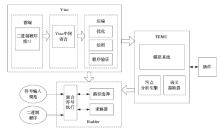
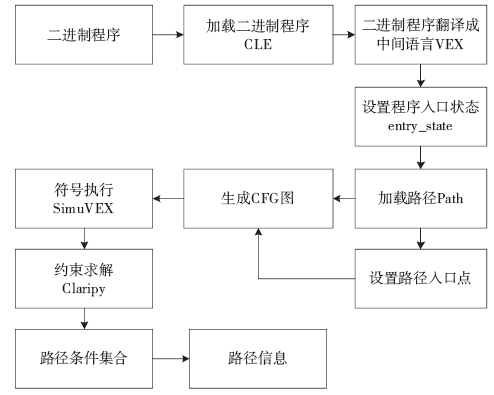
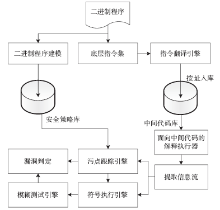
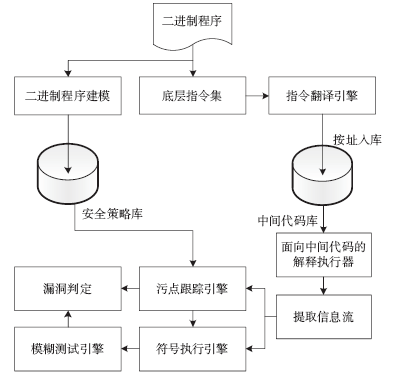
信息网络安全 ›› 2017, Vol. 17 ›› Issue (8): 1-13.doi: 10.3969/j.issn.1671-1122.2017.08.001
• • 下一篇
二进制程序漏洞挖掘关键技术研究综述
- 1.北京理工大学软件学院软件安全工程技术北京市重点实验室,北京 100081
2.中国黄金集团公司,北京 100011
-
收稿日期:2017-06-22出版日期:2017-08-20发布日期:2020-05-12 -
作者简介:作者简介: 王夏菁(1994—),女,山西,博士研究生,主要研究方向为信息安全;胡昌振(1967—),男,湖北,教授,博士,主要研究方向为信息安全;马锐(1972—),女,河南,副教授,博士,主要研究方向为信息安全;高欣竺(1982—),女,山东,助理工程师,硕士研究生,主要研究方向为网络安全。
-
基金资助:国家重点研发计划[2016QY07X1404]
A Survey of the Key Technology of Binary Program Vulnerability Discovery
Xiajing WANG1, Changzhen HU1, Rui MA1( ), Xinzhu GAO2
), Xinzhu GAO2
- 1.Beijing Key Laboratory of Software Security Engineering Technology, School of Software, Beijing Institute of Technology, Beijing 100081, China
2.China National Gold Group Corporation, Beijing 100011, China
-
Received:2017-06-22Online:2017-08-20Published:2020-05-12
摘要:
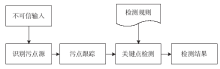
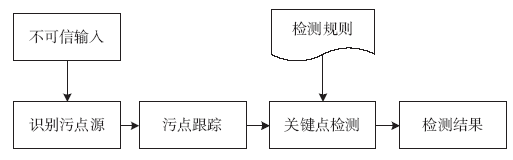
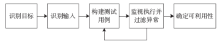
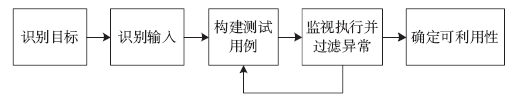
漏洞在当前的网络空间中已被各方所关注。虽然源代码漏洞分析取得显著进展且具有语义丰富的特点,但实际应用中大量软件均以二进制代码形式存在,因此,针对二进制代码的漏洞挖掘技术研究具有很强的实用价值。文章简要介绍了目前较为典型的二进制漏洞分析框架,并根据现有研究工作,提出未来对二进制程序漏洞挖掘技术研究的整体思路,随后对其中的一些关键点、关键技术分别进行了调研。文章首先对中间语言的研究背景和意义进行了简要介绍;其次针对污点分析、符号执行以及模糊测试三项关键技术,分别介绍了三者的基本原理和分类标准、处理流程、研究现状以及存在的问题;最后进行了简单的总结。文章对二进制程序的漏洞挖掘技术进行了简要的研究,有助于开展后续研究工作。
中图分类号:
引用本文
王夏菁, 胡昌振, 马锐, 高欣竺. 二进制程序漏洞挖掘关键技术研究综述[J]. 信息网络安全, 2017, 17(8): 1-13.
