信息网络安全 ›› 2024, Vol. 24 ›› Issue (2): 293-302.doi: 10.3969/j.issn.1671-1122.2024.02.012
融合梯度差分的双边校正联邦入侵检测算法
- 天津大学电气自动化与信息工程学院,天津 300072
-
收稿日期:2023-12-28出版日期:2024-02-10发布日期:2024-03-06 -
通讯作者:武晓栋 E-mail:xdwu@tju.edu.cn -
作者简介:金志刚(1972—),男,上海,教授,博士,主要研究方向为水下网络、传感器网络、网络安全、社交网络与大数据|丁禹(2001—),男,四川,硕士研究生,主要研究方向为入侵检测、联邦学习|武晓栋(1996—),男,内蒙古,博士研究生,主要研究方向为入侵检测、联邦学习、增量学习 -
基金资助:国家自然科学基金(52171337)
Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference
JIN Zhigang, DING Yu, WU Xiaodong( )
)
- School of Electrical and Information Engineering, Tianjin University, Tianjin 300072, China
-
Received:2023-12-28Online:2024-02-10Published:2024-03-06 -
Contact:WU Xiaodong E-mail:xdwu@tju.edu.cn
摘要:
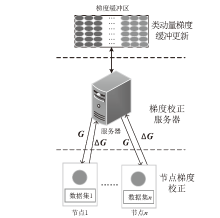
