信息网络安全 ›› 2024, Vol. 24 ›› Issue (2): 282-292.doi: 10.3969/j.issn.1671-1122.2024.02.011
多维深度导向的Java Web模糊测试方法
- 1.武汉大学国家网络安全学院,武汉 430072
2.武汉大学空天信息安全与可信计算教育部重点实验室,武汉 430072
3.中国电力科学研究院有限公司信息通信研究所,北京 100192
-
收稿日期:2023-04-12出版日期:2024-02-10发布日期:2024-03-06 -
通讯作者:蔺子卿 E-mail:linziqing@epri.sgcc.com.cn -
作者简介:王鹃(1976—),女,湖北,教授,博士,CCF高级会员,主要研究方向为系统和软件安全、可信计算、人工智能安全、云计算、物联网安全|龚家新(1999—),男,安徽,硕士研究生,主要研究方向为软件安全、漏洞挖掘与利用|蔺子卿(1996—),女,北京,工程师,硕士,主要研究方向为电力工控安全和网络安全|张晓娟(1988—),女,北京,高级工程师,博士,主要研究方向为数据安全、密码学和网络安全 -
基金资助:国家电网有限公司科技项目(520940210009)
Multidimensional Depth Oriented Fuzzing Method of Java Web Applications
WANG Juan1,2, GONG Jiaxin1,2, LIN Ziqing3( ), ZHANG Xiaojuan3
), ZHANG Xiaojuan3
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
3. Institute of Information and Communication, China Electric Power Research lnstitute Co., Ltd., Beijing 100192, China
-
