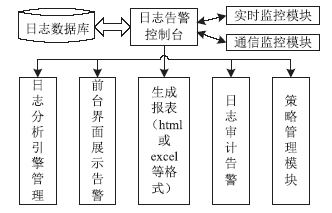
Netinfo Security ›› 2014, Vol. 14 ›› Issue (10): 70-76.doi: 10.3969/j.issn.1671-1122.2014.10.013
Previous Articles Next Articles
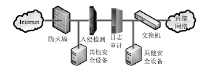
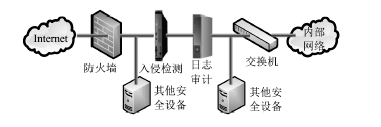
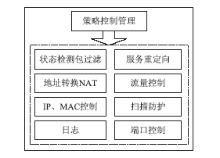
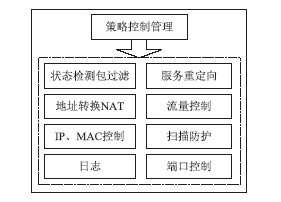
Research and Design of Security Audit Log System Based on Web Application
DUAN Juan1,2, XIN Yang1,2, MA Yu-wei1,2
- 1. Information Security Center, Beijing University of Posts and Telecommunications, Beijing 100876, China
2. National Engineering Laboratory for Disaster Backup and Recovery, Beijing 100876, China
-
Received:2014-09-01Online:2014-10-01Published:2015-08-17
CLC Number:
Cite this article
DUAN Juan, XIN Yang, MA Yu-wei. Research and Design of Security Audit Log System Based on Web Application[J]. Netinfo Security, 2014, 14(10): 70-76.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2014.10.013
| [1] | 梁莹. 基于“WEB日志挖掘”技术的校园网络日志分析与安全审计[D]. 重庆:重庆大学,2009. |
| [2] | 熊艳. 基于网络日志的安全审计系统的研究与实现[D]. 上海:上海交通大学,2002. |
| [3] | 周琪锋. 基于网络日志的安全审计系统的研究与设计[J]. 计算机技术与发展,2009,19(11):139-142. |
| [4] | 韩松言. Windows日志审计系统的设计[D]. 沈阳:东北大学,2009. |
| [5] | 石彪,胡华平,刘利枚. 网络环境下的日志监控与安全审计系统设计与实现[J]. 福建电脑,2004,(12):43-44. |
| [6] | 宋擒豹,沈钧毅. Web日志的高效多能挖掘算法[J].计算机研究与发展,2001,38(3):328-333. |
| [7] | 施建生,伍卫国,陆丽娜,等. Web日志中挖掘用户浏览模式的研究[J]. 西安交通大学学报,2001,35(6):621-324. |
| [8] | 邢东山,沈钧毅,宋擒豹. 从Web日志中挖掘用户浏览偏爱路径[J].计算机学报,2003,26(11):1518-1523. |
| [9] | 石彪,胡华平,刘利枚. 网络环境下的日志监控与安全审计系统设计与实现[J]. 福建电脑,2004,(12):43-44. |
| [10] | 殷秦. 基于云计算服务的Web性能测试服务系统开发[D]. 北京:清华大学,2010. |
| [11] | 梁广泰,王千祥. CODAS:一个易扩展的静态代码缺陷分析服务[J]. 计算机科学,2012,39(1):14-18. |
| [12] | 王海峰,夏洪雷. 入侵检测系统的局限性分析与解决策略[J]. 临沂师范学院学报,2006,28(3):110-113. |
| [13] | Spinellis D, Louridas P.A framework for the static verification of API calls[J]. The Journal of Systems and Software, 2007, 80(07): 1156–1168. |
| [14] | Ayewah N, Pugh W.Evaluating Static Analysis Defect Warnings On Production Software[C]//Proceedings of the 7th ACM SIGPLAN-SIGSOFT workshop on Program analysis for software tools and engineering, 2007: 1-8. |
| [15] | Hovemeyer D, Pugh W.Finding More Null Pointer Bugs, But Not Too Many[C]//Proceedings of the 7th ACM SIGPLAN-SIGSOFT Workshop on Program Analysis for Software Tools and Engineering, 2007: 9-14. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems [J]. Netinfo Security, 2024, 24(7): 1015-1026. |
| [3] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [4] | ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies [J]. Netinfo Security, 2024, 24(7): 1038-1049. |
| [5] | DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism [J]. Netinfo Security, 2024, 24(7): 1050-1061. |
| [6] | ZHOU Shucheng, LI Yang, LI Chuanrong, GUO Lulu, JIA Xinhong, YANG Xinghua. Context-Based Abnormal Root Cause Algorithm [J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| [7] | REN Changyu, ZHANG Ling, JI Hangyuan, YANG Liqun. Research on TTP Extraction Method Based on Pre-Trained Language Model and Chinese-English Threat Intelligence [J]. Netinfo Security, 2024, 24(7): 1076-1087. |
| [8] | CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website [J]. Netinfo Security, 2024, 24(7): 1088-1097. |
| [9] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [10] | SHEN Xiuyu, JI Weifeng. Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security [J]. Netinfo Security, 2024, 24(7): 1110-1121. |
| [11] | ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery [J]. Netinfo Security, 2024, 24(7): 1122-1128. |
| [12] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [13] | LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET [J]. Netinfo Security, 2024, 24(7): 983-992. |
| [14] | LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication [J]. Netinfo Security, 2024, 24(7): 993-1005. |
| [15] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||