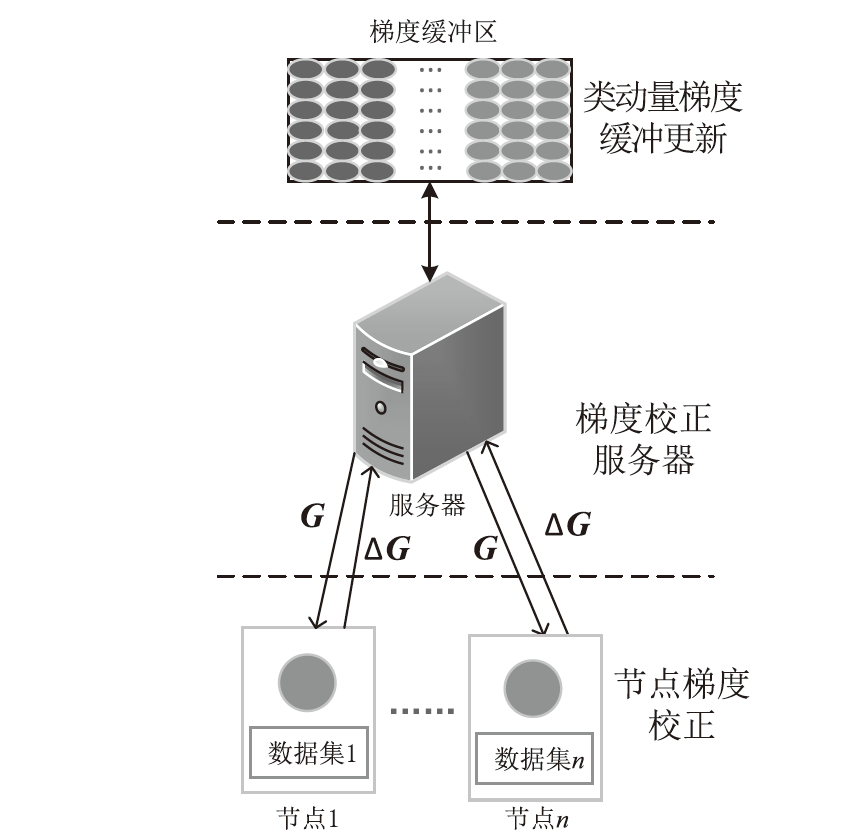
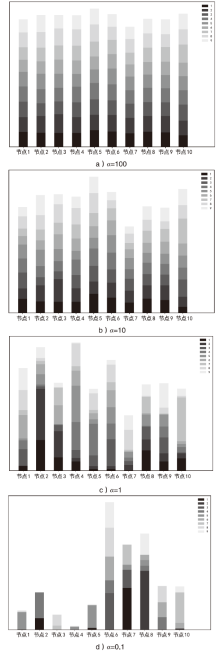
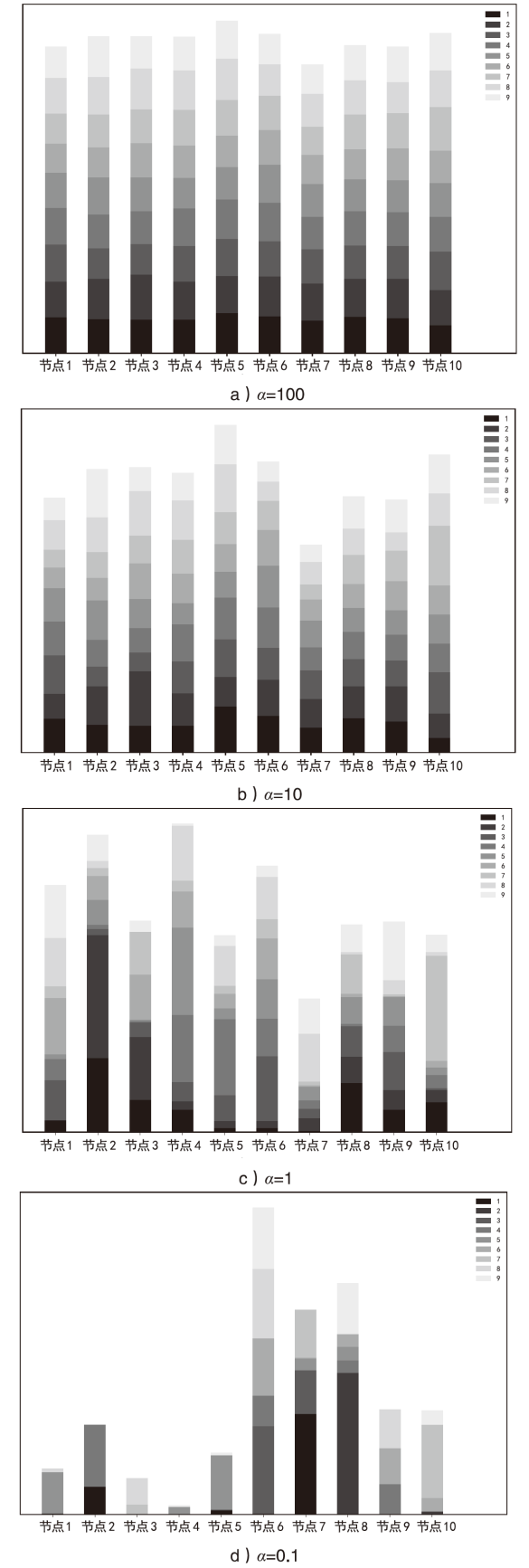
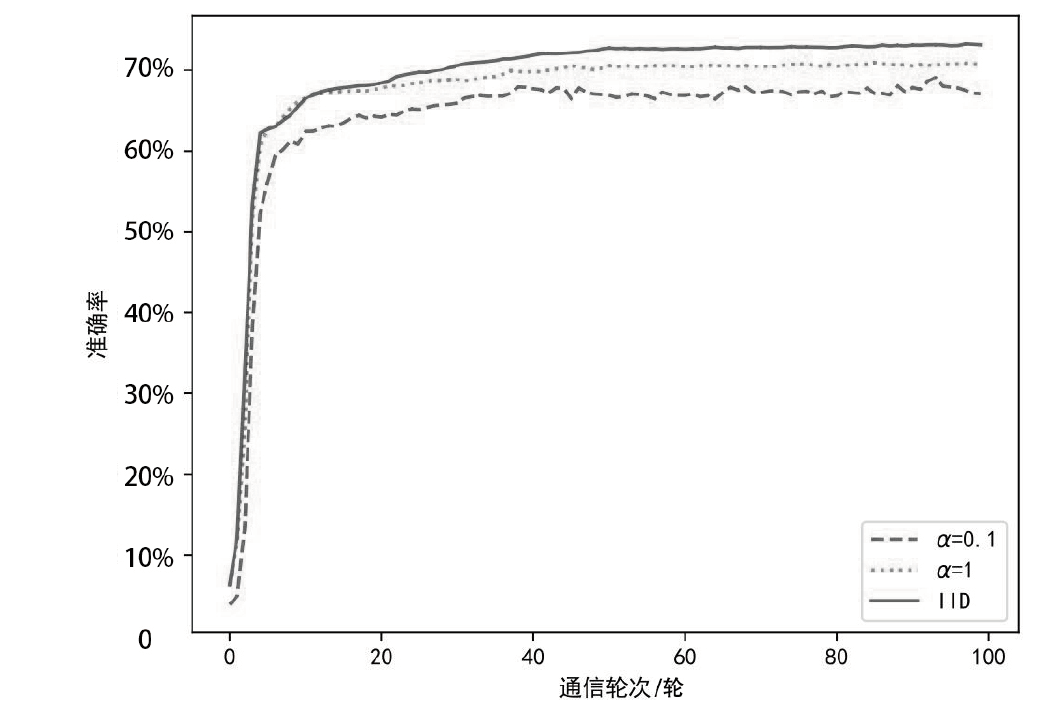
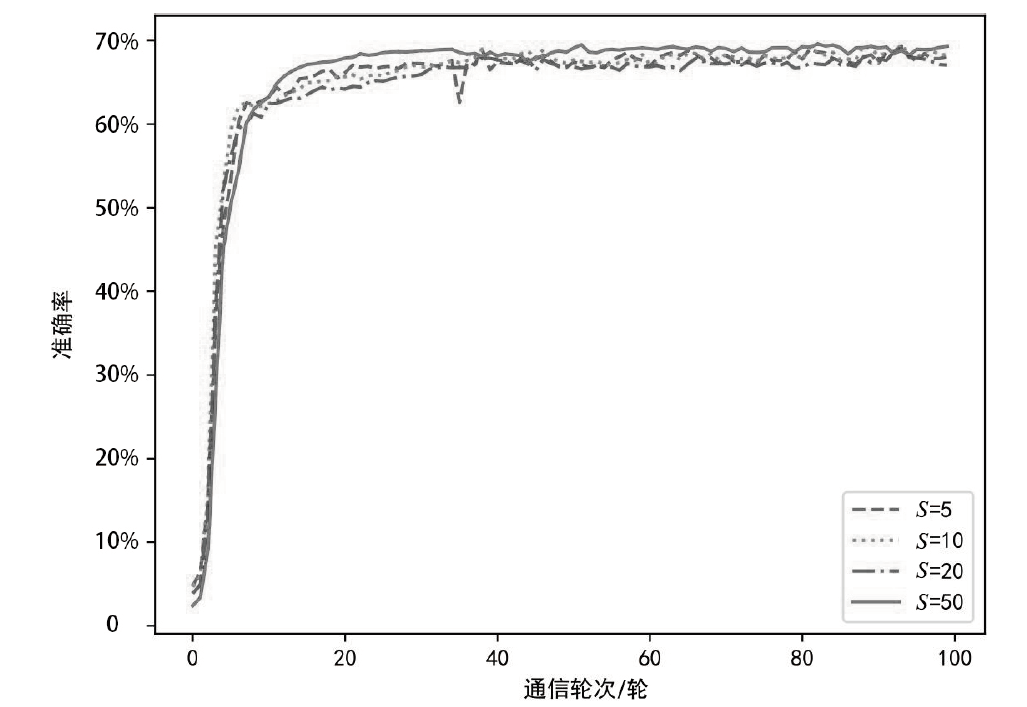
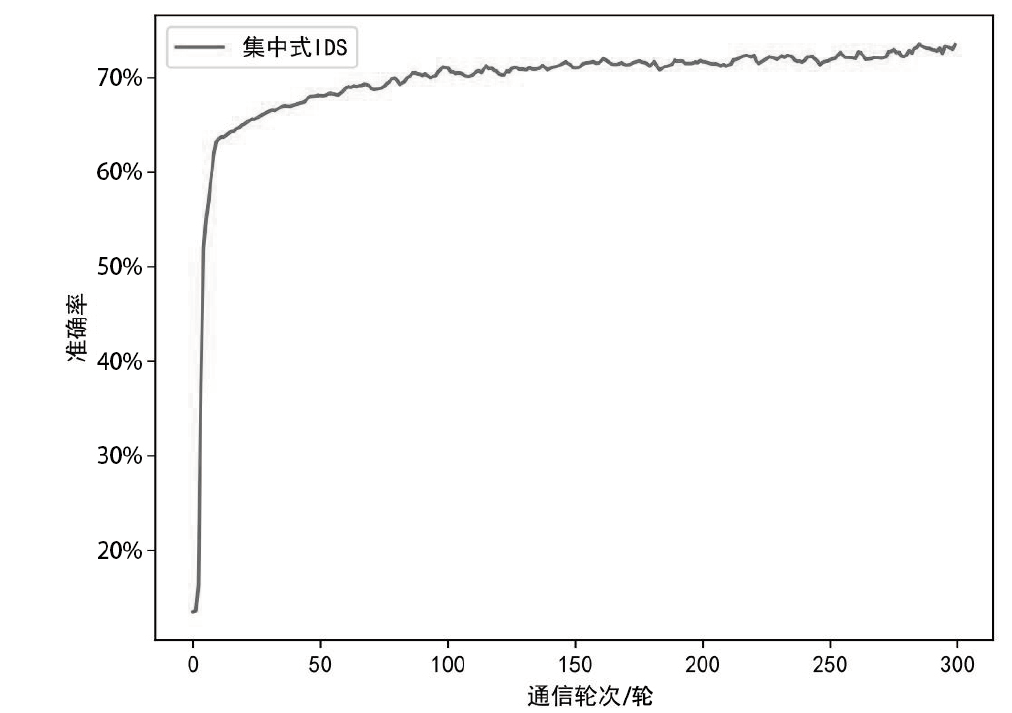
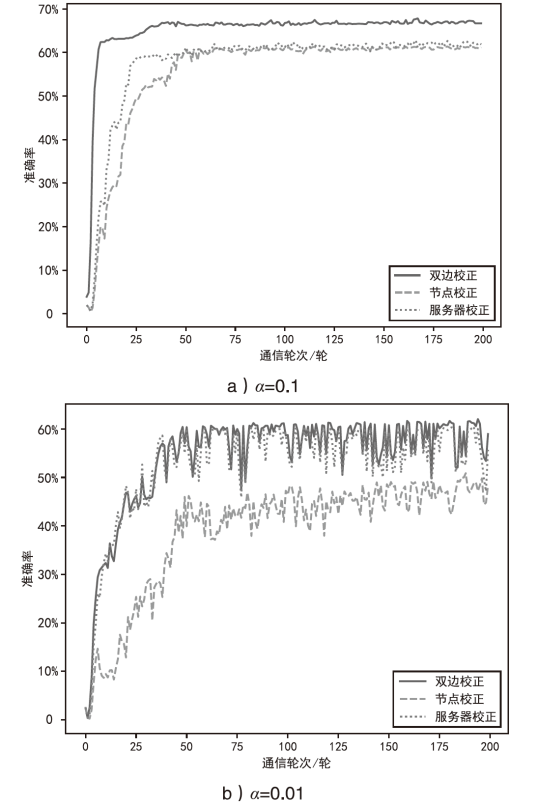
日趋多样的设备组成和灵活的拓扑结构导致联邦入侵检测系统面临数据异质和部分参与的考验,出现了模型泛化性差、本地节点过拟合、灾难性遗忘等问题。为解决上述问题,文章提出融合梯度差分的双边校正联邦入侵检测算法。文章所提算法使用节点更新时的梯度差分在服务器和节点双边校正梯度更新方向。聚合阶段,服务器拟合全局梯度差分校正全局模型的更新方向,并以类动量式的梯度更新策略平衡各节点的全局先验知识,解决低泛化性问题。训练阶段,节点结合本地信息、全局信息、历史信息校正本地模型的更新方向,缓解本地过拟合和灾难性遗忘问题。将该算法应用在FedAvg(Federated Average)的实验结果表明,文章所提算法在多种联邦场景下具有优秀的多分类性能,并在保护数据隐私的同时,有效实现了复杂联邦环境下的网络入侵检测。
中图分类号:
引用本文
金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302.
JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference[J]. Netinfo Security, 2024, 24(2): 293-302.
| [1] | IBM Security, Ponemon Institute. Cost of a Data Breach Report 2022[EB/OL]. (2022-08-08)[2023-12-12]. https://max.book118.com/html/2022/0803/6242012004004221.shtm. |
| [2] | BUCZAK A L, GUVEN E. A Survey of Data Mining and Machine Learning Methods for Cyber Security Intrusion Detection[J]. IEEE Communications Surveys & Tutorials, 2016, 18(2): 1153-1176. |
| [3] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network[J]. Netinfo Security, 2020, 20(4): 47-54. |
| 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. | |
| [4] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2016-02-17)[2023-12-10]. http://arxiv.org/abs/1602.05629. |
| [5] | BAI Hongpeng, DENG Dongxu, XU Guangquan, et al. Research on Intrusion Detection Mechanism Based on Federated Learning[J]. Netinfo Security, 2022, 22(1): 46-54. |
| 白宏鹏, 邓东旭, 许光全, 等. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. | |
| [6] |
RAHMAN S A, TOUT H, TALHI C, et al. Internet of Things Intrusion Detection: Centralized, On-Device, or Federated Learning?[J]. IEEE Network, 2020, 34(6): 310-317.
doi: 10.1109/MNET.65 URL |
| [7] | NGUYEN T D, MARCHAL S, MIETTINEN M, et al. DIoT: A Federated Self-Learning Anomaly Detection System for IoT[C]// IEEE. 39th International Conference on Distributed Computing Systems (ICDCS). New York:IEEE, 2019: 756-767. |
| [8] |
LI Beibei, WU Yuhao, SONG Jiarui, et al. DeepFed: Federated Deep Learning for Intrusion Detection in Industrial Cyber-Physical Systems[J]. IEEE Transactions on Industrial Informatics, 2021, 17(8): 5615-5624.
doi: 10.1109/TII.2020.3023430 URL |
| [9] | LUO Kangyang, LI Xiang, GAO Ming. GradMA: A Gradient-Memory-Based Accelerated Federated Learning with Alleviated Catastrophic Forgetting[C]// IEEE. 2023 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York:IEEE, 2023: 3708-3717. |
| [10] | AGRAWAL S, SARKAR S, AOUEDIET O, et al. Federated Learning for Intrusion Detection System: Concepts, Challenges and Future Directions[EB/OL]. [2023-12-12]. https://www.researchgate.net/publication/352505433_Federated_Learning_for_Intrusion_Detection_System_Concepts_Challenges_and_Future_Directions. |
| [11] | LI Xiang, HUANG Kaixuan, YANG Wenhao, et al. On The Convergence of Fedavg on Non-IID Data[EB/OL]. (2019-07-04)[2023-12-11]. https://arxiv.org/abs/1907.02189. |
| [12] |
LI Jianbin, TONG Xin, LIU Jinwei, et al. An Efficient Federated Learning System for Network Intrusion Detection[J]. IEEE Systems Journal, 2023, 17(2): 2455-2464.
doi: 10.1109/JSYST.2023.3236995 URL |
| [13] | OLIVEIRA J A D, GONÇALVES V P, MENEGUETTE R I, et al. F-NIDS—A Network Intrusion Detection System Based on Federated Learning[EB/OL]. [2023-12-27]. https://doi.org/10.1016/j.comnet.2023.110010. |
| [14] | KAIROUZ P, MCMAHAN H B, AVENT B, et al. Advances and Open Problems in Federated Learning[EB/OL]. (2019-12-10)[2023-12-11]. https://arxiv.org/abs/1912.04977. |
| [15] | ZHONG Zhicong, ZHOU Yipeng, WU Di, et al. P-FedAvg: Parallelizing Federated Learning with Theoretical Guarantees[C]// IEEE. 2021-IEEE Conference on Computer Communications. New York: IEEE, 2021: 1-10. |
| [16] | LI Tian, SAHU A K, ZAHEER M, et al. Federated Optimization in Heterogeneous Networks[EB/OL]. (2018-12-14)[2023-12-13]. https://arxiv.org/abs/1812.06127. |
| [17] | LI Qinbin, HE Bingsheng, SONG D. Model-Contrastive Federated Learning[C]// IEEE. 2021 Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2021: 10708-10717. |
| [18] | KIM J, KIM G, HAN B. Multi-Level Branched Regularization for Federated Learning[EB/OL]. (2022-07-14)[2023-12-13]. https://arxiv.org/abs/2207.06936. |
| [19] |
ZHAO Ruijie, WANG Yijun, XUE Zhi, et al. Semisupervised Federated-Learning-Based Intrusion Detection Method for Internet of Things[J]. IEEE Internet of Things Journal, 2023, 10(10): 8645-8657.