Xiajing WANG, Changzhen HU, Rui MA, Xinzhu GAO. A Survey of the Key Technology of Binary Program Vulnerability Discovery[J]. Netinfo Security, 2017, 17(8): 1-13.
| [1] | 吴世忠,郭涛,董国伟,等. 软件漏洞分析技术[M]. 北京:科学出版社,2014. |
| [2] | 诸葛建伟,陈力波,田繁,等. 基于类型的动态污点分析[J]. 清华大学学报:自然科学版,2012,52(10):1320-1321. |
| [3] | 王铁磊. 面向二进制程序的漏洞挖掘关键技术研究[D]. 北京:北京大学,2011. |
| [4] | 姜玲燕,梁阿磊,管海兵. 动态二进制翻译中的中间表示[J]. 计算机工程,2009,35(9):283-285. |
| [5] | SONG D, BRUMLEY D, YIN Heng, et al.BitBlaze: A New Approach to Computer Security via Binary Analysis[C]//Springer. 4th International Conference on Information Systems Security, December 16-20, 2008, Hyderabad, India. Berlin: Heidelberg, 2008: 1-25. |
| [6] | SHOSHITAISHVILI Y, WANG Ruoyu, SALLS C, et al.The Art of War: Offensive Techniques in Binary Analysis[C]//IEEE. 2016 IEEE Symposium on Security and Privacy, May 22-26, 2016, San Jose, CA, USA. New Jersey: IEEE, 2016: 138-157. |
| [7] | 陈凯明,刘宗田. 符号执行过程的DFA和CFA[J]. 计算机工程,2002,28(11):95-96. |
| [8] | CIFUENTES C, EMMERIK V M.UQBT: Adaptable Binary Translation at Low Cost[J]. Computer, 2000, 33(3): 60-66. |
| [9] | BRUSCHI D, MARTIGNONI L, MONGA M. Boomerang[EB/OL]. , 2017-2-11. |
| [10] | 马金鑫,李舟军,忽朝俭,等. 一种重构二进制代码中类型抽象的方法[J]. 计算机研究与发展,2013,50(11):2418-2428. |
| [11] | NETHERCOTE N, SEWARD J.Valgrind: a Framework for Heavyweight Dynamic Binary Instrumentation[J]. ACM Sigplan Notices, 2007, 42(6): 89-100. |
| [12] | DENNING D E.A Lattice Model of Secure Information Flow[J]. Communications of the ACM, 1976, 19(5): 236-243. |
| [13] | 黄强,曾庆凯. 基于信息流策略的污点分析传播分析及动态验证[J]. 软件学报,2011,22(9):2036-2048. |
| [14] | 史大伟,袁天伟. 一种粗细粒度结合的动态污点分析方法[J]. 计算机工程,2014,40(3):12-17. |
| [15] | 代伟,刘智,刘益和. 基于二进制代码的动态污点分析[J]. 计算机应用与研究,2014,31(8):2497-2505. |
| [16] | YIN Heng, SONG D. Temu: Binary Code Analysis via Whole-system Layered Annotative Execution[EB/OL]. , 2016-6-11. |
| [17] | KANG M G, MCCAMANT S, POOSANKAM P, et al. DTA++: Dynamic Taint Analysis with Targeted Control-Flow Propagation[EB/OL]. , 2011-2-6. |
| [18] | 马金鑫,李舟军,张涛,等. 基于执行踪迹离线索引的污点分析方法[EB/OL]. , 2017-2-20. |
| [19] | 王蕾,李丰,李炼,等. 污点分析技术的原理和实践应用[J]. 软件学报,2017,28(4):1-11. |
| [20] | 宋铮,王永剑,金波,等. 二进制程序动态污点分析技术研究综述[J]. 信息网络安全,2016(3):77-83. |
| [21] | NEWSOME J, SONG D.Dynamic Taint Analysis for Automatic Detection, Analysis and Signature Generation of Exploits on Commodity Software[J] Chinese Journal of Engineering Mathematics, 2005, 29(5): 720-724. |
