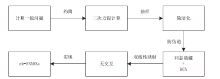
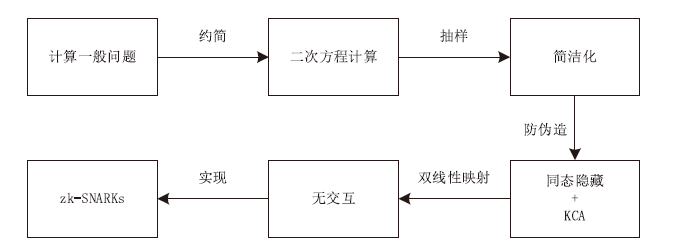
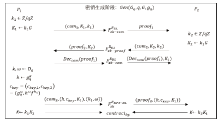
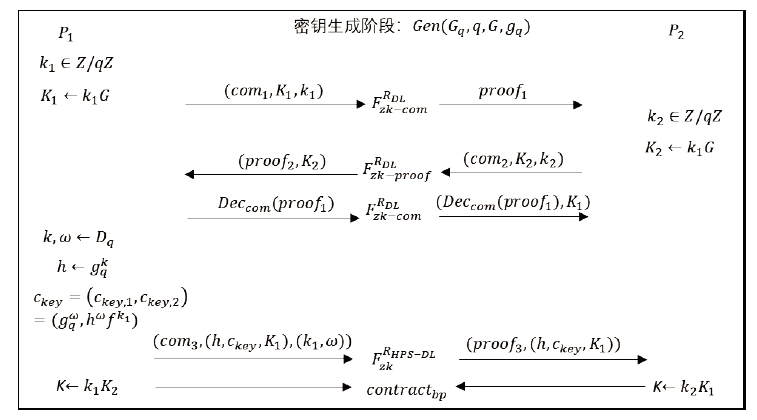
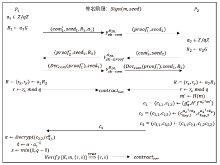
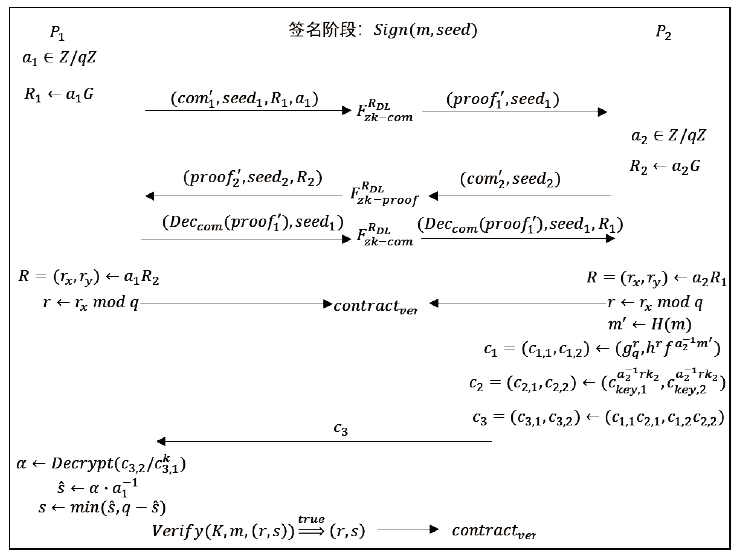
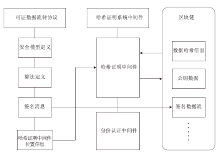
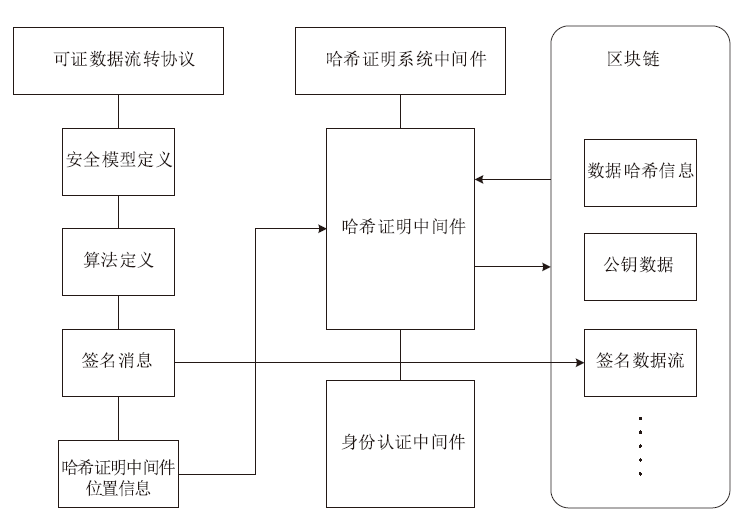
| [1] |
KOBLITZ N. Elliptic Curve Cryptosystems[J]. Mathematics of Computation, 1987,48(177):203-209.
