信息网络安全 ›› 2021, Vol. 21 ›› Issue (10): 25-32.doi: 10.3969/j.issn.1671-1122.2021.10.004
基于图像识别的恶意软件静态检测模型
- 1.南开大学网络空间安全学院,天津 300350
2.天津市网络与数据安全技术重点实验室,天津 300350
-
收稿日期:2021-04-30出版日期:2021-10-10发布日期:2021-10-14 -
通讯作者:张健 E-mail:zhang.jian@nankai.edu.cn -
作者简介:杨铭(1999—),男,湖南,硕士研究生,主要研究方向为云安全、网络安全、系统安全|张健(1968—),男,天津,正高级工程师,博士,主要研究方向为云安全、系统安全、恶意代码防治 -
基金资助:国家重点研发计划(2021YFF0307202);天津市新一代人工智能科技重大专项(19ZXZNGX00090);天津市重点研发计划(20YFZCGX00680)
Static Detection Model of Malware Based on Image Recognition
- 1. College of Cyber Science, Nankai University, Tianjin 300350, China
2. Tianjin Key Laboratory of Network and Data Security Technology, Tianjin 300350, China
-
Received:2021-04-30Online:2021-10-10Published:2021-10-14 -
Contact:ZHANG Jian E-mail:zhang.jian@nankai.edu.cn
