Netinfo Security ›› 2015, Vol. 15 ›› Issue (4): 41-44.doi: 10.3969/j.issn.1671-1122.2015.04.007
Previous Articles Next Articles
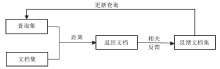
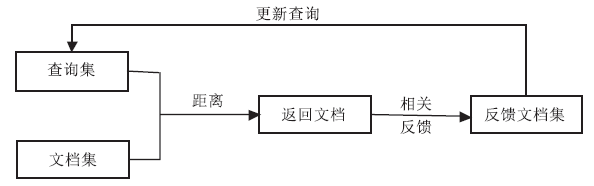
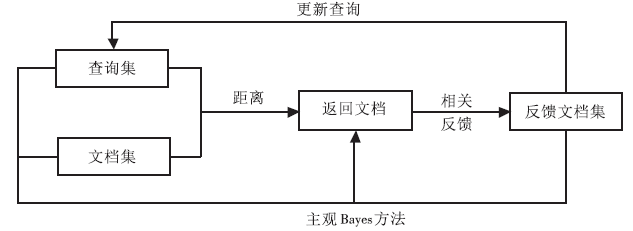
A Document Reranking Algorithm Based on Subjective Bayes Method and Relevance Feedback Technology
- College of Network Security, People’s Public Security University of China, Beijing100038, China
-
Received:2015-01-21Online:2015-04-10Published:2018-07-16
CLC Number:
Cite this article
ZHAO Yan, GU Yi-jun. A Document Reranking Algorithm Based on Subjective Bayes Method and Relevance Feedback Technology[J]. Netinfo Security, 2015, 15(4): 41-44.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2015.04.007
| [1] | 中国互联网络信息中心.第34次中国互联网络发展状况统计报告[R]. 北京: 中国互联网络信息中心,2014-07. |
| [2] | Rocchio J. Relevance feedback in information retrieval: In the SMART retrieval system, 1971[C]. 313-323. |
| [3] | Lavrenko V, Croft W B. Relevance based language models[C]//Proceedings of the 24th annual international ACM SIGIR conference on Research and development in information retrieval, 2001 ACM. 120-127. |
| [4] | Center For Intelligent Information Retrieval, Language Technologies Institute. The Lemur Project[EB/OL].. |
| [5] | John Lafferty C Z. Documnet Language Models,Query Models,and Rish Minimization for information Retrieval[C]//Proceeding of ACM SIGIR, 2001 111-119. |
| [6] | Lv Y, Zhai C. A comparative study of methods for estimating query language models with pseudo feedback[C]//Proceedings of the 18th ACM conference on Information and knowledge management, 2009 ACM. 1895-1898. |
| [7] | 数据堂.新浪微博16个热点话题数据[EB/OL].. |
| [8] | 张华平.NLPIR/ICTCLAS2014分词系统[EB/OL].. |
| [9] | 李珊珊,周爽,蒋天发. 一种分块压缩感知观测值的图像篡改认证算法[J]. 信息网络安全,2014,(4):35-39. |
| [10] | 温万里,游林. 基于混沌和比特级置乱的并行图像加密算法[J]. 信息网络安全,2014,(4):40-45. |
| [11] | 李雪晓, 叶云, 田苗苗, 等. 基于格的大数据动态存储完整性验证方案[J]. 信息网络安全,2014,(4):46-50. |
| [12] | 陈玉琼,游林. 基于两个方向二维核主成分分析的手指静脉识别[J]. 信息网络安全,2014,(4):51-54. |
| [13] | 龚乐,王火剑,万月亮,等. 基于H.323协议通信安全的远程协同鉴定系统[J]. 信息网络安全,2014,(4):55-59. |
| [14] | 王标,陈持协,孙谋,等. 环Zn上广义圆锥曲线多重数字签名方案的分析与改进[J]. 信息网络安全,2014,(4):60-63. |
| [15] | 肖萍. ASP.NET网站重构建与调查[J]. 信息网络安全,2014,(4):64-69. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems [J]. Netinfo Security, 2024, 24(7): 1015-1026. |
| [3] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [4] | ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies [J]. Netinfo Security, 2024, 24(7): 1038-1049. |
| [5] | DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism [J]. Netinfo Security, 2024, 24(7): 1050-1061. |
| [6] | ZHOU Shucheng, LI Yang, LI Chuanrong, GUO Lulu, JIA Xinhong, YANG Xinghua. Context-Based Abnormal Root Cause Algorithm [J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| [7] | REN Changyu, ZHANG Ling, JI Hangyuan, YANG Liqun. Research on TTP Extraction Method Based on Pre-Trained Language Model and Chinese-English Threat Intelligence [J]. Netinfo Security, 2024, 24(7): 1076-1087. |
| [8] | CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website [J]. Netinfo Security, 2024, 24(7): 1088-1097. |
| [9] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [10] | SHEN Xiuyu, JI Weifeng. Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security [J]. Netinfo Security, 2024, 24(7): 1110-1121. |
| [11] | ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery [J]. Netinfo Security, 2024, 24(7): 1122-1128. |
| [12] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [13] | LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET [J]. Netinfo Security, 2024, 24(7): 983-992. |
| [14] | LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication [J]. Netinfo Security, 2024, 24(7): 993-1005. |
| [15] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||