doi: 10.1090/S0025-5718-1987-0866109-5
URL
|
| [2] |
MILLER V S. Use of Elliptic Curves in Cryptography[C] // ACM. Lecture notes in computer sciences 218 on Advances in cryptology—-CRYPTO 85, August 18-22, 1985, Santa Barbara, California, USA. Heidelberg: Springer, 1986: 417-426.
|
| [3] |
HU Y C, LABERTEAUX K P. Strong VANET Security on a Budget[EB/OL]. https://www.researchgate.net/publication/250004065_Strong_VANET_security_on_a_budget, 2020-06-19.
|
| [4] |
ABUEH Y J, LIU H. Message Authentication in Driverless Cars[EB/OL]. https://ieeexplore.ieee.org/document/7568882, 2020-06-25.
|
| [5] |
COURTOIS N, SONG G, CASTELLUCCI R. Speed Optimizations in Bitcoin Key Recovery Attacks[J]. Tatra Mountains Mathematical Publications, 2016,67(1):55-68.
doi: 10.1515/tmmp-2016-0030
URL
|
| [6] |
CHEN Yuan, BAI Enjian, XIAO Guozhen. Equivalence Between Two Definitions of Semantic Security[J]. Acta Electronica Sinica, 2009,37(10):2149-2153.
|
|
陈原, 白恩健, 肖国镇. 两种语义安全性定义的等价性[J]. 电子学报, 2009,37(10):2149-2153.
|
| [7] |
YU Wei, LI Bao, WANG Kunpeng, et al. Co-z Montgomery Algorithm on Elliptic Curves over Finite Fields of Characteristic Three[J]. Chinese Journal of Computers, 2017,40(5):1121-1133.
|
|
于伟, 李宝, 王鲲鹏, 等. 特征3有限域上椭圆曲线的co-Z Montgomery算法[J]. 计算机学报, 2017,40(5):1121-1133.
|
| [8] |
CAMPBELL Sr R. Evaluation of Post-quantum Distributed Ledger Cryptography[J]. The Journal of the British Blockchain Association, 2019,2(1):7679.
|
| [9] |
CASTAGNOS G, CATALANO D, LAGUILLAUMIE F, et al. Two-party ECDSA from Hash Proof Systems and Efficient Instantiations[EB/OL]. https://www.researchgate.net/publication/335077814_Two-Party_ECDSA_from_Hash_Proof_Systems_and_Efficient_Instantiations, 2020-06-29.
|
| [10] |
LINDELL Y. Fast Secure Two-party ECDSA Signing[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=14579863a345247cf28a724049a82c78&site=xueshu_se, 2020-06-30.
|
| [11] |
DOERNER J, KONDI Y, LEE E, et al. Secure Two-party Threshold ECDSA from ECDSA Assumptions[EB/OL]. https://www.computer.org/csdl/pds/api/csdl/proceedings/download-article/12OmNvDI3J1/pdf, 2020-07-10.
|
| [12] |
LINDELL Y, NOF A. Fast Secure Multiparty ECDSA with Practical Distributed Key Generation and Applications to Cryptocurrency Custody[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=114400w0xs5q04p0625h0vf05b514642&site=xueshu_se, 2020-07-13.
|
| [13] |
CRAMER R, SHOUP V. Universal Hash Proofs and a Paradigm for Adaptive Chosen Ciphertext Secure Public-key Encryption[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=114400w0xs5q04p0625h0vf05b514642&site=xueshu_se, 2020-07-15.
|
| [14] |
LAI Qiqi, YANG Bo, YU Yong, et al. A Survey on the Construction of Hash Proof Systems Based on Lattices. Journal of Cryptologic Research, 2017,4(5):474-484.
|
|
来齐齐, 杨波, 禹勇, 等. 基于格的哈希证明系统的构造综述[J]. 密码学报, 2017,4(5):474-484.
|
| [15] |
HOPWOOD D, BOWE S, HORNBY T, et al. Zcash Protocol Specification[EB/OL]. , 2020-07-19.
|
| [16] |
PARNO B, HOWELL J, GENTRY C, et al. Pinocchio: Nearly Practical Verifiable Computation[EB/OL]. http://www.andrew.cmu.edu/user/bparno/papers/pinocchio-cacm.pdf, 2020-07-20.
|
| [17] |
BUNZ B, AGRAWAL S, ZAMANI M, et al. Zether: Towards Privacy in a Smart Contract World[EB/OL]. https://www.researchgate.net/publication/343032027_Zether_Towards_Privacy_in_a_Smart_Contract_World, 2020-07-22.
|
| [18] |
WILLIAMSON Z J. The Aztec Protocol[EB/OL]. https://github.com/AztecProtocol/AZTEC, 2020-07-25.
|
 )
)