摘要:
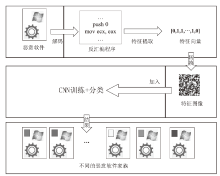
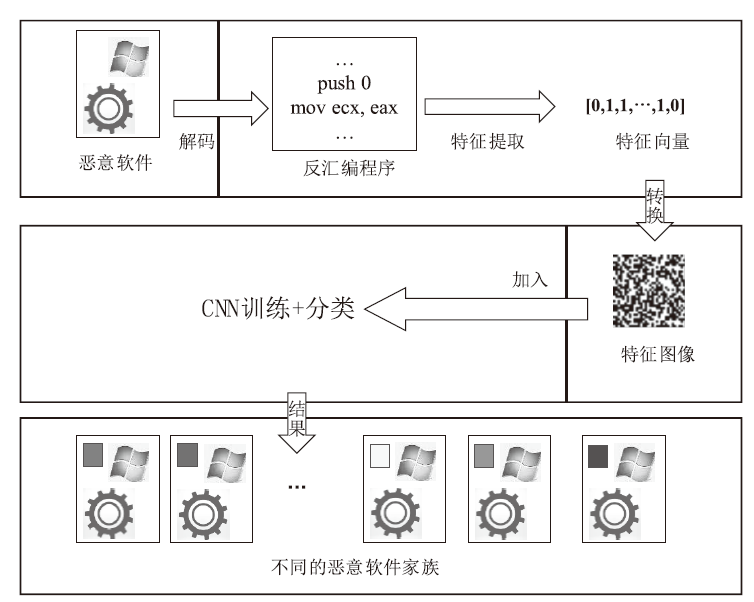
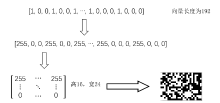
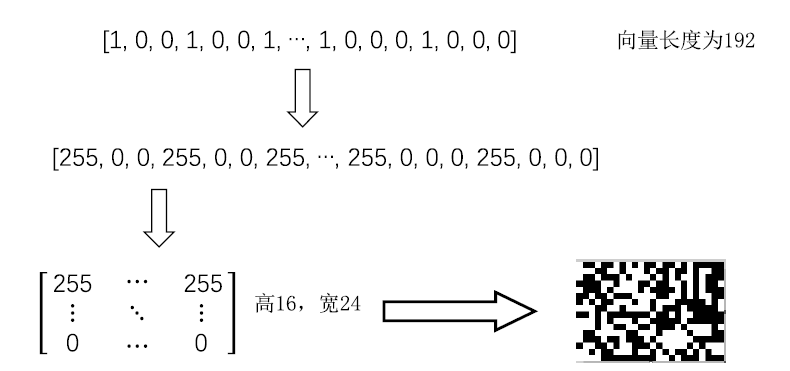
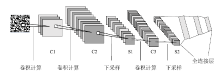
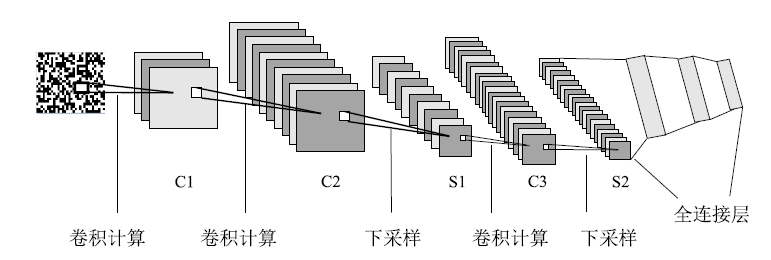
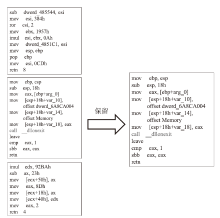
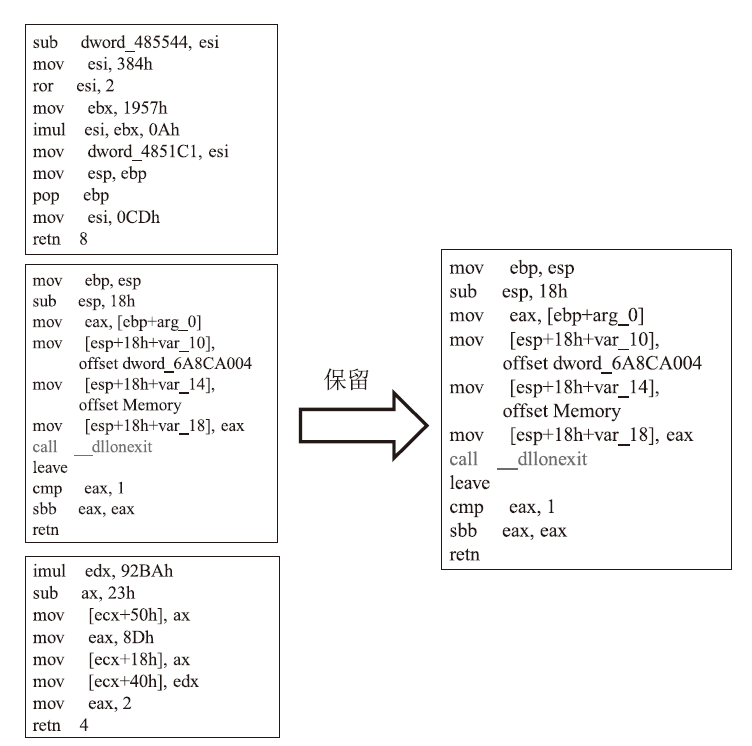
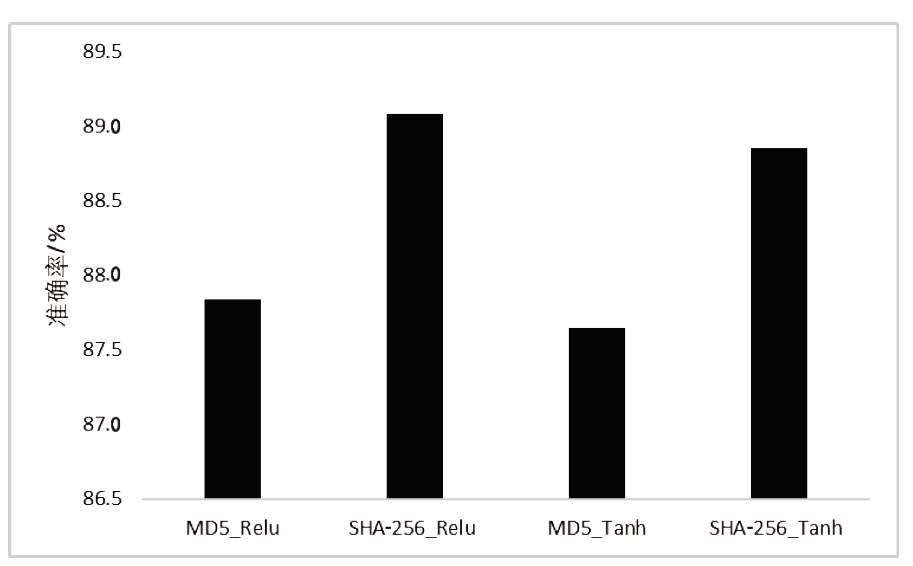
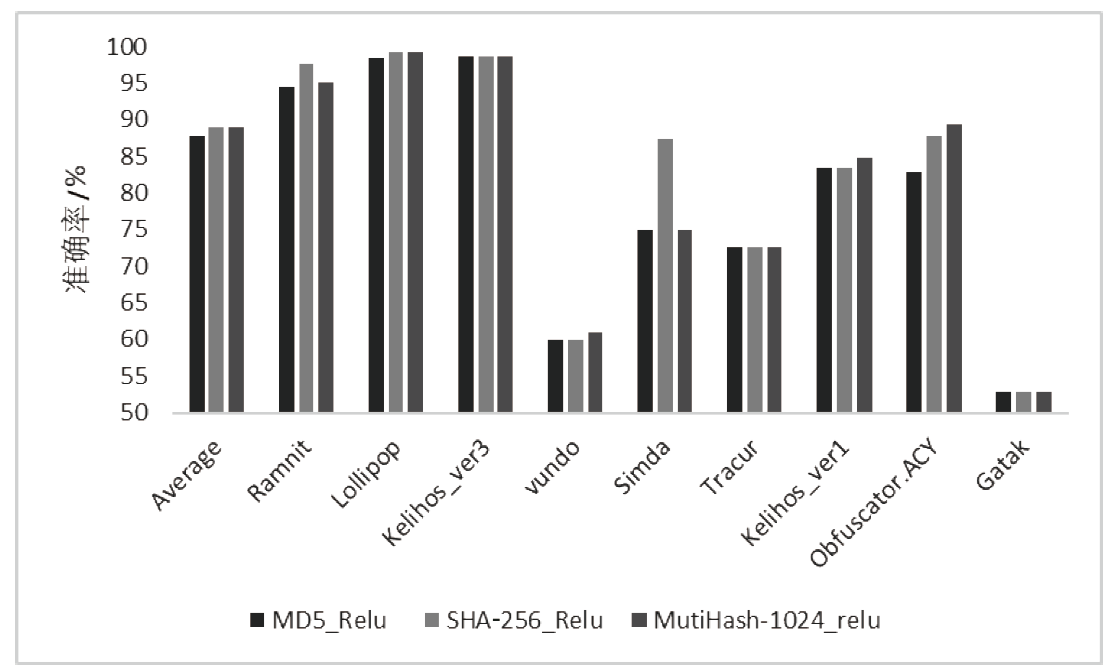
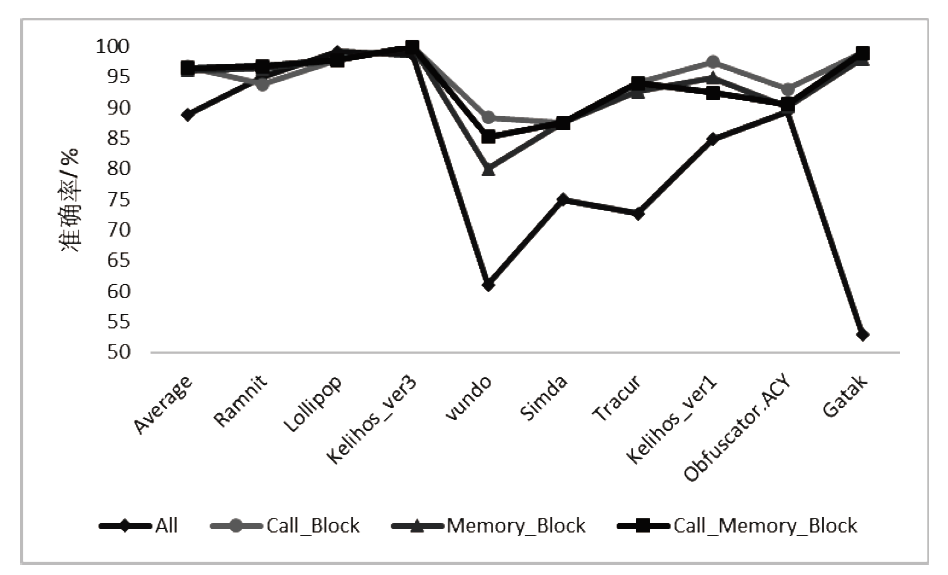
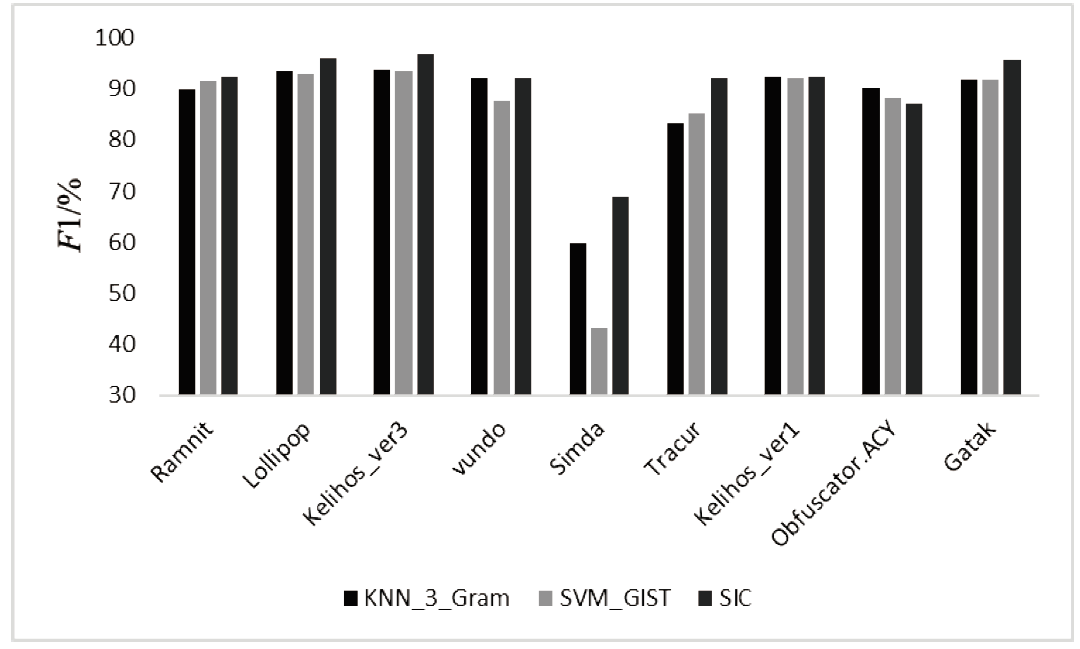
恶意软件是当前互联网安全的主要威胁之一。文章以对恶意软件进行快速有效检测为研究目的,提出了SIC模型,该模型采用SimHash方法,利用恶意软件的操作码的位置特征和数量特征,将恶意软件转换成特征向量,再转换为灰度图,然后使用卷积神经网络(CNN)识别出恶意软件所属的家族。文章使用多重Hash、块选择算法对SIC模型进行优化。模型选用微软2015年发布的恶意软件分类挑战数据集进行训练,实验结果表明,SIC模型的检测识别准确率可达96.774%。相较于其他基于传统的机器学习的恶意软件分类模型,文章方案有一定程度的提高。
中图分类号:
引用本文