Received:2023-04-12Online:2024-02-10Published:2024-03-06 -
Contact:LIN Ziqing E-mail:linziqing@epri.sgcc.com.cn
摘要:
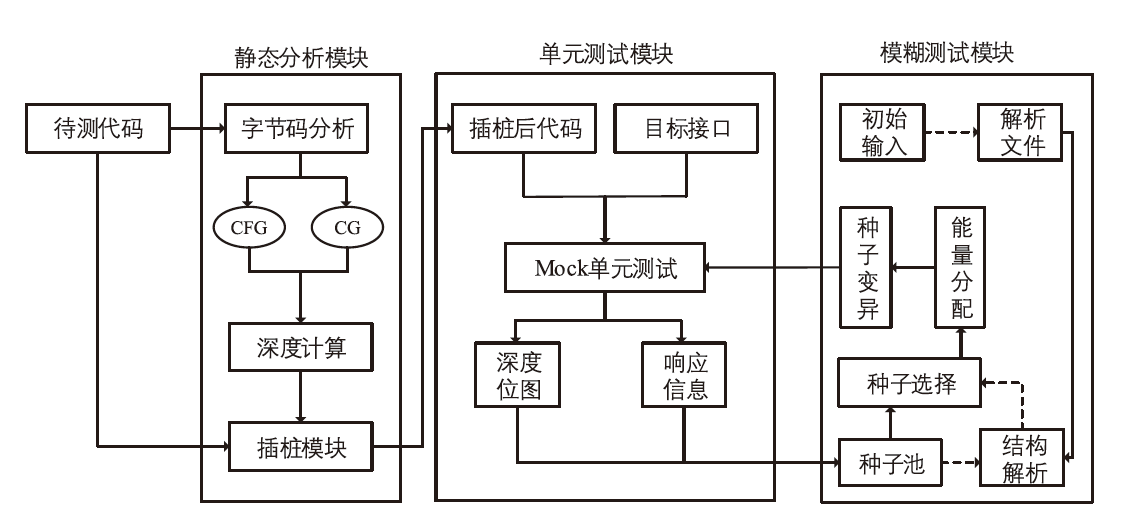
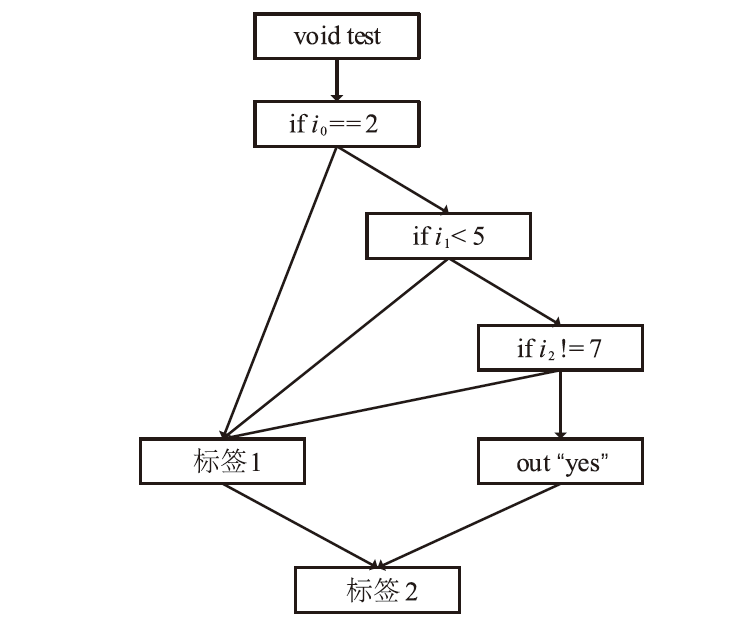
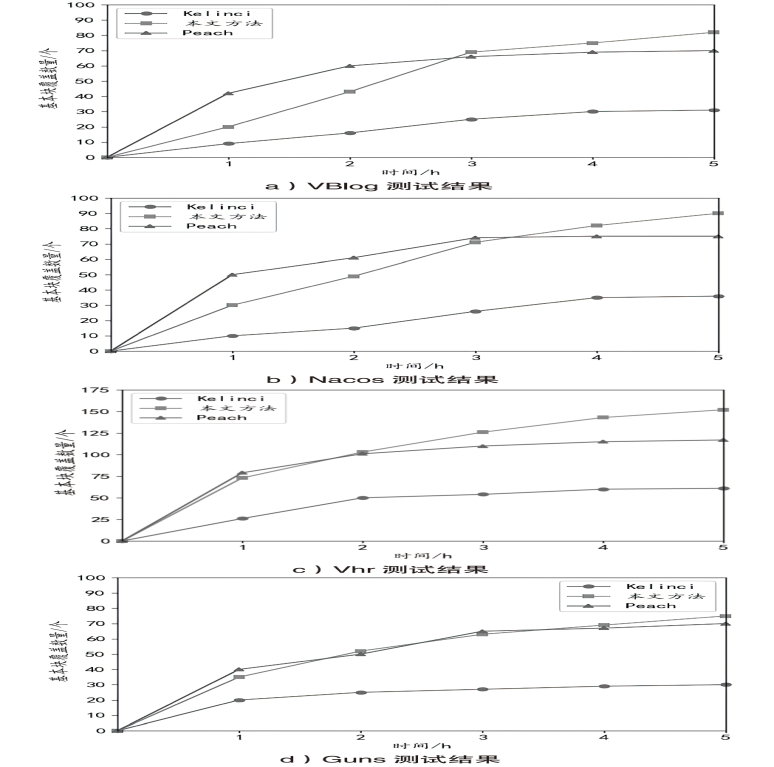
随着Java Web的广泛应用,其安全问题日益突出。模糊测试作为一种有效的漏洞挖掘方法,目前已经被用于Java漏洞的检测。然而,由于Java Web应用代码规模庞大、业务逻辑复杂,现有的漏洞挖掘工具在模糊测试中存在随机性高、代码检测深度低的问题,导致漏洞挖掘的准确率较低。因此,文章提出基于多维深度导向的Java Web模糊测试方法。该方法使用Jimple作为待测Java Web应用字节码的三地址码中间表示,并生成代码对应的函数间调用图和函数内控制流图,在此基础上分析每个基本块的多维深度。同时,根据多维深度和模糊测试执行时间优化模糊测试指导策略,设计相应的输入结构解析策略、能量分配策略和变异算法调度策略,提升模糊测试的准确性。实验结果表明,相较于现有的模糊测试工具Peach和Kelinci,该方法能够在性能消耗较低的情况下取得更好的漏洞检测效果。
中图分类号:
引用本文
王鹃, 龚家新, 蔺子卿, 张晓娟. 多维深度导向的Java Web模糊测试方法[J]. 信息网络安全, 2024, 24(2): 282-292.
WANG Juan, GONG Jiaxin, LIN Ziqing, ZHANG Xiaojuan. Multidimensional Depth Oriented Fuzzing Method of Java Web Applications[J]. Netinfo Security, 2024, 24(2): 282-292.