| [22] | CLAUSE J, LI Wanchun, ORSO A.Dytan: A Generic Dynamic Taint Analysis Framework[C]//ACM. 2007 International Symposium on Software Testing and Analysis, July 9-12, 2007, London, United Kingdom. New York: ACM, 2007: 196-206. |
| [23] | QIN Feng, WANG Cheng, LI Zhenmin, et al.Lift: A Low-overhead Practical Information Flow Tracking System for Detecting Security Attacks[C]//IEEE. 39th Annual IEEE/ACM International Symposium on Microarchitecture, Orlando, FL, USA, December 9-13, 2006. New Jersey: IEEE, 2006: 135-148. |
| [24] | 彭建山,奚琪,王清贤. 二进制程序整型溢出漏洞的自动验证方法[J]. 信息网络安全,2017(5):14-21. |
| [25] | 林伟,蔡瑞杰,祝跃飞,等. 基于语义规则的污点传播分析优化方法[J]. 计算机应用,2014,34(12):3511-3514. |
| [26] | 朱正欣,曾凡平,黄心依. 二进制程序的动态符号化污点分析[J]. 计算机科学,2016,43(2):155-158. |
| [27] | 崔化良,兰芸,崔宝江. 动态污点分析技术在ActiveX 控件漏洞挖掘上的应用[J]. 信息网络安全,2013(12):16-19. |
| [28] | MOLNAR D, LI Xuecong, WAGNER D.Dynamic Test Generation to Find Integer Bugs in x86 Binary Linux Programs[C]//ACM. 18th Conference on USENIX Security Symposium, August 10-14, 2009, Montreal, Canada. New York: ACM, 2009: 67-82. |
| [29] | GODEFROID P, LEVIN M Y, MOLNAR D A. Automated Whitebox Fuzz Testing[EB/OL]. , 2017-2-12. |
| [30] | 陆萍萍. 二进制代码的漏洞挖掘技术研究[D]. 北京:北京理工大学,2013. |
| [31] | BOYER R S, ELSPAS B, LEVITT K N.SELECT—A Formal System for Testing and Debugging Programs by Symbolic Execution[J]. ACM SigPlan Notices, 1975, 10(6): 234-245. |
| [32] | BUSH W R, PINCUS J D, SIELAFF D J.A Static Analyzer for Finding Dynamic Programming Errors[J]. Software-Practice and Experience, 2000, 30(7): 775-802. |
| [33] | SEN K, MARINOV D, AGHA G.CUTE: A Concolic Unit Testing Engine for C[J]. ACM Sigsoft Software Engineering Notes, 2005, 30(5): 263-272. |
| [34] | GODEFROID P, KLARLUND N, SEN K. DART: Directed Automated Random Testing[EB/OL]. , 2017-2-11. |
| [35] | CADAR C, DUNBAR D, ENGLER D R.KLEE: Unassisted and Automatic Generation of High-coverage Tests for Complex Systems Programs[C]//ACM. 8th USENIX Symposium on Operating Systems Design and Implementation, December 8-10, 2008, San Diego, California. New Jersey: 2008: 209-224. |