杨铭, 张健. 基于图像识别的恶意软件静态检测模型[J]. 信息网络安全, 2021, 21(10): 25-32.
YANG Ming, ZHANG Jian. Static Detection Model of Malware Based on Image Recognition[J]. Netinfo Security, 2021, 21(10): 25-32.
| [1] | Symatec Corporation. Internet Security Threat Report[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=e4f762cca6e121c932226ec3b49ec9b6&site=xueshu_se, 2021-02-26. |
| [2] | National Computer Network Emergency Technical Processing Coordination Center. China’s Internet Network Security Monitoring Data Analysis Report in the First Half of 2020[EB/OL]. http://www.cac.gov.cn/2020-09/26/c_1602682854845452.htm, 2020-09-30. |
| 国家计算机网络应急技术处理协调中心. 2020 年上半年我国互联网网络安全监测数据分析报告[EB/OL]. http://www.cac.gov.cn/2020-09/26/c_1602682854845452.htm, 2020-09-30. | |
| [3] |
DANIEL B. Opcodes as Predictor for Malware[J]. International Journal of Electronic Security and Digital Forensics, 2007, 1(2):156-168.
doi: 10.1504/IJESDF.2007.016865 URL |
| [4] | YE Yanfang, LI Tao, CHEN Yong, et al. Automatic Malware Categorization Using Cluster Ensemble [C]//ACM. 16th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, July 25-28, 2010, Washington DC, USA. New York: ACM, 2010: 95-104. |
| [5] |
YUAN Zhenlong, LU Yongqiang, WANG Zhaoguo, et al. Droid-Sec: Deep Learning in Android Malware Detection[J]. ACM Sigcomm Computer Communication Review, 2014, 44(4):371-372.
doi: 10.1145/2740070.2631434 URL |
| [6] |
SUN Guosong, QIAN Quan. Deep Learning and Visualization for Identifying Malware Families[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 18(1):283-295.