表3
具体异常触发情况
| 漏洞类型 | 测试对象 | Kelinci触发的异常数量 /个 | Peach触发的异常数量/个 | 本文方法触发的异常数量/个 |
|---|---|---|---|---|
| 数据库异常 | VBlog | 1 | 1 | 1 |
| Nacos | 0 | 0 | 0 | |
| Vhr | 0 | 2 | 2 | |
| Guns | 0 | 0 | 0 | |
| 未授权访问 | VBlog | 0 | 0 | 1 |
| Nacos | 0 | 1 | 1 | |
| Vhr | 0 | 0 | 0 | |
| Guns | 0 | 0 | 0 | |
| 实例未初始化 | VBlog | 1 | 4 | 9 |
| Nacos | 0 | 0 | 1 | |
| Vhr | 3 | 5 | 14 | |
| Guns | 0 | 0 | 1 | |
| XSS注入 | VBlog | 0 | 0 | 0 |
| Nacos | 0 | 0 | 0 | |
| Vhr | 0 | 0 | 1 | |
| Guns | 0 | 0 | 1 | |
| 类型混淆 | VBlog | 0 | 0 | 0 |
| Nacos | 0 | 0 | 0 | |
| Vhr | 0 | 0 | 0 | |
| Guns | 0 | 0 | 1 |
| [1] | COWARD D, YOSHIDA Y. Java Servlet Specification Version 2.3[EB/OL]. (2001-09-17)[2023-01-15]. https://jcp.org/aboutJava/communityprocess/first/jsr053/servlet23_PFD.pdf. |
| [2] | HUANG Junyong. Research and Design Based on Spring Framework[J]. Computer Knowledge and Technology, 2018, 14(3): 116-117, 120. |
| 黄俊勇. 基于Spring框架的研究与设计[J]. 电脑知识与技术, 2018, 14(3): 116-117, 120. | |
| [3] | QIU Ruonan, HU Anqi, PENG Guojun, et al. Java Web Framework Vulnerability Universal Detection and Location Scheme Based on RASP Technology[J]. Journal of Wuhan University (Science Edition), 2020, 66(3): 285-296. |
| 邱若男, 胡岸琪, 彭国军, 等. 基于RASP技术的Java Web框架漏洞通用检测与定位方案[J]. 武汉大学学报(理学版), 2020, 66(3): 285-296. | |
| [4] | National Internet Emergency Center. Analysis Report on China’s Internet Network Security Monitoring Data in the First Half of 2021[EB/OL]. (2021-07-31)[2023-01-15]. https://www.cert.org.cn/publish/main/upload/File/first-half%20%20year%20cyberseurity%20report%202021.pdf. |
| 国家互联网应急中心. 2021年上半年我国互联网网络安全监测数据分析报告[EB/OL]. (2021-07-31)[2023-01-15]. https://www.cert.org.cn/publish/main/upload/File/first-half%20%20year%20cyberseurity%20report%202021.pdf. | |
| [5] |
TU Ling, MA Yue, CHENG Cheng, et al. Web Security Fuzzy Testing and Utility Evaluation Method Based on Protocol Hybrid Deformation[J]. Computer Science, 2017, 44(5): 141-145.
doi: 10.11896/j.issn.1002-137X.2017.05.025 |
|
涂玲, 马跃, 程诚, 等. 基于协议混合变形的Web安全模糊测试与效用评估方法[J]. 计算机科学, 2017, 44(5): 141-145.
doi: 10.11896/j.issn.1002-137X.2017.05.025 |
|
| [6] |
MILLER B P, FREDRIKSEN L, SO B. An Empirical Study of the Reliability of UNIX Utilities[J]. Communications of the ACM, 1990, 33(12): 32-44.
doi: 10.1145/96267.96279 URL |
| [7] | Google. American Fuzzy Lop[EB/OL]. (2020-07-05)[2023-01-15]. http://lcamtuf.coredump.cx/afl/. |
| [8] | BÖHME M, PHAM V H, NGUYEN M D, et al. Directed Greybox Fuzzing[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2329-2344. |
| [9] | CHEN Hongxu, XUE Yinxing, LI Yuekang, et al. Hawkeye: Towards a Desired Directed Grey-Box Fuzzer[C]// ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 2095-2108. |
| [10] | GWANGMU L, WOOCHUL S, BYOUNGYOUNG L. Constraint-Guided Directed Greybox Fuzzing[C]// USENIX. The 30th USENIX Security Symposium. Berkley: USENIX, 2021: 3559-3576. |
| [11] | JAYARAMAN K, HARVISON D, GANESH V, et al. JFuzz: A Concolic Whitebox Fuzzer for Java[EB/OL]. (2009-04-01)[2023-01-15]. https://people.csail.mit.edu/akiezun/jfuzz/jFuzz.pdf. |