| [36] | BOONSTOPPEL P, CADAR C, ENGLER D.RWset: Attacking Path Explosion in Constraint-based Test Generation[C]//Springer. 14th International Conference on Tools and Algorithms for the Construction and Analysis of Systems, March 29-April 6, 2008, Budapest, Hungary. Berlin: Heidelberg, 2008: 351-366. |
| [37] | 李舟军,张俊贤,廖湘科,等. 软件安全漏洞检测技术[J]. 计算机学报,2015,38(4):717-728. |
| [38] | MILLER B P, FREDRIKSEN L, SO B.An Empirical Study of the Reliability of UNIX Utilities[J]. Communications of the ACM, 1990, 33(12): 32-44. |
| [39] | KAKSONEN R. A Functional Method for Assessing Protocol Implementation Security[EB/OL]. , 2017-2-15. |
| [40] | AITEL D. An Introduction to SPIKE, the Fuzzer Creation Kit[EB/OL]. , 2017-2-15. |
| [41] | EDDINGTON M. sPeach[EB/OL]. , 2017-2-10. |
| [42] | AMINI P. Sulley[EB/OL]. , 2017-2-10. |
| [43] | WANG Tielei, WEI Tao, GU Guofei, et al.TaintScope: A Checksum-aware Directed Fuzzing Tool for Automatic Software Vulnerability Detection[C]//IEEE. 2010 IEEE symposium on Security and Privacy, May 16-19, 2010, Oakland, CA, USA. New Jersey: IEEE, 2010: 497-512. |
| [44] | 杜晓军,林柏钢,林志远,等. 安全软件模糊测试中多种群遗传算法的研究[J]. 山东大学学报:理学版,2013(7):79-84. |
| [45] | 史记,曾昭龙,杨从保,等. Fuzzing测试技术综述[J]. 信息网络安全,2014(3):87-91. |
| [46] | 王连赢. 文件触发类二进制程序漏洞挖掘技术研究[D]. 北京:北京邮电大学,2015. |
| [1] | 段斌, 李兰, 赖俊, 詹俊. 基于动态污点分析的工控设备硬件漏洞挖掘方法研究[J]. 信息网络安全, 2019, 19(4): 47-54. |
| [2] | 胡建伟, 赵伟, 闫峥, 章芮. 基于机器学习的SQL注入漏洞挖掘技术的分析与实现[J]. 信息网络安全, 2019, 19(11): 36-42. |
| [3] | 陈虎, 周瑶, 赵军锁. 针对特定文件结构和关键指令的符号执行优化方法[J]. 信息网络安全, 2018, 18(9): 86-94. |
| [4] | 达小文, 毛俐旻, 吴明杰, 郭敏. 一种基于补丁比对和静态污点分析的漏洞定位技术研究[J]. 信息网络安全, 2017, 17(9): 5-5. |
| [5] | 彭建山, 奚琪, 王清贤. 二进制程序整型溢出漏洞的自动验证方法[J]. 信息网络安全, 2017, 17(5): 14-21. |
| [6] | 郭亮, 罗森林, 潘丽敏. 编码函数交叉定位网络协议测试数据生成方法研究[J]. 信息网络安全, 2016, 16(3): 8-14. |
| [7] | 宋铮, 王永剑, 金波, 林九川. 二进制程序动态污点分析技术研究综述[J]. 信息网络安全, 2016, 16(3): 77-83. |
| [8] | . 基于模糊测试的网络协议自动化漏洞挖掘工具设计与实现[J]. , 2014, 14(6): 23-. |
| [9] | 崔化良;兰芸;崔宝江. 动态污点分析技术在ActiveX控件漏洞挖掘上的应用[J]. , 2013, 13(12): 0-0. |
| [10] | 黄超;李毅;麻荣宽;马建勋. 网页漏洞挖掘系统设计[J]. , 2012, 12(9): 0-0. |
| [11] | 王学;李学新;周智鹏;袁耀文. S2E测试平台及并行性能分析[J]. , 2012, 12(7): 0-0. |
| [12] | 康凯;郭颖;崔宝江. 基于XML的面向二进制漏洞模式形式化描述研究[J]. , 2012, 12(12): 0-0. |
| [13] | 徐有福;文伟平;尹亮. 基于补丁引发新漏洞的防攻击方法研究[J]. , 2011, 11(7): 0-0. |
| [14] | 姚洪波;尹亮;文伟平. 基于FUZZING试技术的Windows内核安全漏洞挖掘方法研究及应用[J]. , 2011, 11(12): 0-0. |
| [15] | 时志伟;李小军. 基于信息流分析的源代码漏洞挖掘技术研究[J]. , 2011, 11(11): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||