doi: 10.1109/JIOT.2022.3175918 URL |
| [20] | YANG Haibo, ZHANG Xin, KHANDURI P, et al. Anarchic Federated Learning[EB/OL]. (2021-08-23)[2023-12-13]. https://arxiv.org/abs/2108.09875. |
| [21] | GU Xinran, HUANG Kaixuan, ZHANG Jingzhao, et al. Fast Federated Learning in the Presence of Arbitrary Device Unavailability[EB/OL]. (2021-06-08)[2023-12-13]. https://arxiv.org/abs/2106.04159. |
| [22] |
JIN Zhigang, ZHOU Junyi, LI Bing, et al. FL-IIDS: A Novel Federated Learning-Based Incremental Intrusion Detection System[J]. Future Generation Computer Systems, 2024, 151: 57-70.
doi: 10.1016/j.future.2023.09.019 URL |
| [23] | MOUSTAFA N, SLAY J. UNSW-NB15: A Comprehensive Data Set for Network Intrusion Detection Systems(UNSW-NB15 Network Data Set)[C]//IEEE. 2015 Military Communications and Information Systems Conference (MilCIS). New York: IEEE, 2015: 1-6. |
| [24] | ZHANG Zheming. Maritime Network Intrusion Detection Based on Deep Learning and Transfer Learning[D]. Shanghai: Shanghai Maritime University, 2022. |
| 张哲铭. 基于深度学习和迁移学习的海事网络入侵检测研究[D]. 上海: 上海海事大学, 2022. |
| [1] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [2] | 林怡航, 周鹏远, 吴治谦, 廖勇. 基于触发器逆向的联邦学习后门防御方法[J]. 信息网络安全, 2024, 24(2): 262-271. |
| [3] | 赵鹏程, 于俊清, 李冬. 一种基于深度学习的SRv6网络流量调度优化算法[J]. 信息网络安全, 2024, 24(2): 272-281. |
| [4] | 孙红哲, 王坚, 王鹏, 安雨龙. 基于Attention-BiTCN的网络入侵检测方法[J]. 信息网络安全, 2024, 24(2): 309-318. |
| [5] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| [6] | 赵佳, 杨博凯, 饶欣宇, 郭雅婷. 基于联邦学习的Tor流量检测算法设计与实现[J]. 信息网络安全, 2024, 24(1): 60-68. |
| [7] | 徐茹枝, 戴理朋, 夏迪娅, 杨鑫. 基于联邦学习的中心化差分隐私保护算法研究[J]. 信息网络安全, 2024, 24(1): 69-79. |
| [8] | 赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105. |
| [9] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [10] | 沈华, 田晨, 郭森森, 慕志颖. 基于对抗性机器学习的网络入侵检测方法研究[J]. 信息网络安全, 2023, 23(8): 66-75. |
| [11] | 彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85. |
| [12] | 刘宇啸, 陈伟, 张天月, 吴礼发. 基于稀疏自动编码器的可解释性异常流量检测[J]. 信息网络安全, 2023, 23(7): 74-85. |
| [13] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [14] | 陈晶, 彭长根, 谭伟杰, 许德权. 基于差分隐私和秘密共享的多服务器联邦学习方案[J]. 信息网络安全, 2023, 23(7): 98-110. |
| [15] | 赵彩丹, 陈璟乾, 吴志强. 基于多通道联合学习的自动调制识别网络[J]. 信息网络安全, 2023, 23(4): 20-29. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||