| [12] | ZHU Hong. JFuzz: A Tool for Automated Java Unit Testing Based on Data Mutation and Metamorphic Testing Methods[C]// IEEE. 2015 Second International Conference on Trustworthy Systems and Their Applications. New York: IEEE, 2015: 8-15. |
| [13] | KERSTEN R, FIELD M, LUCKOW K, et al. POSTER: AFL-Based Fuzzing for Java with Kelinci[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2511-2513. |
| [14] | PADHYE R. JQF: A Feedback-Directed Fuzz Testing Platform for Java[EB/OL]. (2019-07-10)[2023-01-15]. https://github.com/rohanpadhye/jqf. |
| [15] | SHAWN R, JENS D. A Hybrid Analysis to Detect Java Serialisation Vulnerabilities[C]// IEEE. 2020 35th IEEE International Conference on Automated Software Engineering. New York: IEEE, 2020: 21-25. |
| [16] | YU Xintian, MA Enze, NIE Pengbo, et al. Approxi Fuzzer: Fuzzing towards Deep Code Snippets in Java Programs[C]// IEEE. 2021 IEEE 45th Annual Computers, Software, and Applications Conference. New York: IEEE, 2021: 1149-1156. |
| [17] | Peach Tech. Peach Software Official Website[EB/OL]. (2020-06-01)[2023-01-15]. http://www.peachfuzzer.com. |
| [18] | LU Ziguang. Research on Web Vulnerability Mining Algorithm Based on Improved Fuzzy Testing[D]. Nanning: Guangxi University, 2018. |
| 陆紫光. 基于改进模糊测试的Web漏洞挖掘算法研究[D]. 南宁: 广西大学, 2018. | |
| [19] | ZHOU Xinshi. Research and Implementation of Web Vulnerability Mining Technology Based on Fuzzy Testing[D]. Beijing: Beijing University of Posts and Telecommunications, 2020. |
| 周心实. 基于模糊测试的Web漏洞挖掘技术研究与实现[D]. 北京: 北京邮电大学, 2020. | |
| [20] | Sable. Soot: A Java Optimization Framework[EB/OL]. (2012-01-22)[2023-01-15]. https://www.sable.mcgill.ca/soot/. |
| [21] | LI Yuanling, CHEN Hua, LIU Li. Java Program Control Flow Analysis and Graphic Output of Soot[J]. Computer System Application, 2009, 18(10): 88-92. |
| 李远玲, 陈华, 刘丽. Soot的Java程序控制流分析及图形化输出[J]. 计算机系统应用, 2009, 18(10): 88-92. |
| [1] | 洪玄泉, 贾鹏, 刘嘉勇. AFLNeTrans:状态间关系感知的网络协议模糊测试[J]. 信息网络安全, 2024, 24(1): 121-132. |
| [2] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [3] | 钟远鑫, 刘嘉勇, 贾鹏. 基于动态时间切片和高效变异的定向模糊测试[J]. 信息网络安全, 2023, 23(8): 99-108. |
| [4] | 吴佳明, 熊焰, 黄文超, 武建双. 一种基于距离导向的模糊测试变异方法[J]. 信息网络安全, 2021, 21(10): 63-68. |
| [5] | 杜笑宇, 叶何, 文伟平. 基于字节码搜索的Java反序列化漏洞调用链挖掘方法[J]. 信息网络安全, 2020, 20(7): 19-29. |
| [6] | 李明磊, 黄晖, 陆余良. 面向漏洞挖掘的基于符号分治区的测试用例生成技术[J]. 信息网络安全, 2020, 20(5): 39-46. |
| [7] | 段斌, 李兰, 赖俊, 詹俊. 基于动态污点分析的工控设备硬件漏洞挖掘方法研究[J]. 信息网络安全, 2019, 19(4): 47-54. |
| [8] | 胡建伟, 赵伟, 闫峥, 章芮. 基于机器学习的SQL注入漏洞挖掘技术的分析与实现[J]. 信息网络安全, 2019, 19(11): 36-42. |
| [9] | 王夏菁, 胡昌振, 马锐, 高欣竺. 二进制程序漏洞挖掘关键技术研究综述[J]. 信息网络安全, 2017, 17(8): 1-13. |
| [10] | 郭亮, 罗森林, 潘丽敏. 编码函数交叉定位网络协议测试数据生成方法研究[J]. 信息网络安全, 2016, 16(3): 8-14. |
| [11] | . 基于模糊测试的网络协议自动化漏洞挖掘工具设计与实现[J]. , 2014, 14(6): 23-. |
| [12] | 曾刚. 基于Java Web Start技术的网络考试系统安全问题研究[J]. , 2013, 13(4): 0-0. |
| [13] | 崔化良;兰芸;崔宝江. 动态污点分析技术在ActiveX控件漏洞挖掘上的应用[J]. , 2013, 13(12): 0-0. |
| [14] | 黄超;李毅;麻荣宽;马建勋. 网页漏洞挖掘系统设计[J]. , 2012, 12(9): 0-0. |
| [15] | 王学;李学新;周智鹏;袁耀文. S2E测试平台及并行性能分析[J]. , 2012, 12(7): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||