts, 2020-12-11. |
| [16] | KALISZYK C, URBAN J, MICHALEWSKI H, et al. Reinforcement Learning of Theorem Proving[EB/OL]. https://arxiv.org/pdf/1805.07563.pdf, 2018-12-03. |
| [1] | ZHU Yanhua, LIAO Fangyu, HU Lianglin, WANG Zhiqiang. Research on Key Problems of Scientific Data Security Standard [J]. Netinfo Security, 2021, 21(11): 1-8. |
| [2] | ZHAO Xiaolin, ZHAO Bin, ZHAO Jingjing, XUE Jingfeng. Research on Network Security Measurement Method Based on Attack Identification [J]. Netinfo Security, 2021, 21(11): 17-27. |
| [3] | XIA Zhe, LUO Bin, XU Guibin, XIAO Xinxiu. Privacy-preserving Data Aggregation with Fine Grained Access Control for Smart Grid [J]. Netinfo Security, 2021, 21(11): 28-39. |
| [4] | WANG Jian, YU Hang, HAN Zhen, HAN Lei. Access Control Methods of Data Sharing in Cloud Storage Based on Smart Contract [J]. Netinfo Security, 2021, 21(11): 40-47. |
| [5] | LEI Yu, LIU Jia, LI Jun, KE Yan. Research and Implementation of a Image Steganography Method Based on Conditional Generative Adversarial Networks [J]. Netinfo Security, 2021, 21(11): 48-57. |
| [6] | LI Tong, ZHOU Xiaoming, REN Shuai, XU Jian. Light-weight Mutual Authentication Protocol for Mobile Edge Computing [J]. Netinfo Security, 2021, 21(11): 58-64. |
| [7] | LI Kunchang, SHI Runhua, LI En. Survey on Data Aggregation and Privacy Protection of User Query in Smart Grid [J]. Netinfo Security, 2021, 21(11): 65-74. |
| [8] | YU Kechen, GUO Li, YAO Mengmeng. Design of Blockchain-based High-value Data Sharing System [J]. Netinfo Security, 2021, 21(11): 75-84. |
| [9] | WU Jiajie, WU Shaoling, WANG Wei. An Anomaly Detection and Location Algorithm Based on TCN and Attention Mechanism [J]. Netinfo Security, 2021, 21(11): 85-94. |
| [10] | TAN Ruhan, ZUO Liming, LIU Ergen, GUO Li. Malicious Code Detection Based on Image Feature Fusion [J]. Netinfo Security, 2021, 21(10): 90-95. |
| [11] | XIAO Shuai, ZHANG Hanlin, XIAN Hequn, CHEN Fei. A Password Authentication Key Agreement Protocol for IoT Devices [J]. Netinfo Security, 2021, 21(10): 83-89. |
| [12] | HU Jingxiu, YANG Yang, XIONG Lu, WU Jintan. SM Algorithm Analysis and Software Performance Research [J]. Netinfo Security, 2021, 21(10): 8-16. |
| [13] | CHENG Shunhang, LI Zhihua. Research on Threat Intelligence Entity Recognition Method Based on MRC [J]. Netinfo Security, 2021, 21(10): 76-82. |
| [14] | MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model [J]. Netinfo Security, 2021, 21(10): 69-75. |
| [15] | WU Jiaming, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Distance-based Fuzzing Mutation Method [J]. Netinfo Security, 2021, 21(10): 63-68. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||