doi: 10.1109/TDSC.8858 URL |
| [7] | AGHAKHANI H, GRITTI F, MECCA F, et al. When Malware is Packin’Heat; Limits of Machine Learning Classifiers Based on Static Analysis Features [C]//ISOC. 27th Network and Distributed System Security Symposium, February 23-26, 2020, San Diego, CA, USA. Reston: ISOC, 2020: 1-20. |
| [8] | QIAO Yong, YANG Yuexiao, HE Jie, et al. CBM: Free, Automatic Malware Analysis Framework Using API Call Sequences[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=2f9a98813da9302381169505621a5a1d, 2021-02-28. |
| [9] |
ANDERSON B, QUIST D, NEIL J, et al. Graph-based Malware Detection Using Dynamic Analysis[J]. Journal in Computer Virology, 2011, 7(4):247-258.
doi: 10.1007/s11416-011-0152-x URL |
| [10] | FUJINO A, MURAKMI J, MORI T. Discovering Similar Malware Samples Using API Call Topics [C]//IEEE. 12th Annual IEEE Consumer Communications and Networking Conference, January 9-12, 2015, Las Vegas, NV, USA. Piscataway: IEEE, 2015: 140-147. |
| [11] | AMER E, ZELINKA I. A Dynamic Windows Malware Detection and Prediction Method Based on Contextual Understanding of API Call Sequence[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=184b0mv0v2710c503t410e10nv535705&site=xueshu_se, 2020-12-28. |
| [12] | ZHANG Jixin, ZHENG Qin, HUI Yin, et al. IRMD: Malware Variant Detection Using Opcode Image Recognition [C]// IEEE. International Conference on Parallel & Distributed Systems, December 13-16, 2016, Wuhan, China.Piscataway: IEEE, 2017: 1175-1180. |
| [13] | KIM T, KANG B, KWON H. Malware Classification Method via Binary Content Comparison [C]// ACM. 2012 ACM Research in Applied Computation Symposium, October 23-26, 2012, San Antonio, USA. New York: ACM, 2012: 316-321. |
| [14] | SANTONS I, DEVESA J, BREZO F, et al. OPEM: A Static-dynamic Approach for Machine- learning-based Malware Detection[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=73e0e66daef64a6f5d40ec7348d14e34&site=xueshu_se&sc_from=nju, 2021-02-26. |
| [15] | NATARAJ L, KARTHIKEYAN S, JACOB G, et al. Malware Images: Visualization and Automatic Classification [C]// ACM. 8th International Symposium on Visualization for Cyber Security, Pittsburgh Pennsylvania, USA, July 20, 2011. New York: ACM, 2011: 1-7. |
| [1] | 弋晓洋, 张健. 基于图像的网络钓鱼邮件检测方法研究[J]. 信息网络安全, 2021, 21(9): 52-58. |
| [2] | 李彦霖, 蔡满春, 芦天亮, 席荣康. 遗传算法优化CNN的网站指纹攻击方法[J]. 信息网络安全, 2021, 21(9): 59-66. |
| [3] | 徐国天, 盛振威. 基于融合CNN与LSTM的DGA恶意域名检测方法[J]. 信息网络安全, 2021, 21(10): 41-47. |
| [4] | 马骁, 蔡满春, 芦天亮. 基于CNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2021, 21(10): 69-75. |
| [5] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [6] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [7] | 刘静, 张学谦, 刘全明. 混合Gabor的轻量级卷积神经网络的验证码识别研究[J]. 信息网络安全, 2020, 20(7): 77-84. |
| [8] | 郑东, 赵月. 基于SM3与多特征值的Android恶意软件检测[J]. 信息网络安全, 2020, 20(6): 17-25. |
| [9] | 李明磊, 黄晖, 陆余良. 面向漏洞挖掘的基于符号分治区的测试用例生成技术[J]. 信息网络安全, 2020, 20(5): 39-46. |
| [10] | 张蕾华, 黄进, 张涛, 王生玉. 视频侦查中人像智能分析应用及算法优化[J]. 信息网络安全, 2020, 20(5): 88-93. |
| [11] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [12] | 徐国天, 沈耀童. 基于XGBoost和LightGBM双层模型的恶意软件检测方法[J]. 信息网络安全, 2020, 20(12): 54-63. |
| [13] | 王长杰, 李志华, 张叶. 一种针对恶意软件家族的威胁情报生成方法[J]. 信息网络安全, 2020, 20(12): 83-90. |
| [14] | 顾兆军, 郝锦涛, 周景贤. 基于改进双线性卷积神经网络的恶意网络流量分类算法[J]. 信息网络安全, 2020, 20(10): 67-74. |
| [15] | 侯留洋, 罗森林, 潘丽敏, 张笈. 融合多特征的Android恶意软件检测方法[J]. 信息网络安全, 2020, 20(1): 67-74. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||